
- What is Quantum Cryptography?
- Key Principles of Quantum Cryptography
- Challenges and Limitations of Quantum Cryptography
- How Does Quantum Cryptography Work?
- Why is Quantum Cryptography Important?
- Real-World Applications of Quantum Cryptography
- Quantum Cryptography: A New Era in Data Protection
- Quantum Cryptography vs. Traditional Cryptography
- Conclusion
What is Quantum Cryptography?
Quantum cryptography is one of the state-of-the-art areas of cryptography in which the fundamental principles are established using quantum mechanics to secure information transmission. Quantum cryptography differs fundamentally from classical cryptography, based on complex mathematical algorithms; here, quantum cryptography uses effects like superposition, entanglement, and the uncertainty principle to secure the data. At the core of quantum cryptography lies “Quantum Key Distribution (QKD)”. This method allows two parties, Alice and Bob, to exchange quantum key encryption in Cybersecurity Training Courses securely over an untrusted channel so that no one could eavesdrop without being noticed.
Key Principles of Quantum Cryptography
Quantum cryptography hinges on several unique principles of quantum mechanics, which distinguish it from classical cryptographic systems:
- Quantum Superposition:Quantum mechanics describes how photons can exist in multiple states at one moment, an important phenomenon called superposition. Whereas a classical bit is 0 or 1, a qubit enables a linear combination of both values simultaneously, a huge increase in the complexity and potentiality of quantum systems.
- Quantum Entanglement:When two quantum particles are entangled, their states are intrinsically linked, such that the state of one particle will instantly affect the state of the other, no matter how far apart they are. This property is used in quantum cryptography to transfer information securely, as any attempt to alter one of the particles will be instantly detectable.
- Heisenberg Uncertainty Principle:In short, it says that there are some characteristics of particles which can never be known at one time with precision. Those are position and momentum. In the case of quantum cryptography, it has been applied to ensure that if an eavesdropper tries to intercept the data of the quantum security information, his presence will tamper with the information, making intrusion detectable to the parties involved in the communication.
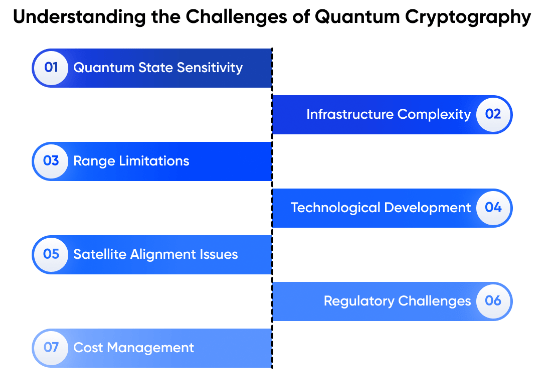
- Technological Complexity: Implementing quantum cryptography requires special hardware, such as photon detectors and quantum security repeaters, making the system quite costly and technically difficult to scale up. This underlines the importance of good Cyber Hygiene in securing currently available systems.
- Distance Limitations:Quantum communication is highly sensitive to environmental interference, and signal loss over long distances is a significant hurdle. To address this, researchers are working on “quantum repeaters”, which can regenerate quantum signals over long distances, but these technologies are still developing.
- Integration with Existing Systems:Integrating quantum cryptography today with current cryptographic systems and infrastructures will require substantial changes to existing protocols and technologies.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Challenges and Limitations of Quantum Cryptography
Despite its promising potential, quantum cryptography today faces several challenges:
How Does Quantum Cryptography Work?
At the heart of quantum cryptography is “quantum key encryption Distribution (QKD)”, which allows two users to exchange a cryptographic key securely. Here’s a simplified overview of how QKD works:
- Photon Transmission:Alice sends Bob a series of photons, each encoded in a random quantum state, representing bits of the quantum key encryption. This process is similar to Enumeration in Ethical Hacking, where information is gathered to identify system vulnerabilities.
- Eavesdropping Detection: If an eavesdropper (Eve) tries to intercept the photons, the quantum state of the particles will change due to the “Heisenberg Uncertainty Principle”.” Alice and Bob can detect this disturbance by comparing a portion of their received bits and immediately discarding any that may have been compromised.
- Key Generation:Alice and Bob end up with a shared cryptographic key after comparing and verifying the transmission. quantum key encryption can now be used for quantum encryption and decryption, ensuring their communication remains secure from third-party interception.
Why is Quantum Cryptography Important?
The main advantage of quantum cryptography is its “security.” While, classically, their methods – RSA and elliptic curve cryptography today – have proven very resistant to computers, a new generation of “quantum computers” threatens this arena. Quantum algorithms, like Shor’s algorithm, break the quantum encryption methods we rely on today by quickly solving exponentially harder problems for a classical computer. Quantum cryptography, especially “QKD,” seems to provide an answer with a secure key exchange resistant to quantum computers. Simultaneously, Network Segmentation can also improve quantum security by constraining the breach’s reach. So, quantum cryptography is also a significant tool for ensuring data secrecy in the quantum computer era.
Become an expert in cyber security. Enroll in this Cyber Security Online Training now to acquire the knowledge you need.
Real-World Applications of Quantum Cryptography
Although quantum cryptography is still in the early stages of development, it holds tremendous potential for a variety of applications, such as:
- Secure Communication: Quantum cryptography could revolutionize secure communication by quantum key encryption exchanges that are impossible to intercept without detection.
- Government and Military Security: Governments and military organizations which rely on highly sensitive information could use cybersecurity cryptography to protect classified communications, national quantum security data, and defence systems.
- Financial Sector Security:Banks, financial institutions, and payment platforms could use cryptography and network security to secure online transactions, protect against cyberattacks, and ensure the confidentiality of sensitive financial data.
- Cloud Computing: As businesses increasingly rely on cloud computing to store and process sensitive data, quantum cryptography today could ensure that this data remains secure from unauthorized access and cyber threats.
Quantum Cryptography: A New Era in Data Protection
Quantum cryptography is a step in the right direction to protect information from quantum computing threats; at this stage, cryptographic methods depend on complicated mathematical algorithms. Such systems are breakable when quantum computers advance. cybersecurity cryptography uses post quantum mechanics laws to create fundamentally hack-proof secure communication channels. Such phenomena as “quantum entanglement” and “superposition,” guarantee the detection of any attempt to intercept the data in Cybersecurity Training Courses. As we move into a future dominated by both quantum computing and increasingly sophisticated cyber threats, quantum cryptography is set to play a vital role in ensuring secure communication and data privacy across industries.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Quantum Cryptography vs. Traditional Cryptography
Understanding the key differences between cryptography and network security and traditional cryptography is crucial as cybersecurity continues to evolve. Both methods aim to protect data, but they do so using fundamentally different principles and technologies.
Traditional Cryptography
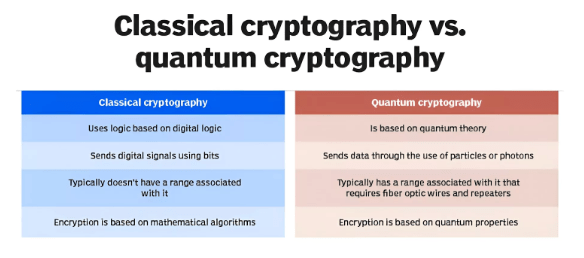
Traditional cryptographic methods such as RSA and AES rely on hard mathematics problems for encrypting information to maintain secrecy. Most of these methods are built around the hardness of factoring large prime numbers or discrete logarithm-related problems. Because of the advent of post quantum computers, these kinds of cryptosystems might become insecure because Shor’s algorithm and other quantum algorithms may solve these problems very efficiently, eventually cracking the quantum encryption and making the system vulnerable to Malware Attacks.
Key features of traditional cryptography include:
- Mathematical Dependence:Security is based on the difficulty of solving mathematical problems.
- Quantum Vulnerability:Classical quantum encryption methods could be compromised by powerful quantum computers.
- Wide Usage:These methods are widely adopted and embedded in many digital quantum security systems.
- Quantum Mechanics: Security is based on the laws of physics, not mathematical computations.
- Unbreakable Security:Any attempt to intercept or tamper with the communication alters the data, revealing the presence of an intruder.
- In Development: While promising, quantum cryptography is still in the experimental phase, with many hurdles to overcome, highlighting the need for Threat Intelligence to secure systems.
- The foundation of security:With traditional cryptography is in the domain of computational complexity, whereas the basis of security in quantum cryptography lies in the principles of quantum physics.
- Defence against Quantum Attacking: classical cybersecurity cryptography can fall victim to post quantum computers, but cryptography and network security has a built-in quantum defence.
- Adoption: Many classical approaches to cryptography are adopted today, while cryptography and network security is still in the early stages of practical deployment.
Quantum Cryptography
Quantum cryptography, on the other hand, relies on quantum mechanics principles to encrypt data. One of the best-known techniques is quantum key distribution, which allows two parties to share cryptographic keys in complete security. cybersecurity cryptography can detect eavesdropping attempts since intercepting data changes its quantum state and alerts the sender and receiver. Unlike traditional cryptographic methods, post quantum cryptography today is very resistant to attacks by quantum computers.
Key features of quantum cryptography include:
Key Differences
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Conclusion
Quantum cryptography is the new trend in securing digital communication in the principles of quantum mechanics, meeting levels of security that traditional cryptographic methods cannot match. With the rise of quantum technologies, the significance of quantum cryptography will aptly guard sensitive information in the quantum computing era. Even though it remains at the nascent stage with various obstacles that need to be crossed, the prospects for the future of cybersecurity cryptography are simply promising in Cybersecurity Training. It could be the key to protecting the digital world from the growing threats of cyberattacks and quantum decryption methods, providing a secure foundation for communications in a post quantum world.





