- PUP in Cyber Security: What Is It?
- Potentially Unwanted Program kinds in cybersecurity
- PUP Enter Your Computer
- Guard Against PUP
- How Can PUP Be Removed?
- PUP Be Recognized
- Conclusion
The term PUP is abbreviated as Potentially Unwanted Program. It refers to software in cyber threads that has the potential to harm or negatively impact the system but does not itself. Examples include adware, toolbars, and additional unwanted applications that don’t pose a direct threat but nevertheless cause the system to function less than optimally, Web Security display intrusive ads, or raise privacy issues.
PUP in Cyber Security: What Is It?
Potentially Unwanted Programs are malicious programs that are frequently included with trustworthy ones. Usually, it carries out undesired tasks like showing intrusive adverts, changing browser preferences, or gathering user data without explicit agreement. It does not fall under the same category as Trojan horses, worms, or ransomware because they typically do not use malevolent methods or take advantage of network security flaws to infiltrate a computer. They are typically detected and removed by antivirus and pup malware Software in Cybersecurity Training Courses. The greatest ways to avoid downloading them further throughout the installation process are to download Software from reliable sources and carefully read installation prompts . Although they do not harm systems in the same way as ordinary pup malware, they can still breach user privacy and cause issues with the user experience. Therefore, knowledge and avoidance are crucial for overall cyber threads.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
PUP kinds in cybersecurity
- One of the most prevalent kinds of cybersecurity program is adware. In an effort to earn money for the developers, it appears on a user’s computer as unsolicited pop-ups, banners, and ads, frequently within web browsers.
- Browser hijackers are programs that alter a web browser’s settings without the user’s permission. They might add undesirable browser extensions or alter the homepage and default search engine.
- Add-ons or browser extensions are called toolbars. They enhance a web browser with new features or capabilities. Although some toolbars are helpful, many are regarded as cybersecurity program as they frequently come packaged with other programs of Keylogger and might generate a cluttered browser interface.
- It certainly gathers user data like surfing preferences, search terms, or private information without the user’s express agreement as cyber threads. This information may be sold to outside parties or used for marketing purposes.
- A few claim that cleaning or optimising a computer increases system performance. Nevertheless, they frequently overstate their expertise and could persuade customers to pay for pointless services.
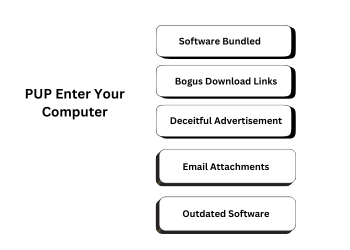
- Software Bundled:Occasionally, after downloading and installing a genuine program, other Software you might not want is included in the package. During the installation procedure, you may unknowingly agree to or ignore the installation of these additional cybersecurity program.
- Bogus Download Links:When looking for files or Software online, you may encounter bogus download links. Clicking on these URLs can inadvertently install Potentially Unwanted Programs..
- Deceitful Advertisements: Certain internet advertisements may entice you to click on them by implying that your machine is infected with a virus or that you want to upgrade your Software. It may download to your computer as a result of these adverts.
- Email Attachments: Exercise caution when opening attachments from unknown senders. Your computer may become infected with cybersecurity program or other pup malware if you do in Resolution Protocol .
- Outdated Software: it may be able to access your computer by exploiting security flaws in out-of-date Software or plugins.
- Employ malware or antivirus software
Use reputable antivirus or pup malware software to do a thorough system scan. These tools are efficient at locating and eliminating cybersecurity program.
- Eliminate Questionable Programs
Uninstall any software that you believe to be a cybersecurity pup by going to the “Control Panel” (Windows) or “Applications” (Mac) on your computer.
- Take out the browser’s extensions
Launch a web browser (such as Edge, Firefox, or Chrome). Navigate to the add-on or extension settings in the browser.
- Reset Browser Settings:
If cybersecurity pup has changed your web browser’s homepage and search engine, you can restore them to their original settings by looking for the “Reset” and “Restore” options in the settings menu.
- Remove Browser Caching and Cookies:
Your browser can leave behind tracking and undesirable data that can be removed by clearing the cache and cookies. Check your browser’s preferences or settings for this option.
- Examine Startup Programs
Make sure there are no questionable entries in your computer’s startup programs that might launch cybersecurity pup when it boots up.
- Perform Manual File and the Registry Cleanup (Advanced):
Perform Manual File and the Registry Cleanup (Advanced): You can manually look for and remove related files and registry entries if you are an advanced user. Handling the system of files and registry on your computer can be dangerous, so proceed with caution. Verify your expertise before acting in Malware Attack .
- Install a Reputable Ad Blocker:
You should consider utilizing a reputable ad blocker program or extension to prevent unsolicited advertisements from appearing.
- Remain Educated and Exercise Caution
To ensure safe browsing practices, choose carefully what software you install on your computer. Update the operating system frequently, and make sure your network security software is current.
- Seek Expert Assistance If Necessary
Seek assistance from an experienced technician or cyber threads specialist if you’re unsure how to remove or believe your machine has been badly affected.
- Remove Browser Caching and Cookies:
Your browser can leave behind tracking and undesirable data that can be removed by clearing the cache and cookies. Check your browser’s preferences or settings for this option.
- Unexpected Toolbars: It may be present if you unexpectedly discover new toolbars in your internet browser that you did not intentionally install. It may have infiltrated your device if you notice a lot of bothersome pop-up advertising that appears out of nowhere.
- Slow Computer:If you’ve noticed a noticeable slowdown in your Computer, it may be using up system resources.
- Modifications to Browser Settings: It frequently alters your browser’s new tab page, search engine, and homepage without your permission. If you observe these developments, it’s a warning sign.
- Unfamiliar Programs:Review the unwanted applications and programs you’ve uninstalled. Any unusual software you encounter might be a PUP.
- Overzealous Prompts: It may constantly pester you to install or update software. If these suggestions seem aggressive or are from unidentified sources, proceed cautiously Network Topology .
- Websites of Doubt: it may be present if you are forwarded to dubious websites or if your web searches return surprising results.
- Privacy Concerns: It may gather personal data or surfing history from you. If privacy is an issue, any unfamiliar programs should be thoroughly investigated.
- Security program Alerts: Occasionally, your antivirus or anti-malware program may identify and flag it. Be mindful of these cautions.
- Unwanted Expansions:Examine your online browsers, such as Chrome and Firefox, for any extensions you did not install.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
PUP Enter Your Computer
Guard Against PUP
Download programs, add-ons, and software from official, trustworthy sources only. Stay away from unofficial download sites. Verify user reviews and ratings before installing software to make sure others have had good luck with it. Always select the advanced or custom installation option when installing software. This allows you to examine and remove any cybersecurity pup or bundled unwanted applications. During installation, take the time to read the Terms of Service or end-user License Agreement (EULA). Seek for provisions for the installation of additional software. Update your network security software, web browsers, and operating system regularly. Patches to defend against known this sare frequently included in updates. Set up and update reputable pup malware and antivirus programs regularly Cybersecurity Training Courses. These tools can assist in locating and blocking. Most web browsers have security settings that you can use to prevent or alert you to potentially dangerous websites or downloads. Refrain from clicking links or opening email attachments from unidentified or dubious sources. Phishing emails are one way that can be shared. Consider utilizing a reliable advertising blocker extension or program to stop fraudulent adverts that could lead to installations.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
How Can PUP Be Removed?
Prepare For Your Cybersecurity Interview Questions and Answers With Our Comprehensive Cyber Security Interview Questions Bank. Get Started Now!
PUP Be Recognized
Conclusion
Read user reviews, only download software from reputable sources, and adjust installation settings to prevent bundling to protect yourself. Use reputable antivirus software, be cautious when opening attachments from emails and clicking links, and keep your network security equipment and software updated Cybersecurity Training. Ensure your browser is secure, use safe browsing techniques, and avoid clicking on pop-ups and advertisements in unwanted applications. You can maintain a safe and clean digital environment free from Potentially Unwanted Programs by adhering to these instructions and keeping informed.