
- Introduction of TCP and UDP
- What is the TCP/IP Model(Transmission Control Protocol)
- Why is the TCP/IP Model important?
- TCP/IP Model Layers
- Advantages of TCP/IP Model
- Disadvantages of TCP/IP Model
- OSI Model vs TCP/IP Model
- Conclusion
Introduction
The TCP/IP model (Transmission Control Protocol/Internet Protocol model) is a set of protocols that govern communication between computers over a network, particularly the Internet. Cybersecurity Training Courses serves as the foundation for how data is transmitted and received across networks. The model breaks down network communication into four layers, each responsible for specific tasks, ranging from application services to data transmission over physical media. The TCP/IP model is widely adopted due to its simplicity, flexibility, and ability to support scalable and reliable communication in diverse network environments. It is essential for the functioning of the Internet and various other networking systems.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
What is the TCP/IP Model?
- The transmission manipulate protocol/net protocol (TCP/IP) version reveals its origins inside the ARPANET reference version. The structure of TCP has advanced from research in strategies for connecting a couple of packet-switched networks.
- The critical purpose of the TCP/IP version is to permit the sending of statistics packets to at least one utility on an unmarried computer. The TCP/IP version is a net-successful set of protocols.
- The TCP/IP version units out how packets change records via the Web Security . This set of conversation protocols determines how statistics are to be broken, addressed, transferred, routed, and acquired for sharing. The server-purchaser version is the conversation version for this set.
- The TCP/IP version describes a way to assemble conversation strains for applications. It additionally manages to divide a message into packets earlier than it’s far despatched throughout and reassembled.
- IP outlines how packets are addressed and routed to ensure that the statistics reach the proper destination. The contemporary net structure makes use of this community concept.
Why is the TCP/IP Model important?
TCP/IP is unpatented and, as a result, isn’t managed with the aid of any unmarried company. The IP suite can accordingly be without a doubt updated. It is interoperable with all running structures and may interface with each different machine. The IP Security has entire laptop hardware and net compatibility. TCP/IP is extensively available and permits the maximum green community course to be described as a routable protocol.
The TCP/IP version has 4 layers: Application Layer, Transport Layer, Network Layer, Physical Layer.
Application Layer
The utility layer is a mixture of the utility, presentation, and consultation layers. This layer is liable for the interplay between the consumer and the utility. Here, statistics are formatted, converted, encrypted, decrypted, and set to the consumer.
Protocols utilized by the utility layer are:
- HTTP Hypertext switch protocol permits the customers to engage with the World Wide Web via browser applications.
- SMTP A simple mail switch protocol is used to ship mail.
- FTP File switch protocol is used for transmitting documents from one gadget to another.
- TELNET The teletype community acts as a client-server protocol. It is used to offer bidirectional connections.
- UDP This protocol offers connectionless carrier and quit-to-quit transport of transmission. It is taken into consideration as a risky protocol as it discovers the mistakes however now no longer specifies them.
- TCP It offers all shipping offerings to the software layer. TCP is a reliable protocol for mistake detection and retransmission. It assures that each segment should be obtained and identified earlier than finishing the transmission and discarding the digital circuit.
- IPV4 Internet protocol model four is hired for packetizing, forwarding, and transport of packets. IP is an unreliable datagram protocol.
- ICMPV4 Interrupt manipulated message protocol controls all mistakes. These errors are treated with the aid of using ICMP protocol all through the transport of the message to goal problems.
- IGMPInternet organization control protocol facilitates multicasting.
Transport Layer
The shipping layer is liable for quit-to-quit communique and offers mistakes-unfastened transport of records. This layer can ship the records via a connection-orientated or connectionless layer.
The protocols used inside the shipping layer are person Database Security protocol (UDP) and TCP.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training.
Network Layer
The community layer offers host addressing and chooses the high-satisfactory direction for the vacation spot community. This layer continues the exceptional carrier and gives connectionless quit-to-quit networking.
The protocols inside the community layer are:
Physical Layer
The bodily layer interacts with the pinnacle degree of the TCP/IP version software. This layer is the closest quit-person TCP/IP layer. It is a method that the purchasers can hook up with different software program apps.
The bodily layer interacts with software programs to expand media platforms in Cybersecurity Training Courses . Data is continuously past the limits of the TCP/IP version to be interpreted inside the software. Software consisting of a records transfer, mail, faraway login, etc., is an instance of this layer.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Advantages of TCP/IP Model
It is an industry-general version that may be efficiently deployed in realistic networking problems. It is interoperable, i.e., it permits cross-platform communications amongst heterogeneous networks. It is an open protocol suite and isn’t owned with the aid of any precise institute; so, it can be utilized by any man or woman, or organization. It is a scalable, client-server architecture. It permits networks to be delivered without annoying the contemporary services. It assigns an IP cope to every pc at the network, for this reason making every tool identifiable over the network. It assigns every web page a website call; it presents calls and copes with decision services.
Disadvantages of the TCP/IP Model
It isn’t generic. So, it fails to symbolize any protocol stack aside from the TCP/IP suite. For example, it can’t describe the Bluetooth connection.It no longer separates the principles of services, interfaces, and protocols. So, it isn’t appropriate to explain new technology in new networks.It no longer distinguishes between the information hyperlink and the bodily layers, which have very one-of-a-kind functionalities. The information hyperlink layer ought to be challenged with the transmission of frames. On the opposite hand, the bodily layer ought to lay down the bodily traits of the transmission. The right version ought to segregate the 2 layers. It was in the beginning designed and applied for wide-vicinity networks. It isn’t optimized and applied for wide-vicinity networks. It isn’t optimized for small Virtual Private Network which include a nearby vicinity network (LAN) and a private vicinity network (PAN.) Among its suite of protocols, TCP and IP have been cautiously designed and nicely applied. Some of the protocols have been advanced advert hoc and proved to be improper in the lengthy run. However, because of the recognition of the version, those protocols are getting used even 30 to 40 years after their introduction.
OSI Model vs TCP/IP Model
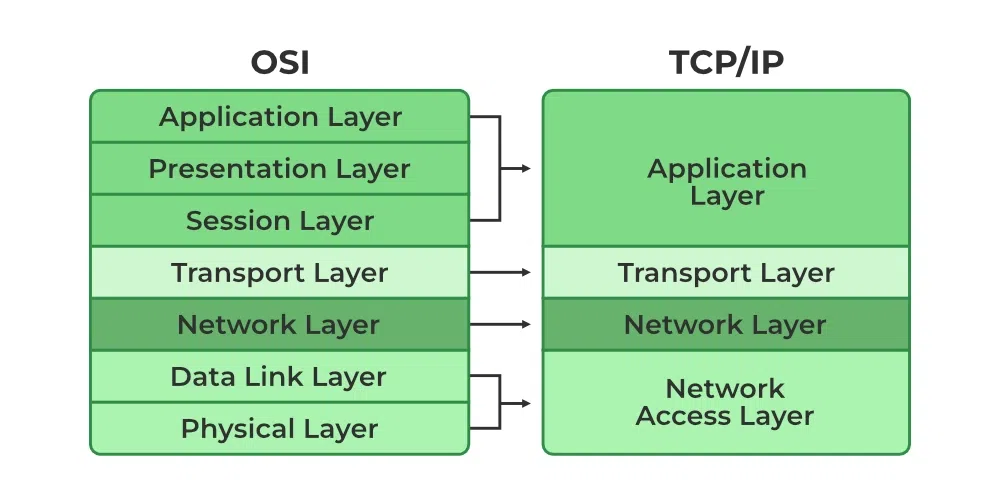
The OSI version is a valid and conceptual layout that illustrates the community connection utilized by structures open to interconnection and communique with different structures. The OSI version is logical and conceptual, defining networking that is used by structures which can be open to communique and connectivity with different structures. The OSI version additionally gives a logical community and successfully depicts pc packet delivery using numerous layers of Address Resolution Protocol.
The OSI version has seven layers:
- Application layer: The software layer interfaces with the top-degree of OSI version software. This layer is the maximum user-pleasant layer of the OSI version.
- Presentation layer: The presentation layer permits you to set up the shape for the statistics trade among each interacting body. It additionally assists you in managing the discount and encryption of statistics.
- Session layer
This layer regulates the pc dialogues. It lets you join the neighborhood and far-flung programs to start up and end.
- Transport layer
The delivery layer builds at the community layer, which transmits statistics from a procedure on a supply device to a procedure on a goal device. It is hosted using character or more than one network and helps carrier high-satisfactory functions.
- Network layer The community layer gives practical and procedural techniques to move statistics sequences of various lengths from one node to any other connected to more than one network.
- Data hyperlink layer The data hyperlink layer corrects bodily-layer-successful faults. The layer permits customers to set a method to sign up for connected community devices, and it can terminate them.
- Physical layer The bodily layer lets you describe the statistics connection`s electric and bodily requirements. This degree determines the hyperlink between the tool and the bodily medium of transmission.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Conclusion
The imperative goal of TCP/IP turned into to allow the sending of statistics packets to at least one software on an unmarried pc. At first, TCP was designed to fulfill the statistics communique wishes of the American DoD. TCP/IP is non-relational and, consequently, no organization is managed through Cybersecurity Training . This permits the IP suite to be up to date easily. It is like-minded and may interface with all different running structures. The IP suite is likewise absolutely like-minded with the computer systems and the internet.





