
- Introduction to ARN
- ARN Structure and Components
- Using ARN for Resource Identification
- ARN in IAM Policies
- Common Uses of ARN
- Managing Permissions with ARN
- Best Practices for Working with ARN
- Conclusion
Introduction to ARN
An Amazon Resource Name (ARN) is a unique identifier used by AWS to refer to resources within its cloud ecosystem. ARNs are used to uniquely identify AWS resources across all services, including EC2 instances, S3 buckets, Lambda functions, IAM roles, and more. They are essential for specifying resources in various AWS operations, such as in API calls, IAM policies, and resource management tasks. In essence, an ARN acts as the address of an AWS resource, allowing other services or users to refer to that resource unambiguously, a concept thoroughly explained in Amazon Web Service Training to ensure users understand how to manage and reference resources effectively within AWS. The ARN structure ensures that every resource in AWS is identifiable globally within the AWS environment. An ARN provides a consistent way to reference resources, ensuring interoperability across different AWS services. It helps in specifying access controls and permissions, enabling fine-grained security for resources. Additionally, ARNs play a crucial role in automation, allowing tools like AWS CloudFormation and AWS Lambda to manage and interact with resources seamlessly.
Are You Interested in Learning More About AWS? Sign Up For Our AWS Course Today!
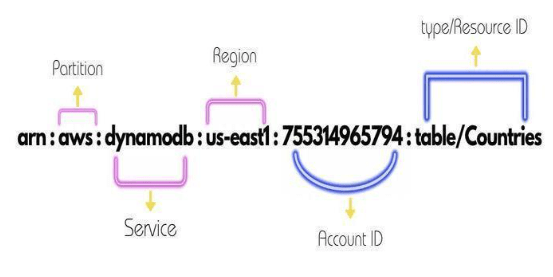
ARN Structure and Components
An ARN follows a specific structure, which makes it easy to interpret and distinguish between different types of AWS resources, similar to how the Microsoft Azure Application Gateway has a defined structure to route and manage traffic across applications in an Azure environment. The general structure of an ARN is as follows:
- #arn:partition:service:region:account-id:resource
Here’s a breakdown of the components:
- arn: The literal prefix that identifies the string as an ARN.
- partition: The AWS partition where the resource is located. Examples include aws (standard AWS), aws-cn (China region), or aws-us-gov (U.S. government).
- service: The name of the AWS service the resource belongs to (e.g., s3, ec2, iam).
- region: The AWS region where the resource is located (e.g., us-west-2, us-east-1). Some global services, such as IAM, do not include a region.
- account-id: The AWS account ID or alias that owns the resource.
- resource: The specific resource identifier. This could be a resource name, ID, or path, depending on the resource type.
Example ARN for an S3 bucket:
- #arn:aws:s3:::my-bucket-name
Example ARN for an EC2 instance:
- #arn:aws:ec2:us-west-2:123456789012:instance/i-0abcd1234efgh5678
Using ARN for Resource Identification
ARNs play a crucial role in identifying resources within AWS. By using ARNs, AWS can accurately reference any resource in an account, across regions or partitions. For example, when managing IAM policies, creating access controls, or specifying resources in API requests, ARNs are the standard format used to uniquely identify resources. Using ARNs allows you to, You can specify an exact AWS resource, regardless of the region, account, or service, in API calls or configurations. ARNs provide a consistent method for linking services together, much like how What is AWS Console offers a unified interface for managing and interacting with various AWS resources and services. For instance, an IAM policy can specify which EC2 instances or S3 buckets a user or role is allowed to access by referencing their ARNs. Using ARNs in scripts or AWS CloudFormation templates helps automate infrastructure provisioning and management. ARNs enable fine-grained control over permissions, allowing you to restrict access to specific resources, such as an individual S3 bucket or EC2 instance, within IAM policies.
ARNs are used to enable cross-account access, allowing resources from different AWS accounts to interact with each other securely and seamlessly. ARNs are used to trigger actions or subscribe to events in services like SNS, CloudWatch, and Lambda, ensuring that the correct resource is acted upon when specific conditions are met.
Want to Obtain Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
ARN in IAM Policies
In IAM policies, ARNs allow administrators to specify exactly which resources a user, group, or role can access, ensuring that access is tightly controlled. For instance, you can use ARNs to specify which S3 buckets or EC2 instances a user is allowed to interact with. This level of granularity ensures that permissions are given only for the necessary resources, reducing the risk of unauthorized access. Additionally, ARNs can be used to manage actions on specific resource types, such as allowing only s3:PutObject or ec2:StartInstances on particular resources. Using ARNs in IAM policies ensures compliance with the principle of least privilege by allowing access to be restricted to specific resources and actions, improving both security and manageability, a key concept covered in AWS Training to help users implement secure and efficient access controls in AWS environments. For example, in an IAM policy, you can allow a user to access a specific S3 bucket by specifying the ARN of that bucket:
- {
- “Version”: “2012-10-17”,
- “Statement”: [
- {
- “Effect”: “Allow”,
- “Action”: “s3:ListBucket”,
- “Resource”: “arn:aws:s3:::my-bucket-name
- }
- ]
- }
This policy grants the user permission to list the contents of the specific S3 bucket my-bucket-name. Similarly, ARNs can be used to specify which EC2 instances, Lambda functions, or IAM roles a user or group can access. For example, you can use ARNs in IAM policies to grant specific permissions on EC2 instances, such as allowing a user to start, stop, or modify only a particular instance identified by its ARN. Similarly, ARNs can be used to control access to Lambda functions, enabling fine-grained permissions for invoking, updating, or managing a function based on its ARN. ARNs are also commonly used in IAM roles to define cross-account access, ensuring that only authorized users or services in other accounts can access specific resources. This granularity extends to other services like SQS, DynamoDB, and SNS, where ARNs help manage who can send messages, read data, or perform actions on resources. By using ARNs in policies, AWS administrators can ensure that resources are accessed in a controlled, precise, and secure manner.
Common Uses of ARN
ARNs are used across various AWS services for several purposes, including:
- IAM Policies: As shown above, ARNs are used to define resource-specific permissions in IAM policies, granting users or roles access to specific resources.
- Service Interactions: ARNs are used in API calls to interact with AWS services. For instance, when using the AWS CLI or SDKs, you specify ARNs to reference the resources you want to manage or operate on.
- AWS CloudFormation:In CloudFormation templates, ARNs are used to refer to resources that are created or managed by the template, such as IAM roles, S3 buckets, or EC2 instances.
- Event Subscriptions: For services like Amazon SNS, CloudWatch Events, and AWS Lambda, ARNs are used to subscribe to events or specify the resources that should trigger certain actions.
- Resource Sharing: In resource sharing scenarios, such as AWS RAM (Resource Access Manager), ARNs are used to define which resources are shared between accounts, organizations, or regions, similar to how What is Amazon Elastic Load Balancer helps distribute traffic across multiple resources for optimal performance and scalability in a cloud environment.
- Cross-Account Access: ARNs are crucial in granting permissions for cross-account access. By referencing ARNs in IAM roles or policies, administrators can allow users or services from other AWS accounts to access resources, such as S3 buckets or EC2 instances, in a controlled manner.
- Logging and Monitoring: ARNs are used in AWS services like CloudTrail and CloudWatch to track resource usage and activity. By specifying ARNs, you can monitor specific resources and log their interactions, making it easier to audit and troubleshoot specific actions related to your resources.
- Custom Resource Policies: Many AWS services, such as S3 and Lambda, allow you to create resource-based policies where ARNs are used to define who can access the resource. These policies can grant permissions to specific users, roles, or even other AWS services, enabling detailed access control based on the ARN of the resource.
Are You Considering Pursuing a AWS Master’s Degree? Enroll For AWS Masters Course Today!
Managing Permissions with ARN
ARNs allow for precise management of permissions in AWS. When creating policies for IAM users, roles, or groups, you can use ARNs to grant specific access to resources. ARNs allow you to restrict access to individual resources. For example, instead of granting broad access to all EC2 instances, you can grant permission only to a specific instance by referencing its ARN.By referencing ARNs in cross-account IAM roles, you can grant access to resources in other AWS accounts. This is essential for collaborative environments or when managing resources across multiple accounts, much like how An Overview of MuleSoft Anypoint helps integrate and manage multiple services across different systems in a unified platform. Many AWS services allow you to define resource-based access policies where you specify the ARN of the resource in the policy to control access. For example, in Amazon S3 bucket policies, you use ARNs to specify which users or accounts can access the bucket. Additionally, ARNs can be used to apply fine-grained access control for services like Lambda, where you can specify permissions for specific functions.
For instance, you can allow a role to invoke a particular Lambda function by referencing its ARN in the policy. ARNs also enable access control for services like AWS SQS (Simple Queue Service), where you can control which IAM roles or users have access to a specific queue by specifying the queue’s ARN. When managing permissions for Amazon SNS (Simple Notification Service), ARNs help in defining which topics or subscriptions can be accessed or modified by particular users or roles. Another use case of ARNs is in configuring access to DynamoDB tables. By referencing a table’s ARN in an IAM policy, you can precisely manage who has read, write, or delete access to specific DynamoDB tablesFinally, using ARNs ensures that access permissions are both specific and scalable, improving security by following the principle of least privilege across complex cloud environments.
Best Practices for Working with ARN
To make effective use of ARNs in your AWS environment, consider the following best practices:
- Use Specific ARNs in IAM Policies: Always use specific ARNs in IAM policies to grant the least privilege access. Avoid using wildcard characters (*) unless absolutely necessary, as they grant broad permissions that could be risky.
- Organize Resources with Clear Naming Conventions:To make it easier to manage ARNs, adopt a consistent naming convention for your resources. This will help you easily reference them in policies, scripts, and configurations.
- Use Tags and Metadata:Use resource tags and other metadata to help manage and group resources logically, similar to how An Overview of AWS SDK and Toolkit enables developers to manage and interact with AWS resources programmatically, streamlining application development and resource management.
- Avoid Hardcoding ARNs in Code:To improve maintainability and flexibility, avoid hardcoding ARNs directly in your code. Instead, use AWS SDKs to retrieve resource identifiers dynamically, or store ARNs in configuration files or environment variables.
- Monitor and Audit Access:Regularly monitor the usage of resources identified by ARNs. Use AWS CloudTrail and AWS Config to track who accessed what resources and when. This helps with compliance and auditing.
- Use ARNs with Service Integration:When integrating AWS services (like Lambda, CloudWatch, and SNS), always use the correct ARN format for the specific service to ensure that resource interactions are precise and secure.
Go Through These AWS Interview Questions & Answer to Excel in Your Upcoming Interview.
Conclusion
In conclusion, Amazon Resource Names (ARNs) are fundamental for managing and identifying AWS resources across various services. They provide a consistent and precise way to refer to resources in IAM policies, API calls, event subscriptions, and resource sharing scenarios. By understanding the structure and uses of ARNs, you can efficiently automate tasks, enforce granular access control, and integrate services across your AWS environment, which is a critical aspect taught in AWS Training to help professionals optimize and secure their cloud infrastructure. Following best practices such as using specific ARNs, organizing resources with clear naming conventions, and avoiding hardcoding ARNs in code will help maintain a secure and well-managed AWS infrastructure. Additionally, leveraging ARNs for monitoring and auditing access ensures that your environment remains compliant and secure. By mastering ARNs, you can better manage your AWS resources, streamline operations, and improve the overall efficiency of your cloud-based applications.





