
- What Is Threat Intelligence?
- Why Threat Intelligence Is Crucial for Cybersecurity
- How to Select the Right Threat Intelligence Platform
- Top Threat Intelligence Tools and Platforms
- Best Practices for Leveraging Threat Intelligence Tools
- The Future of Threat Intelligence
- Conclusion
The ever-changing cybersecurity environment today involves more complex and prolonged cyber security threats to organizations than at any time previously. Since conventional defence methods have failed to protect such vital assets from malicious activities, TI emerges as the solution to this problem. As a preventive measure against cyber intelligence, cyber threat intelligence provides actionable information about current and latent cyber threats to organizations, especially in areas like Web Application Security. To tap the potential of cyber threat intelligence within any organization, various tools and platforms are needed that assist in collecting, analyzing, and disseminating threat data. Of course, such tools play a pivotal role in establishing proactive watch towards detecting vulnerabilities in real-time, which eventually enhances incident response capabilities and improves the overall cyber security intelligence. In this blog, we’ll focus on the major tools and platforms of threat intelligence, their various types, and how they aid different organizations in bolstering cybersecurity defences.
To Explore Threat Intelligence in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
What Is Threat Intelligence?
Threat intelligence involves collecting, analyzing, and distributing information concerning potential or actual threats. It encompasses information about tactics, attack techniques, actors, malware, vulnerabilities, and indicators of compromise (IOCs). The intention behind threat intelligence is to provide organizations with actionable insight for improving security posture and making intelligent decisions concerning protecting systems and networks. Strategic cyber threat intelligence gives high-level views of long-term trends related to threat actor motivations and geopolitical factors that can shape security risks. Tactical Tools and Platforms of Threat Intelligence is about specific attack methodologies, tools, and techniques leveraged by Cyber Security Training Courses, providing actionable data in defence of immediate threats. Operational Threat Intelligence will provide relevant details about the danger and the kind of attack or attacks actively targeting an organization or its sector. Technical cyber threat intelligence is in the form of IP addresses, domain names, file hashes, etc., that provide IOCs to identify and block attacks.
Why Threat Intelligence is the lifeline for cybersecurity
Proactive defence
Cybersecurity threats are constantly advancing with greater force and pace. Protecting organizations using the defence of firewalls and antivirus software alone is not enough. Threat intelligence arms organizations with proactive defence capabilities through early indications of incidents, vulnerabilities, and attack campaigns. Organizations can detect and prevent malicious activity from being escalated by infusing cyber threat intelligence into their security operations.
Enhanced Incident Response
Response time is the pivotal factor when a breach occurs. Threat intelligence assists the incident responder in this regard by providing accurate information about the attack, including its TTPs, the identity of the threat actor, and possible exploited vulnerabilities. All these help speed up containment, eradication, and recovery, reducing the attack’s damage.
Real-time Monitoring of Threats
Through the cyber threat intelligence platform, real-time insights into emerging threats can be gained, and thus, one will stay updated on the latest vulnerabilities, exploits, and campaigns. It keeps track of all observations made on the threat landscape in real-time. This not only streamlines response to new challenges as they surface but also enhances Cyber Awareness within the organization. By staying informed and vigilant, teams can respond quickly and effectively to attacks, ensuring that security measures are always up to date and aligned with the evolving threat environment.
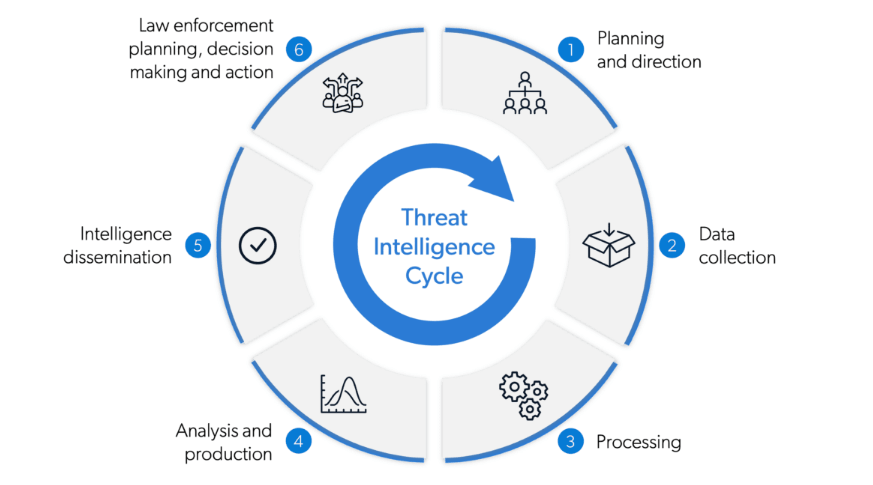
TIP: Threat Intelligence Platforms
Threat Intelligence Platforms (TIPs) are Specific, centralized solutions that collect, aggregate, analyze, and share threat data from various sources. Tips provide organizations with actionable intelligence to enhance their security operations; some specific areas include IOCs, understanding the patterns of attacks, and even sharing cyber threat intelligence with other stakeholders.
Security Information and Event Management (SIEM) Systems
SIEM systems gather and examine data about security events from a company’s network. When linked with cyber threat intelligence feeds, they can be correlated in real-time against known IOCs to alert about potential threats and provide a historical data source for forensics and incident investigations.
Open Source Intelligence Tools
OSINT tools gather open-source data publicly available through social media, forums, and websites to obtain information on emerging threats. OSINT is also a good intelligence-gathering resource for understanding threat actors’ motives, tactics, and attack targets.
Threat Feed Aggregators
They aggregate threat intelligence from multiple sources, including commercial cyber threat intelligence vendors, open-source repositories, and industry-specific sources. Aggregators provide security teams with a holistic view of threats facing their industry and region.
EDR Tools End
EDR tools will monitor and collect data in real time from endpoint devices such as laptops, desktops, and even servers to detect suspicious activities and respond in a timely manner. The integration of EDR tools into cyber threat intelligence empowers organizations to recognize malicious activities in real-time and block them accordingly.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How to Select the Right Threat Intelligence Platform
- The system should be integrated with multiple data sources, including, but not limited to, commercial threat feeds, open-source intelligence, and internal logs.
- The system should allow for real-time data analysis so that threats can be identified in real-time and responded to promptly.
- Dashboards of the application should be customizable enough to highlight pertinent information and metrics relevant to different teams, including insights into potential Payloads used in cyber attacks.
- The platform should support collaboration between security teams, stakeholders, and external partners.
- The system needs to scale up with the growth of the business and the changing threat landscape.
- The TI platform should integrate seamlessly with current security tools, including SIEMs, firewalls, EDR solutions, and any kind of security device. This means the threat intelligence gathered is used across the organization’s security infrastructure.
- You should select a solution that is flexible for your organization’s specific needs and scales with its growth and evolution, as well as the threat landscape.
Top Threat Intelligence Tools and Platforms
MISP is an open-source cyber threat intelligence platform for distributed sharing, storage, and correlating structured threat information. It also allows organizations to collaborate in sharing indicators of compromise (IOCs) and tactics used by threat actors. Anomali is a commercial threat intelligence platform for detecting, investigating, and responding to cyber threats. It integrates with existing security tools, providing actionable intelligence feeds, advanced analytics, and real-time threat monitoring. In cyber threat intelligence, ThreatConnect delivers an integrated and comprehensive platform using a variety of sources of data for advanced analytics, visualization, and collaborations. This helps organizations to manage cyber threats efficiently, investigating them in the right manner and responding.
This cloud-based threat intelligence is provided by IBM X-Force Exchange, offering data related to threats, IOCs, vulnerabilities, and attack patterns that organizations can use and share insight while collaborating with the global security community. AlienVault OSSIM stands for Open Source Security Information and Event Management; it’s an open-source SIEM platform that operates on a free-of-charge model, integrating threat intelligence feeds with event management and the ability to monitor real-time and respond to incidents. OpenDXL is the Cyber Security Training Courses intelligence platform developed by McAfee and can enable organizations to automate and orchestrate security workflows. It integrates threat intelligence with security tools for real-time threat detection and response. VirusTotal is free, based on an online platform that scans suspicious files and URLs for security threats. It collates information from several antivirus engines and Tools and Platforms of Threat Intelligence sources, thereby generating a comprehensive view of the files and URLs. Splunk is an SIEM tool hugely used by analytics to monitor, detect, and respond to threats against cyber. It has multiple cyber threat intelligence feeds where security teams can correlate data and see anomalies across their network.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Best Practices for Leveraging Threat Intelligence Tools
Data Quality
Ensure that your threat intelligence data is fresh, relevant, and current. By ensuring that sources are authenticated, feeds are cross-correlated, and threat intelligence stores are frequently updated, decisions will become more informed.
Collaboration and Information Sharing
Threat intelligence is only as effective as it is shared. Promote collaboration across teams, sectors, and even with other external organizations to share information that may be used to mutually strengthen and defend against cyber threats. This collaborative approach is particularly crucial when addressing risks such as Cyber Defamation, where malicious actors may spread false or damaging information to harm an organization’s reputation.
How to Bring Threat Intelligence into Security Operations
Cyber threat intelligence should now be incorporated into the entire cycle of security operations: detection and response, proactive defence, and recovery. All forms of threat data should be easily available to allow security teams to readily access them in making proper decisions.
The Future of Threat Intelligence
Artificial intelligence or machine learning will absorb the future of threat intelligence. AI and ML will automate threat detection with predictive analytics, improving a deeper understanding of the attack patterns. Automation will make the ingestion, correlation, and response to threat intelligence data easier. This helps security teams not carry out mundane tasks, as automated workflows will speed up incident response times. In an ever-growing world of more and more cloud-based corporations, the foundation of this cyber threat intelligence will represent the core of securing the distributed environment and ensuring the detection and mitigation of threats at all endpoints and services.
As organizations continue to embrace digital transformation and expand their digital footprint, the need for scalable and agile cyber threat intelligence solutions becomes even more critical.AI and ML will enhance the speed and accuracy of threat detection and enable continuous learning, allowing systems to adapt to new and previously unknown threats. This is particularly valuable in the realm of Cyber Media, where emerging threats can quickly spread across social platforms, news outlets, and digital channels. With the ability to analyze vast amounts of data in real-time, these technologies will provide deeper context and better risk assessment, helping security teams prioritize threats based on potential impact. As the threat landscape grows more complex, the fusion of threat intelligence with AI and ML will become indispensable for building a proactive, resilient cybersecurity framework that can respond swiftly to evolving challenges.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Threat intelligence platforms and tools play a significant role in the development of cybersecurity; they offer organizations real-time insights into potential threats. Of course, with the right tools and integration into existing security infrastructures, the right to effectively detect, prevent, and respond to cyberattacks will be made possible. As Cyber Security Training Courses evolve, so will the role that Tools and Platforms of Threat Intelligence will play in building resilient cybersecurity defenses. With the evolution of the threat landscape, cybersecurity strategy must catch up with increasingly sophisticated and targeted attacks, necessitating an understanding of emerging advanced threats against evolving sophisticated and targeted attacks. According to Corey Nachreiner, CTO at WatchGuard Technologies, “Putting cyber threat intelligence into an organization’s security ecosystem is both situational awareness and proactive defense enabled.” Advanced analytics, machine learning, and automation can be very instrumental in enabling security teams to understand emerging threats quickly. These technologies can shorten the response time and may prevent the threat from causing damage in the first place. In an ever-changing threat environment such as this, these critical tools will be instrumental in helping to maintain a robust, adaptive, and resilient cybersecurity posture.





