
- Introduction to AWS STS
- How AWS STS Works
- Use Cases for AWS STS
- Configuring Temporary Security Credentials
- Managing Access with AWS STS
- AWS STS and Identity Federation
- Best Practices for AWS STS
- Conclusion
Introduction to AWS STS
AWS Security Token Service (STS) is a robust web service that allows users and applications to ask for temporary security credentials to use AWS resources. AWS STS provides short-lived, limited-privilege credentials rather than long-term credentials, which can be security threats. This makes it a critical tool for securing access in many situations, such as cross-account permissions, identity federation, and temporary application access. With AWS STS, companies can grant secure and elastic access to AWS services without endangering long-term credential exposure, a key topic covered in Amazon Web Service Training to help professionals understand best practices for secure access management in cloud environments. It is helpful in settings in which users and applications need temporary permission instead of permanent access.
Key Benefits of AWS STS:
- Enhanced Security: Eliminates the need for storing long-term credentials.
- Flexibility: Supports a range of authentication scenarios, including cross-account access and federated identities.
- Scalability: Easily manages temporary access for applications, services, and external users.
- Improved Access Control: Allows organizations to enforce fine-grained security permissions using temporary credentials.
- Seamless Integration: Works with IAM roles, identity federation, and AWS services for streamlined authentication.
To Earn Your AWS Certification, Gain Insights From Leading AWS Experts And Advance Your Career With ACTE’s AWS Course Today!
How AWS STS Works
AWS STS provides temporary security credentials through which AWS services can be accessed. Temporary credentials include an Access Key ID, a Secret Access Key, and a Session Token. They have an expiration date, after which they are revoked, thus reducing security risks. AWS STS ensures that users and applications have safe and secure ways of acquiring and utilizing credentials.
Steps in the AWS STS Workflow:
- Request Credentials: A user or application sends a request to AWS STS for temporary credentials, specifying the required permissions and duration.
- Verification: AWS STS validates the request against policies and permissions before issuing temporary credentials, similar to how What is Dell Boomi integrates and validates data flows between systems to ensure smooth and secure operations.
- Usage: The issued credentials interact with AWS services, such as accessing S3 buckets or launching EC2 instances.
- Expiration: The credentials expire after the configured duration, ensuring access is automatically revoked.
- Renewal or Re-request: If additional access is needed, a new request must be made to AWS STS.
- Cross-Account Access: Enables users or applications in one AWS account to access resources in another AWS account using IAM roles securely.
- Federated Identity Integration: Allows external identity providers, such as Active Directory, Google, or Facebook, to grant temporary AWS access.
- Temporary Access for Applications: Eliminates the need for hardcoded AWS credentials in applications by allowing temporary role assumption, much like how Docker Swarm Architecture manages containerized applications across a cluster without relying on static configurations.
- Secure Mobile and Web Applications: Works with Amazon Cognito to provide temporary credentials for mobile and web applications.
- Short-Term Access for Third-Party Services: Grants external contractors or partners time-bound access to specific AWS resources.
- On-Demand Permission Elevation: Enables temporary privilege escalation for certain administrative tasks while ensuring least privilege principles.
- Create IAM Roles: Define roles with specific policies granting permissions for necessary AWS resource access.
- Define a Trust Policy: Assign a trust policy specifying which entities can assume the role, which aligns with some of the Top AWS Statistics that highlight the importance of secure identity and access management in cloud environments.
- Request Temporary Credentials: Use the AssumeRole API call via AWS CLI or SDKs to obtain temporary credentials.
- Use Temporary Credentials: Pass the credentials in API requests to access AWS services.
- Manage Expiration: Set session duration (default 1 hour, configurable up to 12 hours) based on security requirements.
- Use IAM Roles: Assign precise permissions to IAM roles rather than granting full administrative privileges.
- Limit Session Duration: Set shorter session durations to minimize security risks.
- Monitor Credential Usage: Track access and usage with AWS CloudTrail and CloudWatch.
- Restrict API Access: Apply IAM policies to limit who can request temporary credentials.
- Use Resource-Based Policies: Attach access policies directly to AWS resources to control STS usage.
- SAML-Based Federation: Integrates with identity providers like Microsoft Active Directory Federation Services (AD FS) for single sign-on (SSO).
- Web Identity Federation: Allows authentication through social identity providers like Google, Facebook, and Amazon Cognito.
- Role Assumption: Users authenticate with external IDs and assume AWS IAM roles based on their permissions.
- Follow the Principle of Least Privilege: Grant only the minimum necessary permissions.
- Use Short-Term Credentials: Keep session durations short to reduce exposure risks.
- Rotate Temporary Credentials Frequently: Refresh credentials periodically to maintain security.
- Securely Store Credentials: Avoid exposing session tokens in logs or URLs.
- Monitor and Audit Usage: Use AWS CloudTrail and AWS Config to track credential usage and detect anomalies.
- Enable Multi-Factor Authentication (MFA): Require MFA for sensitive STS operations.
- Restrict Role Assumption: Limit the number of users and services who can assume specific roles in AWS STS.
Use Cases for AWS STS
AWS STS is used extensively when temporary AWS resource access is needed. It is beneficial in situations where security and flexibility are primary concerns. Organizations with scalable and secure access control need AWS STS to help with temporary credentials.
Common AWS STS Use Cases:
Want to Obtain Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
Configuring Temporary Security Credentials
Setting up AWS STS requires proper configuration of IAM roles and permissions. Organizations must define clear trust relationships, assign necessary permissions, and configure role assumption policies to ensure seamless and secure credential management. AWS STS can be configured to work with both AWS-native and external authentication mechanisms, such as Security Assertion Markup Language (SAML) and OpenID Connect (OIDC).
Steps to Configure AWS STS:
Managing Access with AWS STS
Properly managing access to AWS STS ensures that security credentials are only granted to authorized users and applications. Implementing IAM policies, monitoring usage, and setting expiration times are crucial for maintaining security. Organizations should regularly review access patterns and apply security best practices to minimize risks associated with temporary credentials. AWS provides tools such as AWS Identity and Access Management (IAM) and AWS Organizations to help control and audit access to STS credentials, which are crucial topics covered in AWS Training to ensure individuals understand how to effectively manage access and security in AWS environments. Businesses can define policies that limit which roles or services can assume temporary credentials, preventing unauthorized access.
Best Practices for Managing AWS STS Access:
Gain Your Master’s Certification in AWS by Enrolling in Our AWS Masters Course.
AWS STS and Identity Federation
Identity federation with AWS STS enables external identity providers (IdPs) users to access AWS resources securely. Instead of managing individual IAM users, organizations can use STS to authenticate users from corporate directories or social identity providers, similar to what is Azure DNS simplifies domain name management and ensures secure access across different platforms. This allows seamless integration with existing authentication frameworks while ensuring secure AWS resource access.
Types of Identity Federation in AWS STS:
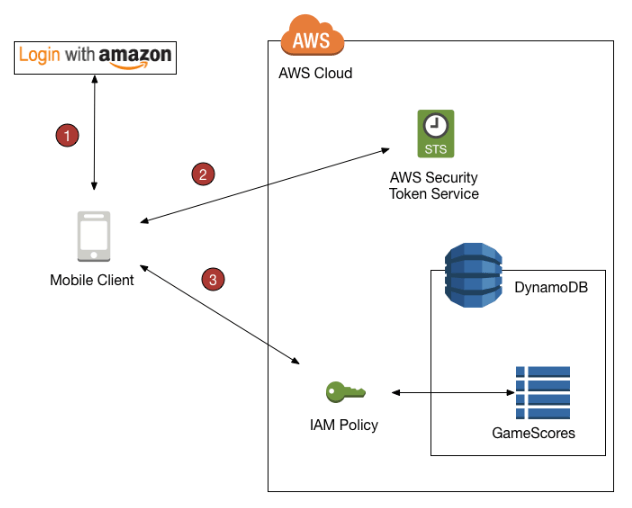
Best Practices for AWS STS
Organizations need to implement robust security controls to ensure the optimal security and effectiveness of AWS STS, similar to what is Azure Active Directory B2C provides secure authentication and access management for customer-facing applications. They can minimize the risks of temporary credentials by enforcing strong policies, auditing usage at all times, and restricting access where necessary.
Security Best Practices for AWS STS:
Want to Learn About AWS? Explore Our AWS Interview Questions & Answer Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
AWS Security Token Service (STS) supports secure, temporary access to AWS resources. It enhances security by issuing short-term credentials while enabling broad use cases like cross-account, federated identities, and temporary application access. By adhering to best practices such as least privilege access, credential usage monitoring, and MFA-friendliness, organizations can optimize the security and efficiency of AWS STS and deliver seamless access control across AWS environments, which is a key focus in AWS Training to ensure professionals are equipped with the knowledge to implement secure and efficient cloud solutions. With ever-growing AWS environments, having the capability to control temporary credentials dynamically using STS gives enterprises security and agility. Whether extending integration with third-party identity providers or maintaining temporary access for applications, AWS STS maintains security while supporting smooth cloud operation. Businesses utilizing AWS STS efficiently can reduce security risks, improve access controls, and enhance operational efficiency in cloud environments.





