
- Define Internet control message protocol?
- Purpose of ICMP
- ICMP Flood Attack
- How can ICMP Work?
- Explain ICMP Port?
- Disadvantages of ICMP
- Conclusion
The ICMP is an essential protocol inside the Internet Protocol (IP) suite, designed to help blunders reporting, diagnostics, and community control tasks. Unlike different protocols that convey personal data, ICMP is utilized by community gadgets like routers and hosts to ship messages that tell of community troubles or reputation changes. Commonly related to equipment like “ping” and “traceroute,” ICMP gives comments on community connectivity, latency, and routing paths that are crucial for diagnosing troubles like unreachable hosts, packet loss, or immoderate transmission delays. ICMP is an supporting protocol withinside the Resolution Protocol suite that community gadgets often use to ship mistakes in addition to different applicable information.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Define Internet control message protocol.
ICMP is part of the TCP/IP protocol stack. It is a mistaken message protocol that integrates the primary Internet Protocol and is located at the Internet Layer. The first interpretation of ICMP was written by Jon Postel, one of the net’s pioneers. When community troubles block IP packet delivery, community gadgets together with routers supply mistakess messages to the supply IP deal with the usage of ICMP ( Cyber Security Training Courses ). ICMP generates and transmits records to the supply IP deal by notifying it that a packet transmission net gateway, together with a router, service, or host, is down. Any IP community tool can send, accept, and manner ICMP messages.
Purpose of ICMP
- IP lacks an integrated mechanism for sending manipulated and blunder messages. That is why a protocol consisting of ICMP is required. In realistic terms, ICMP offers blunder manipulation and is regularly used to file errors and ship strategic queries and operations details.
- To ship error messages, community gadgets such as routers have to use ICMP. As a result, ICMP is seen as a helping protocol.
- Although the decreased Internet Layer no longer needs to be concerned with connection affirmation, ICMP is vital for treasured remarks when troubles arise.
- They intend to disrupt the same old community performance. They release numerous attacks, together with an ICMP flood, a IP Subnet , and a Ping of loss of life attack. Intruders are targeted to dominate the sufferer and disable widespread connectivity.
ICMP Flood Attack
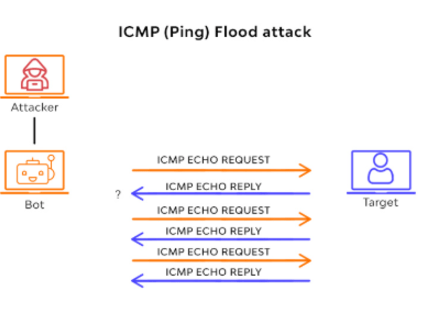
- Ping of Death Attack: A ping of loss of life assault takes place while an attacker sends a ping to a centred device that is larger than the maximum allowable length for a packet, inflicting the tool to freeze or collapse.
- Smurf Attack: The attacker makes use of a faux internet site supply IP cope with to ship an ICMP packet in a Smurf assault Ransomware in Cybersecurity . Networking gadget responds to the packet by sending responses to the faux IP to cope with and bombarding the sufferer with undesired ICMP packets. The Smurf assault, like the `ping of loss of life,` is best feasible with status gadgets today. It is used to expect community performance. It is operated and utilized by famous utilities, Traceroute and Ping. They each supply texts indicating whether or not or now no longer the facts become correctly transmitted.
- Traceroute command: The traceroute command is beneficial for depicting and explaining the routing course taken through distinct Internet devices. It shows the bodily course of related routers that manipulate and switch the inspiration until it reaches its very last vacation spot. Each adventure from one router to any other is called a “hop.” The traceroute command additionally shows the time it took for every hop along the way. This kind of fact is remarkably beneficial for figuring out which community factors alongside the course are inflicting disruption.
- Ping command:The Ping command is comparable but more complex. It measures the velocity of a connection among factors, and the file indicates how lengthy it takes a packet of data to attain its destination and return to the user’s tool. Although the Ping command no longer provides additional statistics about routing or hops, it is a completely beneficial device for figuring out the lag between factors.
- No Error Reporting: If the router discards a records transmission, it may be because of an error; however, there may be no mechanism inside the net protocol that permits the sender to be notified of this error. Assume that the life of a records packet is finished at the same time as visiting over the net, and the cost of the time to stay subject inside the records packet has emerged as zero; in this case of Database Security, the records packet could be discarded.
- No Communication: It is not unusual for one tool to want to engage with another, but Internet Protocol lacks a system for gadgets to share information. For Example, before shifting the records, the host has to decide whether the vacation spot continues to be alive or not.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training .
How Can ICMP Work?
ICMP is a connectionless protocol, which denotes that the transmitter no longer wants to set up a reference to the receiver earlier than transmitting the information. This is why it varies from TCP, for example, in which a hyperlink among gadgets is required. A message can simplest be despatched while each gadgets are geared up thru a TCP handshake. All ICMP messages are forwarded as datagrams with an IP header containing the ICMP statistics. Each datagram is a self-contained, statistics-unbiased entity. Consider it a packet that transports a fragment of a bigger message everywhere in the Network Topology IP packets with ICMP inside the IP statistics component are called ICMP packets.ICMP messages include the complete IP header from the unique message. As a result, the goal machine is aware of which particular packet failed.
Explain ICMP Port.
As formerly stated, the Cyber Security Training Courses is a detail of the Internet protocol suite, additionally extensively diagnosed because of the TCP/IP protocol suite. That is, it is miles restrained to the Internet Layer. Only on the Transport Layer, the layer above, do port numbers look like they were discovered.The (ICMP) does now no longer use ports like TCP and UDP. However, it does use kinds and codes. The ICMP kinds echo request and echo reply (used for Ping) are usually used, and TTL (time-to-live) is passed in transit (used for Traceroute).ICMP does now no longer use ports like TCP or UDP as it operates on the Network Layer (Layer 3) in place of the Transport Layer (Layer 4) of the OSI model. Ports are unique to protocols like TCP and UDP, which control application-unique connections at Layer 4. Instead, ICMP is designed to talk community-stage information, inclusive of mistakes and standing updates, without delay among community gadgets like routers and hosts.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
This shape lets ICMP ship manage messages approximately problems like unreachable destinations, congestion, or packet timeouts, which are critical for community diagnostics. Since ICMP operates without ports, it is predicated on unique “message kinds” to become aware of the cause of every message. For example, “Echo Request” (kind 8) and “Echo Reply” (kind 0) messages are usually utilized in the “ping” tool, at the same time as different kinds, like “Destination Unreachable” or “Time Exceeded,” sign unique community conditions. This portless nature makes ICMP precise in the IP suite, focusing completely on community management and troubleshooting in place of records transport.
Disadvantages of ICMP

The extensive risks of Internet protocol are indexed below. To fully recognize the ICMP requirements, you must first recognize those limitations.
Ready to pass the interview for cybersecurity ? Learn how to answer Cybersecurity Interview Questions and Answers .
Conclusion
The Cybersecurity Training Courses is a terrific community layer protocol that allows gadgets to tell mistakes and enhance interactions. Furthermore, it is it’s miles a first-rate community diagnostic tool. It is not sudden that many directors use it each day to expand a higher know-how in their community through the use of famous utilities like Ping and Traceroute. ICMP performs an essential function in keeping community fitness and stability. By presenting a mechanism for mistake reporting and standing queries, it permits green community troubleshooting and optimization. Although ICMP itself does not transmit consumer data, its signalling competencies contribute notably to the reliability of IP networks, making it a foundational thing in community control and diagnostics. Proper use and tracking of ICMP can beautify community safety and performance, at the same time as misuse or blockading of ICMP can preclude community diagnostics, emphasizing the significance of balanced ICMP control in community configurations.





