
- Introduction
- What is a Watering Hole Attack?
- How Watering Hole Attacks Work
- Common Techniques Used in Watering Hole Attacks
- Real-World Examples of Watering Hole Attacks
- Why Watering Hole Attacks Are Effective
- How to Defend Against Watering Hole Attacks
- Conclusion
This continuously evolving world of cyber security tools is one where attackers are always improving on techniques they use to look for vulnerabilities against individuals and organizations. The attack technique is more complex and often used, called the watering hole attack. Similarly, in a watering hole attack, cyber news wait for their targets to visit a specific website that they know the victims are likely to frequent. Once the victim visits the compromised website, the attackers deploy malicious Payloads malicious software or code designed to exploit vulnerabilities in the victim’s device or network. Likewise, a waterhole attack compromises websites that persons under attack will likely visit and infects those sites with malicious code to exploit a known vulnerability. We will cover what a watering hole attack is, how such attacks function, common techniques that attackers use to perform such crimes, and, most importantly, how organizations and individuals can protect themselves from becoming victims.
To Earn Your Watering Hole Attack Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction
Cyber security attacks are evolving in nature, and the organizations of today need to remain vigilant for new, sophisticated methods of attacks. One such threat is the Cyber Security Training Courses. A very clever and effective tool is used by cyber security threats against their selected targets with such an attack. The attacks are usually highly targeted, so the culprits will mostly choose a set of websites through which they may deliver malicious payloads to unsuspecting victims.
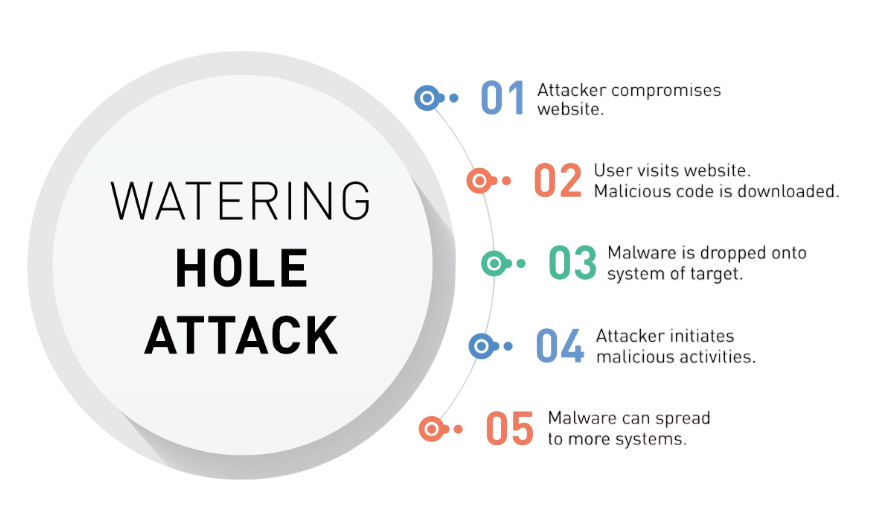
Therefore, individuals and organizations must understand how these attacks occur, why they succeed in the first place, and how to prevent them. That is the intent of this blog: to offer a detailed examination of watering hole attacks, from mechanics to techniques, real-world examples, and, most importantly, how to mitigate risks associated with these attacks.
What is a Watering Hole Attack?
- A watering hole attack is a form of cyberattack in which an attacker targets a specific group of people by compromising a website or service they often use. The common attack involves infecting a website or web service with malware or exploits targeting holes in the site’s infrastructure.
- The infecting agent attempts to reach the victim’s device when they visit the compromised site, usually unaware of the attack. Once the victim lands on the site, the attacker deploys malicious code, which can include a variety of payloads, such as a Keylogger. A “watering hole” attack is a term borrowed from the natural world. The principle behind it is predators waiting by watering holes for unsuspecting prey to come drinking. Similarly, attackers “lie in wait” for their victim to come to a site they trust when delivering malware that is often not easily detectable.
- The attacker identifies a group of people or organizations as a target. This is based on industry, job roles, or other characteristics that define the group’s interests and browsing habits. The attacker then compromises a website the target group makes regular visits to. This could be any website that could hack a blog, a news site, or another online resource the group uses regularly.
- This malware is then transferred to the victim’s machine when he browses the infected website through the already hacked website. It can appear in the form of exploits, drive-by downloads, or social engineering attacks. After the malware is deployed, it is used for data theft, creating a backdoor to continue further attacks or malicious actions.
How Watering Hole Attacks Work
Identifying the Target Group
First, cyber threats determine a target group or individuals. At times, cyber threats focus on a specific industry finance, healthcare, or even government but targeting some particular organization is also valid. Attackers find out information about the sites being visited by their target group: news sites about industry and professional life, social networking sites, blogs, or special forums. Once the hacker identifies the website being visited the most, they proceed.
Leaning on hacking
The hacker is now focused on exploiting the targeted website’s security weaknesses. Hacking the website through SQL injection along with other code injection attacks. Social engineering is a hacking trick in which the attacker fools the website administrator into installing malware. Once the hacker has access to the website, he or she can inject malicious code or add infected files that will be executed once visitors get to the site.
Malware Delivery
Once a user visits a corrupted website, the browser or the device is silently infected with malware. Malicious code may target certain vulnerabilities in the victim’s browser or plugins like Flash and Java. An ostensibly benign website can automatically bring in malware without the user’s consent. Malvertising is also a form of attack in which cybercrooks inject harmful ads into otherwise legitimate websites. At this stage, the infected victim is still unaware of being infected. The malware could then execute various actions, including stealing sensitive information, installing backdoors, or allowing the attacker to execute commands remotely.
To Explore Watering Hole Attack in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Common Techniques Used in Watering Hole Attacks
Attackers exploit zero-day vulnerabilities: zero-day vulnerabilities are unidentified flaws in the software, unknown to the software vendor and the public. They are precious for cyber threats since they are not yet patched and are an absolute entry point for an attack. When identified on a frequently visited site, the attackers can abuse the entry point to deliver malware to visitors. A drive-by download is any malware downloading and installing itself on a visitor’s device without their knowledge, something a website does automatically. When the victim accesses the website, the attackers have seeded malicious code in its scripts and start immediately running it.
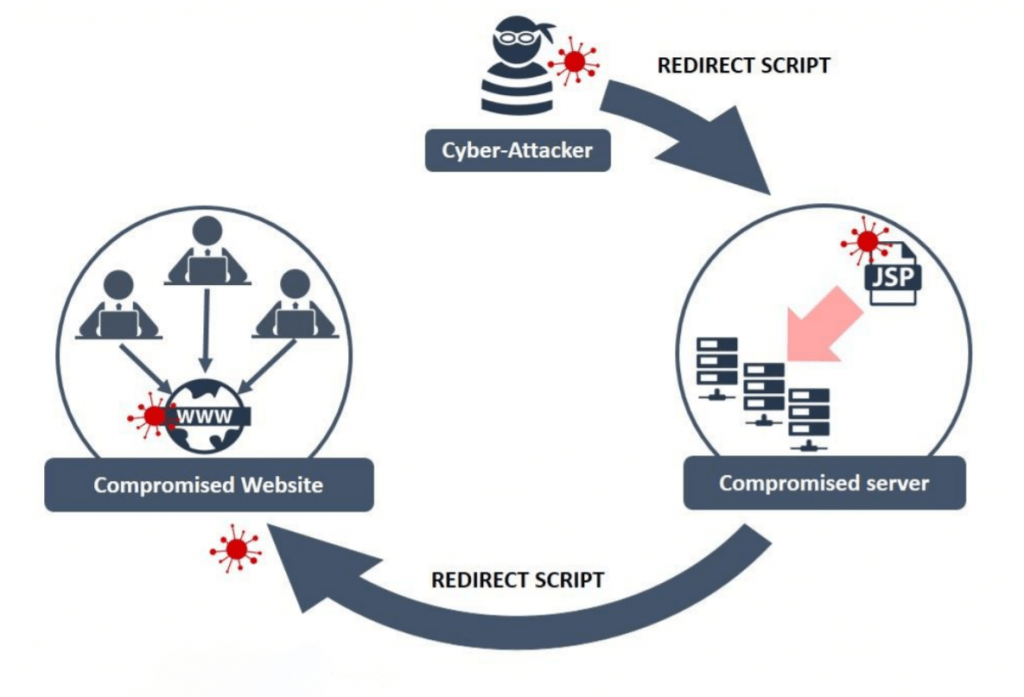
Then follows social engineering tactics. Some of the social engineering techniques upon which the Cyber Security Training Courses depend target at both website administrators and users. For example, attackers may make the website administrator download malware masquerading as an update or content, compromising the site. An attack via watering holes is sometimes called a long-term or high-level Advanced Persistent Threat. Such attacks involve coordinated efforts to infiltrate an organization’s network. An attack on a watering hole can be one of several components of a campaign associated with APT that serves to steal sensitive data or gain unauthorized access to a corporate network for an extended period.
Real-World Examples of Watering Hole Attacks
- Waterhole attacks are no theory. They have already been implemented successfully in several high-profile cases. Google and the Operation Aurora Attack 2009. This year, an attack on Google and other technology companies was recorded as Operation Aurora.
- The hackers penetrated the websites that employees of these companies frequently visited. Using this opportunity, they sent sophisticated malware covertly into the victim systems. Their main intention behind these attacks was to steal intellectual property and access sensitive information, including Gmail accounts operated by Chinese dissidents.
- In 2013, hackers took over a website that State Department employees frequently visited, breaching the State Department. To mitigate the damage from such attacks, many organizations implement a Sandbox Environment, where suspicious files or programs are isolated and run in a controlled, virtual environment. The site contained harmful codes that infected the visitors’ computers, thereby giving the attackers access to some sensitive information owned by the government.
- 2015 saw an attack on Kaspersky Lab, a major international enterprise in the cybersecurity sphere, conducted through a so-called watering hole attack. The attackers had gained access to websites that released malware to which the employees of Kaspersky regularly got access. Such malware granted hackers further access to internal systems.
- This is one reason why this kind of attack is often used as an example of how even firms engaged in the provision of cyber threats fall prey. Organizations whose core missions are data and network protection can fall victim to sophisticated tactics such as watering hole attacks.
- Cyber threats target these firms specifically because they hold valuable information, both proprietary technology and client data. Such breaches would compromise a firm’s security and turn its reputation into chewing gum, thereby damaging the trust that exists between its clients and other partners involved.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Why Watering Hole Attacks Are Effective
There are many reasons why watering hole attacks are effective: Targeted Nature of the Attack: In this type of attack, attackers have targeted specific groups or individuals, making the malware very relevant to the victim. This goes in favour of increasing chances of success. Since the attack has taken place through trusted websites, users are least likely to doubt it. Also, these attackers often use advanced techniques to make the malware undetectable. In attacking compromised websites, attackers strip the victims of their trust, which otherwise lowers their guard. Hence, they tend to become prone to such malware unknowingly.
Watering hole attacks tend to be highly persistent because they are not based on a single victim, but on a collection or community of potential victims. For instance, they might target websites popular within Cyber Media, where journalists, network security professionals, or other individuals from the tech community regularly visit. Attackers select appropriately popular sites that their target audience uses frequently, with minimal effort for coverage. Once the malware reaches the website, it will impact many users over time, and continuously compromise people that visit the site. The strategic character of watering hole attacks, complemented by their multiplier effect on users over an extended period, increases the effectiveness of this type of attack and makes it very attractive to cyber threats.
How to Defend Against Watering Hole Attacks
Protecting Websites
Webmasters ought to update their content management systems (CMS) and plugins regularly to fix known vulnerabilities. This includes secure coding practices, tight access control, and constant site monitoring to detect unusual activities.
Employee Awareness and Training
Employees must be exposed to the risks of watering hole attacks and the importance of not clicking suspicious links or downloading unknown files. By exploiting vulnerabilities in the site’s Web Application Security , attackers can manipulate the website’s backend database or inject malicious code that is then served to visitors. This training should be consistently carried out and augmented by awareness campaigns.
Monitoring and Detection of Network
Network monitoring tools that monitor unusual outbound traffic or unauthorized access can identify when an attack is happening. Organizations should employ Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to scan for and flag malicious activity.
Keeping Software Updated
It is also essential for organizations and individuals to ensure that all their browsers, operating systems, and plugins are updated with security patches so that they are protected from zero-day vulnerabilities, which are inevitable through regular patch management practice.
Are You Preparing for Cyber Security Jobs? Check Out ACTE’s Cyber Security Interview Questions and Answers to Boost Your Preparation!
Conclusion
Cyber Security Training Courses are an extremely sophisticated form of highly targeted attack that can hit the victim at the individual and organizational levels. These attacks exploit trusted sites to silently deliver malware to unknown victims without knowing much about the attacks, making it difficult to identify them. Knowledge of how they work and proper defence measures prevent much of this. As the complexity of cyber threats grows, it is incumbent upon organizations also to be more alert while trying to follow stringent security protocols and train the workforce regarding the vulnerability of getting victimized in such an attack. This will allow businesses and individuals to considerably lower the chances of becoming victims of this highly deceitful cyber threats tactic. New and continuous threat intelligence and ensuring regular website security audits can detect and mitigate such risks long before they worsen. The culture of cybersecurity awareness helps lead to the development of effective defence mechanisms against evolving threats such as the watering hole attack.





