
- RSA Algorithm: What is it?
- RSA Encryption Algorithm
- Application of RSA
- Possible Attacks on RSA
- Advantages of RSA
- Types of RSA
- Conclusion
The RSA algorithm relies on mathematical principles taken from the area of number theory, specifically properties of big prime numbers and modular arithmetic. Decryption rsa algorithm network securityis based on making it impossible for anyone with a public key to factor a product of two large primes into an impossible task, so recovering the private key is practically impossible. RSA encryption decryption is adaptable in its application, such that it can be installed on anything from secure Web Application Security browsing to HTTPS to emailend to end encryption, digital signatures, and even secure file transfers. Its wide usage and success over time made it the backbone of modern cybersecurity frameworks.
RSA Algorithm: What is it?
Rivest, Shamir, and Adleman first presented the RSA algorithm (Rivest Shamir Adleman) as an asymmetric encryption technique in 1978. This algorithm uses both private and public keys. The foundation of the RSA in cryptography is the ease with which huge integers may be found in Cybersecurity Training and multiplied, but the difficulty in determining the factor of their product.According to mathematical studies, it would take an attacker almost 70 years to figure out the value of a key with 100 digits. Selecting and creating the public and private keys is arguably the most challenging aspect of the c code for rsa algorithm.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
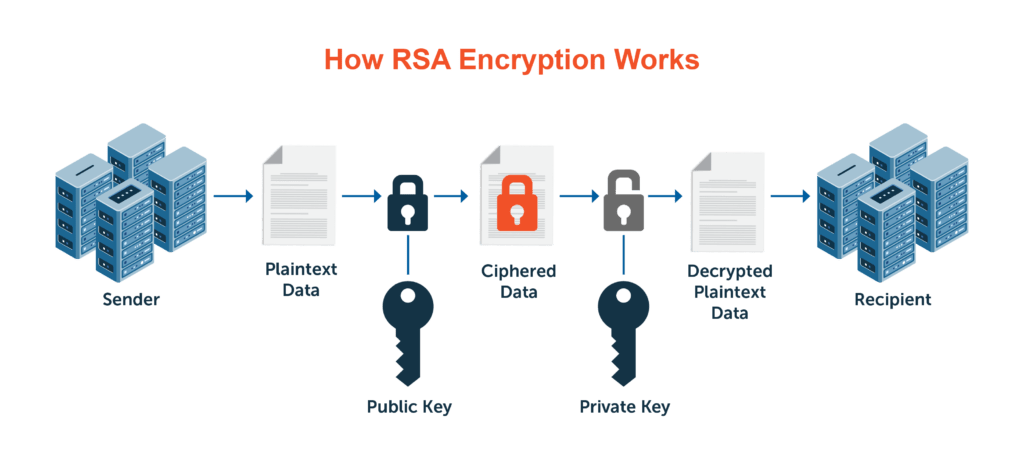
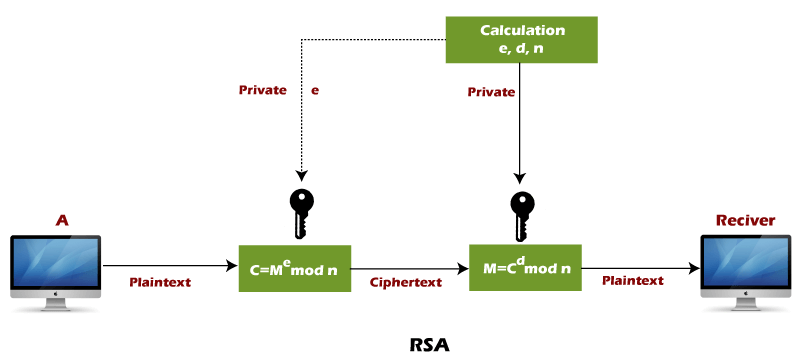
RSA Encryption Algorithm
In the RSA encryption algorithm, a private key, distinct from the public key and known only to the recipient, is used for decryption. The public key would be the product of two huge prime numbers. The public is made aware of such a product. There is no known way to determine the prime factors of such numbers, and decryption would require knowledge of the number’s two prime factors. This implies that the private Keylogger can only be generated by the same individual who created the public key.
Let’s examine the steps in the RSA:
- Any two big prime numbers, such as A and B, will do.
- The product of A and B can then be found, say N. N = A*B.
- For end to end encryption, you must choose a public key, let’s say, E. You must ensure that (A-1) and (B-1) do not depend on this key.
- You can now choose the private key, say D, for decryption. The private key should match this equation: Mod (A-1)*(B-1) = 1 (D*E)
- This formula can be used to determine the ciphertext from the plaintext: Ciphertext = E mod N for plaintext
- The recipient should receive the ciphertext after it has been created.
- This equation can be used to decrypt the plaintext from the ciphertext: * Ciphertext^D mod N = Plaintext
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Application of RSA
- Securing Internet Browsing: In addition, SSL/TLS protocols deploy decryption rsa algorithm to connect browsers with servers over secured connections. When a visitor visits the Web Security, a server starts sending the user’s public key so that he encrypts session keys. Thus, all communication is encrypted.
- Email Encryption:The PGP and S/MIME protocols employ RSA to encrypts emails so that the content is readable only by the recipient.
- Digital Signatures: This implies that RSA encryption decryption is used to generate digital signatures that ensure message integrity and authenticity. The sender would use his private key to sign the document, and the recipient would use the sender’s public key to verify the signature.
- Data Integrity: RSA can be implemented to safeguard data integrity because hash values are generated; the ability of the receiving party to verify that the message has not been altered when a signature is made through a hash of the information signed using a private key.
- Secure File Transfer:The implementation of RSA on several file transfer protocols; for example, SFTP transfers files over unsafe networks, ensuring that the accessed files belong only to them.
- Virtual Private Networks (VPNs): RSA is utilized in VPNs to authenticate users and allow the formation of secure encrypts links between devices connected using the Internet.
- Blockchain and Cryptocurrencies:Blockchain technologies will, therefore, use decryption rsa algorithm to secure and digitally sign transactions so that those transactions will be certain of being made by whom and who the parties involved in the transaction are authentic.
- Authentication Protocols: Authentication protocols typically include RSA to ascertain identities, ensuring that those with legitimate identities gain access to the information deemed sensitive within systems, just like two-factor authentication, for instance.
Possible Attacks on RSA
- Attack using short messages
In short message attacks, it is typically believed that the attacker is already familiar with some plaintext messages. An attacker could now attempt to encrypt the plaintext blocks using the information they know. To stop a short message attack, RSA encryption bits are padded.
- Attack by bicycle
In a cycling attack, the opposite activity occurs. The attacker assumes a few variants of the ciphertext. If this assumption is correct, they can attempt to use the ciphertext to generate the plaintext by reversing the procedure.
- Attack by Factorization
In a factorization attack, the attacker can pose as the key’s owners and circumvent the system’s network security by using the information to decode sensitive data. The attackers target an RSA cryptography library, which generates the RSA key. Because they know the target’s public key, the attackers can access the private keys of different Database Security tokens, motherboard chipsets, and smartcards.
Advantages of RSA
Based on the mathematical problem, RSA encryption decryption relies on factoring large prime numbers being difficult. Hence, for any sufficiently large primes chosen (typically of 2048 bits or greater), it remains secure from the capability of the computing machines presently available. No Shared Secret An rsa algorithm does not have an equivalent symmetric encryption method whereby secret keys must be sent for RSA encryption and decryption procedures, and it requires simple and easier management of keys over a distributed system. Authentication and Integrity. Although the use of a digital signature allows a user to see that the message he has sent is genuine, a digital signature could prove the authenticity of that document, especially during secure transmissions or transactions on the network. RSA is implemented in various protocols and standards, including SSL/TLS for safe web browsing, PGP for email end to end encryption, and many authentication protocols.
The widespread use of RSA implies extensive support across platforms and applications.Decryption rsa algorithm is used for end to end encryption, digital signatures, key exchange, and secure communications. Its versatility makes it suitable for various Cybersecurity Training Courses needs in different environments. Proven Track Record: RSA has been developed since the late 1970s and has withstood extensive scrutiny and analysis. Its longevity and trust received from the security community support its credibility. Operations Simplicity: All the basic operations involved by RSA (multiplication, exponentiation, and modular arithmetic) are very basic, making it easier to implement in software and hardware mediums. Since access alone does not compromise the network security for anyone to acquire a copy of the public key, key distribution is markedly easier than symmetrical schemes that demand the distribution of secret keys. Already on work: whereas quantum computing-based Shor c code for rsa algorithm may break the system RSA, which has proved very flimsy, it still exemplifies that malleability can change using a quantum-proof variety.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Types of RSA
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions. Equip yourself with the knowledge to impress potential employers!
Conclusion
The RSAis an important cornerstone in the heart of modern cryptography how to secure communication digitally with the protection of secret or sensitive information. Using the scheme of public and private key pairs it’s a possible method for secure exchange without knowing a shared secret that simplifies handling keys in the great variability of applications. However, over the decades, rsa algorithm has proved firm Cybersecurity Training based on the mathematical difficulty of factoring large prime numbers. Despite challenges posed by advancements in computational power and potential threats by quantum computing, RSA encryption decryption remains the adopted mainstream in protocols like SSL/TLS and email RSA encryption for digital signatures.





