
- Introduction
- What is Phishing?
- Types of Phishing Attacks
- How Phishing Attacks Works?
- Signs of a Phishing Attack
- Consequences of Falling for a Phishing Attack
- How to Protect Yourself from Phishing?
- Conclusion
A phishing attack is a type of cybercrime where attackers use deceptive tactics, often through email, text messages, or fake websites, to trick individuals into revealing sensitive information such as login credentials, credit card details, or personal identification numbers. These attacks typically impersonate trusted entities, such as banks or well-known brands, and create a sense of urgency or fear to manipulate victims into taking actions, like clicking on malicious links or downloading infected attachments. Enrolling in Cyber Security Training Courses can help individuals recognize these tactics and better protect themselves from falling victim to such attacks. The ultimate goal of phishing is to steal valuable data, often leading to financial loss, identity theft, or malware infections.
Interested in Obtaining Your Phishing Attack Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Introduction
Cybersecurity threats are becoming more complex in the digital world. Phishing has become one of the most common and dangerous tactics of cybercrime. Phishing attacks trick people into giving out sensitive information to hackers, such as login credentials, credit card details, or personal data. Ethical Hackers play a vital role in identifying and mitigating such threats by simulating phishing attacks to help organizations strengthen their security defenses. These attacks can lead to identity theft, financial loss, and unauthorized access to critical systems. In this blog, we will discuss what phishing attacks are, how they work, different types of phishing, and how to protect yourself from falling victim to such malicious schemes.
What is Phishing?
The term phishing involves a cyberattack where a malicious actor pretends to be a trustworthy entity, usually via electronic mail or another form of digital communication, to deceive the recipient into providing sensitive information. The attacker usually tries to trick the victim into clicking on a fake link or downloading an infected attachment, which leads to malicious websites or installs malware on the device. Google Dorking is often used by attackers to find vulnerabilities in websites, making it easier for them to craft targeted phishing attacks or exploit weaknesses in the victim’s security. The term “phishing” is a wordplay, which comes from the concept of using bait or fake communication to “fish” for personal information. It is one of the oldest forms of online fraud but continues to evolve with technological advancement and is still widely used in cybercrime.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
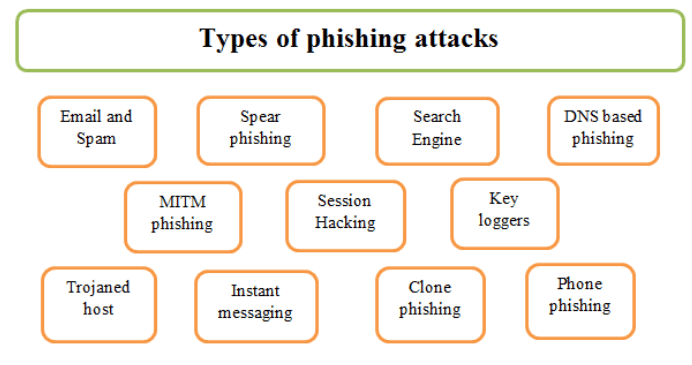
Types of Phishing Attacks
Not all phishing is the same in form. There are many different types of phishing attacks, and each one has its practices and target. Three of the most common types include:
- Email Phishing: Email phishing is the most widely known form of phishing, where attackers send deceptive emails that appear to come from a reputable source, such as a bank, online retailer, or social media platform. These emails often contain a sense of urgency, urging the recipient to click on a link or open an attachment. The objective is to dupe the recipient into inputting personal information, such as usernames, passwords, or financial information, on a phishing website, or infecting their computer with malware via a malicious attachment.
- Spear Phishing: Unlike general email phishing, spear phishing is highly targeted. In this form of attack, the attacker focuses upon a particular individual or organization, often using personalized information, such as their name, position, or company, to better make the message appear credible. Spear phishing is typically more difficult to detect because it is tailored to the victim’s circumstances. It may involve fake emails from colleagues, executives, or trusted contacts, and can have serious consequences for businesses or high-profile individuals.
- Whaling: Whaling refers to spear phishing directed at high-profile individuals, including corporate executives, government officials, celebrities, etc. A whaling attack is conducted to take advantage of the power position by pretending to be a trusted source or organization. The attacker may also use the Internet Protocol Address to spoof legitimate communication channels, making it harder for the victim to distinguish the attack from a genuine message. Whaling attacks are usually highly sophisticated and composed to look like actual requests for a normal process which could include, for example, tax payment notices, legal notices, or business propositions.
- Vishing: Vishing (voice phishing) involves using phone calls or voice messages to impersonate legitimate institutions like banks or government agencies. Attackers might pose as a customer service representative or a government official and ask the victim to provide confidential information, such as credit card numbers or Social Security numbers. Vishing attacks come through normal voice calls, or even through VoIP (Voice over Internet Protocol) services and are often set up to make people believe there is a sense of urgency in divulging sensitive data.
- Smishing: Smishing is another variant of phishing that involves text messages SMS rather than an email or call. Fraudulent text messages from attackers will tell recipients to click on a link or give out some personal information. Smishing messages normally appear to come from legitimate organizations, such as banks, retailers, or government bodies, and more often than not ask the victim to take immediate action that will prevent an adverse consequence such as freezing a bank account or losing access to a service.
- Angler Phishing: Social media users are the target for Angler phishing. The attacker develops a phony customer care page on social media such as Facebook or Twitter so that they would appear like real companies. A user can send complaints or even questions posted by the said real company, which may respond in the form of a private message or an actual reply providing fictitious customer support. This malware aims to manipulate users into disclosing personal information, clicking on spam links, or even downloading the malware as some form of a software update.
- The email or message may seem to come from a familiar source, but the sender’s email address or phone number may look unusual or misspelled. Urgent or threatening language:
- Phishing messages often create a sense of urgency, such as claiming that your account will be locked or that immediate action is required.
- Phishing emails or messages may contain links that, when hovered over, show a different URL than expected. Always check the destination URL before clicking. Generic greetings:
- Phishing emails often use generic greetings like “Dear Customer” instead of your actual name. Requests for personal information:
- Legitimate companies rarely ask for sensitive information via email or text message. Be cautious if asked to provide passwords, credit card details, or Social Security numbers.
- Be wary of unsolicited emails: Do not click on links or open attachments from unknown sources. If you must interact with suspicious content, always use a Sandbox Environment to isolate and analyze the files safely, preventing any potential harm to your main system.
- Verify the sender: If you receive a suspicious message, verify its legitimacy by contacting the organization directly (not through the contact details provided in the email).
- Use email filters: Enable spam filters to catch phishing emails before they reach your inbox.
- Install antivirus software: Keep your devices protected with updated antivirus software that can detect and block malicious links and attachments.
- Enable two-factor authentication (2FA): Add an extra layer of security to your accounts by enabling 2FA, making it harder for attackers to gain unauthorized access.
- Educate yourself and others: Awareness is key. Learn to recognize phishing attempts and educate others to avoid falling for these attacks.
How Phishing Attacks Works?
Phishing attacks operate through manipulating human psychology rather than exploiting technical weaknesses. The general pattern followed by an attacker typically includes three stages Impersonation, Deception, and Exploitation. First, the attacker designs a message or web page that mimics a trusted source, such as a bank, e-commerce platform, or government website, creating a sense of credibility. Then, through social engineering techniques, the attacker deceives the victim into taking a specific action, like clicking a malicious link, downloading an attachment, or disclosing sensitive information. To prevent such attacks, it is crucial to invest in Cyber Security Training Courses that educate individuals on recognizing and avoiding common phishing tactics and other social engineering methods. Once the victim follows the instructions, the attacker gains unauthorized access, steals personal information, infects the device with malware, or compromises accounts or systems. Phishing attacks often trigger feelings of urgency or panic, exploiting the victim’s emotional response, which leads them to act impulsively without fully thinking through the consequences. Attackers may use fear tactics, claiming urgent issues like account suspension or unpaid bills to pressure victims into immediate action. Additionally, phishing attacks can be highly sophisticated, using personalized details to further gain the victim’s trust and increase the likelihood of success. Victims are often unaware of how easily their personal data can be exploited, especially when the attacker mimics familiar and trusted organizations. As a result, constant vigilance and awareness are essential in defending against these types of attacks.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Signs of a Phishing Attack
Signs of phishing attacks are pretty tough to discover but have the following common traits:
- Suspicious sender address:
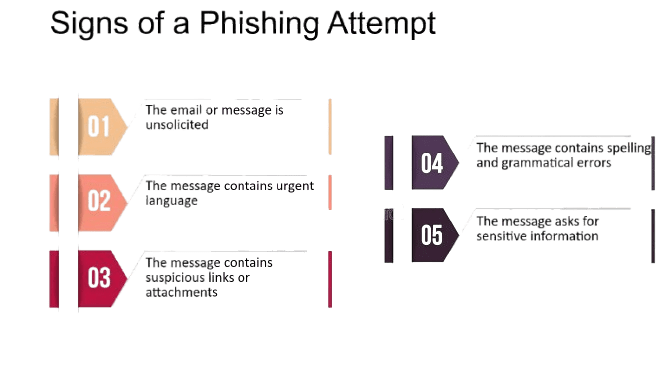
-
Suspicious links:
Consequences of Falling for a Phishing Attack
Falling for a phishing attack can lead to severe consequences, such as identity theft, where attackers steal personal information like Social Security numbers, credit card details, and login credentials. Cybercriminals can also use this stolen information to carry out fraudulent transactions, resulting in financial loss. For businesses, phishing can cause data breaches, exposing sensitive customer or business information. Additionally, clicking on malicious links or downloading infected attachments can introduce malware, including ransomware or keyloggers, onto your device. Attackers may also use Command Prompt Commands to further exploit system vulnerabilities, giving them unauthorized access or control over the compromised device. In the case of businesses, falling victim to phishing attacks can damage trust and reputation, leading to a loss of customers and diminished brand value. Moreover, the recovery process after a phishing attack can be time-consuming and expensive, especially when restoring compromised systems or securing stolen data. The victim may also face legal consequences, particularly if customer information is involved and the breach violates privacy regulations. For individuals, the long-term impact may involve spending months or years trying to resolve fraudulent charges and repairing credit scores. Phishing attacks may even lead to personal distress and anxiety, as victims struggle to regain control of their financial or online accounts. In some cases, attackers may use stolen information to commit further attacks, such as spear phishing or social engineering, exacerbating the damage. Additionally, the cost of reputational damage for both individuals and organizations can be irreversible, as regaining trust can be incredibly challenging after such a breach. Furthermore, stolen login credentials may allow attackers to access a wide range of personal and work-related systems, compounding the impact and complicating the recovery process.
How to Protect Yourself from Phishing?
Here are some steps you can take to help you protect yourself from phishing attacks:
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions and Answers
Conclusion
Phishing attacks typically come in the form of fraudulent emails, text messages, or websites that appear to be from trusted sources, such as banks, retailers, or even government agencies. These communications often contain urgent or alarming messages, such as warnings about account suspensions or promotional offers, designed to provoke immediate action. Victims are encouraged to click on links or open attachments that can either steal personal information or infect their devices with malware, highlighting the importance of Cyber Security Training Courses to help individuals recognize and protect themselves from such threats. Sophisticated phishing scams may even mimic legitimate email addresses and website designs, making it harder to distinguish between what is real and what is malicious. To avoid falling victim to phishing, always be cautious when receiving unsolicited messages or emails, especially those that ask for personal or financial information. Look out for signs such as spelling errors, unfamiliar sender addresses, or strange formatting in emails. When in doubt, contact the company or organization directly using verified contact methods rather than responding to the suspicious message.





