
- What is ethical hacking?
- Is WhatsApp hackable?
- Common Vulnerabilities in WhatsApp
- Importance of WhatsApp Security
- Best Practices for WhatsApp Security
- Ethical Hacking Techniques for WhatsApp
- How to Protect Your WhatsApp Business Account?
- Conclusion
The most widely used messaging service today is WhatsApp, with more than 2 billion users in all. With this high usage for personal, professional, and business communications, securing WhatsApp accounts and their data has become a priority. WhatsApp provides end-end encryption on the messages exchanged by the users, but no system is foolproof. Ethical hacking techniques play a critical role in the identification of vulnerabilities, improvement of Ethical Hacking Course, and prevention of malicious attacks. This article follows a discussion on the role of ethical hacking in improving security on the platform, the common vulnerabilities relating to WhatsApp, and the techniques by which ethical hackers protect users’ data.
Are you curious to know more about Ethical Hacking Techniques? Take advantage of our comprehensive online Ethical Hacking Training!
What is ethical hacking?
This has resulted in ethical hacking, which means probing and testing systems to find their vulnerabilities with permission and improve security deliberately. Contrasting to a malicious hacker, an ethical hacker, sometimes known as a “white-hat” hacker, is paid to find system weaknesses before the malicious hackers use them for their evil purposes. Ethical hacking could be described as the testing of software, systems, or networks, applied with the same tools and techniques Vulnerability Management thieves use but in a controlled, legal manner. The motivation is to find and report those vulnerabilities so that the system can be reinforced and secured. Ethical hackers, in the context of WhatsApp security, try to find loopholes or vulnerabilities in WhatsApp’s app, infrastructure, or interaction with external systems to help developers fix them before malicious hackers exploit such weaknesses.
Is WhatsApp hackable?
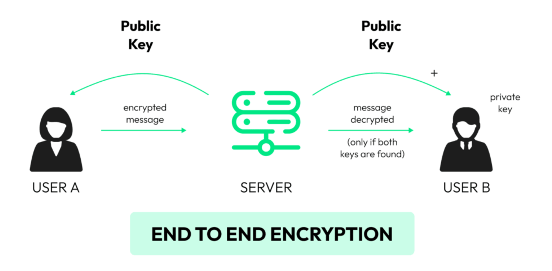
WhatsApp is a cross-platform messaging Web Application Security owned by Facebook and created by some of the most talented developers. End-to-end encryption ensures only the sender and receiver can see what is being communicated. It routinely resolves user-reported security vulnerabilities. Developers cannot control certain things. For example, if you share your email password with someone and they misuse it, this is not considered hacking. But even in this situation, many claim to have been hacked. Even when there is the availability of a robust cryptography and security mechanism, WhatsApp is not free from different vulnerabilities that ethical hackers are helping to identify and solve.
Enrol in ACTE’S Ethical Hacking Training if you want to become an expert in the Ethical Hacking field and have a prosperous career.
Common Vulnerabilities in WhatsApp
Even with robust encryption and security measures, WhatsApp still faces various potential vulnerabilities that ethical hackers help identify and address. Here are some common vulnerabilities
- Account Hijacking: An attacker can hijack the control of a WhatsApp account, usually secured through weak authentication processes or phishing techniques. This can include intercepting and gaining control of a person’s messages by scamming a new SIM card issued by a mobile carrier through SIM swapping.
- Man-in-the-Middle Attacks (MITM): Even though WhatsApp encrypts messages, a man-in-the-middle attack is always possible when an attacker gets control of the network or intercepts communication. This may be when one connects to an insecure public Wi-Fi network. Here, the hacker can easily intercept unencrypted traffic, although WhatsApp uses encryption to counter this problem.
- Insecure Wi-Fi Networks: The connection to public but unsecured public Wi-Fi networks is Database Security risk to the users of WhatsApp. Without proper encryption, either at the network level or device level, attackers sniff the traffic and capture sensitive data like login credentials or messages.
Importance of WhatsApp Security
The most common concern is communication, which occurs when people exchange everything from casual discussions to critical personal and financial facts. WhatsApp is an appealing target for cybercriminals who try to hack accounts for identity theft, fraud, or spying. Therefore, WhatsApp security is a great challenge in safeguarding this sensitive data and ensuring the user’s privacy is well maintained. To address such concerns, Ethical Hacking Course play a crucial role in educating users and organizations about best practices to protect their communication and data. If the application uses end-to-end encryption, it means that the message and the transmission are protected. However, an attacker could bypass all these protections if they can access a user’s device or exploit other vulnerabilities. It is here where Ethical Hacking Techniques becomes relevant; active testing of the app’s security may help strengthen it against future attacks.
Best Practices for WhatsApp Security
Implement some best practices to safeguard your accounts besides the efforts of ethical hackers:
- Enable two-factor authentication (2FA):An added layer of security makes access more difficult for unauthorized users.
- Regular Updates: Use WhatsApp regularly to ensure it is updated to take full advantage of security patches and software.
- Secure Your Phone: Use powerful passwords and adopt biometric verification through fingerprint or facial recognition to enhance the Web Security of the device itself.
- Avoid suspicious links: They might be phishing attempts or malicious links within a message.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Ethical Hacking Techniques for WhatsApp
Ethical hackers use different techniques to strengthen WhatsApp security. These techniques identify potential vulnerabilities that malicious hackers can exploit and provide a defence mechanism for checking a platform.
- Penetration Testing: Penetration testing, sometimes known as “pen testing,” is a technique ethical hackers use to simulate real-world cyberattacks. Testing WhatsApp’s infrastructure would simulate the hacker looking for weaknesses in penetrating the system. Pen tests can identify potential flaws in authentication mechanisms, encryption protocols, or API interactions. Pen testers may also attempt social engineering attacks, such as phishing or pretexting, to see if WhatsApp’s defences can withstand humans’ persuasion powers. Results from tests inform methods to correct or enhance the platform.
- Phishing Simulations: Still, phishing ranks among the effective methods through which attackers get hold of personal data, such as with WhatsApp accounts. Ethical hackers test the app is ability to detect fraudulent login attempts or suspicious links through phishing simulations. Ethical hackers design fake WhatsApp login pages or malicious attachments in this process to check how users react and if they become victims of phishing attacks. Phishing attack simulation: This would allow ethical hackers to determine which areas are devoid of Cyber Awareness on WhatsApp and, therefore, what user education or changes to the system level can be implemented to minimize successful phishing.
- Vulnerability Scanning Tools: Vulnerability scanning tools are software programs that automatically scan computer systems for known vulnerabilities, such as out-of-date software, misconfigured settings, and weak security protocols. Ethical hackers utilize them to probe WhatsApp’s applications and servers so that any known vulnerabilities are patched before malicious actors can exploit them.
- Social Engineering Testing: Social engineering attacks are specifically designed with the intention that their victims disclose confidential information. In the context of WhatsApp security, this could be by forcing users into divulging their credentials or giving somebody unauthorized access. Most ethical hackers do social engineering testing to know how susceptible users are to it. Often, this may be masked by impersonation of someone a victim trusts, like a friend or a technical support representative, so that confidential information may be collected.
How to Protect Your WhatsApp Business Account?
Unfortunately, data breaches occur very often. WhatsApp is not an exception, either. News about data breaches can become a reputational threat and lead to huge financial losses.But do not worry! Here is how you can keep your WhatsApp Business account secure and your customers happy.
- End-to-end Encryption: End-to-end encryption means that only you and your customers will ever see a message. However, incorporating a Demilitarized Zone within your network infrastructure can add an extra layer of security, ensuring that sensitive communication remains protected from potential external threats.
- Two-Step Verification:Two-step verification makes it difficult for unwanted people to access your WhatsApp Business account. This necessity for a second verification step is a milestone in protecting customers’ data from hacking and misuse, thus securing the brand.
- Control Account Access: Can people use your WhatsApp Business account? Well, only some get the keys! Limit the access only to team members who require access. Stay in charge of your channels. This reduces the chances of accidental leaks or someone sharing information they shouldn’t.
- Regular Backups: Scheduled backups create a safety net. This assures that your data will be recovered due to technical glitches and keeps the business running smoothly.
- Customer Privacy Training:Tell your team how to handle all this business data safely. In this way, your team learns to handle the customer data responsibly, reducing the chances of accidental leaks. After all, knowledge is power!
Get interview-ready with our collection of Ethical Hacking Interview Question & Answer. Equip yourself with the knowledge to impress potential employers!
Conclusion
As the world changes daily with threat permutations in digital security, ethical hackers are needed to identify vulnerabilities. In the case of an application, as widely used as WhatsApp, data must be protected more than ever. Testing WhatsApp’s security systems and infrastructure helps build it against phishing, hijacking, and man-in-the-middle attacks.Robust security features have been introduced in WhatsApp, yet ethical hacking techniques ensure that these are re-evolving with the help of times of new and emerging Ethical Hacking Course threats. In this sense, users, too, must remain vigilant through the best security practices. It is for this reason that what is needed from both ethical hackers and users is to support each other in keeping security and privacy intact in the critical tool of communication.





