
- Introduction to Threat Modeling
- Why is Threat Modeling Important?
- Key Concepts in Threat Modeling
- Common Threat Modeling Methodologies
- Steps for Threat Modeling
- Best Practices for Threat Modeling
- Tools for Threat Modeling
- Conclusion
Threat modelling is a structured approach to identifying, analyzing, and mitigating security threats to a system, application, or network. It is an important process for identifying potential risks, Vulnerability Management , and threats before they can be exploited and helps organizations develop proactive security measures.This blog will discuss threat modelling, its importance, and how it can be implemented. We will also discuss various methodologies, best practices, and tools used in threat modelling.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Introduction to Threat Modeling
This technique will help identify potential security threats in an information system, based on which the possibility of those attacks can be anticipated, so steps for mitigating those threats are taken. It’s the most important part of a Cybersecurity Training Courses management process. An organization can identify, assess, and prioritize security risks within its software applications, systems, and networks by modelling this type of threat.In a normal threat modelling process, security professionals analyze a system or application to identify a potential attack vector against that system. This includes all data breaches, access to unauthorized things, or denial-of-service attacks. With those threats in mind, strategies are developed to mitigate the likelihood of these threats materializing or to reduce their impact if they occur.Threat modelling can be performed at any stage of the SDLC, but it is most effective when performed early during the design phase. This allows teams to address potential security issues before they become costly or difficult to fix.
Why is Threat Modeling Important?
Proactive Risk Management would enable the organization to see the security risks at very early stages of development, thus understanding a threat and putting corresponding security measures in place beforehand.Because security risks are identified, organizations can allocate resources better to address critical threats first. Many industries have regulatory requirements for security, and threat modelling helps organizations meet these standards by proactively addressing potential vulnerabilities.Early identification of Ransomware in Cybersecurity issues minimizes the cost and time spent fixing vulnerabilities later in the lifecycle. Addressing security issues in the design phase is easier and cheaper than during deployment.Threat modelling increases the security awareness of all stakeholders, including developers, architects, and security teams. This encourages a security-first mindset and a collaborative approach to addressing threats.
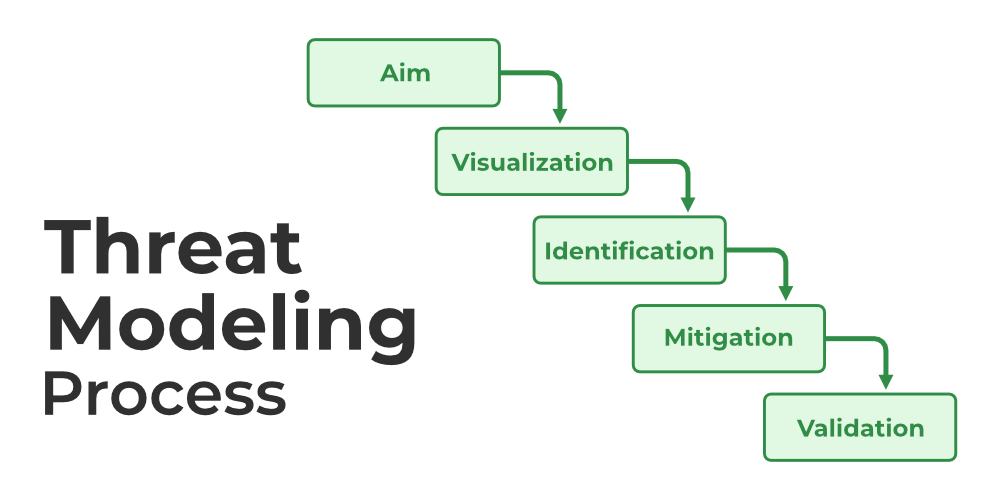
Key Concepts in Threat Modeling
- Assets: These are the valuable resources in a system that need to be protected, such as data, intellectual property, user credentials, and system availability.
- Threats: These are potential actions or events that can harm an asset. A threat could be anything from an attacker gaining unauthorized access to a system to a natural disaster disrupting service availability.
- Vulnerabilities: Vulnerabilities are weaknesses or flaws in the system that threats can exploit. These might be coding errors, poor configurations, or inadequate security controls.
- Attack Surface: The term “attack surface” describes the points of access into a system where a hacker could take advantage of weaknesses. Attackers have more chances to exploit a system when the attack surface is greater.
- Defensive actions: Defensive actions to reduce the risk assessment connected to a specific Threat Intelligence or vulnerability are mitigations. Input validation, firewalls, multi-factor authentication, and encryption are a few examples of mitigations.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Common Threat Modeling Methodologies
STRIDE- Spoofing: Impersonation of some other user or system.
- Tampering: Unauthorized changes to data or system components.
- Repudiation: Denying actions or transactions that took place.
- Information Disclosure: Unauthorized access to confidential information.
- Denial of Service (DoS): Denial of service through overloading the system.
- Elevation of Privilege: Gain unauthorized access to higher levels of system functionality.
- Define objectives and scope: Understand the system’s goals and boundaries.
- Define the attacker’s goals: Identify what an attacker could gain by compromising the system.
- Model the attack surface: Map out the components of the system and identify potential attack vectors.
- Analyze threats: Evaluate the risk management and likelihood of different attack scenarios.
- Identify security controls: Identify existing controls that can mitigate threats.
- Perform attack simulations: Simulate possible attacks to assess the system’s response.
- Define mitigation strategies: Develop strategies to reduce the risk assessment of successful attacks. OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation)
- Identifying critical assets and resources.
- Understanding potential threats and vulnerabilities that could impact these assets.
- Evaluating security controls and their effectiveness.
- Prioritizing risks and deciding on mitigation strategies.
- OCTAVE is particularly useful for large organizations with complex infrastructures, as it involves a detailed analysis of technical and operational factors. VAST (Visual, Agile, and Simple Threat Modeling)
- Identify Assets: Determine what assets should be protected.
- Scope definition: Know the system architecture, which includes its components, data breachers, and users.
- Identify Threats and Vulnerabilities: Apply methodologies like STRIDE or PASTA to identify threats and vulnerabilities.
- Risk evaluation: Assess the likelihood and impact of every identified threat.
- Identify Mitigations: Design and implement mitigations that reduce the risks.
- Documentation of Findings: Write detailed documentation outlining the identified threats, vulnerabilities, mitigations, and the overall risk assessment.
- Review and Refine: Threat modelling is not a one-time activity. As systems change, reviewing and refreshing should happen regularly.
- Microsoft Threat Modeling Tool: A free tool that facilitates teams in developing a threat model using the STRIDE model.
- OWASP Threat Dragon: An open-source tool to assist developers and security professionals create threat models using visual diagrams.
- IriusRisk: A risk management platform that automates the threat modelling process and integrates with CI/CD pipelines.
- ThreatModeler: An all-inclusive threat modelling tool that automates the generation of threat models and helps teams identify and manage security risks. These tools help streamline the threat modelling process and improve collaboration between development, security, and operations teams.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
PASTA (Process for Attack Simulation and Threat Analysis)VAST is an agile approach to threat modelling that blends well into the DevOps pipeline. It emphasizes the simplicity and visibility of threat modelling to identify risks and develop countermeasures quickly and easily in Cybersecurity Training Courses . VAST promotes continuous and international threat modelling for security to be part of the development process.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Steps for Threat Modeling
Best Practices for Threat Modeling
The earlier you integrate threat modelling into the SDLC, the more proactive you can identify and mitigate risks. Threat modelling should include Database Security experts, developers, architects, and other key stakeholders to ensure all perspectives are considered. Threat modelling should be revisited regularly to account for system changes or emerging threats. Detailed documentation is necessary for tracking and managing identified threats and mitigations. Prioritize threats based on their potential impact and likelihood. Not all threats are equally dangerous. Leverage automated threat modelling tools to streamline the process and ensure team consistency.
Tools for Threat Modeling
Several tools exist to aid in threat modelling. Some of the most commonly used tools include:
Conclusion
An essential technique for identifying and resolving security threats related to networks, systems, and applications is threat modeling. Organizations can better establish strong mitigation methods to defend against these assaults by looking at potential threats and vulnerabilities before they materialize. An Cybersecurity Training overall security posture is greatly improved by implementing best practices, appropriate tool utilization, and structured threat modeling methodology.Threat modeling is ultimately a continuous process that ought to be incorporated into each stage of the software development lifecycle rather than being a one-time event. With the right approach, threat modelling helps organizations build secure systems to withstand the ever-changing landscape of cybersecurity threats.





