
- Introduction to Nmap and Its Capabilities
- Basic Nmap Scan Commands
- Advanced Nmap Scanning Techniques
- Nmap Scan Types (TCP, UDP, SYN, etc.)
- Using Nmap for Host Discovery
- Scripting and Automation with Nmap
- Interpreting Nmap Scan Results
- Conclusion
Introduction to Nmap and Its Capabilities
Nmap (Network Mapper) is an open-source tool used for network exploration, security auditing, and vulnerability scanning. It is widely used by network administrators, security professionals, and ethical hackers to assess the security of networks by scanning for live hosts, open ports, and vulnerabilities in Cybersecurity Training Courses . Nmap provides a variety of features and capabilities for network discovery, including host discovery, service version detection, operating system fingerprinting, and scriptable interactions with the network. One of Nmap’s main strengths is its flexibility and range of scan types, which allow users to gather detailed information about network infrastructures. It is commonly used for tasks like identifying open ports, discovering devices in a network, detecting network services, and auditing firewalls and security systems.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Basic Nmap Scan Commands
Nmap can be used with a simple syntax to perform a range of basic network scans. Below are some common basic Nmap scan commands:
-
Basic Host Discovery:
- Command: nmap
- Example: Nmap 192.168.1.1
- This command performs a simple scan to determine if the target IP subnets (or range of addresses) is live and which ports are open. Scan Multiple IP Addresses:
- Command: nmap 192.168.1.1 192.168.1.2
- Example: Nmap 192.168.1.1-5
- Nmap can scan multiple IP addresses at once by specifying them in the command line or using a range. Scan Specific Ports:
- Command: nmap -p
- Example: nmap -p 80,443 192.168.1.1
- You can scan specific ports by using the -p flag followed by the port numbers or ranges. Operating System Detection:
- Command: nmap -O
- Example: nmap -O 192.168.1.1
- This option attempts to determine the operating system running on the target host. Service Version Detection:
- Command: nmap -sV
- Example: nmap -sV 192.168.1.1
- Nmap can be used to detect versions of services running on open ports with the -sV flag.
Advanced Nmap Scanning Techniques
Nmap offers several advanced scanning techniques for in-depth network reconnaissance. The SYN Scan (-sS) is a popular and fast method that sends SYN packets without completing the TCP handshake, making it harder to detect by firewalls and IDS. The UDP Scan (-sU) helps identify open UDP ports on a target, though it requires more time and resources. For service version detection, the -sV option probes open ports to gather detailed version Information Security about the services running on them. The aggressive scan (-A) combines OS detection, service version detection, script scanning, and traceroute in one scan. Additionally, the firewall evasion technique (-f) fragments packets to bypass firewalls and IDS, making it harder for network defenses to detect the scan.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
Nmap Scan Types (TCP, UDP, SYN, etc.)
Nmap supports different types of scans to interact with various protocols in a network. These include:
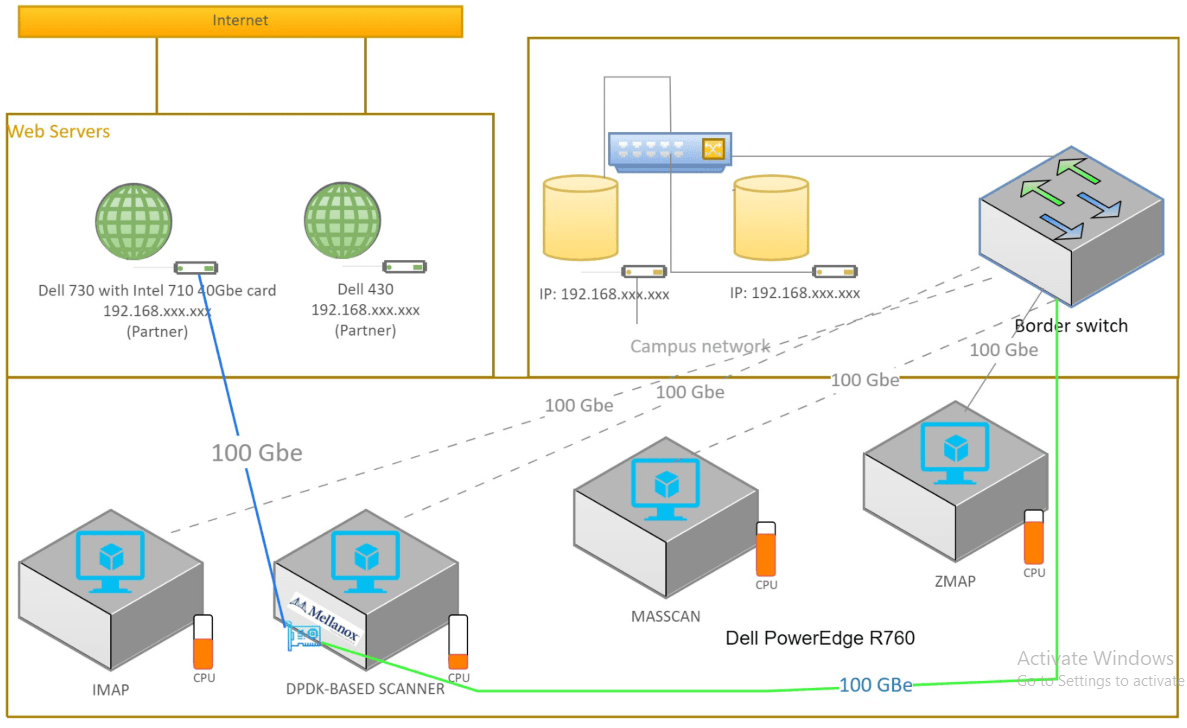
A full TCP handshake is performed during this scan type. While it’s more likely to be detected, it is useful if SYN scanning is blocked or if root privileges are not available. SYN Scan is a stealth scan where only the SYN flag is set during the handshake. If the target responds with a SYN-ACK, the port is open. This method is faster and more stealthy.UDP scanning checks for open UDP ports. UDP does not establish a connection like TCP, so scanning requires a different approach, making this scan type more challenging and slower.This scan sends a TCP FIN packet to the target, which is usually used to terminate a connection. It can bypass Packet Filtering Firewall and packet filters, but it’s less reliable on modern systems.This scan sends TCP packets with the FIN, PSH, and URG flags set, which can sometimes bypass firewalls or intrusion detection systems. This scan works by analyzing the TCP window size to determine the open ports. It is a stealthy technique that can evade detection.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Using Nmap for Host Discovery
Host discovery is one of the primary tasks that Nmap performs. It identifies which devices are alive and reachable in a Cybersecurity Training Courses.
-
Ping Scan:
- Command: nmap -sn
- Example: nmap -sn 192.168.1.0/24
- This scan only determines whether a host is up or down. It sends ICMP echo requests and skips port scanning. DNS Resolution:
- Command: nmap -R
- Example: nmap -R google.com
- Nmap can resolve hostnames to IP addresses to aid in identifying active hosts on a network. Host Discovery with OS Fingerprinting:
- Command: nmap -O -sn
- Example: nmap -O -sn 192.168.1.1
- In addition to detecting live hosts, Nmap can also attempt to detect the operating system and version of the device.
Scripting and Automation with Nmap
Nmap supports automation through the Nmap Scripting Engine (NSE), which allows users to execute scripts for tasks such as scanning, vulnerability detection, and information gathering. By using the Command Prompt Commands `nmap –script=`, users can run pre-defined or custom scripts like `http-vuln-cve2006-3392`. Additionally, multiple scripts can be run simultaneously using commands like `nmap –script=default,vuln`, enabling more comprehensive scans, such as vulnerability detection and detailed service information retrieval. Nmap can also be integrated with automation tools like Ansible, Puppet, or Python to schedule and automate network scans, ensuring continuous monitoring and security assessments.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Interpreting Nmap Scan Results
Once an Nmap scan is complete, interpreting the results is crucial to understanding the security and configuration of the scanned systems. The output typically includes the following information:
Host Information: The IP address or hostname of the scanned device, along with any available information like the operating system and device type.
Port Information: The list of open ports, closed ports, and filtered ports on the target, along with the associated services and versions. This is critical for identifying vulnerable services.
Service Information: Nmap attempts to identify the software running on the open ports, including version numbers. This helps in detecting outdated or vulnerable services.
Operating System Detection: Nmap attempts to guess the target’s operating system based on network characteristics such as response times and packet behavior. This can help security professionals identify outdated Intrusion Detection System .
Vulnerabilities and Warnings: Nmap will often flag potential vulnerabilities or security issues, especially when running scripts or using advanced scanning techniques.
Example of Nmap Output:- #Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-04 14:30 PDT
- #Nmap scan report for 192.168.1.1
- #Host is up (0.0010s latency)
- #Not shown: 993 closed ports
- #PORT STATE SERVICE VERSION
- #80/tcp open http Apache httpd 2.4.29
- #443/tcp open https Apache httpd 2.4.29
- #8080/tcp open http Apache Tomcat 8.5.45
Conclusion
Nmap is an indispensable tool for network discovery, vulnerability assessment, and security auditing. With its flexibility, scalability, and powerful scanning options, it is the go-to choice for professionals in Cybersecurity Training . By mastering Nmap’s basic and advanced scanning techniques, you can significantly improve your network security posture and reduce the risk of potential cyberattacks. Nmap is an indispensable tool for network discovery, vulnerability assessment, and security auditing. With its flexibility, scalability, and powerful scanning options, it is the go-to choice for professionals in cybersecurity. By mastering Nmap’s basic and advanced scanning techniques, you can significantly improve your network security posture and reduce the risk of potential cyberattacks. Nmap’s ability to identify open ports, services, and OS information provides crucial insights into network weaknesses. Its scripting engine (NSE) enhances automation for vulnerability scanning, further strengthening security assessments. Regular use of Nmap can ensure continuous monitoring and proactive threat mitigation across the network.





