
- Cyber Vandalism: What Is It?
- Vandalism Types
- The Effects of vandalism
- Future Trends
- How to Avoid Cyberattacks
- Examples of Vandalism in the Real World
- Conclusion
In the digital world, vandalism has taken on a different meaning than its simplest definition of physical destruction or property defacement. Cyber vandalism is one form in which this act manifests in contemporary society if it is aimed at a website, digital content, or any other online threats platform. This paper addresses definitions, motivations, methods used, implications of vandalism, its prevention in a Cyber Media, and future tendencies.
Cyber Vandalism: What Is It?
As part of hacking and Cyber Vandalism in the cyberattack world, someone may delete or damage online threats content in a defaced website attack or inject into a user’s browser such malicious code so that users themselves become vehicles to spread harm done to target systems. Of course, such Cyber Security Training Courses actions not only damage the targeted system but will also impact the vandalism in cyber security and safety perception of trust among its many users such actions will often follow political, social, and personal agendas, thus making it more of a weapon for protesting a cause illegitimately. These actions will therefore have very bad outcomes, including financial loss or reputation damage to the affected organization. Recovery may require such huge forensic analysis and an enormous effort in remediating their activities, which can be interpreted to mean that an imperative for significant vandalism in cyber security practices needs to be enhanced further. The blow goes deeper than these immediate subjects and and extends to the much larger web community, creating an aura of fear and mistrust. Digital vandalism can only be prevented through proactive measures like regular security audits, education of users, and implementation of strong access controls. Organizations should encourage a culture of cybersecurity awareness by educating employees on what to look for and report suspicious activities. Collaborative efforts in the vandalism in cyber security community can enhance resilience against potential attacks.
Are you curious to know more about cyber vandalism? Take advantage of our comprehensive online Cyber Security Online Training !
Vandalism Types
- Attacks known as Distributed Denial of Service (DDoS): DDoS attacks are cyber attck strategies in which a target system or network attacks is inundated with a tremendous amount of traffic via several hacked devices. The goal of this traffic overload is to render the target unusable for authorized users.
- Botnets:A botnet is an assembly of compromised computers that is frequently controlled remotely by online threats fraudsters. Numerous illegal operations, including DDoS assaults, widespread spam email distribution, and data theft, are carried out via these network attacks.
- Identity Theft: Identity theft is the stealing of a person’s personal information, such as bank account details, for fraud or other unlawful activity. Using the stolen information, Cyber crime may use it to construct false identities, gain unauthorized access to the victim’s financial accounts, engage in illicit activity, or even pose as the victim.
- Phishing Attack: Phishing is a tactic used to trick people into divulging personal information, such as credit card numbers or passwords. They accomplish this by seeming to be a trustworthy source, usually by using shady websites, emails, or messages. These bogus emails could look real, but their real goal is to steal your personal information.
- Malware: A broad category of harmful software, such as viruses, Trojan horses, and ransomware, is referred to as “malware,” which is short for “malicious software.” The purpose of these programs is to damage computer systems or gain unauthorized access to them in a Malware Attack.
- Website Vandalism:Online hacking and Cyber Vandalism that modifies a website’s appearance and content, usually for political or ideological motives, is referred to as website vandalism. This change is intended to both deliver a message and stop the websites from functioning normally.
- Data Breaches: Sensitive information may be stolen or made public when unauthorized persons gain access to databases. This information could be maliciously used or sold. Search engines promote trustworthy sources in their results, which helps to keep users safe.
- Online harassment and trolling:Similar to hate speech and cyber attck, online harassment seeks to threaten or injure someone via the internet threats. Addressing online threats harassment is essential if we want to make sure that everyone enjoys a safe and friendly internet threats experience.
- Attacks Using Social Engineering: Social engineering is a tactic that preys on people’s inclinations to divulge private information or perform actions that jeopardize security. Reputable websites rank higher in search results to help visitors find information about recognizing and protecting themselves against social engineering techniques.
- Financial Loss: Due to several circumstances, including theft, fraud, and ransom payments, hacking and Cyber Vandalism can cause serious economic problems for people as well as businesses. Cyber crime might utilize sensitive information they have harmed by breaching security measures to steal money or demand ransom, which can result in significant financial losses.
- Threats to National Security: Vandalism can develop into state-sponsored attacks that surpass the scope of individual targets and endanger national security. Cyber crime breach government servers and intelligence through these attacks, with the potential to steal confidential information or compromise critical infrastructure.
- Legal Repercussions: If proven guilty of this crime, vandals may be subject to penalties and perhaps jail time. Vandals may have to pay for the cost of repairing or replacing the items they harmed in addition to facing legal repercussions. Vandalism can also have a wider societal impact, harming community cohesiveness and confidence while costing local governments and property owners money.
- Infractions of Privacy: Vandalism can violate people’s privacy and intervene inappropriately in their lives by revealing personal information. By disclosing sensitive information, such as financial or personal addresses, these breaches put people at risk of identity theft, harassment, and other forms of cyber abuse.
- Infractions of Privacy: Hacking and Cyber Vandalism can violate people’s privacy and intervene inappropriately in their lives by revealing personal information. By disclosing sensitive information, such as financial or personal addresses, these breaches put people at risk of identity theft, harassment, and other forms of cyber threats .
- Infrastructure Damage: Cyber Security Training Courses can lead to assaults on vital infrastructure, such as power grids or transportation network attacks, which could disrupt life-supporting services and endanger public safety. These attacks could have a huge influence on a lot of people’s daily lives since they could result in widespread power outages, transportation difficulties, and other concerns. Safeguarding our vital infrastructure against cyberattack is a national priority.
- Remain Up to Date: It’s critical to remain current with the cyber threats and developments in cybersecurity. Alertness constitutes the first line of defense. Keep yourself updated about potential cyber threats by regularly reading vandalism in cyber security news. You can better secure your online threats presence and make adjustments when you are aware of new hazards.
- 2FA (two-factor authentication) and strong passwords: Ensure that the passwords you use for your online threats accounts are secure, distinct, and updated often. Whenever possible, activate two-factor authentication (2FA) to boost security.
- Phishing Tip: Exercise caution when clicking on unsolicited emails, texts, or links. One tactic that cyberterrorists commonly employ is phishing. To stay away from fraudulent schemes, it’s imperative to learn how to spot phishing efforts.
- Firewalls and Antivirus Software: Your devices should be equipped with both dependable antivirus software and firewalls. Because these technologies can recognize and thwart malicious activity, they provide an additional layer of Database Security. Firewalls and antivirus software act as digital guards, keeping your devices safe from internet threats.
- Frequently Make Backups: Store your important data on an external disk or cloud service regularly. In the case of a cyberattack, you can be sure not to lose critical data by keeping a backup. Having regular backups allows you to recover your data even in the worst-case situations, acting as a safety net.
- Stuxnet Worm (2010): 2010 saw the discovery of the very sophisticated Stuxnet worm, which was created to target industrial control systems. It was intended to harm centrifuges to impede Iran’s nuclear development. This event illustrated how susceptible vital infrastructure is to vandalism.
- 2014’s Sony Pictures Hack: Cyber crime broke into Sony Pictures Entertainment’s network attacks in 2014, taking private communications and sensitive data with them. This incident not only resulted in financial losses but also demonstrated how vulnerable even large organizations are to cyberattacks through Network Topology .
- WannaCry Ransomware Epidemic 2017: The WannaCry ransomware epidemic affected more than 200,000 computers across 150 countries. Files belonging to users were encrypted, and a payment was demanded to unlock them. This event illustrated the pervasiveness of vandalism.
- 2020 Twitter Bitcoin hoax: Several well-known Twitter accounts, including those of politicians and celebrities, were used in 2020 to promote a Bitcoin hoax. This incident showed how public perception can be influenced by vandalism.
Sign up for ACTE Cyber Security Online Training and get a head start in your career Cyber vandalism.
The Effects of Vandalism
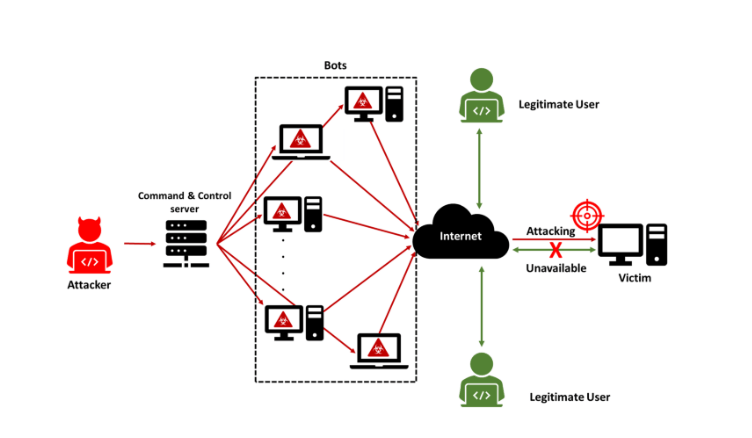
Future Trends
More AI ApplicationArtificial intelligence could be applied by attackers and defenders alike in the cyber vandal context. As much as AI can enhance measures of cybersecurity, it can also be used by hackers to automate attacks in a Web Application Security .
Cybersecurity Becomes Highly RelevantThe reliance on digital platforms will likely push organizations to increase their investments in vandalism in cyber security. It is liable to take a landscape where attackers and defenders adapt in tandem with the emerging cyber threats to a much more sophisticated frontier.
Increased Legal FrameworksUltimately, vandalism could increase pressure for more rigorous legal frameworks and greater global cooperation in attacking cyber crimes. Cyber crimes also mean an intricate dance with jurisdictional issues for policymakers.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cybeysecurity Expert Masters Program Training Course Today!
How to Avoid Cyberattacks
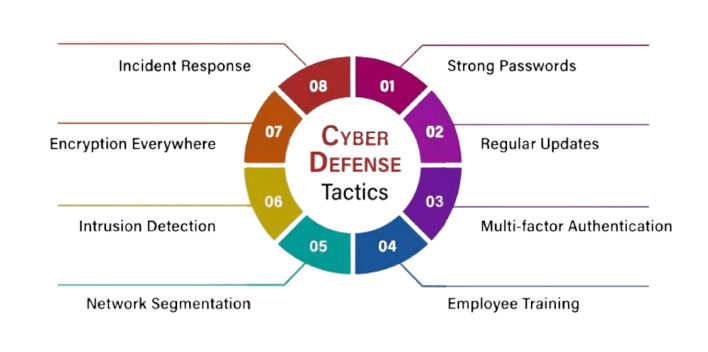
Ready to pass the interview for cyber vandalism? Learn how to answer Cyber Security Interview Questions and Answers Question.
Examples of Vandalism in the Real World
Conclusion
An increasing threat that impacts both individuals and companies is cyber vandalism. DDoS network attacks, data breaches, and cyberbullying wreak havoc. Events from the actual world, such as Stuxnet and WannaCry, serve to illustrate the impact. The favorable tidings? Preventive measures work well. Keep yourself informed, make strong passwords, update your software, and beware of phishing attempts.vandalism in cyber security is a crucial shared role in our connected world. Recognize the signs, follow the guidelines, and promote responsible use of technology. The culture of cybersecurity awareness between organizations and communities has a significant role in lightening the risks posed by Cyber Security Training Courses. Training tends to reduce vulnerabilities very effectively when regarded as the method for educating workers/users concerning the possible cyber threats from cyber vandalism, such as making them aware of phishing emails or the reasons for keeping data private. Open communication in the practice of security might make it possible for its members to share insights concerning digital environments and the related strategies for safeguarding digital environments. Therefore, vandalism in cyber security would come along with the ever-evolving technology that will continuously bring about acts to ensure that no more cyber vandalism exists.






