
- What is internet of things security?
- Why IoT Security Matters
- IoT Security Threats
- IoT Security Types
- Top Techniques for IoT Security
- IoT Security’s Future
- Conclusion
Security is a significant issue with these thousands of devices, the IoT, connecting and communicating over the Internet. Smart appliances, wearable technology, industrial sensors, and other connected devices, such as those increasingly becoming a part of our everyday lives and operations, have a new sense of urgency to secure. Devices inherently carry sensitive data, thereby making them a target for cybercrooks. Such devices are often exploited to gain access, which develops into data breaches and huge attacks on the Cybersecurity Training Courses . A multi-layered security approach with device authentication, encryption of data, secure communication protocol, and periodic updates will ensure effective IoT security. It is further necessary to educate the users on risk potentiality and how safe practices can significantly mitigate such threats.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
What is the Internet of Things security?
IoT security is embedded within the plan and technologies designed to protect IoT devices and networks from cyber attacks. As more smart home devices, industrial sensors, and other artefacts move online, security for these devices must be ensured. Because Database Security can manage sensitive information and are often entry points for hackers, they are also considered unsafe. Effective IoT security strategies incorporate device authentication that limits the connection of only authorized devices, data encryption during transmission to protect the information, and robust network security by implementing firewalls and intrusion detection systems.
Executing timely updates and patches to safeguard against known vulnerabilities is important. Educating users to understand possible risks and best practices further helps maintain a secure IoT environment. With IoT security, people and organizations will avoid risks associated with this highly interconnected world and guarantee the security of the connected data and devices.
Why IoT Security Matters
The importance of IoT security cannot be underestimated because it poses several reasons. Usually, IoT devices have stored information, which may contain critical financial and personal data. Therefore, care needs to be taken to safeguard the same. This information falling into the wrong hands may result in loss of identity theft and other negative effects. Threat Intelligence are categorized as core infrastructure. These encompass all the power grids, transportation systems, and healthcare mechanisms. Unauthorized access to any of these will create severe repercussions a power failure, a transport halt, or even loss of life.IoT devices are normally connected to corporate networks; attackers use this avenue as an entry and exit point to the corporations’ systems. This may lead to sensitive information breaches, intellectual property loss, and many other circumstances.
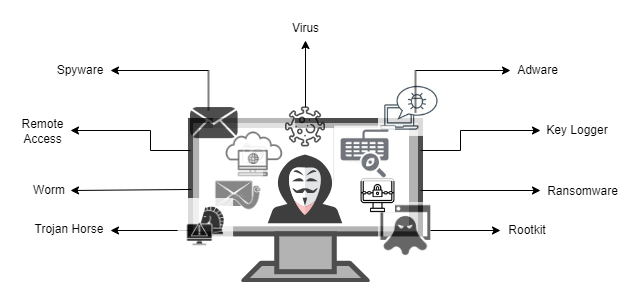
IoT Security Threats
- Botnets:Botnets are networks of compromised devices that cybercriminals can use to carry out Distributed Denial of Service (DDoS) attacks, data theft, and other malicious activities. This is mainly because the number of IoT devices seems to have increased, and they are secured with inadequate measures.
- Malware: Malware is an application designed to attack and damage computers and other devices, making them go out of function or even steal data. A Malware Attack on IoT devices is quite common due to its vulnerability to malware attacks.
- Physical Interventions:This method involves physically accessing an IoT device so that unauthorized access can be attained to the device and network. This could be done by breaking or intercepting signals between the device and the network.
- Weak Passwords:Since many IoT devices utilize standard login credentials that are simple to figure out or crack, weak passwords pose a common security risk to the IoT. As a result, attackers can easily access IoT networks and devices.
- Network Security:To reduce corporate attack surfaces, IoT network security employs a zero-trust approach. Users must safeguard their devices against unwanted access and possible exploitation.
- Embedded:Nano agents provide Internet of Things devices with on-device security. To detect and stop zero-day attacks, runtime protection monitors their condition and reacts when anomalies are found.
- Firmware Assessment:The first step in firmware security is to thoroughly analyze the firmware to identify potential vulnerabilities in an IoT device’s code.
- Device identification and access control are two crucial components in ensuring the security of the IoT. Only authorized devices can access the network thanks to device authentication, which verifies the identification of IoT devices. The degree of privileges that are given to specific devices or people is then controlled by access control. IoT devices should be set up to use strong authentication techniques, like digital certificates and two-factor authentication, or biometric authentication, to confirm the identity of users and devices to improve security.
- Encryption is a crucial component of IoT security, ensuring the privacy and security of data exchanged between IoT devices and Network Topology. The procedure for creating ciphertext from plain text involves using an algorithm for encryption and an encryption key. Only those who are The plain text data can be viewed by those who are allowed and have the key to decrypt the ciphertext.
- Regular updates are essential for IoT networks and devices to remain reliable and secure. To address known vulnerabilities and problems, it’s critical to routinely install the latest firmware, software, and security fixes on IoT devices. Extensive verification and testing should be carried out before deploying updates to avoid IoT security threats or any detrimental effects on device performance.
- Network segmentation, a crucial security measure, involves breaking a network up into distinct subnetworks or segments to prevent threats from spreading and lessen the effect of security breaches. Organizations can use network segmentation to group related IoT devices and implement security policies according to each segment’s criticality and risk level.
- 5G networks
5G networks are crucial to the security of the IoT in the future. Thanks to these networks’ increased capacity and lower latency, many IoT devices and apps can be deployed. However, new security issues posed by 5G networks include increased Network Penetration Testing complexity and the possibility of new attack paths.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
- Artificial intelligence (AI)
It are anticipated that modern technologies like artificial intelligence (AI) and machine learning (ML) will significantly contribute to IoT security in the future. These cutting-edge instruments can quickly detect and neutralize cyber threats, guaranteeing timely action to stop serious damage.
- Blockchain Technology
Blockchain technology can enhance IoT device security and privacy. It makes it possible to store data in a decentralized, extremely secure way, making it more difficult for cybercriminals to obtain illegal access to private data.
- The Quantum Computer
The fast-evolving science of quantum computing has the potential to upend several encryption techniques used to secure IoT devices. Investigating new encryption techniques will be essential as quantum computing’s capabilities develop.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
IoT Security Types
Both device manufacturers and consumers can deploy IoT security solutions in Cybersecurity Training Courses . IoT security comes in three different forms:
Top Techniques for IoT Security
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
IoT Security’s Future
Conclusion
IoT security is indispensable to secure the number of devices connected with our individual and professional lives. Since the growth in IoT-related devices mostly relates to collecting, transmitting, and storing large volumes of sensitive information, the associated threats through cyber risks increase. Cybersecurity Training will protect unauthorized access to confidential information and data breaches by proper security measures like authenticating devices, encrypting data, securing networks, and educating users. In addition, continuous monitoring and regular updates are crucial in dealing with vulnerabilities as they surface. As the Internet of Things landscape continues evolving, awareness of emerging threats and best practices will ensure people and organizations are headed in the proper direction to create a secure environment.





