- Cybersecurity: What is it?
- Cybersecurity Types
- Advantages of cyber security
- Cybersecurity cons
- Best Practices for Effective Cybersecurity
- Important Cybersecurity Concepts
- Conclusion
Thus, cybersecurity has become essential to protect sensitive information and generate confidence in online communication, especially in the virtual world. The more dependency there is on technology, the more dangers there are about cyber threats, data breaches, ransomware attacks, etc. While adopting cybersecurity measures has benefits like protection of personal data, compliance with regulations, and enhancement of the reputation of organizations, it has negatives like high costs, complexity, and user resistance. This current study on the Cyber Security Training Courses aims to proffer a balanced view of its implications for individuals, business organizations, and society.
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training.
Cybersecurity: What is it?
It protects against theft, unauthorized access, and other network, computer systems, and private information damage. Cyber security comprises many different types of security measures designed to prevent cyber attacks, safeguard private information, and put in place things such as intrusion detection systems, firewalls, antivirus software, and encryption. Cyber security is one of the key requirements as our lives get increasingly digitalized; it forms a part of our individual and professional lives.
Cyber security refers to protecting the safety, integrity, and accessibility of information. The ability to ensure that data is correct and consistent is referred to as integrity. Keeping private information from unwanted access is known as confidentiality. Availability guarantees that authorized individuals may access data as needed. Protection from Cyber Insurance and other online threats like phishing, malware, and hacking fall under cyber security. People and businesses can take protective measures against such threats by implementing efficient cyber security measures to protect themselves to ensure their networks and systems’ safe, effective, and uninterrupted functioning.
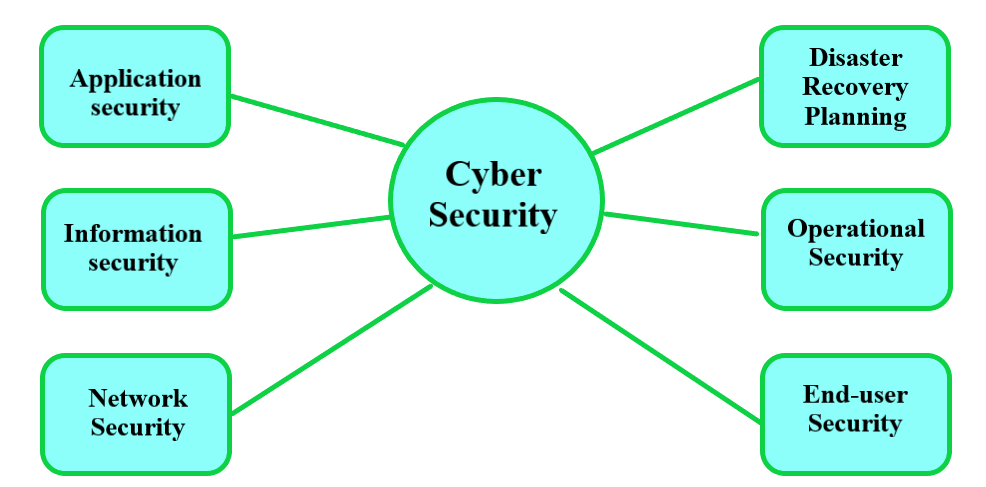
Cybersecurity Types
- Security of Networks:Network security protects computer networks from theft, damage, and illegal access. This entails implementing security methods like VPN and Secure Sockets Layer, or SSL, cryptography and safeguarding switches, routers, firewalls, and other types of network equipment.
- Cloud Protection:The essence of cloud security is protecting data and applications stored in the cloud. Cloud security measures can include monitoring, access limits, and encryption to prevent illegal access or data breaches.
- Security of Applications:Protecting software applications from online attacks like SQL injection and cross-site scripting is the focus of application security. This entails performing routine vulnerability and penetration testing and implementing security measures like firewalls, access controls, and encryption.
- Data Protection:The essence of information security is protecting sensitive data, including financial, personal, and intellectual property information. This includes conducting regular risk assessments, conducting security audits, and implementing policies and procedures for data classification, access controls, and retention.
- Security of Endpoints: Endpoint security involves protecting certain devices, such as laptops, desktop computers, and mobile devices, from Cyber Media. This includes installing firewalls, antivirus software, and other security measures to stop malware.
To Learn About Different Cyber Security Techniques, Sign Up for Our Cyber Security Course Right Now!
Advantages of cyber security
- Guards Against Internet Dangers:Cybersecurity’s ability to defend against internet attacks is among its most significant advantages. Due to the increase in cybercrime, Cyber Security Training courses is now crucial to protecting sensitive data, including financial, intellectual, and personal information. Cybersecurity solutions that can help stop unwanted penetration of networks and systems include intrusion detection systems, firewalls, and antivirus software.
- Improves Data Privacy:One direct result of cyber security’s contribution is better data privacy. Encryption and other security measures can protect sensitive data and avoid unwanted access. This is especially important for businesses managing private information, including customer and financial information.
- Encourages the continuation of business: cyber may result in severe financial losses and damage to a company’s reputation. Cybersecurity measures can help avoid these attacks, guaranteeing that the business can continue even in the event of a security breach. Businesses may minimize the impact of a cyberattack and recover quickly with regular backup and disaster recovery strategies.
- Boosts Client Trust:Cybersecurity measures may also increase client trust. Businesses that have a solid reputation for protecting their customers’ personal information are more likely to win their business. By implementing strong cyber security measures, companies can show dedication to safeguarding customer data and fostering loyalty and trust.
Leverage Cyber Security to Unlock the Future! Enroll in the Master of Cyber Security Program at ACTE Right Way !
Cybersecurity cons
Cost One of cyber security’s primary drawbacks is the expense. Strong cyber safety precautions can be costly, particularly for small organizations with little funding. Adopting cutting-edge hardware and software, training staff, and continuing maintenance and updates are some examples of costs.Intricacy Because online safety is a complicated topic, specific knowledge and skills are needed. Small organizations may find it challenging to deploy and maintain efficient security measures because they lack the funds to hire specialized cyber security specialists.Inauthentic Feeling of Safety E-mail Security measures can create a false sense of security even while protecting against various online threats. Cybercriminals always devise new methods and strategies to circumvent security measures, making even the strongest defenses susceptible to compromise.Possibility of Human Error One of the biggest risks to cyber security is human error. Workers might unintentionally download a file containing a virus or click on an infected link, endangering the network as a whole. Human error can still pose a serious risk even with strong security measures.
Best Practices for Effective Cybersecurity
- Regular Risk Assessment The identification of vulnerability and risk, essential for effective cybersecurity, must be done regularly. Regular assessment helps organizations stay one step ahead of emerging risks.
- Comprehensive Security Policies Clear security policies and protocols with defined roles for each employee to protect sensitive information.
- Employee Training Programs The employee training program provides ongoing awareness of potential threats and encourages employees to use safe practices when online, preventing human errors.
- Multi-layered security approach Various combinations of security measures will enhance security. Firewalls, encryption, and intrusion detection systems are some Database Security measures used in multi-layered approaches.
- Awareness of threat trends Updates on the cybersecurity trends and threats that can be happening around the organization, and organizations will keep adapting their defences based on what is found.
- A culture of security awareness will allow free communication about security concerns. This will create a culture of awareness, and employees will then be able to take more active roles in security Frequent updating and patching help ensure that software and systems are as current as possible to help protect against known vulnerabilities.
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions!
Important Cybersecurity Concepts
- Confidentiality safeguards sensitive information by preventing unwanted access. Data classification, access controls, and encryption are crucial tools for this. Confidentiality is necessary to protect intellectual property, financial information, and personal data.
- The term “integrity” refers to the precision and coherence of data. Steps like data backups, version management, and data validation can greatly aid in maintaining data integrity, which is crucial for protecting against data corruption and preserving information accuracy.
- Ensuring that information is accessible to authorized users at the appropriate time is known as availability. Strategies like redundant operation, failover, and preparation for disaster recovery can help accomplish this. Ensuring availability is essential to avoid downtime and ensure the continuity of business activities.
- Authentication is the process of verifying a person’s or device’s identity. It can be accomplished using multi-factor authentication, biometrics, and passwords. Web Security is necessary to prevent unwanted access to networks and systems.
- Authorization is the process of granting access to resources according to user roles and permissions. Privilege management and access controls can be useful in this regard. Authorization is essential to prevent unwanted access to resources and sensitive data.
- Holding people and organizations accountable for their deeds is known as accountability. Logging and auditing are two methods for accomplishing this. Detecting and responding to cyberattacks and other security issues requires accountability.
Conclusion
The Cyber Security Training is one essential factor that guards our lives digitally. It provides immense data security, financial stability, and public safety benefits. However, the challenges associated with the implementation must be addressed; there are costs, complexity, and the dynamic nature of threats. Organizations must balance the strength of the security measures and the user experience while promoting awareness and vigilance in culture. This will enable individuals to maximize the benefits of cybersecurity, diminish its drawbacks, and lead to a safer digital environment for all users. The landscape of technology in the future will only highlight the importance of effective cybersecurity, making it a strong consideration for any individual and organization.





