
- Introduction
- The Development of Cyber Warfare
- Types of Cyber Attacks
- Notable Instances of Cyber Warfare
- Consequences of Cyber Warfare
- Countermeasures against cyber-warfare
- Prospects of Cyber Warfare: Comprehensive Analyses
- Conclusion
Cyberwarfare represents a new and evolving frontier in global conflict, where digital tools and tactics replace traditional military means. Nations and organizations are increasingly using cyberattacks to target critical infrastructure, disrupt economies, steal sensitive data, and manipulate public opinion. Unlike conventional warfare, cyberwarfare is often covert, making it difficult to attribute attacks to specific actors, which complicates response strategies. These digital battles can take various forms, including denial-of-service attacks, data breaches, Ransomware in Cybersecurity, and disinformation campaigns. As countries strengthen their cyber capabilities, the line between state-sponsored attacks and cybercrime becomes increasingly blurred. Protecting against cyberwarfare requires robust cybersecurity infrastructure, advanced threat intelligence, and international cooperation to establish norms and protocols.
Become an expert in cyber security. Enroll in this Cyber Security Online Training now to acquire the knowledge you need.
Introduction
The one extreme dimension of war under present connection-oriented conditions is cyber warfare, which is quite different from the warfare of the old. Such warfare is spread in the digital world and crosses the boundaries of critical infrastructure and governmental systems down to common civilians. It can destabilize societies while undermining national security without the need to fire a single bullet while attempting to disrupt economies. Cybersecurity Training Courses is the constantly changing face of 21st-century conflicts. The best examples include the life-changing Stuxnet worm, the SolarWinds intrusion, and the catastrophic NotPetya ransomware. Therefore, this paper will take an in-depth look at cyber warfare, along with an analysis of its various categories, an examination of concrete examples, and an examination of how nations and entities are gearing up to counter this modern enemy.
The Development of Cyber Warfare
Early Basics Cyber Warfare’s roots trace back to the Cold War period, as far as one may reflect. It was a time when intelligence agencies began experimenting with electronic espionage. The early forms of hacking were quite simplistic and utilized dial-up networks and relatively simple forms of malware. However, these practices were primitive and formed the base for the full-scale tactics today. Digital Transformation The emergence of the internet during the 1990s and early 2000s transformed communication while concurrently revealing new vulnerabilities. Various entities, including governments, corporations, and individuals, increasingly depended on interconnected systems, resulting in a considerably extensive attack surface. Concurrently, nation-states developed offensive cyber capabilities, perceiving these tools as economical means to weaken adversaries.Modern DangersCyber Warfare has come to become an absolute instrument for the countries of the 21st century. These have emerged with exceedingly high sophistication to be carried out by nation-states using advanced technologies like AI, ML, and QC. Such technologies allow precision attacks that can cripple whole sectors or government structures in a quicker time.
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training.
Types of Cyber Attacks
- Espionage: Espionage refers to stealing sensitive information or intellectual property from a rival nation or organization. Gurus Employ Tools: Phishing campaigns, spyware applications, and APIs. The Office of Personnel Management breach (2015) involved Chinese hackers allegedly stealing the personal data of over 20 million U.S. federal employees.
- Subversion: Sabotage is a form of cyber operations used to damage or disrupt a system. The Stuxnet worm (2010), collaborated by the U.S. and Israel, closed in on Iran’s nuclear centrifuges, causing it to experience significant delays in its nuclear development program.
- Denial-of-Service (DoS) Attacks: These attacks overwhelm servers or networks with excessive traffic, rendering them inoperative. In 2007, Estonia faced large-scale Distributed Denial-of- Cloud Security Service on the country, weakening the government, banks, and media websites. The attack was purportedly perpetrated by pro-Russian hacktivists as a protest over political tensions.
- Propaganda and Psychological Operations: These include spreading false information, fake news, or creating fear to destabilize societies and influence political outcomes. Russia’s interference in the elections of 2016 U.S. elections by using fake social media accounts to alienate voters further and call for propaganda.
- Economic Shock: Financial-related systems can be targeted to unleash economic chaos. The Bangladesh Bank Heist (2016) occurred when hackers attempted to steal $1 billion using the SWIFT banking system. Although the bank lost only $81 million, the incident was a huge vulnerability blow to the global banking system.
- Infrastructure Attacks: Critical infrastructure, including power grids, transportation systems, and healthcare networks, represents significant targets. The ransomware incident targeting the Colonial Pipeline in 2021 severely affected the fuel supply on the U.S. East Coast, underscoring the vulnerability of essential infrastructure to cyber threats.
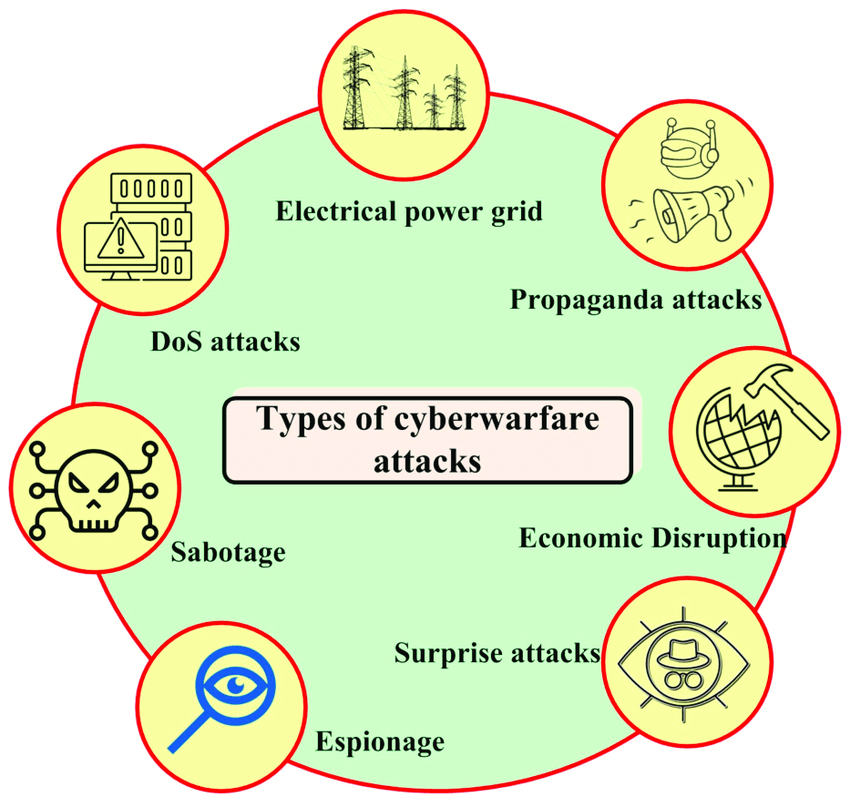
Notable Instances of Cyber Warfare
Stuxnet (2010) Iran’s nuclear enrichment plants. The malware exploited zero-day vulnerabilities in industrial control systems. Ramified Iran’s atomic program and heightened global awareness of cyberwarfare capability. NotPetya (2017) Initially Ukrainian organizations, but it spread globally. A ransomware attack is posing as legitimate software. The fallout has led to damages surpassing $10 billion, affecting major corporations like Maersk and FedEx. SolarWinds Hack (2020) U.S. government agencies and private companies. Hackers inserted malware into SolarWinds software updates, gaining access to Cybersecurity Training Courses. One of the most sophisticated supply-chain attacks, compromising data of critical organizations.Ukraine Power Grid Attacks (2015-2016) Ukraine’s Power Supply Grid. Hackers successfully compromised power substations, resulting in widespread power outages. Projected the vulnerabilities of energy infrastructures to cyber attacks.
Consequences of Cyber Warfare
Cyber warfare affects governmental structures, economic systems, and social frameworks very powerfully. Due to the secretive nature and scope of cyber warfare, these ramifications are extensive and complex. The primary domains affected by cyber warfare include National Security Threats Critical Infrastructure Vulnerability Cyberattacks on power grids, transportation, and water services can collapse necessary services, thereby destabilizing nations. The attack on the 2015 Ukraine power grid left hundreds of thousands without electricity. Defense System Risk: Breaches in military networks can compromise national security through exposed classified information or disruptions in operations. Economic Impact of Economic Detriment Cyber intrusions targeting financial organizations may lead to considerable fiscal deficits. Bangladesh Bank heist in 2016 it lost $81 million. Business Disruption Network Security Keys create downtime, reputational loss, and compliance expenses. NotPetya ransomware (2017) did $10 billion or more in damages worldwide. Social disturbance Misinformation Campaigns: propaganda and fake news can polarize societies, influence elections, and erode trust in democratic systems. Russia’s alleged interference in the 2016 U.S. presidential elections. Panic and Fear Attacks against critical services, such as healthcare or fuel supplies, instill widespread public fear. The attack on the Colonial Pipeline in 2021 resulted in fuel shortages throughout the Eastern United States. Erosion of Privacy and Civil Liberties Mass Surveillance To counter cyber threats, governments may adopt intrusive surveillance practices, raising privacy concerns. Data Breaches Incidents that disclose personal information compromise individual privacy and heighten identity theft risks. The Equifax data breach (2017) affected 147 million people.
Countermeasures against cyber-warfare
- International Cooperation: Agreements like the Budapest Convention on Cybercrime intend to offer cooperation but still need global consensus.
- Complex technologies: AI and Machine Learning: For detection and response in real-time. Emerging as a defense against quantum computing-based attacks, Quantum Cryptography.
- Official Policies: Many nations, including the U.S., have implemented national cybersecurity strategies to address threats comprehensively.
- Education and Training: Raising awareness and training professionals are the steps needed to create the right cybersecurity workforce.
Prospects of Cyber Warfare: Comprehensive Analyses
As cyberwarfare evolves, it creates new challenges and opportunities for attackers and defenders. Serious technological development and ethical dilemmas are poised to shape the next phase of cyber battles. The following are a few critical advancements that will shape the course of future cyber warfare.
AI-Powered Cyberattacks
- Mechanization and Precision: AI is going to add more precision, flexibility, and automated capability for cyberattacks. Cyber-criminals will use it to create self-learning malware, which adjusts its strategy upon adoption of countermeasures. This should help defeat the conventional security networks with increased efficiency. Finally, AI can be used for automating all tasks related to the detection of weaknesses within any network or even orchestrating multi-stage attacks via varied attack vectors. Instead, machine learning algorithms can scan a target’s network to identify weaknesses and launch targeted attacks with minimal human intervention, thereby amplifying the speed and efficiency of the process to unprecedented levels.
- AI-Powered Defense Mechanisms: In defense, AI will significantly enhance our ability to detect and respond to cyberattacks in real-time, providing a crucial advantage against evolving threats. Harnessing vast data streams empowers AI-driven cybersecurity systems to identify unusual behaviors and thwart potential attacks before they happen, ensuring a more secure digital environment. AI-based cybersecurity systems can change their safeguards to new threats faster than the traditional methods whereby response times shall be measured in milliseconds.
- Possible Hazards: However, cybercrooks can also misuse this technique to design more sophisticated attacks using social engineering, such as deepfakes or AI-based phishing, which might be considerably difficult for users to understand.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Quantum Computing
- Encryption Breakthroughs: Quantum computing is the use of principles of quantum mechanics to process information that would one day revolutionize cyberwar. Quantum computers can easily break through some standard encryption algorithms by solving difficult mathematical problems in a few seconds, which would take years using current computing power. Accordingly, many End-to-End Encryption used today, like RSA, will gradually become obsolete because sensitive information will then become vulnerable to attackers who have access to this specific quantum computing technology. A nation-state or well-funded hacker group with a quantum computer could decrypt vast amounts of encrypted intelligence, communications, or financial data, threatening national security and private sector confidentiality.
- Quantum-Resistant Cryptography: In response to these threats, researchers are developing “quantum-safe” encryption algorithms that are immune to quantum decryption techniques. However, the mass adoption of these new encryption algorithms will take time, and in the interim, the world will be vulnerable.
- The Dichotomous Nature: Although quantum computing holds transformative promise for encryption methodologies, it simultaneously poses significant threats to both cybersecurity and national security as adversaries gain the ability to breach existing safeguards.
Space Systems Vulnerability
- Targeting Satellites and Space Communication Networks: Even with the well-developed infrastructure in space, including satellites used for communication, navigation, and other meteorological observations, this is rapidly emerging as a target for cyber warfare. As countries increasingly use satellites for military and civil operations, such systems display large vulnerabilities. Cyberattacks on satellites can readily disrupt military factions’ communications, cripple financial systems reliant on GPS, or even cripple all-important weather forecasting systems, which are all crucial for disaster management. A cyber assault targeting a satellite’s control system has the potential to usurp its operations, leading to a failure in functionality, destruction, or repurposing as an offensive tool against other satellites.
- Weaponization of Space: As countries build up their military capabilities on land, at sea, and in the air, outer space is also becoming a battleground, incorporating cyber and physical elements. This development may lead states to create cyber weapons designed to disrupt or turn off satellite communications while military space forces are stepping up efforts to protect against these threats.
- Satellite Data Manipulation: Satellite cyber attacks might involve data manipulation techniques, such as altered GPS signals or weather data, to cause confusion or disrupt operational functionality. For example, faulty GPS information can cause an autonomous vehicle, a military drone, or a commercial airline to alter course and miss its intended destination.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Ethical Issues
- Responsibility in Cyber Warfare: As cyberweapons grow in sophistication and prevalence within contemporary military engagements, accountability issues will become progressively intricate. In contrast to conventional armaments, cyberattacks are frequently executed from a distance and without identification, provoking apprehensions regarding the attribution of responsibility when such assaults lead to detrimental outcomes.
- Morality of Cyber-Weapons: Cyber Weapons do not have the potential of any localized damage by way of destruction on land, air, or water; therefore, they are a little hard to place anywhere in the existing rules of warfare. Cyberstalking on civilian infrastructure, such as hospitals or power grids, raises moral ambiguity. Under traditional rules of warfare, international humanitarian law prohibits attacking civilian infrastructure but makes enforcing such distinctions very tough because cyberattacks are nameless and fly low on the radar. Such attacks against hospitals or other critical infrastructure can be devastating to non-combatant proportions. Their ethical implications raise profound concerns about the rules of engagement in cyberwarfare.
- Proportionality and Escalation: The principle that guides military activities in war is proportionality: that is, the damage inflicted must not be disproportionate or excessive to the military advantage anticipated. Defining proportionality in cyberwarfare presents notable challenges, as an initial cyberattack on vital systems may appear inconsequential yet could trigger catastrophic repercussions. Moreover, a targeted cyber attack on a country’s critical infrastructure could quickly escalate, possibly leading to a broad cyberwar and, in extreme cases, even a conventional military conflict.
Conclusion
Cyber warfare has fundamentally altered the nature of conflict, making it possible for attacks to occur without physical borders or traditional battlefields. In Cybersecurity Training , adversaries can target critical infrastructure, steal sensitive data, and disrupt essential services with devastating consequences. This highlights the urgent need for international collaboration to develop advanced technologies that can defend against such attacks. Nations must work together to create comprehensive frameworks that promote cybersecurity while addressing emerging threats. As technology becomes more integrated into every aspect of life, proactive measures, such as robust encryption, threat intelligence sharing, and real-time monitoring, are crucial. Heightened vigilance is necessary to protect national sovereignty, as cyber threats can undermine a country’s economy, security, and political stability. By investing in cybersecurity research and fostering global cooperation, we can create a safer and more resilient digital landscape. A unified approach will ensure a secure future where nations can thrive without the constant fear of cyberattacks undermining their progress and stability.





