
- Introduction
- What is an AWS NAT Gateway?
- NAT Gateway vs NAT Instance
- Setting Up a NAT Gateway in AWS
- Monitoring AWS NAT Gateway
- Scaling NAT Gateway in AWS
- Security Considerations for NAT Gateway
- Troubleshooting NAT Gateway Issues
- Conclusion
Introduction
In modern cloud architectures, the need for secure and reliable internet connectivity for private resources is essential. AWS offers a solution in the form of the Network Address Translation (NAT) Gateway, a fully managed service that allows instances in private subnets to access the internet while keeping them secure from inbound traffic. Whether you are operating in a simple application environment or a complex, multi-tiered architecture, understanding how to implement and manage a NAT Gateway is key to ensuring your resources can interact with external services securely and efficiently, which is a critical topic covered in Amazon Web Service Training to help professionals optimize their cloud infrastructure. This article explores the concept of AWS NAT Gateway, compares it with the NAT Instance alternative, outlines best practices for setup, monitoring, and security, and provides insights into troubleshooting common issues.
Want to Obtain Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
What is an AWS NAT Gateway?
A Network Address Translation (NAT) Gateway is a fully managed service provided by AWS that enables instances in a private subnet of a Virtual Private Cloud (VPC) to securely access the internet or other AWS services, while preventing inbound internet traffic from directly accessing those instances. Essentially, it allows for outbound internet access for resources in private subnets, such as instances in a web application, without exposing those instances directly to the public internet. This ensures that your sensitive resources in private subnets remain protected while still being able to interact with external services, similar to how A Complete Citrix Certification Path helps professionals master secure application delivery and virtualization solutions. The NAT Gateway simplifies network management by offloading the need for manual configuration and scaling, allowing you to focus on your applications instead.
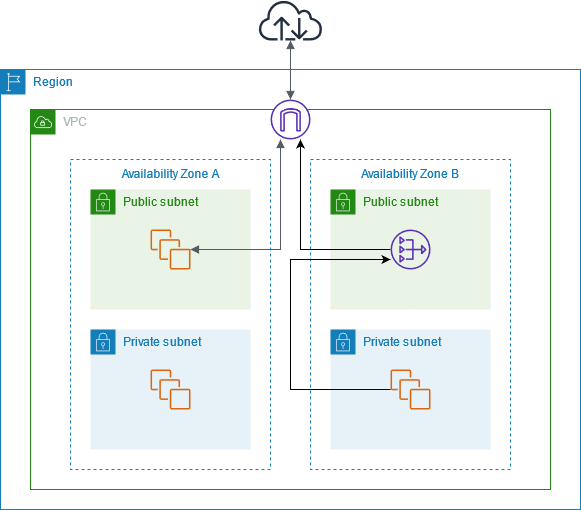
- Public IP Addressing: The NAT Gateway uses an Elastic IP (EIP) address, which allows it to act as the gateway for internet-bound traffic from private subnet instances.
- Highly Available: AWS manages the availability and scalability of the NAT Gateway across availability zones, offering high resilience.
NAT Gateways are typically used when applications in private subnets need to fetch updates, access external APIs, or download packages from the internet, while still maintaining security and privacy by not allowing direct inbound access to those instances.
NAT Gateway vs NAT Instance
Both NAT Gateway and NAT Instance provide internet access for private subnet resources, but there are important differences between them:
| Feature | NAT Gateway | NAT Instance |
|---|---|---|
| Management | Fully managed by AWS | Requires user management and maintenance |
| Performance | Scales automatically based on traffic | Requires manual scaling by resizing or adding instances |
| Cost | Generally more expensive due to managed service | Typically cheaper, as you pay for the EC2 instance running NAT |
| Scaling | Automatically scales with traffic | Manual scaling required based on load |
| Ease of Setup | Quick and easy to set up, no instance management | Requires more configuration and management |
| Customizability | Less customizable (designed for simplicity) | Highly customizable, as it’s based on EC2 instances |
In general, NAT Gateway is recommended for most production workloads due to its automatic scaling, high availability, and ease of management, while NAT Instance may still be appropriate for smaller or cost-sensitive environments where manual scaling is manageable, much like how What is Hybrid Cloud refers to combining on-premises infrastructure with cloud resources to optimize cost and scalability.
Are You Interested in Learning More About AWS? Sign Up For Our AWS Course Today!
Setting Up a NAT Gateway in AWS
To set up a NAT Gateway in AWS, follow these steps:
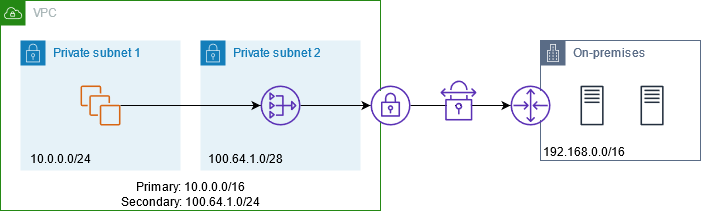
- Create a Public Subnet: Ensure that you have a public subnet in your VPC. This subnet will contain the NAT Gateway and be accessible from the internet.
- Allocate an Elastic IP (EIP): In the Elastic IP section of the AWS Management Console, allocate a new EIP. This IP address will be used by the NAT Gateway for internet communication.
- Create the NAT Gateway: Navigate to the VPC Dashboard in the AWS console. Under NAT Gateways, click on Create NAT Gateway, a process that can be tested and optimized through What is Chaos Engineering, ensuring the system remains resilient under unpredictable conditions. Select the public subnet where you want the NAT Gateway to reside. Associate the Elastic IP you allocated earlier. Optionally, enable the Auto-assign Public IP feature if you want the NAT Gateway to automatically acquire a public IP.
- Update Route Tables: Update the route table of your private subnets to route outbound internet traffic to the NAT Gateway. For this, go to Route Tables, select the route table for the private subnet, and add a route. Destination, 0.0.0.0/0 (for all IPv4 traffic). Target, Select your NAT Gateway.
- Test Connectivity: After setting up the NAT Gateway, launch an EC2 instance in the private subnet and verify that it can access the internet by pinging an external website or accessing updates.
Monitoring AWS NAT Gateway
AWS offers several tools to monitor the performance and health of your NAT Gateway. Amazon CloudWatch provides key metrics like Bytes In/Out, Packets In/Out, and Active Connections, allowing you to track the traffic volume and overall performance of the NAT Gateway. Additionally, you can set up CloudWatch Alarms to notify you if any of these metrics cross predefined thresholds, such as high data throughput or latency, a key concept taught in AWS Training to help users effectively monitor and manage AWS services. VPC Flow Logs enable you to capture detailed network traffic information, giving you insight into the traffic flowing through the NAT Gateway, which can help identify potential issues. Finally, AWS CloudTrail logs all API calls made to manage or configure the NAT Gateway, offering an audit trail for any changes or actions related to the service. These tools work together to provide comprehensive monitoring and troubleshooting capabilities for your NAT Gateway.
Are You Considering Pursuing a AWS Master’s Degree? Enroll For AWS Masters Course Today!
Scaling NAT Gateway in AWS
NAT Gateways automatically scale based on traffic, but there are still considerations for handling high volumes of traffic or workloads:
- High Throughput: The NAT Gateway is designed to scale automatically to handle increased traffic. AWS ensures that performance and capacity increase as needed without the need for manual intervention.
- Multi-AZ Deployment: To improve availability and resilience, it’s recommended to deploy NAT Gateways in multiple Availability Zones. If one NAT Gateway fails, the other can continue handling traffic.
- Performance Testing: Conduct regular performance tests to monitor the bandwidth, latency, and throughput of your NAT Gateway, similar to how Azure ExpressRoute provides dedicated, high-performance connectivity to Azure, ensuring optimal performance for cloud resources. If you have particularly high traffic workloads, consider using multiple NAT Gateways in different AZs for optimal performance.
- Failover: For critical applications requiring minimal downtime, ensure that you have a failover mechanism in place. You can implement automatic failover using Route 53 or by setting up a secondary NAT Gateway in another AZ.
- Check Route Table Configurations: Ensure that your private subnet’s route table is correctly configured to direct internet-bound traffic to the NAT Gateway. If there’s an issue with the route, your private instances won’t be able to access the internet.
- Verify Security Group and Network ACLs: Ensure that the security groups and network ACLs for your instances and subnets allow the correct types of traffic. Misconfigured rules can block access to the NAT Gateway.
- Monitor CloudWatch Metrics: Review CloudWatch metrics for the NAT Gateway. If metrics such as Bytes In/Out or Active Connections are unexpectedly high or low, this could indicate a performance issue or a misconfiguration.
- Check Elastic IP Association: If the NAT Gateway’s Elastic IP (EIP) is not correctly associated, or if there are network issues, the gateway may not function as expected, which is an important concept covered in AWS Training to help professionals troubleshoot and ensure proper configuration of AWS resources.
- Examine VPC Flow Logs: Review VPC Flow Logs for traffic logs related to the NAT Gateway. They can provide insights into why requests are failing or not reaching their destination.
Security Considerations for NAT Gateway
When using a NAT Gateway, it is important to follow security best practices to protect your resources. First, control access by using security groups for the resources connected to the NAT Gateway, such as EC2 instances. Ensure that your private instances’ security groups allow outbound traffic to the internet through the NAT Gateway. While NAT Gateways do not allow inbound traffic, you should still configure access control lists (ACLs) and security groups correctly to secure any instances that might be indirectly reachable, much like how A Definitive Guide for Azure Automation Benefits and Special Features emphasizes the importance of securing and automating cloud environments for better control and efficiency. Additionally, enable CloudWatch Logs and VPC Flow Logs to monitor traffic to and from the NAT Gateway, helping you identify unauthorized or unusual access patterns. Finally, ensure that any AWS services or EC2 instances accessing the internet via the NAT Gateway are assigned the appropriate IAM roles and policies, limiting unnecessary access and permissions to enhance security.
Preparing for a AWS Job Interview? Check Out Our Blog on AWS Interview Questions & Answer
Troubleshooting NAT Gateway Issues
If your NAT Gateway is experiencing issues, here are some troubleshooting steps to follow:
Conclusion
In conclusion, AWS NAT Gateway provides a robust and scalable solution for enabling secure internet access for instances in private subnets without exposing them to inbound traffic. Its fully managed nature, automatic scaling, and high availability make it a preferred choice for most production environments. While NAT Instances may be suitable for smaller or cost-sensitive use cases, the NAT Gateway offers simplicity, reliability, and seamless performance for larger, more demanding workloads. By properly setting up, monitoring, and securing your NAT Gateway, and understanding how to troubleshoot common issues, you can ensure optimal performance and security for your AWS infrastructure. Whether you’re just starting or managing a complex architecture, leveraging NAT Gateway can significantly enhance the efficiency and security of your cloud environment. As cloud infrastructures grow and evolve, understanding and effectively managing services like the NAT Gateway will be essential for maintaining a secure and high-performance network. With the right configuration and best practices in place, your AWS resources can interact with the internet safely and without interruption.





