
- What is an Active Attack?
- What is a Passive Attack?
- Difference between Active and Passive Attacks
- Types of Active and Passive Attacks
- Examples of Active and Passive Attacks
- Conclusion
Active attacks involve deliberate actions by attackers to alter, disrupt, or damage a system or its data, such as injecting malware, modifying data, or causing service outages. Active attacks involve deliberate actions by attackers to alter, disrupt, or damage a system or its data, such as injecting malware, modifying data, or causing service outages. These attacks directly affect the system’s functionality and can result in significant harm. In contrast, passive attacks are more covert, where attackers silently monitor or intercept communications to gain unauthorized access to sensitive information without affecting the system’s performance. To better defend against both types of threats, individuals and organizations can benefit from enrolling in Cyber Security Training Courses, which provide the knowledge and skills needed to identify, prevent, and respond to such attacks effectively. While active attacks cause immediate disruptions, passive attacks focus on gathering intelligence, often leaving no trace of the intrusion. Both pose serious security risks, but active attacks are typically more direct and damaging.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
What is an Active Attack?
Attacks, wherein hackers try to govern or regulate the content material of communications or facts, are referred to as lively assaults. These cyberattacks, in opposition to cyber security, jeopardize the system’s integrity and authenticity. These threats can harm structures and tamper with facts. Organizations using cloud platforms like AWS EKS need to be especially vigilant against such attacks, as they can compromise not only the system’s data but also the scalability and security of containerized applications deployed within their infrastructure.
Imagine Tom and Jerry are friends. Tom is sending a letter to Jerry. So, earlier than the letter reaches Jerry, Rachel takes the letter and alters the message. Now, what Jerry gets isn’t the facts despatched through Tom.Here, the facts have been altered through a 3rd party. This is a capability hazard because the facts despatched through Tom changed into touchy and crucial. If Jerry isn’t smart sufficient to perceive the alteration inside the message, he would possibly continue with the changed facts. This can result in a variety of troubles and is a severe hazard to any organization.
So, that is the solution for what’s a lively assault?Sometimes, the sufferers are notified approximately the assault. This is a bonus due to the fact as soon as an assault is identified, it’s miles feasible to repair the statistics in addition to the system. So, precedence is given to detecting such assaults instead of stopping them. Active assaults, such as Phishing Attacks, may be decreased through the usage of One-Time Passwords (OTP) to authenticate the communication process between entities. It is feasible to create a random session key that is both effective and valid for a single transaction, enhancing security by ensuring that even if a Phishing Attack occurs, the attacker cannot reuse credentials or session information. OTPs add an additional layer of protection, making it difficult for malicious actors to exploit intercepted data or impersonate legitimate users in ongoing sessions. This makes it extra hard for the attacker to switch statistics after the consultation has expired.
What is a Passive Attack?
- It is the kind of assault wherein a third-party attacker intercepts the messages between entities and replicates the content of these messages with malicious intent. This is commonly known as a Man-in-the-Middle (MITM) Attack.
- To mitigate such risks, Cyber Security Training Courses can help individuals and organizations understand how to identify and protect against such threats, including encryption methods, secure communication protocols, and best practices for secure data transmission.
- The goal of those varieties of assaults is to acquire touchy and personal information. Neither do those assaults regulate the information nor do they ruin the device.
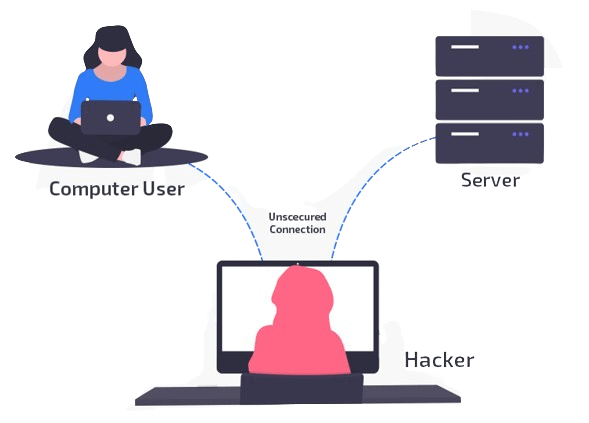
- Let me simplify the process. In the earlier example, Rachael altered the message between Tom and Jerry. Here, Rachel no longer regulates the message.
- Rachel without a doubt observes the content material of the message between Tom and Jerry, so that she is aware of the touchy statistics this is being conveyed among Tom and Jerry.
- In other words, Rachel invaded the privacy of Tom and Jerry. Hope this solutions the question, what’s a passive assault?`
- One of the viable shielding measures that may be taken to save you from those varieties of passive assaults is the usage of encryption strategies for touchy statistics so that they stay unreadable to outsiders.
- Such passive assaults also can be averted via way of means of now no longer the usage of online structures to percentage personal and touchy statistics.
- Masquerade: It is a sort of assault wherein one person acts or pretends to be someone else and alters the system and data. This type of attack is commonly known as Impersonation or Identity Fraud. To mitigate the risks associated with such attacks, organizations can implement a Cloud Security Service.
- Repudiation: This assault may be achieved with the aid of using both the sender and the receiver. The sender or receiver would possibly ship or acquire a selected message, however, they decline this reality later on. Let us apprehend it surely with an instance.
- Replay: Suppose Julie is a better authority legitimate to send a message to Mark. John captures Julie`s message or content material and sends it to Mark to persuade Mark that John is the authority. Now, in this situation, Mark could interpret John as legitimate. This is called replay attack.
- Denial of Service or Fabrication: In this sort of assault, the intruder prevents all sorts of communique among entities. All communications addressed to a certain vacation spot may be disabled with the aid of using an entity. Another sort of carrier denial is whilst an entire community is disrupted, both with the aid of deactivating it or with the aid of flooding it with messages to go to pot performance. An easy instance of this form of assault is proven in the picture below. Emily is sending a message to Ruby. Rob, the cracker, overloads the server with the aid of sending fake statistics and requests. This can affect the rate of data modification at which Emily`s message is despatched to Ruby.
- Traffic Analysis: Due to the elevated lively assaults and passive assaults, the encryption of statistics has been the latest savior. When statistics are encrypted, an outsider can not study the content material of the messages. The intruder might take advantage of this information to predict what kind of communication is taking place. This is called traffic analysis. To defend against such risks, Network Penetration Testing can be employed. Penetration testing helps identify vulnerabilities in a network, including areas where traffic could be intercepted or analyzed.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Difference Between Active and Passive Attacks
An energetic assault includes the attacker actively interfering with or manipulating the device, regularly to inflict harm, change information, or disrupt services. These assaults consist of sports like denial of service (DoS), man-in-the-center assaults, and changing transmitted information. The purpose is to extrude the regular operation of a community or device, probably main to information loss, unauthorized access, or device downtime. In contrast, a passive assault happens when an attacker only monitors or eavesdrops on network traffic without editing or disrupting it. The attacker’s purpose is to acquire information, such as sensitive data, passwords, or encryption keys, often without the knowledge of the victim. To defend against such threats, organizations can deploy Intrusion Detection Systems. These systems can help detect suspicious activities and unauthorized access attempts in real-time, enabling quick responses to potential passive attacks and minimizing the risk of sensitive data being compromised.Passive assaults are tougher to hit upon due to the fact they no longer immediately regulate the device, however, they nonetheless pose extensive threats to confidentiality and privacy. Examples consist of site visitors’ evaluation and unauthorized information interception in session hijacking. While each varieties of assault threaten security, energetic assaults tend to be greater adverse and disruptive, whilst passive assaults recognition greater on stealthy information gathering.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Types of Active and Passive Attacks
Want to Learn About Cyber Security? Explore Our Cyber Security Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Active and passive attacks pose significant threats to organizations, with the potential to cause widespread damage. Active attacks, which involve an attacker actively engaging with a system to alter or disrupt its normal operation, can lead to data corruption, unauthorized access, or service disruptions, directly compromising the integrity and confidentiality of the organization’s resources. On the other hand, passive attacks involve the attacker intercepting and eavesdropping on communications or systems without directly altering them, but they can still lead to the unauthorized collection of sensitive information, putting the organization at risk of data breaches, espionage, or other forms of exploitation.
Both types of attacks represent critical vulnerabilities that can undermine the security infrastructure of any organization, leading to financial loss, reputational damage, legal consequences, and, in some cases, even the collapse of the organization’s operational framework. Given their potential for widespread harm, it is essential for organizations to adopt proactive cybersecurity measures, stay vigilant, and implement robust countermeasures to protect against such threats. Enrolling employees in Cyber Security Training Courses can be a key part of this strategy. These courses help build awareness and provide the necessary skills to recognize and defend against attacks, ensuring that all team members are equipped to protect sensitive data and respond effectively to potential threats.





