
- A DMZ network: what is it?
- Purpose of a Demilitarized Zone
- Types of DMZ Services
- Security Considerations for a DMZ
- Best Practices for Designing a DMZ
- Basic DMZ Architecture
- Trends in DMZ
- Conclusion
DMZ is an isolated network segment between an organization’s internal, trusted network and an external, untrusted network. This is often the Internet. It is a buffer or intermediary zone that safeguards the internal network from outside threats yet allows some public-facing services to be accessed by external users. In the military context, it acts as an area devoid of any military forces, preventing conflict and safeguarding sensitive regions. Similarly, in the context of networking, a Cybersecurity Training Courses is a secure area in which public-facing dmz services could be located that are accessible by users but remain isolated from the inside to reduce the threat of an external influence penetrating an organization’s sensitive systems and data.
A DMZ network: what is it?
A DMZ is a logical or physical subnet that separates a local area network (LAN) from untrusted networks, such as the Internet. Every service provided to users via the public Internet must be installed within the DMZ network. It is typically where the resources, services, and dns servers visible to the outside world are located. The services offered include web, email, file transfer protocol (FTP), DNS, proxy servers, and voice-over-internet protocol (VoIP). Although the DMZ servers and resources are segregated and have very little LAN connectivity, they are reachable via the Internet. A hacker cannot immediately access internal servers and data from the Internet thanks to this method, which adds an extra layer of Quantum Cryptography to the LAN. Systems that operate services on a DMZ server are accessible to hackers and cybercriminals. To resist ongoing attacks, the servers’ security needs to be strengthened. A DMZ’s primary goal is to allow businesses to access the public Internet while maintaining the security of their dmz in network security or LANs.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Purpose of a Demilitarized Zone
The purpose of the DMZ is to safeguard the most vulnerable hosts. Most DMZ servers provide services to users not local area network (LAN). They must be installed in the monitored subnetwork due to the heightened risk of assaults. If the rest of the network is compromised, this will safeguard it. Because data passing via the DMZ is less safe, hosts in the DMZ have access permissions to dmz services within the internal network, and this access is strictly regulated. The connectivity between the DMZ hosts and the outside network is limited to aid in expanding the protected border zone. This permits communication between the hosts in the protecteddmz in network security, while the firewall manages the separation and Vulnerability Management of all shared traffic between the DMZ and the internal network.
Are you curious to know more about Cybersecurity? Take advantage of our comprehensive online Cyber Security Online Training .
Types of DMZ Services
DMZ is generally used for hosting services that need to be accessed externally but do not require direct access to the internal network. The following are some typical instances of services that are located in the DMZ:
- Web Servers:We often place dmz web server with public sites in the DMZ. They must be reachable from the Internet but do not require internal access to the systems.
- Mail Servers: Mail servers, which may accept incoming or outgoing emails, are often placed in a DMZ. dns servers interact with both external mail servers and internal users.
- DNS Servers: DNS servers that resolve internal and external domains are placed inside the DMZ
- FTP Servers: FTP servers that allow users outside the network to upload or download files.
- VPN Gateways: VPN gateways for remote access to an internal network can be located in the DMZ to allow encrypted communications into the internal network without bringing a direct Internet connection inside the internal network.
- Proxy Servers: Proxy servers typically are installed on a DMZ for managing traffic between users inside the dmz in network security and the Internet. These proxy servers are used to anonymize and filter incoming traffic into the network.
Security Considerations for a DMZ
- Limit the flow of traffic between the internal network and the DMZ. Only communication necessary for the functionality of dmz web server, mail servers, etc., is allowed, even with strict ACLs to prevent unauthorized traffic.
- Allow specified traffic from external networks into the DMZ, such as HTTP/HTTPS for dmz web server, SMTP for mail servers, etc. Block incoming traffic to prevent malicious or unauthorized access attempts. Rate limiting, deep packet inspection, and blocking known malicious IP addresses are typical.
- Most organizations deploy Intrusion Detection and Prevention Systems in their DMZ for Supply Chain Management . The IDPS system can spot suspicious activity in real-time, so action is automatically taken to prevent threats from reaching sensitive systems in the internal network.
- Attackers generally target servers within the DMZ, so an organization must maintain regular patching and updating of the software installed on the servers. An attacker could use a vulnerability to steal access to a server or elevate privileges.
- Constant monitoring and logging of activities in the DMZ will be essential to detect potential breaches. All necessary logs must be collected and analyzed for anomalies such as unusual traffic patterns, failed login attempts, and access requests that seem to come from unauthorized people. SIEM systems are often used to consolidate and analyze logs across the network.
- Segmentation of the DMZ from the internal network appropriately, both in application and dmz in network security. The users should have the minimum required access to perform their tasks. For example, thedmz web server in the DMZ should only access databases directly if necessary and in a controlled manner.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Best Practices for Designing a DMZ
- Minimal Exposure:Only place services that should be accessed from the outside within the DMZ and maintain sensitive internal systems and critical infrastructure outside the DMZ.
- Layered Security: Use as many layers of security as possible, including intrusion detection and prevention systems, firewalls, and ACLs. Defence in depth ensures that if one layer is compromised, the entiredmz in network security is not penetrated.
- Separation of Duties: Do not allow internal access to DMZ system management. This prevents an attacker from using internally compromised privileges to access the DMZ.
- Redundancy and High Availability: Ensure high availability by load balancing and providing other fallback and redundant hardware in thedmz services available within the DMZ.
- Regular Audits and Penetration Testing: Do regular Threat Intelligence audits and penetration tests to determine vulnerabilities in the DMZ and correct them before they would be exploited.
Basic DMZ Architecture
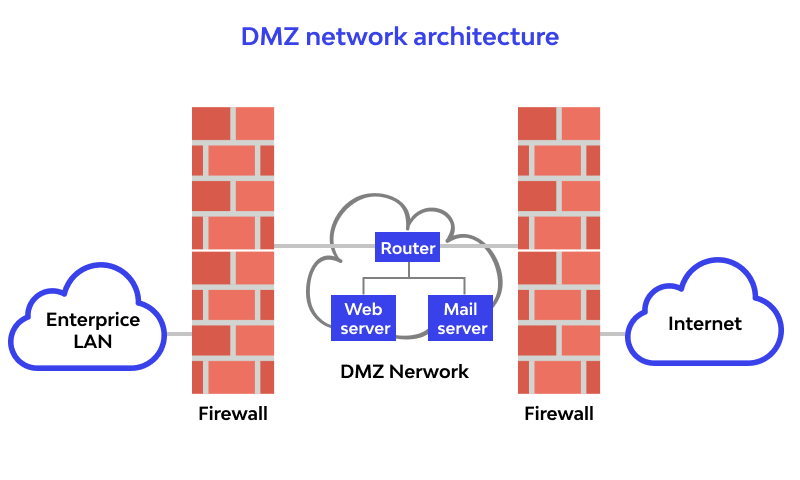
Single Firewall DMZ One firewall is configured to separate the internal network from the Cybersecurity Training Courses and the external network. In such a configuration, the firewall has three network interfaces.
- Internal Interface:Connected to the internal network (trusted zone).
- External Interface: Connected to the public Internet (untrusted zone).
- DMZ Interface:Connected to the DMZ network.
This design allows all internet traffic to access the DMZ, but data traffic between the internal network and the DMZ is highly controlled. And outbound traffic from the internal network to the DMZ is restricted to minimize exposure.DMZ with Two Firewalls This dual dmz architecture requires the deployment of two firewalls in a more secure configuration between the DMZ and the Internet and between the DMZ and the internal network. This is expected to ensure more security by placing an additional layer of protection between the internal network and the DMZ and between the DMZ and the external network. Firewall 1 A front-end firewall between the Internet and the DMZ lets users access public-facing services but denies them access to internal resources. Firewall 2 is a back-end firewall between the DMZ and the internal network that further filters traffic entering the internal network.Dmz architecture is often used because it allows better traffic filtering, a strong sense of separation between internal and external networks, and reduced chances of unauthorized access between the internal network and the DMZ.
Preparing for a job Interview? Check out our blog on Cybersecurity Interview Questions and Answers .
Trends in DMZ
- Cloud-Based DMZs and Hybrid Architectures:One of the most significant trends is the shift from traditional on-premises DMZs to cloud-based or hybrid DMZ architectures. With the extensive use of cloud computing, services are hosted in a wide range of cloud environments, including Amazon Web Services (AWS), Microsoft Azure, Intrusion Prevention System , and others.
- Zero Trust Security Model: The older DMZ model was just a perimeter security system where everything on the inside of the internal network was trusted. This approach, known as “trust but verify,” has been increasingly forced out through the growing use of Zero-Trust Security. The Zero-Trust model presumes that nothing from an internal or external network can be trusted; therefore, access must always be verified.
- NGFWs: Though legacy firewalls are still the core of most DMZ security configurations, Next-Generation Firewalls (NGFWs) are commonly implemented for finer controls and more visibility. NGFWs do much more than a simple packet filter and can also enable DPI, application-layer filtering, and intrusion prevention.
- Automation and Orchestration in DMZ Security: Organizations must shift towards automation and orchestration for DMZ security because the response time has to be faster when emerging threats come into play. Recently, the security tools and firewalls in the DMZ were integrated with automation platforms that dynamically responded to threats and changed policies in real-time.
- Microservices and Containerization in the DMZ: The rise of microservices and containerization throughout IT infrastructures further influences the architecture of DMZs. Microservices-based dmz architecture often require flexible, lightweight, and scalable security controls that are applied on a service-by-service basis rather than as dns servers.
Conclusion
The DMZ network plays a basic role in modern security, acting as a buffer zone between an internal network and the outside internet. Segregation of public-facing services from internal systems reduces the likelihood of an inside attack along its boundary moving into its core network. An implemented Cybersecurity Training properly boosts an organization’s overall security posture, offering additional protection against attacks from outside threats. However, it must be designed with strong firewall rules, proper segmentation, and constant monitoring to be effective. This DMZ, properly designed, will ensure that a balance between accessibility and protection is struck in such a way that an organization can offer its dmz services to the outside world while protecting its most sensitive internal resources.





