
- Definition and Overview of Cryptanalysis
- Historical Background and Evolution of Cryptanalysis
- Statistical Cryptanalysis
- Types of Cryptanalysis Techniques
- Known-Plaintext and Chosen-Plaintext Attacks
- Tools and Software for Cryptanalysis
- Conclusion
Definition and Overview of Cryptanalysis
Cryptanalysis is the science and practice of analyzing and breaking cryptographic systems. It involves studying ciphers and cryptographic protocols to identify weaknesses and vulnerabilities and decrypt encrypted information without needing a secret key. Cryptanalysis is critical for ensuring the security of encryption systems and helps strengthen cryptographic algorithms by identifying and addressing flaws in Cybersecurity Training Courses .While cryptography focuses on creating and implementing secure encryption techniques, cryptanalysis focuses on breaking these encryption schemes. The field has evolved with advancements in computing power, mathematical theories, and algorithms, becoming vital in securing and breaking encrypted data.
Historical Background and Evolution of Cryptanalysis
Cryptanalysis has a long history, dating back to ancient times when the first ciphers were created. Some of the most notable milestones in the evolution of cryptanalysis include:
- Ancient Cryptanalysis: In ancient times, simple substitution ciphers, like the Caesar cipher, were used for encrypting messages. These ciphers were easily broken using basic methods, such as frequency analysis. Frequency analysis, the study of letter or symbol frequencies in a ciphertext, was one of the first cryptanalytic techniques used in ancient cryptography. It was first formally recorded by Al-Kindi, a 9th-century Arab scholar.
- The Renaissance Period: During the Renaissance, cryptography became more advanced with the introduction of polyalphabetic Playfair Cipher, such as the Vigenère cipher. These ciphers were more resistant to frequency analysis but could still be broken using other methods, such as the Kasiski examination. The development of formal mathematical principles in cryptanalysis during this period paved the way for the modern field.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
- World War II and the Enigma: One of the most famous events in cryptanalysis history occurred during World War II with the breaking of the German Enigma cipher. British cryptanalysts, led by Alan Turing, developed techniques to decrypt Enigma-encrypted messages, significantly aiding the Allied war effort. The work of Turing and others led to the development of early computers, which would later revolutionize cryptanalysis.
- Modern Cryptanalysis: With the advent of computers and more sophisticated algorithms in the late 20th century, cryptanalysis evolved from manual methods to computational techniques. The rise of public-key cryptography introduced new challenges for cryptanalysts, with algorithms such as RSA requiring more complex mathematical methods to break. Advances in number theory, computer science, and algorithm design have allowed cryptanalysts to tackle more challenging encryption systems, but new encryption methods, such as quantum Encryption in Network Security also present future challenges.
Statistical Cryptanalysis
Statistical cryptanalysis involves studying patterns and statistical properties in ciphertexts to exploit weaknesses in encryption algorithms. Cryptanalysts can deduce key bits or plaintext data by analyzing how frequently particular symbols or groups of symbols appear in the ciphertext. This approach is particularly effective against classical ciphers like Caesar cipher or Vigenère cipher, which do not have strong diffusion properties. For modern ciphers, statistical attacks typically focus on exploiting weaknesses in how randomness is generated or how the encryption algorithm operates. Statistical cryptanalysis can also be applied to stream ciphers, which rely on pseudorandom number generators. Any predictable patterns in these generators can be exploited to decrypt the ciphertext.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
Types of Cryptanalysis Techniques
Cryptanalysis encompasses various techniques based on the type of cipher being attacked. Some of the most common types of cryptanalysis include:
- Brute Force Attack: A brute force attack is the most straightforward cryptanalytic technique, testing every possible key until the correct one is found. This method is computationally expensive and infeasible for ciphers with long keys (e.g., AES-256), but it can be effective against weak or poorly implemented encryption systems.
- Frequency Analysis: This technique is used primarily for breaking substitution ciphers, such as the Caesar cipher. By analyzing the frequency of letters or symbols in the ciphertext and comparing it to known letter frequencies in the plaintext language, cryptanalysts can make educated guesses about the mapping between plaintext and ciphertext characters.
- Known-Plaintext Attack: In a known plaintext attack, the Dictionary Attack has access to both the ciphertext and a portion of the plaintext. The goal is to use this information to determine the key or to gain insight into the structure of the cipher. This attack is effective against many ciphers, particularly if the plaintext contains common or predictable words or phrases.
- Chosen-Plaintext Attack: In a chosen plaintext attack, the attacker can choose a particular plaintext message and encrypt it using the cipher. By analyzing the resulting ciphertext, the attacker may be able to deduce the key or other useful information about the encryption algorithm. This type of attack is particularly effective against certain block ciphers.
- Ciphertext-Only Attack: A ciphertext-only attack occurs when the attacker only has access to the ciphertext and no information about the plaintext. This is the most common form of attack in real-world scenarios, and modern encryption algorithms are designed to be resistant to such attacks. However, weaknesses in the cipher or algorithm implementation can still be exploited.
- Side-Channel Attacks: Side-channel attacks exploit physical information leakage, such as timing information, power consumption, or electromagnetic radiation, to deduce information about the secret key or encryption process. These attacks are especially relevant in hardware implementations of cryptography.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Ciphertext-Only Cryptanalysis
Ciphertext-only cryptanalysis refers to situations where the attacker only has access to the ciphertext without any corresponding plaintext or known-plaintext data. The attacker must rely solely on the properties of the ciphertext to recover the secret key or plaintext message.
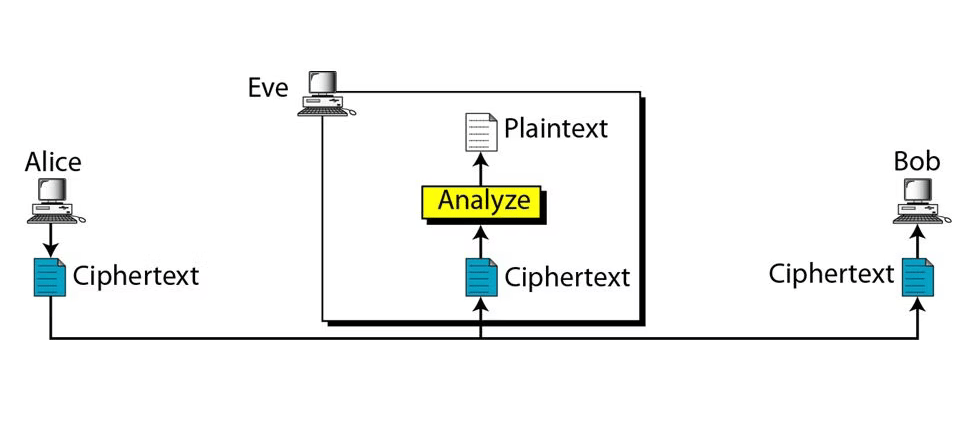
Modern Private Key and Public Key Cryptography systems, such as AES, are designed to resist ciphertext-only attacks by making the relationship between the ciphertext and the plaintext as complex and non-linear as possible. However, weaknesses in the implementation or design of the cipher can still make ciphertext-only cryptanalysis feasible.
Known-Plaintext and Chosen-Plaintext Attacks
Known-Plaintext Attack (KPA) has access to both the ciphertext and its corresponding plaintext data. The attacker uses the known plaintext data to derive the encryption key or to find patterns in the encryption scheme that can be exploited. For example, if a common phrase like “Hello World” is encrypted, the attacker can guess the corresponding ciphertext, which helps determine in Cybersecurity Training Courses the encryption key.
Chosen-Plaintext Attack (CPA) can choose specific plaintext data messages and obtain their corresponding ciphertexts. This attack allows the cryptanalyst to gather information about the encryption algorithm by observing how different inputs of plaintext data are transformed into ciphertext. In many cases, CPAs can be used to derive the encryption key, especially if the encryption method is weak or the system has poor key management.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Tools and Software for Cryptanalysis
Various tools and software are available for cryptanalysis, ranging from open-source libraries to specialized commercial software. Some of the most commonly used cryptanalysis tools include:
- John the Ripper: John the Ripper is one of the most popular password-cracking tools. It performs dictionary attacks, brute force attacks, and other forms of cryptanalysis on password hashes.
- Cain and Abel: Cain and Abel is a widely used password recovery tool that can perform a variety of cryptanalysis techniques, such as dictionary attacks, brute force attacks, and cryptanalysis of encrypted network traffic.
- Hashcat: Hashcat is a powerful password recovery Container Security Tools designed for high-performance cracking of password hashes. It supports GPU-accelerated cracking and is widely used for cryptanalysis of hashed data.
- Wireshark: Wireshark is a network protocol analyzer that can capture and inspect packets in real time. It can be used for cryptanalysis of network traffic, including encrypted communications, to discover weaknesses in the encryption protocol.
- Cryptool: Cryptool is an open-source cryptanalysis software that allows users to visualize and experiment with cryptographic algorithms and attacks. It provides a variety of cryptanalytic features for educational and research purposes.
- GPG (GNU Privacy Guard): GPG is an open-source implementation of the OpenPGP standard that can encrypt and decrypt messages and files. It is also used to perform cryptanalysis of certain encryption systems.
Cryptanalysis remains a critical field of study in cybersecurity, as it helps ensure that cryptographic systems are secure and reliable. By continuously analyzing encryption schemes, cryptanalysts contribute to developing stronger, more robust encryption algorithms. The use of cryptanalysis software has become more prevalent as these tools continue to advance, offering more sophisticated techniques to break down complex encryption systems. Cryptanalysis software plays a key role in the ongoing development of robust encryption systems and is vital in testing the strength of encryption methods.
Conclusion
Cryptanalysis plays a crucial role in the field of cybersecurity, helping to identify and mitigate vulnerabilities in cryptographic systems and cryptographic protocols. From its early beginnings with simple ciphers to the advanced techniques used today, the field has evolved significantly, driven by advancements in mathematics, computing power, and algorithmic design. Through various cryptanalytic methods such as brute force attacks, statistical cryptanalysis in Cybersecurity Training , and known-plaintext or chosen-plaintext attacks, cryptanalysts are able to test the robustness of encryption systems and cryptographic protocols to ensure their effectiveness in protecting sensitive information.





