
What is Steganography?
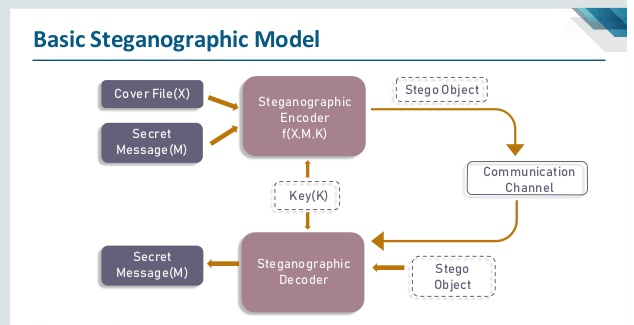
Steganography can be defined as the science of hiding the data like file, image, video, or any message to the other file, image, video, or message. In Steganography the useless bits are actually replaced by the useful bits in order to hide the required file into any of the files or data mentioned above. It plays a vital role in cybersecurity by allowing the legitimate users or peers to send the data in a way which is highly secured so that it could be protected from the hacker or malicious users who are intended to harm or abuse the system. It can be done using software that is available in the market for free or paid.
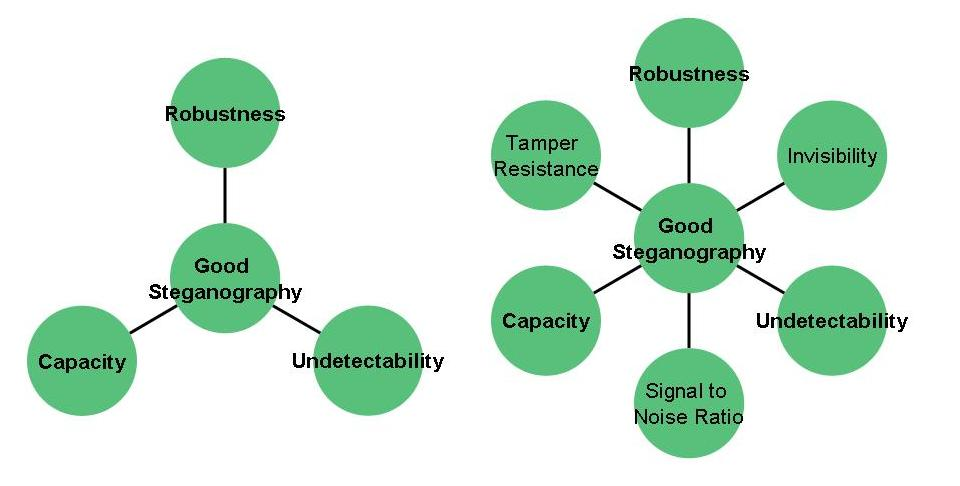
Steganography can also be considered as the practice of concealing the crucial data into any of the files so that it could be transmitted securely. The applications like SteganPEG, OpenStego and so on are used to fulfill the purpose of wrapping up one file into another. The applications used for Steganography hides the bits of the required file into another file in a manner so that the original file doesn’t lose its characteristics. It can be considered pretty more secure than encryption or hashing as in these cases the attacker can sniff at least the junks but in the case of Steganography, they won’t be able to detect if anything important has been transmitted. It is usually applied at a place where the data has to be sent secretly.

- Steganography is the technique of hiding secret data within an ordinary, non-secret, file or message in order to avoid detection; the secret data is then extracted at its destination. The use of steganography can be combined with encryption as an extra step for hiding or protecting data.

Steganography Techniques
- Depending on the nature of the cover object(actual object in which secret data is embedded), steganography can be divided into five types:
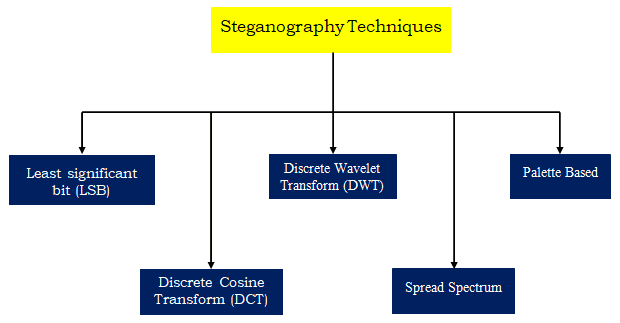
- Text Steganography
- Image Steganography
- Video Steganography
- Audio Steganography
- Network Steganography
1.Text Steganography
Text Steganography is hiding information inside the text files. It involves things like changing the format of existing text, changing words within a text, generating random character sequences or using context-free grammars to generate readable texts. Various techniques used to hide the data in the text are:
- Format Based Method
- Random and Statistical Generation
- Linguistic Method
2.Image Steganography
Hiding the data by taking the cover object as the image is known as image steganography. In digital steganography, images are widely used cover source because there are a huge number of bits present in the digital representation of an image. There are a lot of ways to hide information inside an image. Common approaches include:
- Least Significant Bit Insertion
- Masking and Filtering
- Redundant Pattern Encoding
- Encrypt and Scatter
- Coding and Cosine Transformation
3.Audio Steganography
In audio steganography, the secret message is embedded into an audio signal which alters the binary sequence of the corresponding audio file. Hiding secret messages in digital sound is a much more difficult process when compared to others, such as Image Steganography. Different methods of audio steganography include:
- Least Significant Bit Encoding
- Parity Encoding
- Phase Coding
- Spread Spectrum
- This method hides the data in WAV, AU, and even MP3 sound files.
4.Video Steganography
In Video Steganography you can hide kind of data into digital video format. The advantage of this type is a large amount of data can be hidden inside and the fact that it is a moving stream of images and sounds. You can think of this as the combination of Image Steganography and Audio Steganography. Two main classes of Video Steganography include:
- Embedding data in uncompressed raw video and compressing it later
- Embedding data directly into the compressed data stream
5.Network Steganography (Protocol Steganography)
- It is the technique of embedding information within network control protocols used in data transmission such TCP, UDP, ICMP etc. You can use steganography in some covert channels that you can find in the OSI model. For Example, you can hide information in the header of a TCP/IP packet in some fields that are either optional.
Installation
$ poetry install Stegano
- You will be able to use Stegano in your Python programs.
- If you only want to install Stegano as a command-line tool:
$ pip install Stegano
- pip installs scripts (system-wide available) provided by Python packages into separate virtualenvs to shield them from your system and each other.
Use Stegano as a library in your Python program
- If you want to use Stegano in your Python program you just have to import the appropriate steganography technique. For example:
- >>> from Stefano import lsb
- >>> secret = lsb.hide(“./tests/sample-files/Lenna.png”, “Hello World”)
- >>> secret.save(“./Lenna-secret.png”)
- >>> clear_message = lsb.reveal(“./Lenna-secret.png”)
Use Stegano as a command-line tool
- Hide and reveal a message
- $ Stefano-LSB hide -i ./tests/sample-files/Lenna.png -m “Secret Message” -o Lena1.png
- $ Stefano-lsb reveal -I Lena1.png
Secret Message
Hide the message with the Sieve of Eratosthenes
- $ Stefano-lsb-set hide -i ./tests/sample-files/Lenna.png -m ‘Secret Message’ –generator Eratosthenes -o Lena2.png
- The message will be scattered in the picture, following a set described by the Sieve of Eratosthenes. Other sets are available. You can also use your own generators.
- This will make a steganalysis more complicated.
Running the tests
- $ python -m unittest discover -v
- Running the static type checker:
- $ python tools/run_mypy.py
Contributions
- Contributions are welcome. If you want to contribute to Stegano I highly recommend you install it in a Python virtual environment with poetry.
Differences between steganography and cryptography
- Steganography is often compared to cryptography. While steganography hides information, cryptography focuses on rendering the data unreadable to everyone except its intended recipient. Once a stream of data is encrypted, only a person who has access to its decryption key will be able to unlock it.
- But if cryptography provides better protection for secret data, why use steganography at all?
- The presence of cryptography reveals that something is hidden, and in many cases, this is enough to get the sender in trouble.
- “In a highly monitored country, like say China or Iran or North Korea, cryptographic files can be detected and the very fact you are sending/receiving them could raise suspicion,” says security researcher John Ortiz.
- “When they show up and put a gun to your head for the key, even the most secure crypto is worthless.”
- Sometimes, steganography and cryptography are used together.
- “Steganography and encryption are not actually mutually exclusive,” says Jerome Segura, director of threat intelligence at Malwarebytes. “The former is mainly a way to conceal data within an image file, but that data doesn’t have to be in the clear text either.”
- Segura and researchers at Malwarebytes have been recently investigating a case where attackers were using image-based steganography to hide encrypted data. Even if someone discovers the hidden data, they will still need to decrypt it to reveal its contents.
Detect steganography
- The practice of detecting steganography is called ‘steganalysis’. There are several tools that can detect the presence of hidden data such as StegExpose and StegAlyze. Some analysts use other general analysis tools such as hex viewers to detect anomalies in files.
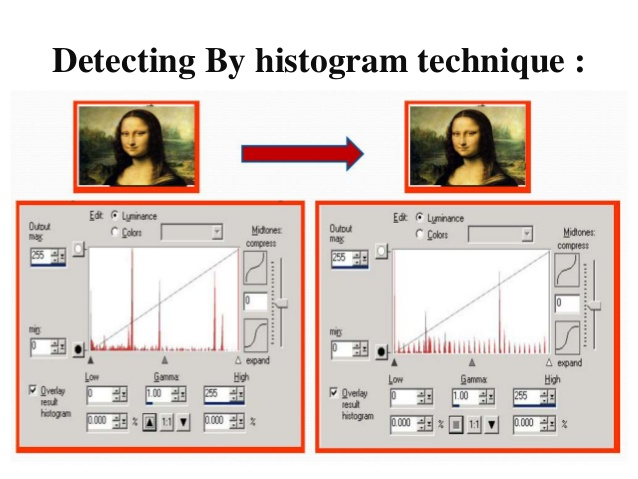
- Finding files that have been modified through steganography continues to remain a challenge, however. For instance, knowing where to start looking for hidden data in the millions of images being uploaded on social media every day is virtually impossible.
- “The data looks like/sounds like noise, so it is difficult to distinguish from the existing noise. Or it is in very little data,” Ortiz says. “And there are so many different hiding techniques that you need multiple detection techniques to detect them – there is no one-size-fits-all”
- Guardicore’s Harpaz warns: “Threat actors have a decent arsenal of steganography techniques they use as part of their modus operandi – it is not a new trend. As our research shows, it remains in the wild to this day and is not likely to disappear.”
Steganography Implemented
- There are several different techniques for concealing data inside of normal files. One of the most widely used and perhaps simplest to understand is the least significant bit technique, known commonly as LSB.
- This technique changes the last few bits in a byte to encode a message, which is especially useful in something like an image, where the red, green, and blue values of each pixel are represented by eight bits (one byte) ranging from 0 to 255 in decimal or 00000000 to 11111111 in binary.
- Changing the last two bits in a completely red pixel from 11111111 to 11111101 only changes the red value from 255 to 253, which to the naked eye creates a nearly imperceptible change in color but still allows us to encode data inside of the picture.

- The least significant bit technique works well for media files, where slightly changing byte values create only slight imperceptible changes, but not so well for things like ASCII text, where a single bit out of place will completely change the character. That’s not to mention the fact that data hidden using LSB steganography is also easy to detect if someone is looking for it.
- For this reason, there are a plethora of other steganography techniques out there, each with their own benefits and drawbacks. Another far less detectable one is called the discrete cosine transform coefficient technique (I know, it’s a mouthful), which slightly changes the weights (coefficients) of the cosine waves that are used to reconstruct a JPEG image.
Embed Hidden Data into a File
- Using Steghide is very easy. To install it from the terminal in Linux, just use apt.
- apt-get install steghide
- Once it’s installed, in order to embed data in a file, type the command below.
- steghide embed -ef secret file -cf cover file -SF outputFile -z compression level -e scheme
The arguments are broken down as follows:
- -ef specifies the path of the file that you want to hide. You can embed any kind of file inside of the cover file, including Python scripts or shell files.
- -cf is the file that the data is embedded into. This is restricted to BMP, JPEG, WAV, and AU files.
- -sf is an optional argument that specifies the output file. If this is omitted, the original cover file will be overwritten by your new steganographic file.
- -z specifies the compression level, between 1 and 9. If you prefer not to compress your file, use the argument -Z instead.
- -e specifies the type of encryption. Steghide supports a multitude of encryption schemes, and if this argument is omitted by default, Steghide will use 128-bit AES encryption. If you prefer not to use encryption, simply type -e none
- example, I’m hiding secret text inside an image of a cat. I’m not overwriting the original image or compressing it, nor do I care about encryption right now.
steghide embed -ef secret.txt -cf StegoCat.jpg -e none -Z
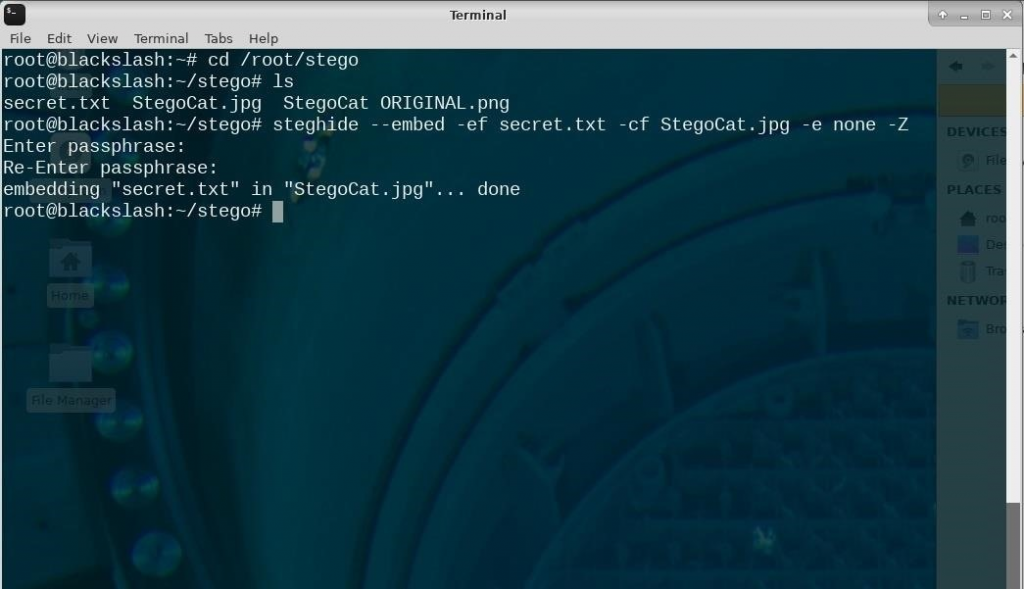
- Once you have executed the Steghide command, you will be prompted to set a password that will allow you to extract the embedded data later. So enter your passphrase and re-enter it to confirm. Once you get used to this process, it’ll only take seconds to hide your data inside an image or audio file with Steghide.

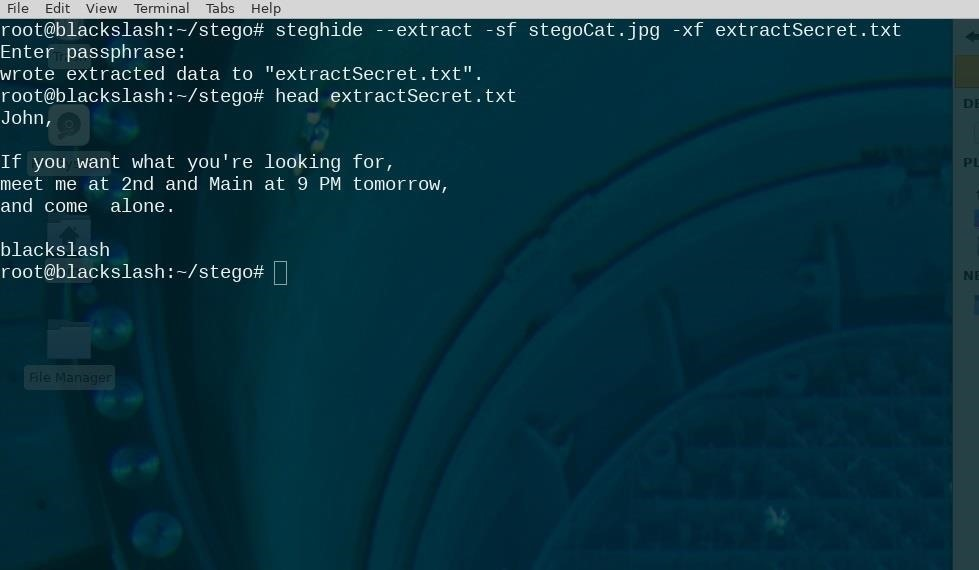
Extract Hidden Data from the File
- Extracting hidden data from a steganographic image is even easier. The command uses the syntax below.
$ steghide extract -sf stegoFile -xf outputFile
- Once you run this command, you’ll be prompted to enter the same password you created above in order to create the extracted file. It’s that simple!
Hiding Data in Images Is Just Too Easy
Advantage of steganography

- The advantage of steganography is that you can hide data in plain sight, but you can really blow it if you don’t follow some common-sense rules. First, the small differences steganography introduces are hard to detect — unless you have the original.
- Using an image you found off the internet without modifying it significantly makes it easy to detect that an image has hidden information. To check this, try a reverse Google Image search to make sure the original isn’t floating around somewhere.
Conclusion
- Steganography is in the nascent stage of development.
- The importance of Steganography has not been realized to that stage where it is preferred over its close rival “Encryption”.
- New techniques are being discovered and implemented. It is analyzed that time is not far away when its importance would be realized by organizations in general and the arm forces in particular.





