
- What is CISSP?
- What Does CISSP Cover?
- CISSP Domains
- CISSP Exam
- Benefits Of CISSP
- Future of CISSP
- Conclusion
One of the most prestigious credentials any information security professional can hold is CISSP. It validates one’s ability to design, implement, and manage a cyber security certifications program recognized by organizations across industries worldwide. This certification also ensures proficiency in creating secure Sandbox Environment, where security professionals can safely test and analyze potentially malicious software or conduct penetration testing without risking harm to production systems. Success in passing the CISSP examination results from arduous preparation, hard work, and carefully crafted study strategies for the aspirant. It highlights six tested study techniques for passing the CISSP exam and performing well in your career, including penetration testing and cybersecurity frameworks.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
What is CISSP?
CISSP stands for certified Information Systems Security Professional, a certification that shows how well a person can design, implement, and run a cyber security certifications program. The Cybersecurity Training Courses certification was established by the International Information Systems Security Certification Consortium, ISC2, to ensure the computer security professional has standardized knowledge of the field. cissp boot camp is an accreditation qualification for senior and director-level managers in information security. Employers highly value it, and it represents an important step in a career path toward director and board-level management positions.
What Does CISSP Cover?
The CISSP (Certified Information Systems Security Professional) is one of the most sought-after information security credentials provided by ISC². This is for professionals who work and manage security programs for organizations. These experts are also equipped to handle emerging threat intelligence like Cyber Defamation, which involves the use of digital platforms to spread false and damaging information about individuals or organizations. It evaluates a candidate’s ability to plan, carry out, and oversee top-notch cyber security certifications initiatives. The certification is based on the Common Body of Knowledge, which provides an all-encompassing set of principles, frameworks, and best practices related to security issues that span eight core domains. The domains cover all phases of information security, from risk management to cryptography and security testing.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
CISSP Domains
Security and Risk Management
This is one of the CISSP domains, encompassing around 15 per cent of the exam. It is one of the core domains of the CISSP exam that can provide a comprehensive summary of the information systems management needed to be known.
Asset Security
This CISSP domain is about protecting resources. It covers around 10 per cent of the CISSP exam. Asset security concerns information administration topics, which include information ownership. It integrates numerous roles’ skill sets concerning data management, ownership, processing, privacy, and usage limitations.
Security Architecture and Engineering
This CISSP domain requires the application of principles in IS architecture design. It makes up almost 13 percent of the CISSP exam and has a broad scope covering a few major concepts of data security. Candidates on safety engineering procedures, models, design regulations, vulnerabilities, database security, cryptosystems, and cloud systems are examined.
Communication and Network Security
This cissp boot camp domain concerns the process of developing and securing network security. It also includes practical knowledge of tools and techniques used to identify vulnerabilities, such as the Google Hacking Database. Applicants must answer questions about network design, communication policies, separation, transmission, and wireless communications.
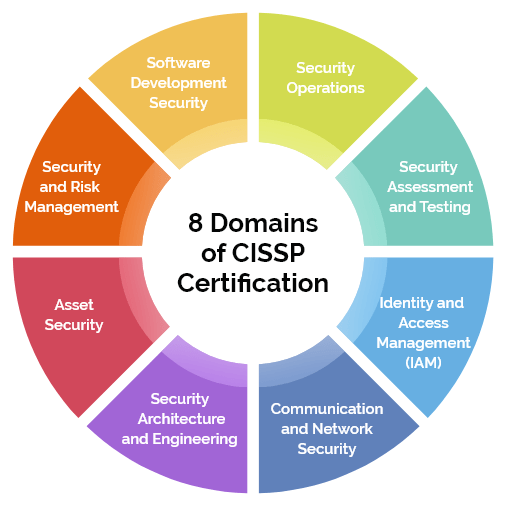
Identity and Access Management (IAM)
This CISSP domain enlightens attacks that manipulate the human element to access information and ways of detecting people who have the right to log on to servers and access data. It covers about 13% of the CISSP exam and the concepts of phases, multifactor authentication, and credentials.
Security Assessment and Testing
This is the CISSP domain that provides tools and techniques that check the security of processes and determine weak areas, coding and design faults, vulnerabilities, and weak spots that are left unreformed by policies and systems. This is one of the smallest parts of the CISSP exam and amounts to about 12 percent.
Security Operations
This CISSP domain involves fundamental concepts, audits, incident management, and disaster recovery. It constitutes about 13 per cent of the CISSP exam. It is a wide-ranging and useful field that includes firewalls, sandboxing, intrusion prevention and detection tools, digital forensics, and probes.
Software Development Security
This CISSP domain focuses on implementing security regulations on software systems inside the environment that the security data system professional is responsible for.
CISSP Exam
CISSP Examination An applicant for cissp boot camp status sits the examination, which lasts six hours and consists of 250 MCQs and complex, innovative questions to test the knowledge and understanding within the eight Cybersecurity Training domains security and risk management, identity software development security, asset security, communications and network security, engineering, access control, security testing and evaluation, and security operations. Scores are scaled; an applicant has to score 700 or better on a scale of 1,000 to qualify for the credential.
The CISSP exam is available in English, Chinese, Korean, French, German, Brazilian Portuguese, Spanish, and Japanese. The CISSP exam price is about $699; however, the actual cost and tax will differ according to the site where you will sit for the exam. One can reschedule one’s attendance to the certification exam for a $50 fee, but if you cancel an exam, you incur a cost of $100.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cybersecurity Expert Masters Program Training Course .
Benefits Of CISSP
Global Acceptability
CISSP is the gold standard for information security professional certificate worldwide. It increases a person’s credibility, and organizations around the globe accept it as a benchmark for excellence.
Leader Opportunities
The CISSP provides exhaustive coverage of security domains, preparing professionals for leadership and enabling them to contribute to strategic and managerial aspects of information security. People with the CISSP are usually tasked with shaping and implementing organizational security policies of threat intelligence.
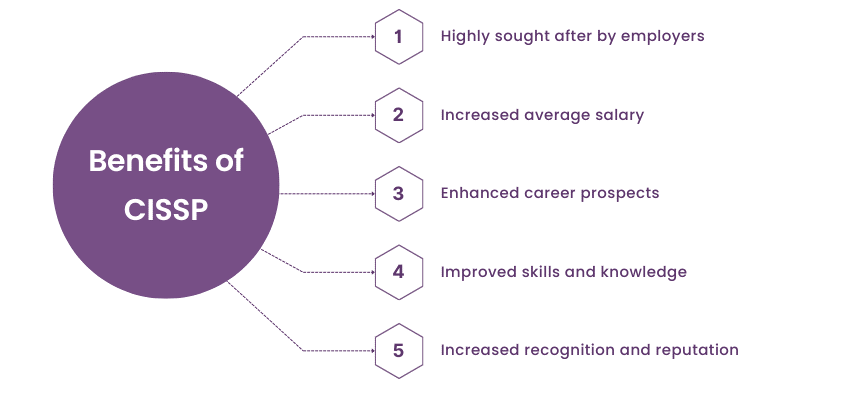
Labour Demand
With an estimated 5.5 million global cyber security certifications workforce, the CISSP meets a growing demand for expert professionals in certified scrum master, where certification holders are highly sought after in the industry. Beyond technical skills, these professionals also play a crucial role in promoting Cyber Awareness within organizations.
Certification Requirement
Significantly, 72% of cyber security professionals are certified scrum master as required by their employers, and thus, CISSP certifications are an important requirement in the labour market. CISSP is a professional certificate achievement that often precedes a promotion to leadership or a key position in the organization.
Career Opportunities
Even trained professionals have positive salary gains. CISSP, a comprehensive program that fits strategic roles in information security, offers competitive pay to certified scrum master professionals.
Future of CISSP
The CISSP certification has a promising future. Here’s why it matters and how it will continue to be useful in the ever-changing world of cybersecurity. The necessity for more robust information security measures will only increase as the danger level rises. The CISSP will remain a crucial professional certificate, enabling them to meet evolving difficulties. The CBK of CISSP is updated with time to accommodate the trends and information security technologies. For instance, Google Dorking is a technique that security professionals use to find hidden or sensitive information on websites using advanced Google search queries. Thus, it keeps the certificates of the professionals relevant to their work, and those who hold them keep up to date. With the increased emphasis on cybersecurity across all spheres of industry, CISSP-professional certificate can expect a higher demand within the job market. Increased job opportunities and roles within the sector will arise in threat intelligence, but further career advancement will depend on the certification holders. Great emphasis is also put on continual learning and professional development for a future in CISSP. The demand for continuing professional education credits will ensure that professionals stay atop current trends, techniques, and best practices in securing information.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions. Equip yourself with the knowledge to impress potential employers!
Conclusion
The CISSP domains outline a broad framework to understand and manage the multi-dimensional nature of information security. The areas covered in each domain encompass critical security topics that, taken together, empower organizations to protect their data, systems, and networks against a diversified range of threat intelligence . A penetration tester should know how each domain relates to the activity. Penetration testing falls under most of these domains, especially in security assessment, network security, access management, and software security. Therefore, penetration testers who understand the cissp boot camp domains will have a better view of the larger context of their work and the broader security landscape. Familiarity with the Cybersecurity Training domains gives penetration testers an understanding of how pieces of an organization’s security posture fit into an overall security structure, For instance, once penetration testers grasp security and risk management, it enables them to identify and assess vulnerabilities within the larger framework related to the overall risk profile of an organization. Understanding network security and security operations means that a tester might see precisely how effective the firewalls, intrusion detection systems, and other network defences are. Moreover, knowledge of access control and secure software development equips penetration testers with the ability to test the strength of authentication mechanisms in certified scrum master, authorization policies, and application security.





