
- In terms of cybersecurity, what is buffer overflow?
- What is overflow buffer?
- Buffer Overflow Attack Types
- What is the process of a buffer overflow attack?
- The Repercussions of Buffer Overflow
- Strategies for Mitigation
- Conclusion
A buffer overflow is a serious cybersecurity vulnerability that an attacker could use to run arbitrary code, change system settings, or obtain unauthorized access to private information. This happens when software uses more memory than it has been allotted, causing extra data security to overwrite nearby memory regions. In the context of a Sandbox Environment, this type of issue can be safely identified and mitigated. An attacker can interfere with the program’s regular execution and possibly introduce malicious code that the system will subsequently run by carefully constructing the input. Many high-profile computer security breaches have been caused by buffer overflows, which emphasizes the significance of safe coding techniques and strong input validation.
Are You Interested in Learning More About Overflow Buffer? Sign Up For Our Cyber Security Online Training Today!
In terms of cybersecurity, what is buffer overflow?
In essence, a buffer overflow is a software flaw, vulnerability, or opening. It happens when a program tries to overwrite data while increasing the amount of RAM that is allotted into a buffer or temporary storage region. Data overflow into other memory regions as a result corrupts or overwrites the contents of those places. Attackers often identify Overflow Buffer as significant vulnerabilities that they might use to introduce malicious code into the system and obtain unauthorized access.
An example of a Cyber Security Training Courses danger is a buffer overflow attack, which happens when an application security or software tries to store more data in a buffer (temporary storage) than it can contain. This extra data may overflow into nearby memory regions, perhaps erasing crucial data or resulting in a software crash. Attackers may be able to use this vulnerability in some circumstances to run malicious code and obtain unauthorized access to a system or application.
What is an overflow buffer?
Programming errors known as buffer overflows happen when a program writes more data to a buffer a block of memory than it was allotted. This may result in the program crashing, nearby memory locations being overwritten, perhaps damaging data, or information security flaws being introduced. In terms of Risk Threat and Vulnerability, such memory issues can create significant security risks.
Since there is no built-in bounds checking for arrays in languages like C and C++, buffer overflows usually occur in these languages. This vulnerability can be used by attackers to introduce malicious code or obtain unauthorized access to a system. Bounds checking, safe coding techniques, and the use of contemporary programming languages or tools with automatic memory management are all necessary to prevent buffer overflows.
Interested in Obtaining Your Overflow Buffer Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Buffer Overflow Attack Types
- Stack-based Overflow of Buffers: Stack-based buffer overflows are the most prevalent kind of buffer overflow. This type of vulnerability highlights the importance of Cyber Awareness, as individuals and organizations need to understand the potential risks of buffer overflow attacks.
- Heap-based Buffer overflow: Unlike stack-based overflow buffer, heap-based buffer overflows aim for the dynamically allocated memory on the heap. Similar to stack-based ones, attackers can change the program, overwrite nearby memory areas, and take control of it by using heap data structures like malloc or free.
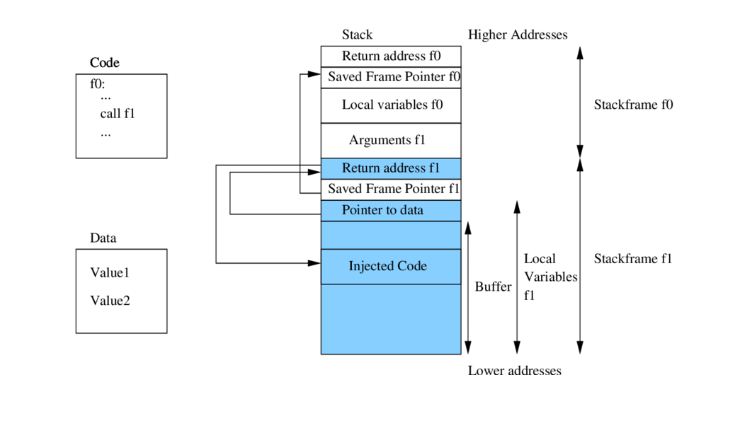
- One-off Error: When a program writes one byte over the allotted buffer, an off-by-one error happens. Even while it could appear to be a small mistake, an attacker can take advantage of it by changing crucial information and data.
- Vulnerability of Format String: Format string weaknesses can affect programs that use format string functions (printf, sprint, etc.) without doing enough validation. If an attacker manages to take control of the format string parameter and alter the program’s memory, they could be able to misuse it or replace crucial data.
- Overflow of Integers: Integer overflows can cause comparable problems, however they are not quite the same as buffer overflows. It happens when values generated by arithmetic operations are too large to fit into the allotted memory space.
What is the process of a buffer overflow attack?
- Excessive Data Writing: An attacker purposefully inserts more data into the buffer than it can contain in order to take advantage of this vulnerability. This extra data floods neighboring memory regions, perhaps overwriting important data.
- Overwriting Memory: Critical data structures including function pointers, return addresses, and control flow variables may be overwritten by the overflowing data. The attacker can take advantage of known vulnerabilities or divert the program’s execution to malicious code by changing these variables.
- Execution of Malicious Code: The attacker wants to run their own code or insert shellcode into the compromised software after they have successfully overwritten important memory regions. This code has the ability to carry out a number of harmful tasks, including gaining access without authorization, increasing privileges, and initiating other attacks.
- Possible Repercussions: A Overflow Buffer attack can have detrimental effects in Cyber Security Training Courses. Crashing, unstable systems, illegal access, data breaches, and even remote code execution are all possible outcomes.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
The Repercussions of Buffer Overflow
- Random Code Execution: On a susceptible system, a buffer overflow attack that is successful could allow the execution of arbitrary code. In such cases, Payloads are often used by attackers to deliver malicious code once the vulnerability is exploited.
- Execution of Code Remotely: By using a network connection, buffer overflow vulnerabilities can be remotely exploited to allow attackers to execute code on a target system. This might lead to a total compromise of the system, giving hackers the ability to perform a range of destructive operations or redirect their attention to other machines linked to the network.
- Denial-of-Service: Buffer overflow vulnerabilities can cause denial-of-service scenarios, which can cause a targeted system or application to crash, become unresponsive, or use excessive amounts of resources.
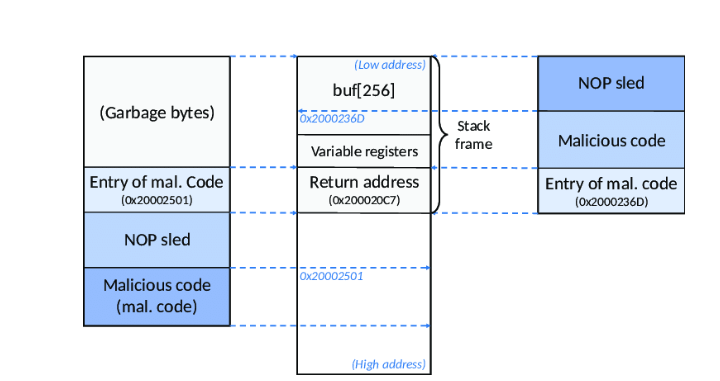
- Disclosure of Information: Buffer overflow vulnerabilities may cause private data kept in memory to be revealed. Adjacent memory areas holding sensitive information, such as encryption keys, passwords, or private files, can be overwritten by an attacker.
- Injection of Code: Attackers may be able to insert and run their own malicious code within a compromised system by taking advantage of buffer overflows. This can be used to carry out additional attacks within the targeted environment, alter or steal data, or influence the behavior of apps.
- Getting Around Security Measures: Vulnerabilities related to buffer overflows might compromise different security measures or mitigations put in place inside a system. Attackers can get around memory safety measures like Data Execution Prevention (DEP) and address space layout randomization by taking advantage of a buffer overflow.
- Discredit and Monetary Losses: Successful buffer overflow attacks have the potential to seriously harm an organization’s reputation. In addition to financial losses and regulatory fines, data breaches, system hacks, and service interruptions can also lead to a loss of customer faith and trust as well as legal and regulatory responsibilities.
Strategies for Mitigation
- Safe Coding Procedures: It is essential to adhere to secure coding techniques to stop buffer overflow vulnerabilities. Safe string manipulation routines and libraries should be used, user input should be thoroughly validated and sanitized, and all input and memory operations should adhere to stringent bounds checking.
- Validation and Sanitization of Input: To guarantee that user-supplied data is within expected bounds and does not contain dangerous code or characters, provide robust input validation and sanitization procedures. Verify the validity and duration of the input, and sanitize it to eliminate or escape any potentially harmful characters or sequences.
- Employ Programming Languages: The purpose of secure programming languages is to lower the possibility of buffer overflow vulnerabilities. They achieve this by adding built-in memory safety features. In addition to secure coding practices, Whitelisting can further enhance cyber security tools by ensuring that only trusted applications and processes are allowed to execute on a system.
- Limitations on Buffer Size: To protect against vulnerabilities brought on by buffer overflows, impose rigorous buffer size constraints. Determine the appropriate amount of buffers depending on the expected input and consumption.
- A stack of canaries: Stack canaries are a type of security measure used to detect buffer overflow vulnerabilities. It usually sits in between the local variables and the function’s return address. Stack canaries, or random values put between buffers and control data, are used to identify buffer overflows.
- Prevention of Data Execution (DEP): Turn on Data Execution Prevention (DEP) or similar protections to mark memory regions as non-executable. DEP reduces the likelihood of successful attacks by blocking code introduced via buffer overflow vulnerabilities from being executed.
- Analysis, Both Static and Dynamic: Use dynamic analysis methods like fuzzing and static code analysis tools to identify buffer overflow problems throughout the development and testing stages. Vulnerable coding patterns and inadequate input validation can be identified by automated tools.
Want to Learn About Cyber Security? Explore Our Cyber Security Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Companies that take a proactive approach to secure development, enforce stringent input validation, and implement appropriate security measures can significantly reduce the risk of Overflow Buffer vulnerabilities and enhance the overall cyber laws in their systems. In the field of Cyber Security Training Courses, buffer overflow vulnerabilities are a serious and widespread danger. They may result in severe repercussions such as information leakage, denial-of-service, privilege escalation, arbitrary code execution, remote code execution, code injection, evading security measures, and harm to an organization’s reputation and finances.





