
- Understanding ARP: The Foundation of Networking
- How ARP Functions
- Integrating DHCP and DNS with ARP
- Varieties of ARP
- ARP vs. RARP: Key Differences Explained
- The Role of ARP in Networking
- ARP Spoofing
- Conclusion
- Using ARP, IP addresses are translated into corresponding MAC addresses.
- It sends out request messages over the network and returns unicast responses.
- Maps are momentarily stored on an ARP cache.
In the age of digital technology, communicating should be effortless. Using protocols like DNS, DHCP, and ARP can help achieve this. Address Resolution Protocol (ARP) connects IP addresses to MAC addresses, Domain Name System (DNS) converts domain names into ipv4 address, and Dynamic Host Configuration Protocol (DHCP) distributes IP addresses in a dynamic manner. Combined with the growing influence of Cyber Media, which spreads information rapidly across platforms, the potential for cyber threats to exploit vulnerabilities in DHCP systems has also increased.
To Earn Your Address Resolution Protocol Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Understanding ARP: The Foundation of Networking
ARP in Cyber Security Training Courses, is a mechanism that links MAC and IP addresses and enables communication between local networks. This protocol broadcasts queries and saves the answers momentarily to facilitate more communication. The salient characteristics of ARP are as follows:
How ARP Functions
The ARP protocol (Address Resolution Protocol) links IP addresses to MAC addresses for local area network data transfer. When a device wants to communicate data to another, it broadcasts an ARP request using its IP and MAC addresses. The device then searches for the recipient’s MAC address connected with this IP address. All other LAN devices receive this request until the one with a similar IP responds with its MAC address. The data packet is then properly transmitted by the sender, who uses this MAC address to encapsulate it.
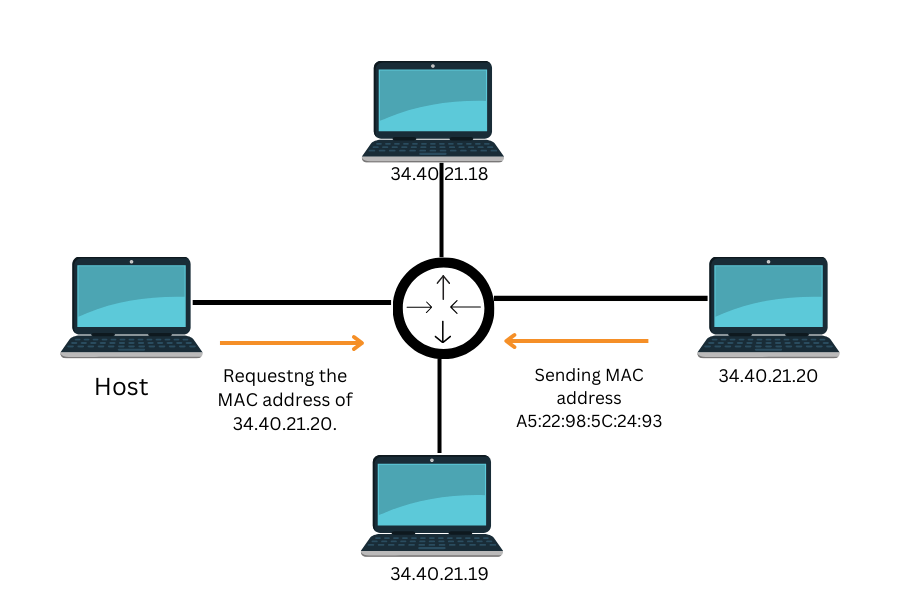
For example With its own identification of “192.168.1.20,” as confirmed by an ARP request broadcast by Computer A asking, “Who has IP 192.168.1.20?” Computer A wishes to send some data to Computer B. Computer A’s Ip address location is 192.168.1.10; its MAC address is AA:BB:CC:DD: EE. Such attacks can be detected and analyzed through resources like the Google Hacking Database, which can help identify potential vulnerabilities in network protocols and prevent unauthorized access.
A specific computer B, whose MAC address is 11:22:33:44:55:66 and whose IP address is 192.168.1.20, answers this request by disclosing its MAC address. Conversely, Computer A retrieves this data from a cache and modifies it instantly; as a result, all incoming packets will now be routed to Computer B’s MAC address (11:22:33:44:55:66). This guarantees that the data is sent to Computer B securely because we can’t send it there until we know who owns it!
Are You Interested in Learning More About Address Resolution Protocol? Sign Up For Our Cyber Security Online Training Today!
Integrating DHCP and DNS with ARP
DHCP with ARP
While they serve different purposes in networking, Cyber Security Training Courses and Dynamic Host Configuration Protocol (DHCP) collaborate to make networks functional for communication.
DHCP
When a device connects to a network, it needs an IP address to communicate with other devices. This is achieved by dynamically allocating an IP address to the devices via the DHCP server, which offers an IP address for a predetermined time, known as the DHCP lease period.
ARP
A device should discover the MAC address of the target device it wishes to communicate with after getting an IP address via DHCP. When a device on a local network wishes to interact with another, it sends an ARP request using the ARP protocol to find out the target device’s MAC address. The ARP protocol connects MAC addresses to IP addresses. In summary, ARP transforms IP addresses into MAC addresses to enable network communication, whereas DHCP distributes IP addresses to devices in a network dynamically. These two protocols work together to allow devices to get their IP addresses and efficiently interact over LANs.
ARP and DNS
Two distinct protocols that cooperate to transfer information between IP addresses and other types of addresses are the Domain Name System (DNS) and the Address Resolution Protocol (ARP).
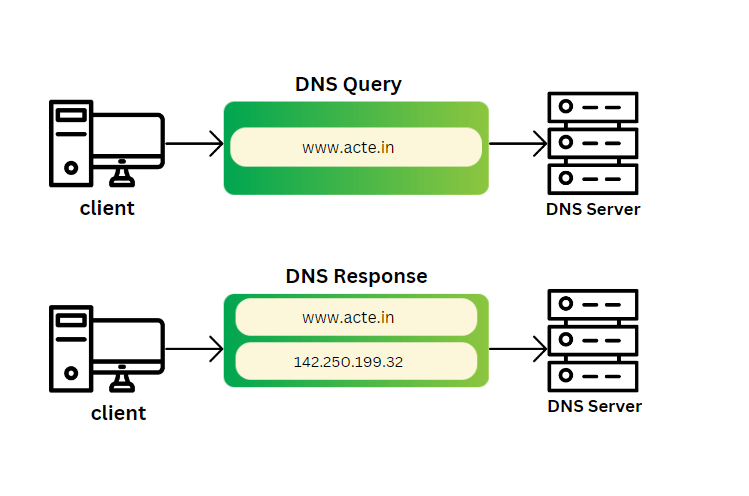
DNS
DNS assists in converting domain names into IP addresses, which are then used for packet routing by the TCP/IP suite. For instance, a human-readable hostname like “acte.in” can be converted into an IP address using DNS.
ARP
ARP converts IP addresses into MAC addresses, which networking devices utilize as distinct physical addresses. ARP is required whenever you wish to send a packet between hosts on the same network or even across networks. In networking, DNS and ARP serve distinct purposes. DNS’s primary function is to convert easily navigable domain names into their equivalent IP addresses, which facilitates the retrieval of websites and services.
Varieties of ARP
Four different forms of ARP are proxy ARP, gratuitous ARP, RARP, and InARP. Let’s study them in more detail.
1. Proxy ARP
A router or other network equipment answers to ARP requests from another device in a proxy ARP exchange. This makes it possible for devices on one network to speak with devices on other networks without requiring routing configuration or MAC address knowledge. This convenience can also introduce security risks, as it can be exploited by attackers during a Network Penetration Testing exercise to perform man-in-the-middle attacks or bypass network segmentation.
2. Gratuitous ARP
An Address Resolution Protocol(ARP) request or reply sent in response to no request is known as a gratuitous ARP. Typically, a node uses it to expose its IP to MAC mapping, which helps identify IP conflicts or refreshes other nodes’ ARP caches with its current MAC address.
3. Reverse ARP (RARP)
Reverse Address Resolution Protocol (RARP) is a technique used by gateway servers to allow a computer to find its IP address. Diskless workstations used to use this because they required an IP address from the server but only knew their MAC addresses. DHCP has essentially taken the position of RARP.
4. Inverse ARP (InARP)
Given a MAC address, the Inverse Address Resolution Protocol (InARP) determines an IP number. It maps virtual circuit identities into Internet Protocol addresses in frame relay and ATM networks.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
ARP vs. RARP: Key Differences Explained
| Key Aspects | ARP | RARP |
|---|---|---|
| Full-Form | Address Resolution Protocol | Reverse Address Resolution Protocol |
| Definition | Finding a receiver’s physical address on a network is the aim of the ARP. | RARP helps in discovering the logical address of its computer from an attendant. |
| Usages | ARP was intended for various purposes, such as locating the addresses of other LAN devices via hosts or routers. | Thin clients can use RARP because of its restricted capabilities. |
| Mapping | These mappings make sure that each node has a unique IP and MAC address combination. | RARP maps MAC addresses (48-bit physical) into Internet Protocol Addresses (32-bit logical). |
| Addresses | IP addresses | MAC addresses |
| Operation | With a known IP address obtain the MAC address | With a known MAC address obtain the IP address |
| Fetching | MAC address fetched by the receiver’s | IP address fetched by the receiver’s |
The Role of ARP in Networking
The Address Resolution Protocol (ARP) is a networking protocol that maps IP addresses to MAC addresses to improve device connectivity. However, ARP can be exploited by attackers to deliver malicious Payloads. Consider the scenario when a computer with the IP address 192.168.1.2 wishes to connect to a device in the network that is only connected to the IP address 192.168.1.3. Next, the machine sends an ARP request asking, “Who has IP address 192.168.1.3?” The device with such an Internet address will reply with something like “00:1A:2B:3C:4D:5E” as its MAC address. Now, the computer may send data directly to a particular device using its MAC address, guaranteeing quick network communication between the two.
Go Through These Cyber Security Interview Questions and Answers to Excel in Your Upcoming Interview.
ARP Spoofing
ARP spoofing, or cache poisoning, is an attack where a hacker uses a local area network (LAN) to broadcast false Cyber Security Training Courses messages. The aim is to connect the hacker’s MAC address to a working website Ip address of any other network resource, such as a server or router. In this manner, communication intended for such a legitimate resource might be intercepted, changed, or redirected by the attacker, opening the door to various security risks like eavesdropping, session hijacking, and denial of service (DoS) assaults. ARP spoofing can have serious implications for network security, as it undermines the integrity of network communications.
Once the attacker successfully associates their MAC address with a legitimate IP address, they can gain unauthorized access to sensitive data, monitor network traffic, and potentially inject malicious packets into the communication stream. This makes it easier for the attacker to carry out further attacks, such as stealing credentials, installing malware, or disrupting the network’s functionality. To mitigate the risk of ARP spoofing, network administrators often employ security measures like static ARP entries, ARP monitoring tools, and encryption protocols, which help detect and prevent unauthorized access and ensure the authenticity of network traffic.
Conclusion
Complex computer networks require these essential protocols ARP, DHCP, and DNS to communicate constantly. ARP is an IP address location to MAC address mapping mechanism, while DHCP assigns website IP addresses dynamically, and DNS converts domain names into IP addresses. These facilitate effective data transfers across network computers, but risks like ARP spoofing draw attention to the necessity of strong security measures. Therefore, alongside the implementation of these protocols, Web Application Security becomes crucial in safeguarding against vulnerabilities that could be exploited by attackers. By understanding how these protocols interrelate, organizations can design secure and functional networks that protect both the infrastructure and web applications from potential threats.





