
Introduction
With the world getting digitally more active session hijacking with online interactions and transactions, threats have existed since immemorial. Session hijacking is one of the big threats today for users and Vulnerability Management Since active session hijacking hijacking could be a way to reach all kinds of sensitive information, knowing how it works can help any online individual navigate their way out. In this blog, basic active session hijacking concepts and some techniques used by session fixation attack with real-world examples of how it works in reality.
Become an expert in cyber security. Enroll in this Cyber Security Online Training now to acquire the knowledge you need.
What is session hijacking?
It involves hijacking a cyber hijacking who, after taking a user’s session after the latter has been successful with the web application login authentication, normally takes away session identifiers. Session IDs manage user sessions in this web application, which targets every login activity. As one logs into a particular account, the server initiates a session and creates a unique ID number, Malware Analysis which is kept within the cookie or passed on to the user as part of the URL parameter.
After obtaining this session ID, Web Security an session fixation attack can assume the victim’s identity and access the account and its associated data without requesting login credentials. This ultimately results in illegal transactions and data theft, which frequently result in serious confidentiality violations.
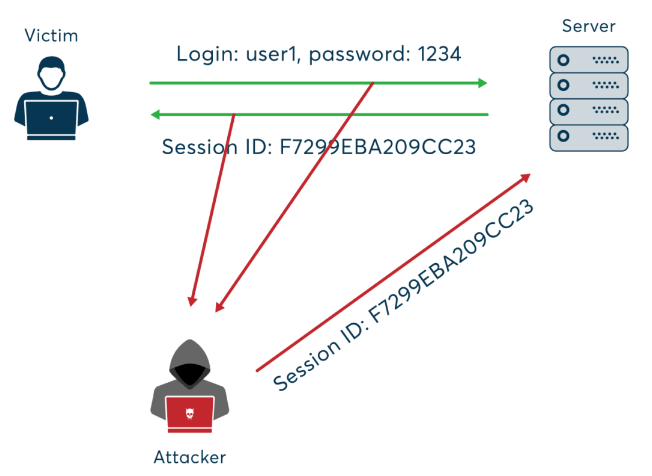
Methods of Session Hijacking
Various approaches are used to implement Cybersecurity Training Courses attacks. It is crucial for developers and users to familiarize themselves with these methods to protect their online presence.
1. Session Fixation
Session fixation is an session fixation attack in which an attacker makes a user log in to a web application with a pre-set session ID. The attacker obtains a session ID and then persuades the user to use it, usually through a link that contains the session ID in the URL. Once the attacker is logged on, he can hijack the session by taking advantage of the fixed session ID. This attack succeeds if the web application does not regenerate session IDs after authentication.
2. Cross-Site Scripting (XSS)
A flaw known as cross-site scripting (XSS) allows hackers to insert harmful code onto the web pages accessed by other users. By exploiting XSS, an attacker can steal session cookies directly from the victim’s browser. When a user accesses an exploited page, the bad script can run in their browser and forward the session ID to the attacker. This technique shows the importance of validating and sanitizing user input to prevent such vulnerabilities.
3. Packet Sniffing
Packet sniffing intercepts data packets as they travel over a network security. In this method, an attacker can capture session IDs transmitted over an unsecured network security, such as a public Wi-Fi. One can use tools like Wireshark to intercept data. To avoid packet sniffing, you should use encrypted Resolution Protocol . For example, HTTPS encrypts data in transit; thus, it becomes significantly harder for attackers to read.
4. Man-in-the-Middle (MitM) Attacks
In a Man-in-the-Middle attack, a hacker secretly intercepts the communication between two parties and relays it back. This results in stealing session tokens from the users and manipulating their data. MitM is very effective when used over unsecurednetwork security that do not enforce encryption firewall security . Using a VPN and making sure websites use HTTPS can work to mitigate this risk factor.
5. Malware
Other harmful uses of sessions include cookie hijacking by malware like keyloggers or trojans that record keystrokes and screen information. It may even steal session IDs stored in cookies or local storage. Keep your hijacking in cyber security software updated, and you will always browse the web safely to avoid any malware threat.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
Real-World Examples of Session Hijacking
The session hijacking can be best understood through real-life scenarios and the measures that can be taken to avoid this attack.
Example 1: Facebook Session cookie hijacking Incident
In 2011, a major hijacking in cyber security breach of Cybersecurity Training Courses was reported on Facebook. The attackers exploited an XSS vulnerability, which allowed them to steal session cookies from the users. After getting these cookie hijacking, the attackers could easily log into the victims’ accounts without requiring passwords. In return, Facebook had to strengthen its security. That meant input validation improvements and features such as “Login Alerts,” where a user is alerted about an unrecognized login.
Example 2: Online Banking Fraud
In another scenario, hackers hijacked users’ online banking sessions and targeted them. They resorted to packet sniffing over public Wi-Fi network security at cafes to steal session IDs. After getting hold of the active session hijacking, they altered transactions, which led to huge losses for the targeted victims firewall security . Banks responded by tightening their hijacking in cyber security systems,firewall security such as two-factor authentication, and closely monitoring suspicious activities.
Example 3: Yahoo Data Breach
Yahoo had one of the most significant data breaches in 2013 when hackers compromised over three billion accounts. Although this breach utilized different approaches, one of them was session cyber hijacking, which relied on the compromised stolen credentials. After the breach, Yahoo made additional Database Security changes, forcing a password reset and encrypting data with a higher grade.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Preventing Session Hijacking
Session hijacking needs to be protected by users and developers with preventive security measures. Implementing strong encryption, secure session management, and multi-factor authentication can significantly reduce the risk.
For Users:
- Select Strong Passwords: Select something impossible to recall for everyone; different ones for accounts each.
- Enable Two-Factor Authentication: This needs access, rather than a pass for a secured way to look for authentication.
- Do not use public WIFI: Not secured and try the Vulnerability Management to make you feel even better and get that.
- Log Out After Use: Users should log off each time they are done. Logging out should be automatic every time with the one-time log out while on an office-shared laptop.
- Session ID Regeneration: Always generate a new session ID after the authentication phase to avoid a session fixation attack.
- Using Secure Cookies: Set cookies with “Secure” and “HttpOnly” flags to restrict access and transmit less
- Input Validation: Preventing XSS by validation and sanitization of input from the user.
- Suspicious Activity Monitoring: Use logging and monitoring for possible cookie hijacking attempts.
For Developers:
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Conclusion
Cybersecurity Training remains one of the top cybersecurity threats, impacting users and organizations similarly. Information about the attack methods, including the active session hijacking fixation attack, and knowledge gained through real-world experiences can be applied to devise effective security measures. When best hijacking in cyber security practices are implemented in firewall security , sensitive information becomes safer for users, and developers can create web applications that better protect their clients. As technology and cyber hijacking evolve, staying vigilant is essential for everyone operating within the digital realm.





