
- Introduction to Information Security
- Key Principles of Information Security
- Types of Information Security
- Common Threats to Information Security
- Importance of Information Security
- Best Practices for Ensuring Information Security
- Conclusion
Introduction to Information Security
Information security protects data from unauthorized access, use, disclosure, modification, or destruction. As businesses and individuals increasingly rely on digital technologies, safeguarding sensitive information has become more critical. Information security aims to ensure data confidentiality, integrity, and availability. It is about protecting data from cyber criminals and ensuring that data is accessible to those who need it while preventing unauthorized individuals from accessing Cybersecurity Training Courses. In today’s digital landscape, information security has evolved into a multi-layered approach involving policies, technologies, and processes to safeguard sensitive data. As cyber threats continue to rise, organizations and individuals must remain vigilant and proactive to protect their information.
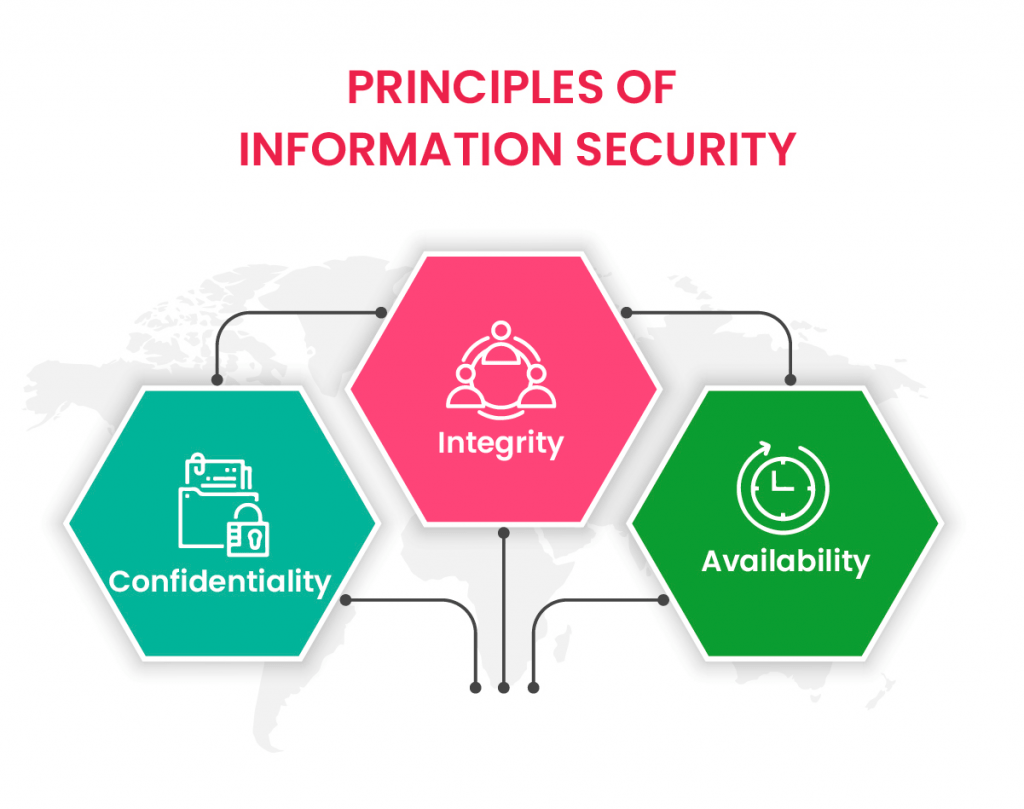
Key Principles of Information Security
Information security revolves around several core principles, each of which contributes to the overall protection of data. These principles form the foundation of security measures and policies. The three primary principles of information security are:
To become a certified cyber security, have a look at our Cyber Security Online Training right now
- Confidentiality: Confidentiality is the act of safeguarding sensitive information from unauthorized access. That means that data is accessible only to those permitted or cleared to access such information. Cipher Encryption and stringent access controls are usually used for confidentiality.
- Integrity: Data integrity means the consistency and accuracy of data. Data cannot be altered in an unauthorized manner, or it is not tempered in an unauthorized manner. There are measures such as checksums, hash functions, and digital signatures that maintain integrity.
- Availability: Availability ensures that data and systems are accessible to authorized users when needed. This principle is vital for ensuring business continuity. Backup systems, disaster recovery plans, and redundancy are key to maintaining availability.
Types of Information Security
Network Security:- Network security secures computer networks from Cybersecurity Training Courses , intrusions, and unauthorized access.
- It involves using firewalls, intrusion detection and prevention systems, and encryption protocols to secure data as it travels across a network.
- Network security is needed to prevent access to internal systems and ensure that they are protected during transfer over public networks such as the Internet.
- Application security involves protecting applications and software programs from vulnerabilities the attacker would use. It includes web applications, mobile apps, and enterprise software.
- Some common methods for ensuring application security include secure coding practices, vulnerability scanning, and regular software patching.
- Applications have become complex and interconnected, making security very important to prevent data breaches and cyberattacks. Data Security
- Data security involves safeguarding data, whether in motion or at rest, from unauthorized access, theft, or corruption. It incorporates techniques such as encryption, access controls, and tokenization to protect sensitive information.
- It is particularly important for protecting sensitive personal and business data, including financial records, medical information, and proprietary business details, from Cybersecurity Training Courses
- Encryption is one of the most widely used methods for ensuring data security, as it transforms data into an unreadable format, preventing unauthorized access to sensitive information.
- Endpoint security protects devices that join the network, including laptops, smartphones, and tablets.
- These devices are often prime targets of cyberattacks. So, endpoint security is very important for an organization’s information security policy.
- Typical endpoint security solutions usually incorporate antivirus software, firewalls, and tools for managing and monitoring all devices connected to the network.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training
Application Security:Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Endpoint SecurityCommon Threats to Information Security
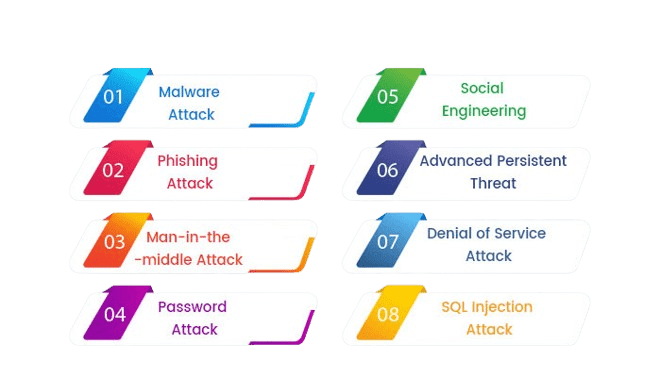
Understanding the common threats to information security is essential for developing effective defense strategies. One prevalent threat is malware, malicious software designed to damage or exploit systems, networks, or devices. Types of malware include viruses, worms, Trojans, and ransomware, which can steal data, corrupt files, or even lock users out of their systems. Another common threat is phishing attacks, where cybercriminals trick individuals into revealing sensitive information like passwords or credit card details. These attacks often appear as fraudulent emails or websites that mimic legitimate ones aimed at stealing personal data. Additionally, insider threats pose a significant risk to the organization’s employees, contractors, or business partners. These insiders may intentionally or unintentionally compromise security by misusing their access to sensitive data. Denial-of-Service (DoS) attacks are another common threat, where attackers flood a system or network with excessive traffic, making it unavailable to legitimate users. Distributed Denial-of-Service DDOS Mitigation attacks take this further by utilizing multiple systems to launch large-scale disruptions, which can be costly and disruptive for organizations.
Importance of Information Security
- Protection of Sensitive Data:As organizations hold more sensitive data, such as customer information and intellectual property, securing this data becomes an important factor in maintaining the privacy and trust of individuals.
- Regulatory Compliance: Many industries are governed by stringent regulations, such as GDPR and HIPAA, making protection measures for Database Security. The absence of such compliance can bring significant fines and reputational loss.
- Preventing Financial Loss: Cyberattacks can lead to significant financial losses, whether through direct theft, legal fines, or reputational damage. Investing in information security helps avoid such losses.
- Maintaining Trust and Reputation: A customer or client data breach can severely damage an organization’s reputation. Customers trust businesses to protect their personal information, and failing to do so can result in loss of trust and future business.
Ready to pass the interview for cybersecurity ? Learn how to answer Cybersecurity Interview Questions and Answers
Best Practices for Ensuring Information Security
To have robust information security, organizations and individuals should use best practices such as the Implementing Strong Password Policies using strong passwords and regularly changing them can prevent unauthorized system access. Regular Software Updates and Patching by updating the software will ensure known vulnerabilities are patched, reducing cyberattacks. Training employees should be trained constantly on best security practices and recognizing phishing emails and other social engineering attacks. Data Encryption in Network Security ensures that it cannot be read without the proper decryption key, even if it is intercepted. MFA adds a layer of security by requiring users to verify their identity through multiple methods, such as a password and a fingerprint scan. Regular backups and a comprehensive disaster recovery plan ensure that data can be restored in case of an attack or system failure.
Conclusion
Information security has become ever more important in a digital world. From safeguarding personal data to ensuring enterprise systems’ security, the organization needs proactive protection against cyber threats. Understanding the key principles of information security, various security measures, and common threats will better equip individuals and organizations to be more prepared to defend against cyber attacks. As cybercriminals evolve, staying updated and following best practices in information security will be crucial in safeguarding sensitive data and maintaining business continuity. Cybersecurity Training is not about technology alone; it’s about creating a culture of security and responsibility within the organization and society.





