
- Introduction to Denial-of-Service (DoS) Attacks
- What is a DoS attack?
- Traditional Common Types of DoS Attacks
- Mitigating a DoS Attack in Real-Time
- Difference Between DoS and DDoS Attacks
- Tools Used for DoS Attacks
- DoS Attack Prevention
- Conclusion
Denial-of-Service (DoS) attacks are a type of cyber attack where the attacker aims to make a network service or system unavailable to its intended users, often by overwhelming the targeted system with excessive traffic or resource requests. This disrupts the normal functioning of the service, causing it to crash or slow down significantly. DoS attacks can target various systems, including websites, servers, and networks. To better understand and defend against such attacks, it’s crucial to enroll in Cyber Security Training Courses that provide essential knowledge and strategies for preventing service disruptions. A common form of DoS attack is the Distributed Denial-of-Service (DDoS) attack, where multiple compromised systems are used to launch an attack, making it harder to mitigate due to the volume of incoming traffic. Attackers may use different methods, such as sending a large amount of traffic (flood attacks) or exploiting vulnerabilities to exhaust system resources.
Are You Interested in Learning More About Denial-of-Service (DoS) Attacks? Sign Up For Our Cyber Security Online Training Today!
Introduction to Denial-of-Service (DoS) Attacks
In today’s digital age, online services, websites, and networks have become vital functions in the everyday activities of businesses, organizations, and people. There is, however, a growing threat to these platforms: Denial-of-Service attacks. A DoS attack significantly undermines service availability by overwhelming it with relentless traffic, effectively barring legitimate users from accessing the essential resources they require. This blog post will outline the foundation of DoS attacks, typical types, the difference between DoS and DDoS attacks, tools used by attackers, and prevention and mitigation strategies, including how to defend against Malware Attacks that often accompany such disruptions. Recognizing the significance of DoS attacks is crucial for safeguarding your online assets and guaranteeing that users maintain their access to vital services. With the rise of cybercrime and the increasing reliance on digital platforms, businesses face immense pressure to protect their online presence. While DoS attacks can be disruptive, they also provide a unique opportunity to assess vulnerabilities and improve overall cybersecurity. Understanding the mechanics behind these attacks and staying informed about the latest mitigation techniques is essential for organizations to stay ahead in the ever-evolving landscape of cybersecurity threats.
What is a DoS attack?
A Denial-of-Service attack is a malicious cyber-attack that makes a service, server, or network resource unavailable to its intended users. It typically happens because an attacker overloads the target with too many requests or data beyond what it can handle, slowing down the system, crashing it, or making it unresponsive. Regular Vulnerability Scanning can help identify potential weaknesses in the system, reducing the risk of such attacks. A DoS attack disrupts normal operations, preventing legitimate users from accessing services.
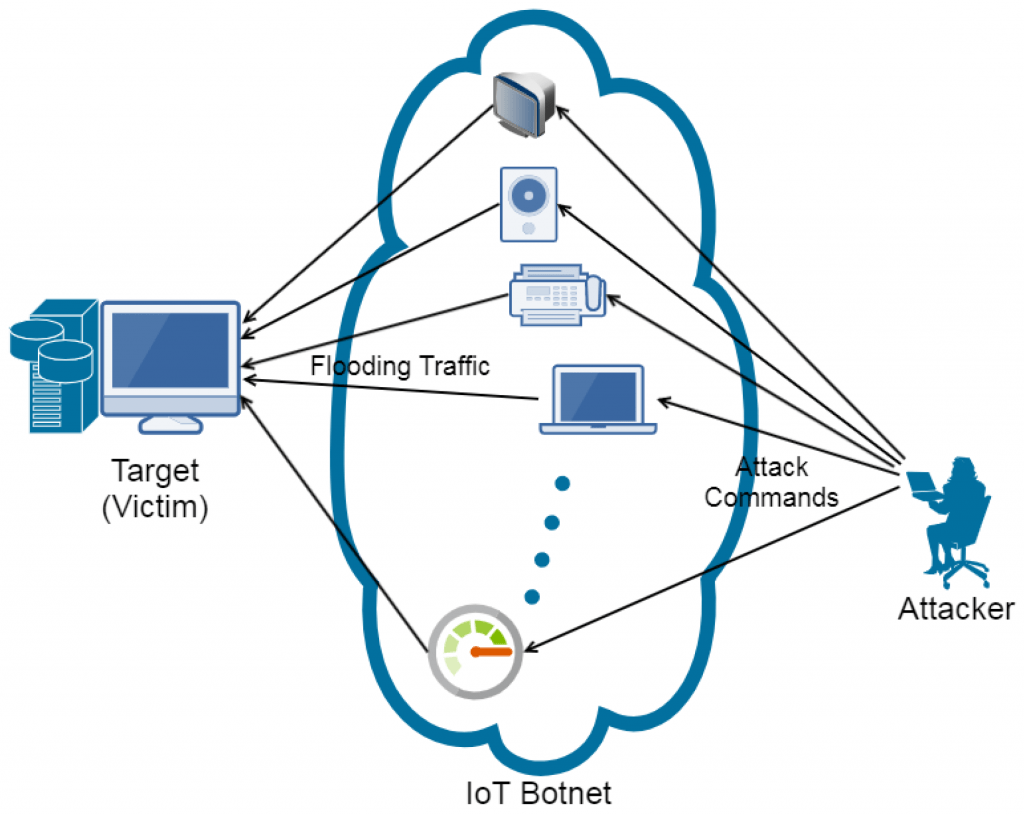
To Explore DoS Attacks in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Traditional Common Types of DoS Attacks
DoS attacks can be classified into attacks that pinpoint more specific weaknesses or functions within the network. Implementing a Demilitarized Zone can help protect critical network resources by isolating them from direct exposure to potential threats like these attacks. The most common types are:
-
Volumetric Attacks
- Description: The attack targets bandwidth by flooding traffic on the bandwidth, which then overtakes the bandwidth. Through packet flooding on the network, an attacker consumes the whole bandwidth to the extent that legitimate traffic cannot pass through. Examples:
- UDP Flood: In this form of attack, thousands of User Datagram Protocol packets are sent at random ports of a server. This makes the server process the requests sent and subsequently causes congestion.
- ICMP: Ping Flood – Leverages ICMP packets repeatedly “ping” the server, forcing exhausting bandwidth use across the network. Protocol Attacks
- Description: These attacks exploit some vulnerabilities in network protocols, such as TCP, draining server resources. They tend to consume the tables of connections or timeout and then prevent normal operations. Examples:
- SYN flood: An attacker sends many SYN requests that attempt to establish a connection but do not complete a handshake process that ties up server resources and prevents legitimate connections.
- Smurf Attack: This attack sends forged ICMP requests to a network’s broadcast address, which causes all devices in the given network to act by amplifying the attack. Application Layer Attacks
- Description: Layer 7 attacks target applications at their layers instead of the physical network infrastructure. Because such attacks imitate normal user activities, such attacks are more complex to detect Examples:
- HTTP Flood: It relies on multiple HTTP requests targeting server resources, much unlike volumetric, as it will require fewer requests to be successful but is still pretty hazardous.
- Slowloris: Issues partial HTTP requests to maintain open server connections, leading to incomplete connections that can overwhelm the server.
Mitigating a DoS Attack in Real-Time
Real-time mitigation during a Denial-of-Service (DoS) attack can help maintain service availability. Block malicious IPs quickly to reduce attack traffic. Temporarily blocks traffic from specific regions during concentrated attacks. Blocks malicious traffic sources by known malicious IP databases. They distribute incoming traffic to global servers that minimize loads on the origin server. To understand how to set up and secure such systems, Cyber Security Training Courses can provide valuable insights into managing and protecting distributed networks. Services like AWS Shield or Google Cloud Armor can absorb volumes of attack traffic by rerouting through distributed data centers.This method automatically adjusts request limits based on traffic to prevent overload. It is good at filtering out too many requests, especially at the application layer. Many ISPs provide DDoS mitigation services that protect your network by blocking harmful traffic from reaching the edge or rerouting it so your servers aren’t overwhelmed. These measures enhance service performance by filtering, distributing, and blocking malicious traffic at various levels.
Difference Between DoS and DDoS Attacks
In a nutshell, while DoS and Distributed Denial-of-Service (DDoS) are intended to degrade service availability, they differ in scale, complexity, and sources.
-
DoS (Single Source)
- From a single device or network.
- Usually, it’s smaller in scale and easier to detect and block.
- Thus, it is more straightforward to establish but disastrous when small networks occur. DDoS (Multiple Sources)
- It usually originates from multiple compromised devices, typically forming a botnet.
- It is more massive and harder to mitigate as traffic derives from different sources.
- More difficult to track back to the attacker, which makes it hard to shut down.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Tools Used for DoS Attacks
Certain tools can be linked to DoS attacks. While some are legitimate and intended for network testing, they are misused for malicious purposes. Understanding the Tools and Platforms of Threat Intelligence is essential to distinguish between legitimate tools and those that could be exploited for harmful activities like DoS attacks.
- LOIC (Low Orbit Ion Cannon) Originally designed as a network stress test, LOIC is for simple DoS attacks. It slams a flood of TCP, UDP, or HTTP requests to the target and can drain resources there.
- HOIC (High Orbit Ion Cannon) An upgraded variant of LOIC is referred to as HOIC, which allows an attacker to target multiple URLs simultaneously. HOIC can generate as many as 256 unique requests, increasing the likelihood of executing a successful DoS attack.
- HULK (HTTP Unbearable Load King) Because this tool creates single HTTP requests with randomized headers and payloads, it is difficult for the servers to identify the traffic as an attack. HULK often fills up web servers with its legitimization traffic patterns to overload the same.
- Mirai Botnet Mirai malware effectively infiltrates IoT devices and creates a powerful botnet capable of launching massive DDoS attacks. With Mirai-based assaults, attackers can take down major websites by harnessing the power of millions of compromised devices to overwhelm their infrastructure.
DoS Attack Prevention
Defensive techniques should always be accompanied by proactive monitoring, especially when it comes to Website Servers, to quickly identify and mitigate potential threats before they cause significant damage. The following are some effective prevention methods:
- Firewalls and Intrusion Detection Systems: For instance, firewalls allow unwanted traffic to be filtered. The IDS systems monitor the systems for known attack patterns. Together, they provide frontline definitions against known attack patterns.
- Rate Limiting: It limits incoming requests per user and prevents attackers from sending too many requests to a server, which is useful against application-layer attacks.
- Traffic Monitoring and Analysis: Monitoring tools such as SolarWinds, Wireshark, or Nagios assist in early identification of abnormal traffic patterns. As well, real-time traffic analysis is necessary to get ahead of potential threats before they become attacks.
- Load Balancers: Load balancers effectively distribute incoming traffic across multiple servers, significantly reducing the load on any single server. This strategic distribution prevents overload and ensures that services remain operational and available for extended periods.
- Content Delivery Networks (CDNs): Content Delivery Networks (CDNs) revolutionize data distribution by strategically placing servers around the globe. This intelligent approach ensures that content is delivered closer to users, significantly enhancing response times, particularly during peak traffic. CDNs proficiently handle incoming requests, providing robust protection against DoS attacks and ensuring your services remain reliable and secure.
- Redundant Infrastructure: A system can ensure continuous service by implementing backup servers and failover systems to take over if the primary server fails. Having redundant infrastructure reduces the chances of a total service outage.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
In the digital world’s ever-evolving landscape, denial-of-service attacks pose a significant threat. These attacks can lead to devastating consequences, including severe disruptions to business operations, loss of revenue, and harm to reputations. Understanding DoS attacks and their associated tools is essential not just for safeguarding your business but also for protecting your interests. Enrolling in Cyber Security Training Courses can equip you with the necessary skills and knowledge to effectively defend against these types of attacks. Being informed is the first step toward ensuring security in today’s interconnected environment. Implementing a combination of proactive monitoring, filtering, and traffic distribution methods can mitigate the impact of a DoS attack and allow services to be available to legitimate users. Keeping current with the newest attack methods and regularly updating security measures will constitute the best defense against these disruptive attacks. In cybersecurity, always remember that prevention is better than recovery.





