
- What is Meant by Web Security?
- Common Threats to Web Applications
- OWASP Top 10 Overview
- Web Application Firewalls (WAFs)
- HTTPS and Secure Communication
- Input Validation and Sanitization
- Secure Authentication Mechanisms
- Session Management
What is Meant by Web Security?
Web security, also known as website security, refers to the protective measures and protocols implemented to safeguard websites and online services against cyber threats, unauthorized access, data breaches, and other malicious attacks. It ensures the integrity, confidentiality, and availability of data transmitted through the web. A crucial part of web security is Website Security Testing, which involves systematically checking a website for vulnerabilities, weaknesses, and potential exploits that attackers could target. Equally important is Web Application Penetration Testing, a simulated cyberattack used to evaluate the security of web applications by identifying coding errors, insecure configurations, or broken authentication mechanisms skills often emphasized in comprehensive Cyber Security Training programs. To strengthen defenses further, organizations often deploy Web Application Firewalls (WAFs), which act as a protective barrier between the web application and external traffic, filtering out malicious requests and preventing threats like SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks. With the constant evolution of cyber threats, web security must be an ongoing process involving regular updates, patching, secure coding practices, and proactive monitoring. Ultimately, effective web security not only protects sensitive data and user privacy but also helps build trust, ensures compliance with legal standards, and maintains the overall reputation and functionality of digital platforms in today’s interconnected world.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Common Threats to Web Applications
- SQL Injection (SQLi): Attackers manipulate input fields to execute malicious SQL queries, accessing or tampering with databases. Tools like Acunetix Web can help detect and prevent such vulnerabilities.
- Cross-Site Scripting (XSS): This occurs when attackers inject malicious scripts into web pages viewed by users, often stealing cookies or session tokens posing a growing concern even in the Future Of Cyber-Physical Systems, where web interfaces and embedded technologies increasingly converge.
- Cross-Site Request Forgery (CSRF): By tricking users into executing unwanted actions, CSRF exploits trust between a browser and a web application. Implementing strong JWT mechanisms helps reduce this risk.
Web applications are frequent targets for cyberattacks due to their accessibility and the valuable data they handle. As developers embrace modern technologies like Firebase Hosting, JWT mechanism, and advanced web programming frameworks, attackers continuously evolve their techniques to exploit weaknesses. Understanding the common threats is essential to build secure and resilient applications. Here are six common threats to web applications:
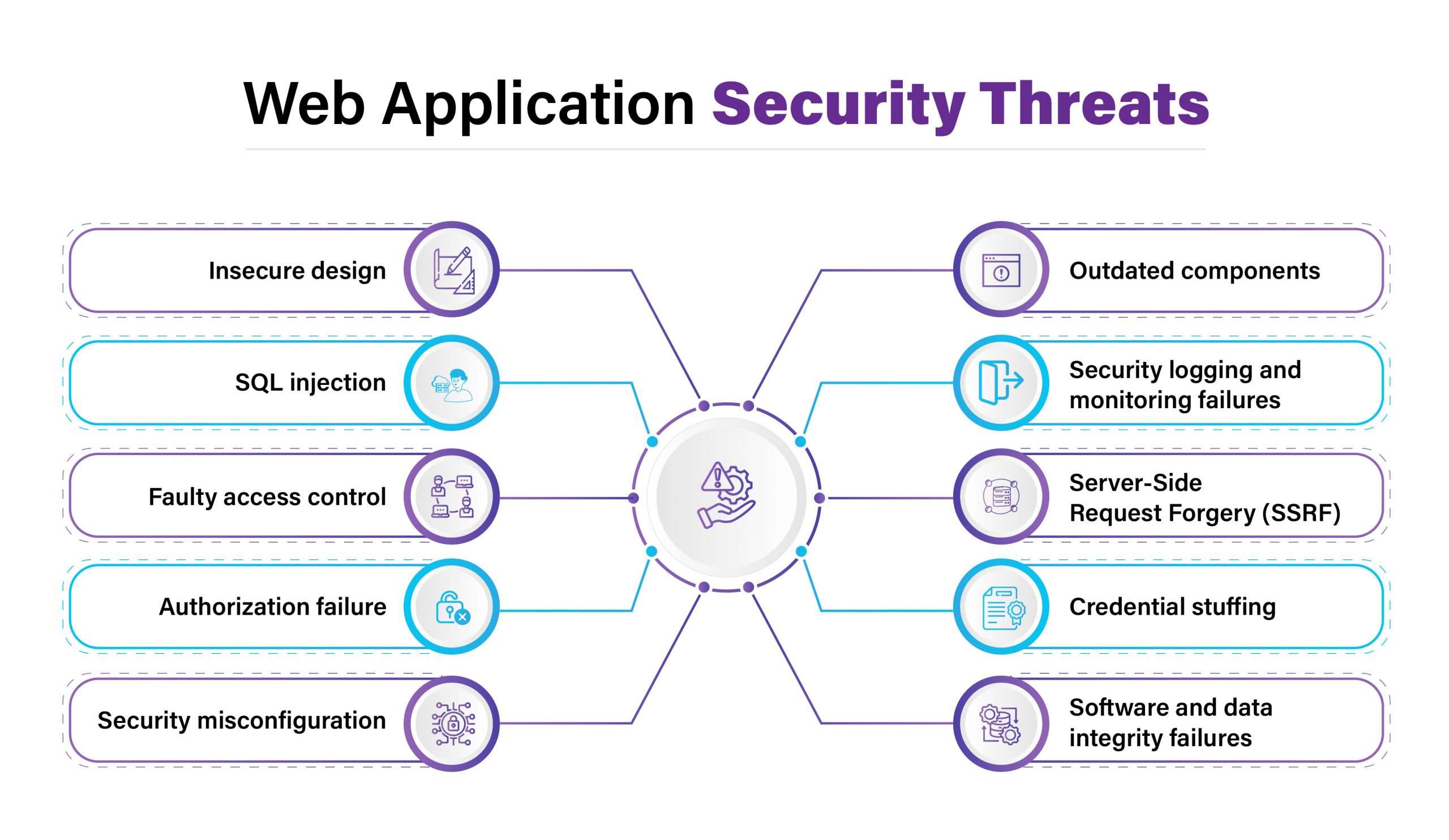
- Broken Authentication: Weak login systems or session handling flaws allow attackers to hijack user accounts. Proper token management and secure coding in web programming are critical.
- Security Misconfigurations: Misconfigured servers, cloud storage, or APIs can expose sensitive data. Firebase Hosting must be properly secured to prevent unauthorized access.
- Insufficient WAF Protection: Without an effective WAF (Web Application Firewall), malicious traffic can reach vulnerable endpoints, increasing the risk of compromise.
OWASP Top 10 Overview
The OWASP Top 10 is a globally recognized list that highlights the most critical security risks to web applications, serving as a foundation for developers, testers, and organizations to enhance their cybersecurity posture. This list, curated by the Open Web Application Security Project (OWASP), includes threats such as broken access control, injection attacks, insecure design, and security misconfigurations, among others. It emphasizes the importance of proactively identifying and mitigating vulnerabilities before they can be exploited. Website Security Testing plays a vital role in uncovering these risks during development and deployment stages, allowing developers to patch flaws before they become liabilities, while Network Penetration Testing helps ensure the broader infrastructure is equally secure against external threats. Similarly, Web Application Penetration Testing involves simulating real-world cyberattacks to assess how well a web app can withstand threats like cross-site scripting, authentication flaws, or data exposure. To further strengthen defense, organizations rely on Web Application Firewalls (WAFs), which help filter out malicious traffic and block common attacks automatically, aligning with OWASP recommendations. By understanding and implementing practices based on the OWASP Top 10, businesses not only secure their digital assets but also build user trust, ensure compliance with data protection standards, and maintain operational resilience in an increasingly hostile online environment.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Web Application Firewalls (WAFs)
- Real-Time Threat Mitigation: WAFs provide instant protection by identifying and blocking attacks in real time before they reach your application, a key concept often covered in Cyber Security Training courses.
- Defense Against OWASP Top 10: WAFs are tailored to guard against common vulnerabilities like injection, broken authentication, and XSS vital for modern apps using JWT mechanisms for security.
- Integration with Security Tools: Tools like Acunetix Web can work alongside WAFs to scan for vulnerabilities and strengthen overall application defenses.
Web Application Firewalls (WAFs) are specialized security solutions designed to monitor, filter, and block malicious traffic between the internet and a web application. Unlike traditional firewalls, WAFs operate at the application layer and are specifically built to defend against threats such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. Whether you’re using Firebase Hosting, custom web programming, or third-party platforms, integrating WAF protection is critical to ensuring the integrity and safety of your applications. Here are six key points about Web Application Firewalls:
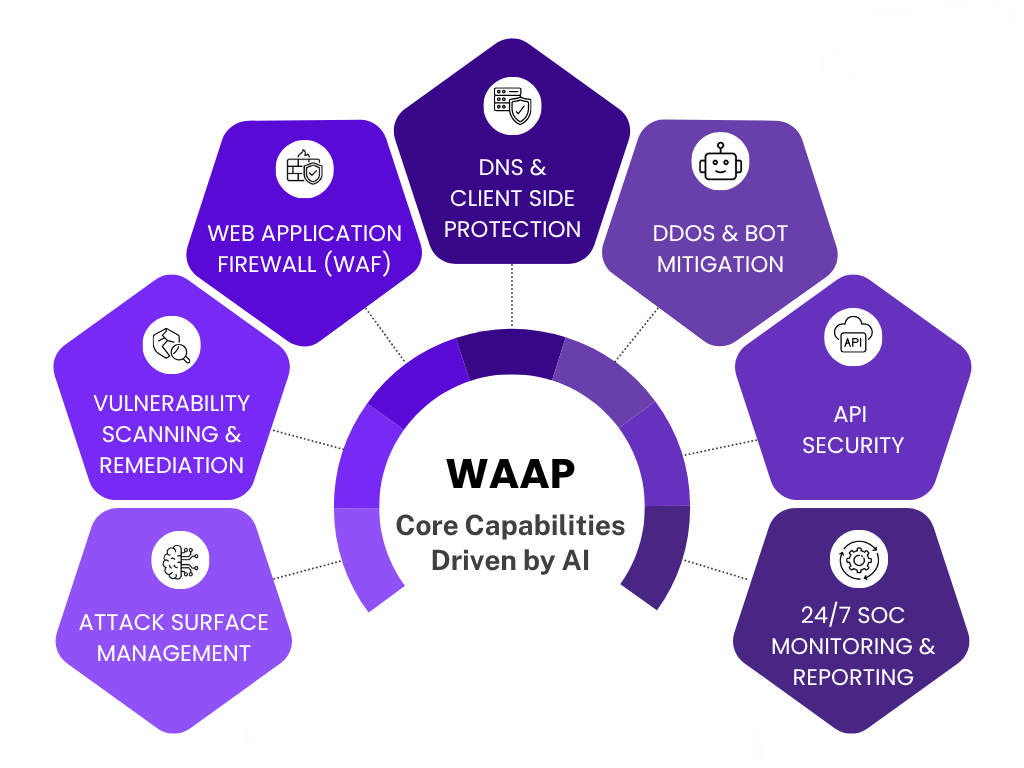
- Customization and Rule-Based Filtering: WAFs allow users to define custom security rules based on application needs and traffic behavior.
- Protection for Hosted Apps: Platforms like Firebase Hosting benefit from WAFs that protect cloud-deployed apps without affecting performance.
- Support for Modern Web Development: WAFs adapt to evolving web programming trends and frameworks, offering scalable protection for both legacy and modern apps.
- Data Encryption: HTTPS uses SSL/TLS to encrypt data in transit, preventing hackers from intercepting sensitive information like passwords and payment details.
- Authentication and Trust: HTTPS ensures users are communicating with the intended server, strengthening trust especially important for apps built on Firebase Hosting or other cloud platforms.
- Protection from MITM Attacks: HTTPS defends against man-in-the-middle attacks, a common threat in insecure networks. Tools like Acunetix Web help test for such vulnerabilities, similar to how topics covered in an Intro To What Is Jailbreaking in Cyber Security explore threats arising from compromised systems and insecure communication channels.
- JWT Security Enhancement: When using JWT mechanisms for user authentication, HTTPS is critical to prevent token theft and session hijacking.
- Improved SEO and Performance: Search engines favor HTTPS-enabled sites, and modern web programming practices often integrate HTTPS by default for better performance.
- Layered Security with WAF: Combining HTTPS with WAF protection ensures encrypted traffic is also scanned for malicious payloads, adding a powerful layer of defense.
HTTPS and Secure Communication
HTTPS, or HyperText Transfer Protocol Secure, is the foundational protocol for secure communication over the web, ensuring that data transferred between a user’s browser and a web server is encrypted and protected from eavesdropping, tampering, and impersonation. Unlike HTTP, HTTPS uses SSL/TLS protocols to encrypt the connection, making it essential for protecting sensitive data like login credentials, payment information, and personal details. This level of security is particularly crucial for websites that handle user data, perform financial transactions, or require authentication. As part of a comprehensive cybersecurity strategy, Website Security Testing is employed to verify that HTTPS is properly implemented, with valid certificates and strong encryption configurations an approach aligned with the principles found in Understanding Cybercrime and Its Implications. Additionally, Web Application Penetration Testing can help uncover weaknesses such as protocol downgrade attacks or improper SSL settings that could compromise secure communication. Complementing these efforts, Web Application Firewalls (WAFs) further protect HTTPS traffic by monitoring and filtering out malicious requests, even over encrypted connections. As cyber threats grow increasingly sophisticated, adopting HTTPS and reinforcing it with layered security measures is vital not only for user trust but also for compliance, performance, and the overall resilience of modern web applications.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Input Validation and Sanitization
HTTPS and Secure Communication are essential for protecting data exchanged between users and web applications. By encrypting traffic, HTTPS ensures confidentiality, data integrity, and authentication, making it a critical layer in any modern cybersecurity strategy. Whether you’re building apps with Firebase Hosting, implementing JWT mechanisms, or using custom web programming, secure communication is non-negotiable. Here are six key points to understand its importance and implementation:
Secure Authentication Mechanisms
Secure authentication mechanisms are vital for verifying user identities and preventing unauthorized access to web applications. These mechanisms include multi-factor authentication (MFA), strong password policies, biometric verification, and token-based authentication systems such as OAuth and JWT. Implementing secure authentication not only protects sensitive data but also forms the foundation of a trustworthy user experience. To ensure these mechanisms function correctly and securely, Website Security Testing is essential for identifying flaws such as weak password enforcement or unencrypted login forms issues that can be exploited in various cyber threats, including those discussed under What Is Cyber Trolling. In more advanced scenarios, Web Application Penetration Testing helps simulate real-world attacks to uncover vulnerabilities like credential stuffing, brute force attempts, or session hijacking. Additionally, Web Application Firewalls (WAFs) add an extra layer of defense by filtering malicious login attempts and blocking automated attacks. Together, these tools and practices ensure that authentication systems are resilient against modern threats. As cyberattacks grow in complexity, relying solely on traditional username-password combinations is no longer sufficient. Organizations must adopt layered, adaptive authentication strategies to stay ahead of attackers. Ultimately, robust authentication not only secures user accounts but also plays a critical role in protecting the entire application ecosystem from breach or compromise.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Session Management
Session management is a critical component of web application security, responsible for maintaining user identity and ensuring continuity throughout a user’s interaction with a site or app. Proper session handling prevents attackers from hijacking or impersonating users, which could lead to unauthorized access and data breaches. Modern applications built with web programming frameworks and hosted on platforms like Firebase Hosting often rely on secure tokens, such as those provided by the JWT mechanism, to manage sessions efficiently and securely. However, session management must be implemented with caution tokens should be securely stored, have expiration times, and be transmitted only over HTTPS connections, as emphasized in professional Cyber Security Training programs. Tools like Acunetix Web are invaluable for identifying session-related vulnerabilities, such as session fixation or improper token invalidation. Additionally, WAF protection plays a key role by blocking common session attacks, including brute-force login attempts and session replay. Secure session management also involves regenerating session IDs after login, enforcing inactivity timeouts, and ensuring that sessions are properly terminated upon logout. With the increasing complexity of web applications, robust session control is essential for protecting user data and maintaining application integrity. By integrating strong session management practices, developers create safer, more reliable experiences for users across all platforms.




