
- Introduction
- What is a Vishing Attack?
- Vishing Attacks: The three main forms
- How Vishing Works
- Vishing Attack Techniques
- Common Vishing Attack Examples
- How to Detect Vishing Attacks
- How to Protect from Vishing Attacks
- Real-life Examples of Vishing Scams
- Conclusion
Introduction
In our digital-first world cybercriminals are refining their tactics to exploit weaknesses. While email phishing is widely recognized, a particularly alarming threat has emerged vishing (voice phishing). The human voice authentication to deceive, attackers impersonate trusted figures to manipulate individuals into sharing sensitive information. Cyber Security Training Courses can help individuals recognize such tactics and strengthen their ability to protect against social engineering attacks like these. In this blog, we will uncover the intricacies of vishing attacks, analyze the techniques employed, share real-world examples, differentiate them from traditional phishing techniques and equip you with practical strategies to protect yourself. Don’t become a victim it’s crucial to stay informed and prepared.
Are You Interested in Learning More About Vishing Attack? Sign Up For Our Cyber Security Online Training Today!
What is a Vishing Attack?
Vishing, short for voice phishing is another scam that occurs over the telephone or even through voice messages. It is a social engineering technique in which attackers employ psychological manipulation to obtain secret information such as access passwords, credit card information, and personal identification information. Understanding these techniques is a key component of an Ethical Hacker’s Toolkit, which helps professionals identify and defend against such malicious tactics. Unlike Phishing Techniques which occurs over Emails or websites, vishing employs telecommunication as a launching pad for the attack. Vishing scams exploit trust, fear, or urgency. For instance, a scammer may pretend to be a bank official warning of unauthorized transactions or a government representative demanding unpaid taxes.
Vishing Attacks: The three main forms
Here are three ways Vishing attacks take form, each customized by various designs to exploit specific vulnerabilities. Understanding these will help highlight the kinds of scams that need to be identified and prevented, and incorporating technologies like Quantum Cryptography can provide enhanced protection against such attacks by securing sensitive communications.
- Impersonation of trusted entities: This type encompasses those impersonators who pose as agents of law-abiding organizations such as Banks Claiming suspicious activity on your account or requesting card verification,Government Agencies,Threatening litigation regarding unpaid taxes or immigration issues,Utility firms, Notification of uncollected rates or service being cut off and How it works The attacker uses caller ID spoofing to mimic an official number and persuasive phrases to earn the victim’s trust.For Example,This is your bank. We’ve detected unauthorized transactions. Please share your account details to secure your funds.
- Emotional Manipulation: Attackers exploit emotions like fear, greed, or empathy to pressure victims into compliance.Fear-Based Scams as the Threat of Penalties or Account Closure Gives False Urgency to Convict,Greed-Based Scams Rewarding immediate benefits like lottery wins or reward based benefits in return for sensitive information,Empathy-Based Scams,Requesting donations for fake charities, often during crises or disasters,How it works,This makes the victim have little time to validate what the attacker is trying to say.For Example,You’ve won a $10,000 prize! To claim it provide your bank account details for the transfer.
- Audio Recording Misuse: This strategy emphasizes the importance of collecting the victim’s voice authentication for deceptive purposes, potentially to create voice-activated commands or to bypass voice recognition systems. Typical attacks would involve an attacker questioning for specific responses, like “Yes” or “No,” and recording these, which are later misused.How it works and the attacker pretends that he conducts surveys or makes verification calls slowly extracting voice samples.For Example “Is your name [your name]?” Confirm only by saying ‘Yes’ if you keep Know them better know the red flags and be a scam avoider. Being extra careful on the telephone can keep you from being led into the harmful hands of these threats.
- Researching the Target: Scammers gather information about a potential victim through social media, data breaches, or their public records while appearing authentic.
- Spoofing Caller IDs: Attackers employ caller ID spoofing tools, where they masquerade their number as from a trusted source, such as a bank or a government agency.
- Creation of a Viable Excuse: They fabricate scenarios such as account issues, unpaid taxes, or claims for a prize to gain the victim’s trust and establish the victim’s urgency.
- Emotional Manipulation: They exploit emotions like fear, greed, and sympathy to control their victims. It can include threats of penalties, promises of rewards, or deceptive charity requests designed to extract money.
- Emerging Information: The attacker requests OTPs, credit card numbers, or account credentials. Even voice samples may be collected to avoid voice authentication applications.
- Data Construction: The compromised information is often used for identity theft, fraudulent purchases, or sold on the dark web, presenting a danger to individuals. Frequently, scammers trick victims into allowing remote access to their devices, which can result in additional theft and possible financial devastation.
- Obscuring trails: Attackers use disposable numbers, operate internationally, and often shift their tactics to avoid vishing prevention.
- Bank Fraud Alert Scam: A strong password is the first defense against a dictionary attack. Create a good password using uppercase and lowercase letters, numbers, and special characters. Do not use simple words or short phrases that can easily appear in a dictionary list.For Example,A suspicious transaction was detected with your credit card number. To protect your account validate the card number and OTP sent to your mobile.
- Government Agency Impersonation: A scammer claims to be a taxman or other official indicating threats of such men if one does not pay money.For Example:You owe $5,000 in taxes. Failure to pay today will result in legal action. Please provide your credit card details to settle the amount.
- Tech Support Scam:The attacker claims your computer has been hacked or infected with malware. They ask for remote access to fix it, often installing malicious software instead. To protect against such threats, employing Cryptographic Techniques can help secure your system and prevent unauthorized access to sensitive data.For Example Your Windows license has timed out. Now, the machine is at risk. Let me gain remote access to have it renew the subscription.
- Charity or Donation Scam: Scammers prey on emotional triggers during crises seeking donations for fake causes.For Example,We are collecting money for disaster relief. May I get a credit card donation in the name of?
- Job Offer Scams:The attacker presents an attractive job opportunity but requests money first for handling, background checking, or training.For Example,Congraulations! You have been shortlisted for a high-paying position. To finalize your application, please pay a $100 processing fee.
- Unsolicited Calls : Be guard against unsolicited calls from unknown numbers, especially those that ask for sensitive information.
- Pressure Techniques: Genuine organizations rarely demand immediate action or threaten consequences.
- Request for personal and financial information: Never give out sensitive information like passwords, PINs, or bank account numbers over the phone.
- Disturbing Payment Requests: Likely, some unconventional ways they seek to get paid are gift cards or cryptocurrency.
- Too Good to Be True Offers: Do not entertain calls claiming impossible rewards or prizes.
- Verification Requests: Legitimate companies primarily do not ring clients requesting detailed verification through a phone call.
- Case 1: IRS Scam in the US Attackers posed as Internal Revenue Service officials, threatening legal action unless victims paid “tax dues” via gift cards or wire transfers. This trick lured fraudsters into thousands of accounts.
- Case 2: Bank OTP Fraud in India Victims were called by fraudsters claiming to represent the bank, requesting OTPs to “validate” transactions which thereby unauthorized withdrawals from their accounts.
- Case 3: COVID-19 Donation Scams Many frauds, in this case, started with full-on blatant scamming pretending to be charity workers soliciting donations for nonexistent COVID-19 relief efforts.
Interested in Obtaining Your Vishing Attack Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How Vishing Works
In vishing or voice phishing, the hacker manipulates the victim over the telephone to fetch sensitive information. Here is how it looks in simple terms:
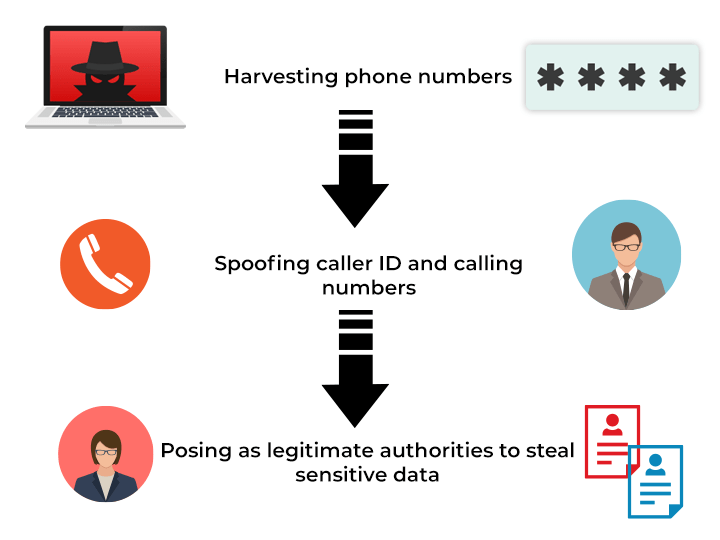
Vishing Attack Techniques
Cyber thieves use many tactics to make vishing calls sound legitimate. Some of these tactics include:Caller ID spoofing,makes it harder to tell fake calls from real ones since attackers spoof caller ID to show bank or government numbers.Impersonation,typically pretend to be well-known people, such as bank managers, IT support experts, or charity employees. They are required to quickly gain the victim’s confidence. Urgency and fear, along with psychological pressure, compel the victim to act without thinking critically. Cyber Security Training Courses can teach individuals how to recognize these psychological tactics and respond appropriately to avoid falling victim to such manipulation. Attackers create a sense of immediate danger by claiming your bank account will be frozen or even threatening legal action.Pretexting,This involves crafting a believable scenario. For instance, claiming fraudulent activity on a bank account and needing your account details to “secure” it.Baiting with offers or rewards,Some vishing calls promise too-good-to-be-true rewards, like lottery winnings or exclusive deals, but require victims to provide personal details or payment first.Recording and Verification, fraudsters can make the victim ‘confirm’ his data thus making him vulnerable to the crime.
Common Vishing Attack Examples
While both involve deception, smishing uses SMS to lure victims, whereas vishing prevention relies on phone calls to exploit trust and emotions. Both aim to steal personal or financial information. While both rely on deception, the immediacy and personal touch of voice communication make vishing prevention attacks particularly convincing.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
How to Detect Vishing Attacks
Do not use dictionary words, phrases, or predictable patterns such as “123456” or “password.” In addition, implementing Network Segmentation can help limit the impact of a compromised account by isolating sensitive systems from the rest of the network.
How to Protect from Vishing Attacks
Verify Caller Identity,When in doubt dial up and hang up and call the organization directly using the official contact information.Do Not Disclose Sensitive Information,Avoid sharing personal or financial details over the phone, especially if unsolicited.Permit Call Blocking,Block call software filters out known spam or fraudulent numbers.Educate Yourself,Learn the most common vishing prevention scams and warning signs.

Report Scams, report these calls to the authorities, such as your local cybersecurity agency or consumer protection body. Use Multi-Factor Authentication (MFA). Even though attackers may acquire your credentials, MFA stops unauthorized logins to your account. Additionally, implementing an Intrusion Prevention System can help detect and block malicious activities before they cause harm.
Real-life Examples of Vishing Scams
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Vishing attacks often begin with an unexpected phone call from someone pretending to be a legitimate organization, such as a bank, government agency, or tech support service. These attackers may use fear tactics or create a sense of urgency, claiming that your account has been compromised or that immediate action is needed to prevent further damage. Their goal is to manipulate you into providing sensitive information like passwords, Social Security numbers, or credit card details. Enrolling in Cyber Security Training Courses can help you identify these threats and develop strategies to protect your personal and financial information. By creating a false sense of trust and urgency, vishers can exploit human emotions to lower defenses and increase the likelihood of falling victim to the scam. To protect yourself from vishing, it’s important to approach unsolicited phone calls with caution. Never share personal or financial information over the phone unless you are certain of the caller’s identity. When in doubt, hang up and call back using a verified phone number, such as the one found on your official bank statement or website. Additionally, be wary of callers who ask for immediate action or threaten dire consequences, as these are common signs of fraudulent attempts. Regularly monitoring your accounts and credit reports can also help detect any unusual activity early on, giving you a better chance to take action before the damage is done.





