
- What Is Network Segmentation?
- Why is Network Segmentation Important?
- How Network Segmentation Works
- Types of Network Segmentation
- Benefits of Network Segmentation
- Best Practices for Effective Network Segmentation
- Common Network Segmentation Tools and Technologies
- Challenges of Network Segmentation
- Conclusion
Network segmentation has been one of the best techniques to safeguard sensitive data and reduce the damage of cyber attacks in an ever-changing cyberspace. But what is network segmentation, and why is it particularly important for organizations of all sizes? In this blog post, I discuss computer network security, its advantages, methods, and good practices, and how it fits into enhancing your security. By dividing a network into smaller, isolated segments, businesses can limit the potential reach of cyber attackers, minimize the spread of malware, and reduce the impact of security breaches. Implementing a Sandbox Environment within each segment can further enhance security. This approach ensures that sensitive data and critical systems are better protected, making it more difficult for attackers to access or exfiltrate valuable information. Implementing network security has become a vital step in building a resilient cybersecurity framework as cyber threats evolve.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
What Is Network Segmentation?
Network segmentation is dividing a computer network into various small sub-networks or segments for betterment in terms of network performance, security, and manageability. Cyber Security Training Courses can be done either physically or logically. In this network segmentation approach, some barriers exist between different network segments instead of having one big monolithic network where everything is connected and can freely communicate with every other device.
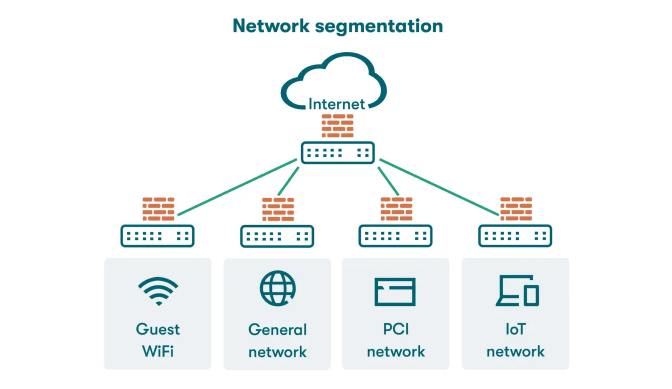
Network segmentation reduces the possibilities of an attacker’s free flow across the entire network, hence limiting their ability for lateral movement. It aims to allow granular control over devices and users meant to gain access to sensitive resources and is a further defence against cyber threats. Organizations can implement strict accessorganizationsisolating different network segments to ensure that only authorized users or devices can communicate with critical systems. This added layer of security prevents attackers from exploiting vulnerabilities in one part of the network to compromise other, more sensitive areas. Network security also allows for better monitoring and detection of unusual activity, making it easier to spot potential threats early. Ultimately, it strengthens an organisation’s defence posture by containing threats before they can escalate into full-blown breaches.
Why is Network Segmentation Important?
- The need for network segmentation has become more pressing over the years as the complexity of cyberattacks has increased. In the case of one section of the network, segmentation will limit the attack and deny it the freedom it may have in spreading throughout the entire network.
- Segmentation isolates network sections with critical applications in dedicated segments, making it difficult for attackers to access such sensitive information. With the concept of segmentation, the network minimizes congestion, which is the volume of traffic a given area can receive. Other standards, such as PCI DSS, HIPAA, and GDPR, imply regulatory compliance requiring organizations to protect sensitive data via access controls, thereby often necessitating the implementation of network security.
- This might ensure faster data transmission, which usually means better network speed. If users or departments are made to communicate through specific segments of the network, this also provides better control over access to sensitive data and resources, limiting unauthorized users’ access to control systems. By isolating critical systems and sensitive data, network segmentation helps mitigate risks associated with Cyber Defamation, where malicious actors could spread false or damaging information about a company.
- Network segmentation also plays a crucial role in incident response and disaster recovery. When an attack occurs, segmented networks allow security teams to quickly isolate the compromised segment and prevent further damage. They also help pinpoint the source of the breach, speeding up the investigation process.
- Moreover, in the event of a system failure, segmentation makes it easier to restore affected segments without disrupting the entire network, ensuring business continuity. By isolating critical infrastructure and sensitive data, organizations are better equipped to meet compliance requirements, mitigate risks, and safeguard their digital assets from external and internal threats.
- Network security works by logically or physically dividing a network into different segments. Such divisions can normally be created through firewalls, VLANs, ACLs, and routers.
- Firewalls are boundaries that filter traffic between network segments, allowing authorized traffic to move between them. Security professionals can leverage resources like the Google Hacking Database to identify potential vulnerabilities or weak spots in their firewall configurations.
- VLANs refer to the virtualized network, which logically groups devices on the same network even though they may not reside in a part of the same infrastructure. VLANs enable traffic separation, isolate sensitive systems, and segment users.
- ACLs This is called an Access Control List which describes who or what can gain access to a particular segment using rules based on IP addresses, ports, and protocols.
- Once these technologies are installed, administrators can configure each segment to enforce policies controlling traffic flow and access between segments.
- Firewalls, for example, pfSense and Cisco ASA
- Virtual LANs (VLANs)
- NAC solutions
- SD-WAN to segment remote locations or branch
- NGFW for more granular filtering and security
- IDS/IPS Intrusion Detection/Prevention
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
How Network Segmentation Works
Types of Network Segmentation
Physical Segmentation: In physical segmentation, hardware devices like firewalls, switches, or routers are used to physically separate the networks. These devices ensure independent segments that cannot communicate with others. Physical segmentation can provide greater security measures, as each segment is isolated, so it will be challenging for any attacker to move from one segment to another. For example, a company may have separate physical networks for its internal systems, the guest Wi-Fi network, and the external-facing servers.
Logical Segmentation: Logical segmentation does not need separate physical devices. It can be done using software configuration. VLANs and subnets are mostly utilized as virtualization technologies in logical segmentation. Devices on the same physical network can be combined into different groups logically, where an opposite set of rules and policies can be defined for each group. Logical segmentation is more flexible and cheaper than physical segmentation but does not offer the same isolation level. However, it could still ensure substantial protection combined with other security measures such as firewalls and ACLs.
Benefits of Network Segmentation
Network segmentation limits access to important data and systems, preventing attackers from accessing critical assets. For example, if an attacker were to compromise a user’s machine on one of these segmented networks, which is not considered important, the attacker would be unable to move to finance laterally or HR systems. Zero Trust models become easier to implement with segmentation where trust is never implicitly granted, and each access request is verified. Segmentation eliminates traffic congestion in networks since it limits the scope of broadcast traffic and separates those load-intensive traffic elements.
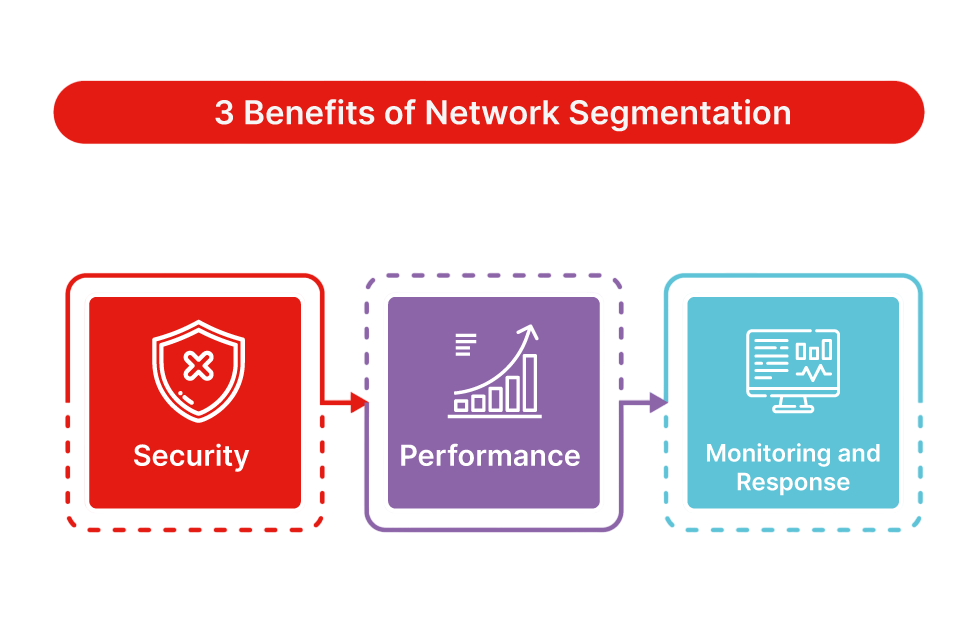
For example, you can set up one segment which acts as the path for bandwidth applications such as video conferencing and another for administrative matters. This limits network bottlenecks and makes data flow more efficient. Many regulatory requirements require organizations to protect confidential information and enforce very granular access controls. A good method of achieving PCI DSS compliance is through Cyber Security Training Courses. This is because PCI requires the isolation of cardholder data. Segmentation aids in the exhibition of evidence at audit time and improves risk management by placing stricter policies on access.
Best Practices for Effective Network Segmentation
Planning and Design
Before a company begins to segment its network, it must ascend design for designing a segmentation plan tits the company’s security and compliance performance requirements. This includes prioritizing high-security da, ta anit d systems but could also impact network performance.
Access Control Implementation
Protect every part’s access with the principle of least privilege. Authorize access to sensitive data and systems only for established users, devices, and applications. Access policies must be reviewed periodically against organizational needs. It’s essential to be vigilant about threats like Vulnerability Management, which can capture keystrokes and compromise login credentials or sensitive information.
Monitoring and Maintenance
Traffic between the segments must be monitored for any indication of malicious activity or bypassing access control. Network security configurations must periodically be reviewed and updated in response to new threats or to a network’s changing needs.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Challenges of Network Segmentation
Network segmentation is complex, and its implementation in a large, multi-site network may take much work. Proper planning and seamless segmentation management are called for so that segregation does not invite more problems than it solves. It is possible to have too many segments, leading to troubles in communication between various systems and inefficiency in managing the network. Certain physical segmentation methods, for example, setting up additional firewalls or networking devices, are cost-intensive. It’s not a one-time fix. Network administrators can use techniques like Google Dorking to identify potential vulnerabilities in their network setup. Network security is something that can be done only once and then be remembered. System updates, or new systems added to your infrastructure require revisiting, adjusting, and maintaining your network segmentation. The complexity of network security increases as the organization grows or adopts new technologies like cloud computing, IoT devices, or remote work solutions. These additions may introduce new challenges in maintaining a secure and segmented network. For instance, ensuring proper segmentation between on-premises and cloud-based systems or managing access controls across various devices requires continuous oversight. As businesses evolve, so do their network security needs. Therefore, regular assessments, vulnerability testing, and adjustments are essential to keep the segmentation strategy effective. This ongoing process helps mitigate risks associated with misconfigurations, overlooked access points, or changes in regulatory requirements.
Common Network Segmentation Tools and Technologies
The following are the tools and technologies that may be followed to implement network segmentation:
These technologies assist in segmenting the network and ensure that all security policies are applied uniformly.
Want to Learn About Cyber Security? Explore Our Cyber Security Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Network security is one of the most effective ways to increase an organization’s security, performance, and compliance. It offers limitations and isolation of critical resources to greatly mminimizedata breaches and cyberattacks. However, organization segmentation must be well planned and maintained to prevent complexity and over-segmentation, which involve overcoming problems. Network segmentation is no longer considered a luxury but a necessity for organization suffering from increasing Cyber Security Training Courses and regulatory pressure. When implemented effectively, it promises to be one of the best ways of securing your network or keeping sensitive data out of harm’s way. Organizations can enforce more granular access controls by isolating critical infrastructure and segmenting different departments or user groups, reducing the risk of unauthorized access. It also allows for quicker detection of suspicious activities, making it easier to mitigate potential threats before they spread. Network segmentation supports compliance with data protection regulations, ensuring sensitive information is properly secured. In today’s rapidly evolving threat landscape, network segmentation provides a proactive and scalable solution to safeguard digital assets and maintain operational integrity.





