
- Introduction to SSL/TLS Protocol
- Role of SSL Handshake in Secure Communication
- Step-by-Step Process of SSL Handshake
- Key Exchange and Authentication in SSL Handshake
- The Role of Certificates in SSL Handshake
- Cipher Suites in SSL Handshake
- Troubleshooting SSL Handshake Issues
- Conclusion
SSL and TLS are used to secure the communication between a client (such as a web browser) and a server, ensuring data confidentiality, integrity, and authentication. Cybersecurity Training Courses achieve this by encrypting data transmitted between the client and server, preventing eavesdropping and tampering with the data. Websites use SSL/TLS to protect sensitive information such as passwords, credit card details, and other personal data.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Introduction to SSL/TLS Protocol
The SSL (Secure Sockets Layer) and TLS (Transport Layer Security) protocols are cryptographic protocols designed to provide secure communication over a computer network, most commonly the Internet. An SSL Certificate plays a crucial role in this process by verifying the identity of websites and enabling encrypted connections, ensuring data integrity and security. SSL was the original protocol developed by Netscape in the 1990s, but due to security Vulnerability Management , it was replaced by TLS, a more secure version of the protocol. TLS has undergone several iterations to improve its security features, and it is the current standard for secure communication. A TLS Certificate plays a crucial role in this process by ensuring authentication and encryption, making online interactions more secure.
Role of SSL Handshake in Secure Communication
The SSL handshake is a crucial part of the SSL/TLS protocol. The initial process establishes a secure connection between the client and the server. During the handshake, several key parameters, including encryption keys, RSA Algorithm preferences, and certificates, are exchanged to ensure the communication channel is secure. The SSL handshake involves authenticating both parties (client and server) and agreeing on the encryption methods for the session.
The purpose of the SSL handshake is to:- Authenticate: Authenticate the server (and, optionally, the client) to verify their identities.
- Agree on encryption algorithms: Agree on encryption algorithms and cryptographic keys to ensure secure communication.
- Establish a secure communication channel: Establish a secure communication channel where data is transmitted confidentially and without tampering. Once the handshake is complete, the client and server can exchange encrypted data over the secure connection.
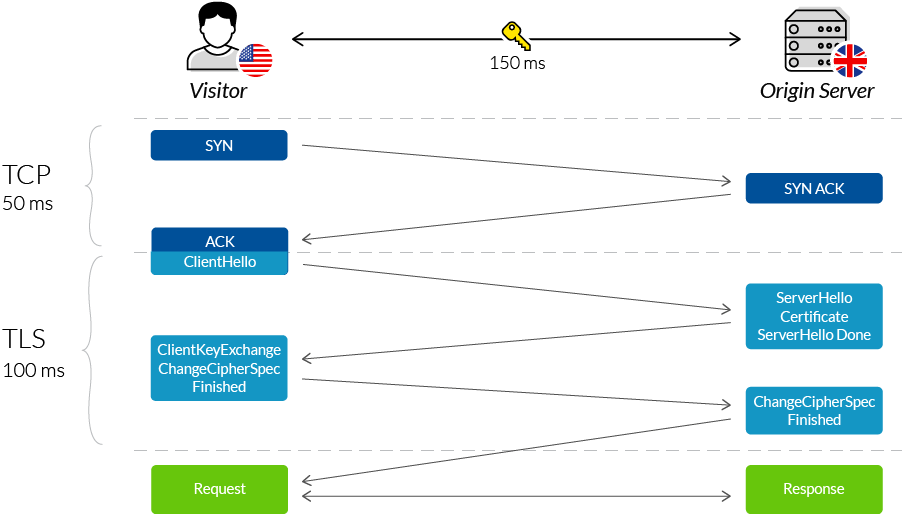
Step-by-Step Process of SSL Handshake
The SSL handshake involves a series of steps, each ensuring the connection is secure before exchanging data. Below is a step-by-step overview of how the SSL handshake works Client Hello The client (e.g., a web browser) sends a ClientHello message to the server. This message includes The version of SSL/TLS that the client supports. A list of supported cipher suites (encryption algorithms). A randomly generated number called the client random. The session ID (if resuming a previous session). The client also specifies the compression methods it supports. Server Hello The server responds with a ServerHello message. This message includes The chosen SSL/TLS version. The selected cipher suite. A randomly generated number is called the server random. The Session Hijacking ID (if continuing a previous session). The server also sends its digital certificate containing the public key and other identifying information. Server Authentication and Pre-Master Secret If the cipher suite chosen requires authentication, the server sends a digital certificate to the client. This certificate contains the server’s public key and is signed by a trusted Certificate Authority (CA).
The client verifies the server’s certificate using the CA’s public key to ensure its authenticity. Once the certificate is validated, the client generates a pre-master secret, encrypts it using the server’s public key (from the certificate), and sends it to the server. This pre-master secret is used to generate session keys for encrypting data. Session Key Generation The client and the server use the pre-master secret and the two random numbers (client and server random) to generate the same session keys. These session keys will be used to encrypt and decrypt data during the session. Client Finished The client sends a Finished message, encrypted with the session key, to indicate that the client has completed its part of the handshake and that the key exchange was successful. Server Finished The server sends its Finished message, also encrypted with the session key, to indicate that the server has completed the handshake successfully. After these steps, the SSL/TLS handshake is complete, and the client and the server can securely exchange encrypted data.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Key Exchange and Authentication in SSL Handshake
The key exchange and authentication processes are crucial for establishing a secure SSL/TLS handshake connection.
Here’s how these steps work:- Key Exchange: The key exchange ensures that the client and the server end up with the same session keys for encryption and decryption. In earlier versions of SSL/TLS, RSA was commonly used for key exchange, but modern protocols often use Elliptic Curve Diffie-Hellman (ECDHE) for better security and efficiency. This method allows both parties to exchange keys securely without transmitting the private key. The client uses the server’s public key (from its certificate) to securely send the pre-master secret, which is then used to derive the session keys.
- Authentication: The server authentication is achieved by the client verifying the server’s digital certificate, issued by a trusted Certificate Authority (CA) in Cybersecurity Training Courses . The certificate contains the server’s public key and identifies the server’s domain name.Client authentication can be optional. If required, the client will send its certificate to the server, and the server will verify it similarly. Authentication ensures both parties are who they claim to be and helps prevent man-in-the-middle attacks.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
The Role of Certificates in SSL Handshake
Certificates play a vital role in ensuring the security and authenticity of the connection in an SSL/TLS handshake. The server sends its digital certificate to the client during the handshake.
This certificate serves the following purposes:- Authentication: The certificate proves the identity of the server. It is issued by a trusted Certificate Authority (CA), a third-party organization that verifies the legitimacy of the server’s identity.
- Public Key: Public Key Cryptography certificate contains the server’s public key, which the client uses to encrypt the pre-master secret for secure exchange.
- Digital Signature: The certificate is signed by the CA using the CA’s private key. The client uses the CA’s public key to verify the certificate’s authenticity and ensure it hasn’t been tampered with.
Cipher Suites in SSL Handshake
A cipher suite combines cryptographic algorithms used during the SSL/TLS handshake to secure the communication channel. Each cipher suite specifies Key Exchange Algorithm. This algorithm determines how the client and server exchange keys. Common key exchange algorithms include RSA, ECDHE (Elliptic Curve Diffie-Hellman), and DH (Diffie-Hellman). Encryption Algorithm This algorithm Hashing vs Encryption the data transmitted between the client and server. Examples include AES (Advanced Encryption Standard) and 3DES (Triple DES). Message Authentication Algorithm This algorithm ensures the integrity of the data by creating a hash that verifies the data hasn’t been tampered with. Common algorithms include SHA-256 and HMAC. Hashing Algorithm The hash function is used to verify data integrity. Examples include SHA-256 or SHA-1.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Troubleshooting SSL Handshake Issues
SSL handshake issues can occur for various reasons, such as incompatible cipher suites, expired certificates, or network problems.
Here are common SSL handshake issues and troubleshooting steps:- Certificate Errors: Ensure that the server’s certificate is valid and not expired. Check if the certificate is correctly installed on the server and matches the domain name. Verify that the certificate is signed by a trusted Certificate Authority (CA).
- Incompatible Cipher Suites: Check if the client and server support common cipher suites. Some older browsers or servers may not support modern encryption algorithms. Ensure that the SSL/TLS protocol versions are compatible on both sides.
- Protocol Mismatch: Ensure that the client and server support compatible versions of SSL/TLS. For instance, TLS 1.2 is more secure than SSL 3.0, and many servers have disabled SSL 3.0 due to its vulnerabilities.
- Firewall or Network Issues: Check if any Firewall and Antivirus Software or proxies are interfering with the SSL handshake. Firewalls may block the necessary ports (typically 443 for HTTPS).
- Server Configuration: Review the server’s SSL/TLS configuration settings. Ensure that it supports the necessary versions of TLS and has the correct cipher suites enabled.
Conclusion
The SSL/TLS handshake is a vital process that initiates a secure communication channel between a client and a server over the internet. It involves several key steps, starting with the client sending a “ClientHello” message to the server, which includes supported encryption methods was learned in Cybersecurity Training . The server responds with a “ServerHello,” selecting a cipher suite and presenting its digital certificate to authenticate its identity. This certificate contains the server’s public key, allowing the client to verify the server’s authenticity using a trusted certificate authority. The client then generates a pre-master secret, encrypts it with the server’s public key, and sends it to the server. Both parties use this secret to generate session keys for encrypting and decrypting the data. Throughout the handshake, both confidentiality and integrity are ensured, protecting the data from interception or tampering. The process concludes with a “Finished” message, signaling that the secure connection is established and data can now be transmitted safely.





