
- What is AWS CloudTrail?
- Why is AWS CloudTrail Required?
- Features of AWS CloudTrail
- AWS Trail
- AWS Event
- Advantages of AWS CloudTrail
- Conclusion
What is AWS CloudTrail?
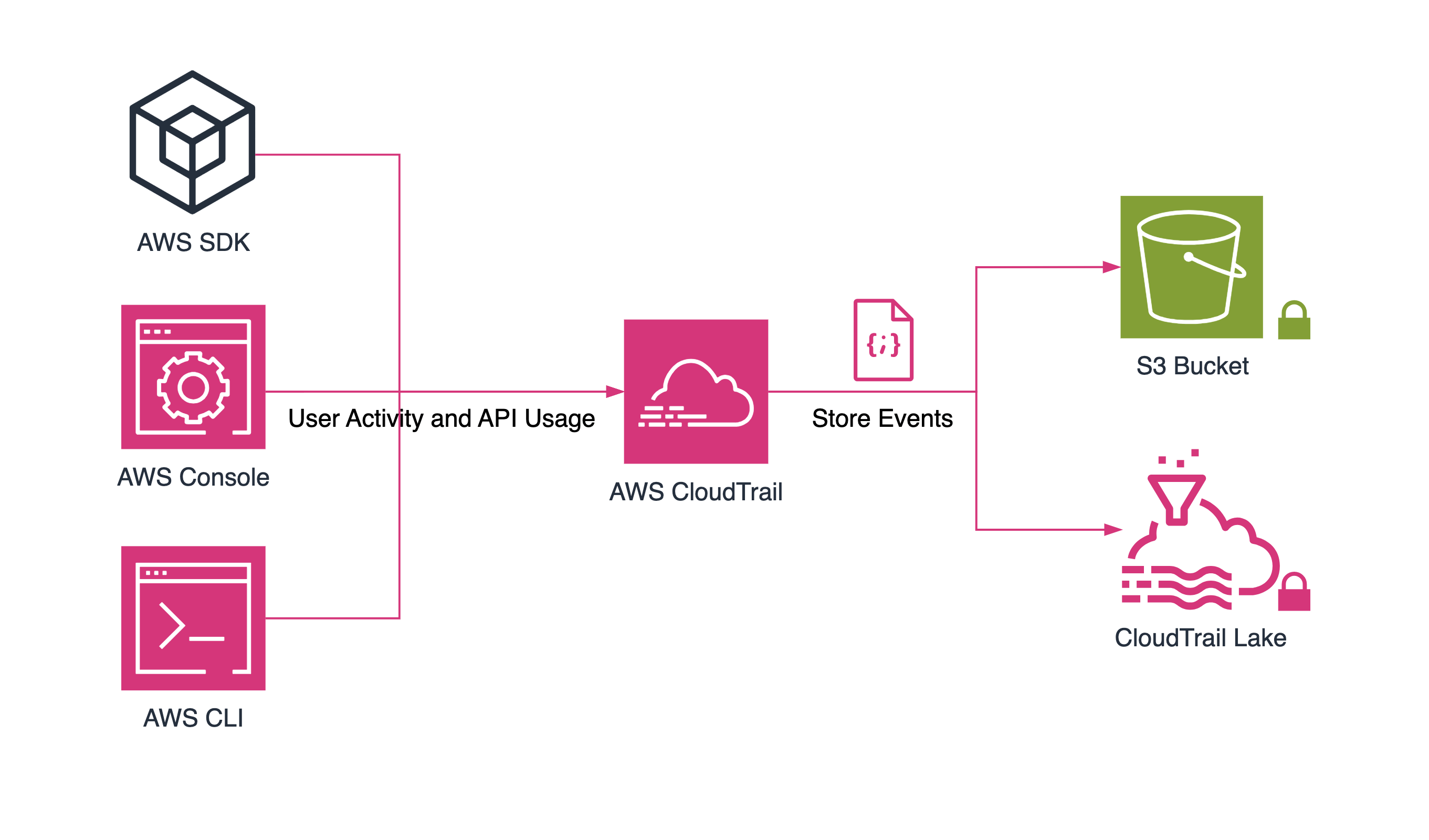
AWS CloudTrail is a provider provided through AWS that permits operational and chance auditing, as well as governance and compliance on your AWS account. Events in CloudTrail are actions performed by a user, role, or AWS provider. The AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are only some examples of the activities that could occur.AWS CloudTrail best helps the AWS offerings located right here and presents the CloudTrail Event History facts for the preceding ninety days for the region you’re presently browsing. These best encompass control activities concerning account interest, along with creating, modifying, and deleting API requests.You should install a CloudTrail to get a complete record of account interest, along with all management activities, facts activities, and read-most effective interest.Enable the AWS CloudTrail function, which creates a digest document for every log document it presents, by turning on the capability for log document integrity at the trail. Utilize the digest documents created to test the accuracy of the furnished CloudTrail documents.Use AWS Config to immediately permit the log document integrity function in CloudTrail. For every log document that CloudTrail sends, a digest document could be created automatically. Use the digest documents to test the accuracy of the furnished CloudTrail documents.
Why is AWS CloudTrail Required?
We use AWS Cloudtrail to observe, search, download, archive, examine, and react to account activity throughout your AWS infrastructure; use CloudTrail.To examine and react to activities for your AWS account, you can discover who or what took what action, what assets were used while the occasion occurred, and other information. You can track who made what modifications to your programs using CloudTrail. Issues are probably discovered. They aren’t unique, and you could configure CloudTrail to supply events, for example, to a CloudWatch log. Monitoring sports for your AWS surroundings is the principal utility of AWS CloudTrail. Because it can offer records of sports for your AWS surroundings, CloudTrail additionally serves as compliance support. Thus, it’s easy to ensure your business enterprise is following internal guidelines and regulatory regulations. AWS CloudTrail provides detailed records of API calls made on your AWS account, allowing for improved monitoring and security. With CloudTrail, you can identify anomalies, track access to sensitive resources, and maintain an audit trail for compliance purposes. It helps detect unauthorized access and ensures that changes made to the AWS environment are properly documented. Additionally, CloudTrail integrates with other AWS services like AWS Lambda, CloudWatch, and SNS to automate alerts and responses to suspicious activities. By configuring CloudTrail for proactive monitoring, you can enhance security posture and maintain operational oversight of your AWS resources.
Features of AWS CloudTrail
- Amazon CloudTrail Insights:By constantly comparing CloudTrail control occasions, Amazon CloudTrail Insights permits clients of Amazon Web Services to identify and take motion on unusual conduct related to writing API calls. When CloudTrail notices a sudden write control API pastime to your account, insights occasions are logged.When CloudTrail identifies an unusual pastime, the occasion is transmitted to the trail’s vacation spot S3 bucket even when Insights is enabled.
- Data Events:You may also document object-stage API activity and attain complete statistics, together with who made the request, wherein and when it was made, and other statistics, by turning on information event recording in CloudTrail. Data events maintain the tune of the moves taken on or internal resources (information aircraft operations).Data occasions regularly encompass high-extent operations. CloudTrail information occasion recording covers operations such as Amazon S3 object-stage APIs, Amazon Lambda characteristic Invoke APIs, and Amazon DynamoDB item-stage APIs.
- Management Events: Control (“manage aircraft”) operations performed at the sources of your Amazon Web Services account are discovered via control occasions.You could use document management strategies like Amazon EC2, such as creation, deletion, and change.You may also see statistics for every occasion, together with the Amazon Web Services account, IAM person role, IP address of the person who initiated the motion, the time the motion took place, and the sources that were impacted.
- Multi-place configuration: For an unmarried account, you can install Amazon CloudTrail to ship log documents from many places to an unmarried Amazon S3 bucket. All modifications may be carried out uniformly throughout all presently energetic and released areas, leading to a setup that applies to all areas.For complete instructions, see Aggregating CloudTrail Log Files to a Single Amazon S3 Bucket in the Amazon CloudTrail User Guide.
- Event History: Your current Amazon Web Services account pastime is to be had for viewing, searching, and downloading. You can use this to enhance your safety strategies and resolve operational problems more truthfully by gaining visibility into adjustments to your Amazon Web Services account sources.
- Management Event: By default, logged-in and Management occasions, additionally called manage aircraft operations, deliver facts on control operations made on sources for your AWS account.
- Data Event: It’s no longer through default logged Data occasions, occasionally called information aircraft operations, that facts on aid sports performed on or in aid are delivered. Data occasions often consist of vast volumes of hobbies.
- Insights Event: Observable conduct for your AWS account is captured through insights occasions. When you permit Insights occasions, CloudTrail will discover suspicious behavior and log it to S3. The pertinent information that insights occasions provide, including the related API, incident time, and statistics, permits you to understand sudden hobbies and take suitable action.
- Security Analysis and Troubleshooting: By periodically shooting in-depth records of adjustments made to the AWS account, AWS CloudTrail will allow the consumer to discover and troubleshoot protection and operational issues.
- Simplified Compliance: By routinely shooting and retaining occasion logs for movements created periodically inside the AWS account, AWS CloudTrail can alternate the compliance audits. Searching via the log records is made easy by integrating with Amazon CloudWatch Logs. Additionally, it aids in figuring out activities that might be out of compliance and hastens incident investigations and auditor request responses.
- Visibility into consumer and useful resource pastime: By shooting AWS Management Console activities and API calls, Amazon CloudTrail will enhance consumers’ perception and applicable resource pastimes.The consumer can confirm which money is owed, and customers are called AWS. Once the calls took place, the calls` deliver net protocol deal changed into form.
- Security Automation: The consumer can use Amazon CloudTrail to routinely respond to the account for the safety of Amazon resources. The consumer might be capable of specifying workflows that run as soon as activities that might bring about protection vulnerabilities are located, a way to combine Amazon CloudWatch Events.
- Real-Time Monitoring and Alerts: AWS CloudTrail enables real-time monitoring of events and can be configured to send alerts for specific activities, such as unauthorized access attempts or changes to critical resources. By integrating CloudTrail with Amazon CloudWatch, users can set up custom alarms to quickly detect security incidents and trigger automated responses.
- Detailed Audit Trail: CloudTrail offers a comprehensive, detailed audit trail that allows users to trace every action taken in their AWS environment. This level of transparency ensures that any suspicious or unauthorized activity can be identified and investigated, providing critical information for forensic analysis and enhancing the overall security posture.
- Access Management and Role Review: CloudTrail provides visibility into who accessed what resources and when, allowing for a detailed review of user roles and permissions. This helps ensure that only authorized personnel have access to sensitive data and resources, minimizing the risk of privilege escalation and improving access control.
- Incident Response and Forensic Investigation: CloudTrail logs can serve as a crucial tool in incident response and forensic investigations. By retaining logs of all AWS API calls and actions, CloudTrail helps security teams reconstruct timelines of events leading to a security breach or operational failure, allowing for a more effective and rapid resolution of security issues.
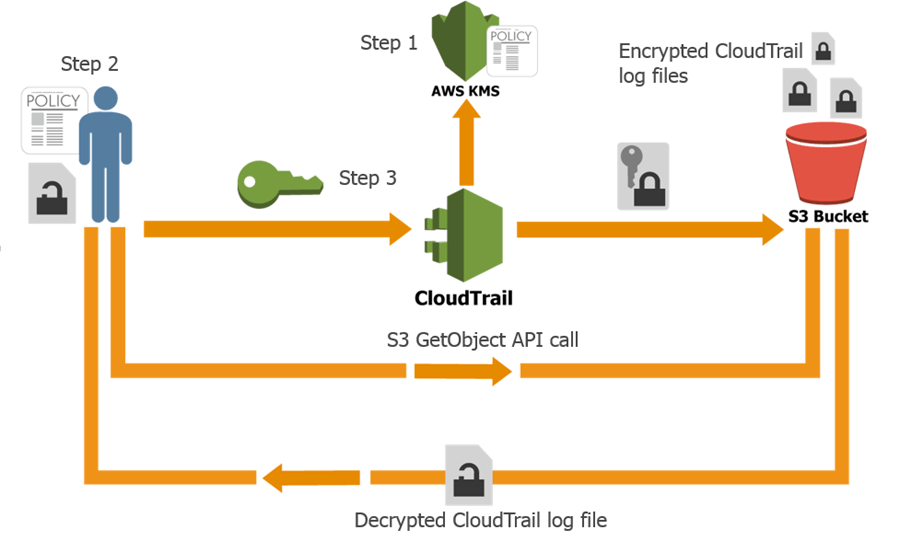
AWS Trail
AWS path is a setup that lets you ship events to a particular Amazon S3 bucket. With AmazonCloudWatch Logs and Amazon EventBridge, you could additionally distribute and study events in a path. A path may be produced through the CloudTrail console, AWS CLI, or CloudTrail API. When you set up a path that applies to each place, CloudTrail logs occasions in each area and sends the CloudTrail occasion log documents to a particular S3 bucket. Once you assemble a path that applies to all areas, a new place is immediately covered, and its occasions are tracked if it’s miles delivered. An all-areas path is chosen by default when you create a path inside the CloudTrail interface in view of its miles, which is suggested as an exceptional exercise to achieve this with the intention of documenting hobbies throughout all areas for your account. Only the AWS S3 CLI can improve a single-area path to log all areas.Once the all-regions path is set up, it ensures that CloudTrail logs events from every AWS region, providing a comprehensive view of activity across your entire AWS environment. This is particularly useful for organizations with resources deployed in multiple regions, ensuring no critical activity is overlooked. The logs stored in the S3 bucket can be easily accessed for analysis, auditing, and troubleshooting. Additionally, integrating with Amazon CloudWatch Logs or EventBridge enables real-time monitoring and automatic triggering of workflows based on the logged events. By using this setup, you maintain a centralized, consistent log that meets compliance and operational needs across all regions.
AWS Event
This hobby might also contain a circulation made by a user, role, or carrier that CloudTrail can watch. Events are transmitted to any path consisting of international offerings and are pronounced as happening within the US East (N. Virginia) Region for international offerings like IAM, STS, CloudFront, and Route 53.The following attributes: event name, User name, Resource name, Event Source, Event ID, and Resource kind may be used to clear out logs further into the Time range varieties of AWS Events are as follows:
Only when CloudTrail notices modifications to your account`s API usage that extensively deviate from the account`s ordinary usage styles are insights occasions recorded.
AWS Cloudtrail Pricing
Management events are provided free of charge for the first time in each AWS region, allowing you to track and manage control events without incurring additional costs. However, once you exceed the free tier, there are charges for additional copies of management events, which are billed based on the volume of logged data.For data events, charges apply to specific AWS resources that are being tracked, such as Lambda functions, DynamoDB tables, and S3 buckets. Only the designated resources are recorded, and you are billed for the event logging of these resources. It’s important to carefully monitor which resources are being tracked to manage costs effectively.
Since CloudTrail sends logs to an S3 bucket, the cost associated with storing the logs depends on the storage class and usage. If you use features like event filtering or have a large volume of logs, the associated S3 costs could increase. Additionally, accessing and retrieving logs from S3, especially in high-frequency use cases, may incur additional costs.To minimize storage costs, it is advisable to periodically review and archive logs that are no longer required for immediate analysis. You can also set lifecycle policies to transition older logs to cheaper storage tiers like S3 Glacier, helping you optimize costs while maintaining access to historical event data.
Advantages of AWS CloudTrail
Conclusion
Since all AWS money owed has Amazon Cloudtrail enabled, we researched how it captures consumer account pastime upon account creation. The consumer might be capable of studying and switching the beyond 90 days` worth of sports finished on their supported offerings money owed, such as creating, modifying, and deleting. AWS CloudTrail captures and logs account activity, including actions such as creating, modifying, and deleting resources within supported AWS services. By default, CloudTrail logs are retained for 90 days in the CloudTrail event history, allowing users to view past activities within that time frame. However, users can modify the retention period by exporting the logs to Amazon S3 for long-term storage and further analysis. CloudTrail provides detailed logs, which include information on the API calls made, the identity of the user, and the source IP address, offering transparency and security. Organizations should configure appropriate permissions and policies to ensure the integrity and confidentiality of the logs.





