
- What is hacking?
- Phases of Hacking
- The Role of Ethical Hacking in Cybersecurity Strategy
- Why Ethical Hacking is Critical to Modern Cybersecurity
- Types of Hackers
- The Future of Ethical Hacking And Cybersecurity
- Conclusion
With a day in which threats are cropping up in cyberspace at unprecedentedly alarming rates, the ability to provide robust cybersecurity has perhaps never felt so urgently needed. Even traditional methods of securing systems and data aggressively applied today are being challenged by increasingly sophisticated malware, ransomware, phishing, and APTs. The cybersecurity professional is also to continuously innovate and design ways of defending sensitive data and infrastructure. Ethical hacking and Ethical Hacking Course is one of the best means used to fight cybersecurity threats. As a result, ethical hacking refers to white-hat hacking or penetration testing the legitimate and systematic probing of systems for vulnerabilities before malicious hackers can exploit the same vulnerabilities.
Are you curious to know more about Ethical Hacking? Take advantage of our comprehensive online Ethical Hacking Training!
What is hacking?
Ethical hacking is the procedure of testing and evaluating the safety of computer systems, networks, or applications. It includes the simulating of the malicious hackers’ actions but is done with the consent and agreement of the hiring organization. In general, ethical hacking is aimed at discovering vulnerabilities that can be exploited by malicious attackers to be fixed and strengthen an organization’s overall security posture.
Ethical hackers operate in essentially the same way as black-hat hackers, but they do so at the request of the target organization. Sometimes, they test:
- Scanning for vulnerabilities
- Exploiting weaknesses in security
- Jumping over security controls
- Social engineering attacks
- Testing vulnerabilities in networks
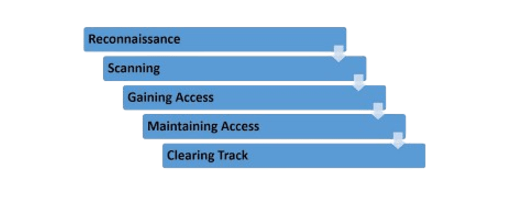
- Reconnaissance:It is at this stage that the hacker finds very useful information, such as old passwords and names of important employees (such as the head of the network department), and conducts active surveys to learn how the organization runs. As a next step, the hacker performs a process termed footprinting to gather information regarding the security posture, narrows down the area of concentration by coming up with specific IP addresses.
- Scanning: In this stage, the hacker identifies an easy way of penetrating the system and begins searching for information. There are three scanning techniques: pre-attack, port scanning/sniffing, and information-gathering hacking. Each of the above stages portrays a different degree of vulnerability that they can use to penetrate the weakness in the system. This is the pre-attack phase, in which the hacker monitors the Network Topology for specific information gleaned during reconnaissance.
- Gaining Access:This is the phase where an attacker accesses the system/network using various tools or methods. Once he has entered a system, he has to boost his privileges to the administrator level so he can install an application he needs, modify data, or hide data.
- Maintaining Access: A hacker may hack the system to prove that it is vulnerable, or he may be so malicious that he wants to maintain or perpetuate the connection in the background without his knowledge. This can be achieved through Trojans, rootkits, or other malicious files. He wants to keep access to the target until he has completed the objectives that he set out to do.
- Clearing Track: No thief wants to get caught. A smart hacker always cleans away all traces so that no one can trace him afterwards. For this purpose, he focuses on modification/destruction/erasing the values of logs, changing registry values, de-installing all the applications he has used, and deleting all folders created. Even in the case of a compromised site, it should be addressed and remedied as soon as possible to thwart damage that will most likely be caused by future unauthorized access.
- Preemptive Identification of Vulnerabilities
In modern cybersecurity, one of the most major impacts that ethics hacking has brought into place is it’s potential towards proactive identification of vulnerabilities before criminals and malicious actors have an opportunity to exploit them. Ethics hackers use several tools and techniques, such as network scanning, code analysis, and penetration testing, which make it possible for them to dissect security flaws. Based on such weaknesses identified early in the process, firms can, after that, plug the vulnerabilities, implement countervailing measures, and enhance their defences.
- Simulating Real-World Cyberattacks
These hackers can also replay actual cyberattacks. Ethical hackers, most of the time, emulate what the attackers in cyberspace use so that the organizations know how such an attack might play out and what effect it will have on their systems. This will thus give the organizations simulations to date as far as the effectiveness of their existing measures in defence is concerned, and hence, they will make better positions. Penetration tests might try an ethical hacker to hack into an internal network of a company through unauthorized means using phishing and social engineering tactics or through software-related vulnerabilities.
- Reducing the Attack Surface
Ethical Hacking Course threats typically exploit an area in the attack surface of a system, such as areas where the system can be accessed or attacked by unauthorized users. Examples of attack surfaces include open ports, old software, misconfigured settings, and weak passwords. Ethical hackers meet these duties in trying to ensure that there is a decline in the attack surface via vulnerability discovery and address. Ethical hacking and cyber security can assist firms in identifying hidden or overlooked vulnerabilities that could occur due to being outdated-patched or unsecured endpoints through vulnerability assessments.
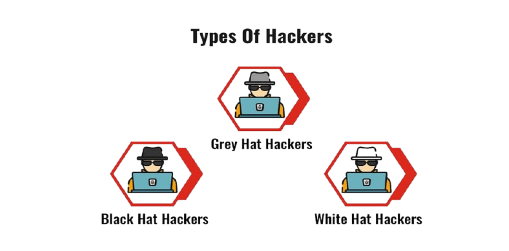
- Black Hat Hackers: They are often called Crackers. Black Hat Hackers can gain unauthorized access to your system and destroy your vital data. The method of Malware Attack they use is common hacking practices they have learned earlier. They are considered to be criminals and can be easily identified because of their malicious actions.
- White Hat Hacker: White hat hackers are approved or certified hackers who work for governments and corporations to undertake penetration testing and detect security flaws. They also provide security against malicious cyber crimes. They follow the laws and restrictions established by the government, which is why they are known as ethical hackers or cybersecurity specialists.
- Grey Hat Hacker: Gray hat hackers are somewhere in between white hat and black hat hackers. They are not officially authorized hackers. They operate with both good and bad motives, and they may utilize their expertise for personal benefit. It all depends on the hacker. If a grey hat hacker uses their skills for personal benefit, they are classified as a black hat hacker.
Why Ethical Hacking is Critical to Modern Cybersecurity
Fast-Changing Threat Environment Because threats are continuously evolving, ethical hackers have a critical role in updating defence approaches to exploit new vectors of attack. By doing so, organizations are better protected against advanced threats.Preventing Data Breaches and Financial Loss By identifying weaknesses before they are exploited, ethical hackers prevent costly data breaches, financial loss, reputational damage, and legal consequences.Building Trust Organizations prioritizing ethical hacking ensure their commitment to Web Application Security by earning the trust of customers, partners, and stakeholders regarding the security and privacy of the data given to them.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Program to Begin Your Adventure Now.
Types of Hackers
 Ethical Hacking Sample Resumes! Download & Edit, Get Noticed by Top Employers! Download
Ethical Hacking Sample Resumes! Download & Edit, Get Noticed by Top Employers! DownloadThe Future of ethical hacking and cyber security
While cybersecurity threats become both voluminous and increasingly complex, the role of the ethical hacker will become especially important in these light situations. Future directions for ethical hacking are integrally tied to technological changes that are progressively moving toward wider use of artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT). New opportunities the emerging technologies open up let the lands of ethical hackers go for exploration and for addressing vulnerabilities but, at the same time, open up new attacking surfaces and potential risks. Ethical hackers will undoubtedly have a much more complex role in years to come as part of any Web Security team working with automated systems and AI-driven tools to identify better and mitigate threats quickly and efficiently. Defence against new, ever-changing, sophisticated cybersecurity threats will, therefore, continue to include front-line ethical hackers.
Prepare For Your Ethical Hacking Interview Question & Answer With Our Comprehensive Ethical Hacking Interview Questions Bank. Get Started Now!
Conclusion
Ethical hacking has a great impact on modern Ethical Hacking Course, as it proactively identifies vulnerabilities that reduce the attack surface and enables organizations to understand and mitigate emerging threats. In this fast-growing cyber world, where threats become increasingly sophisticated and are arguably at their most innovative and complex levels, ethical hacking and cyber security become a critical line of defence. Testing, threat intelligence, and cooperating with the security team are some of the key factors that can bring every organization closer to an ideal cybersecurity posture to realize enhanced resilience against cybersecurity threats.
Ethical hackers essentially allow an organization to patch its flaws before the bad guys can use them, thereby reducing its attack surface and staying ahead of Cyber Media.
Phases of Hacking
To become a certified Ethical Hacker, have a look at our Ethical Hacking Training right now.





