
- Introduction
- Important Cryptography Terms
- Cryptographic Algorithms Types
- What are the elements of cryptographic keys?
- What Are the Applications of Cryptography?
- Conclusion
- Full Disk Encryption (FDE)
- Document Level Encryption
- Data set Encryption
- Application Layer Encryption
Introduction :-
Cryptography is presently an exceptionally far and wide prerequisite of different corporate association. It secures us with the classification (or protection) of information just and executing it at the right layer will assist with guaranteeing we have the whole CIA ternion met.Prior to diving profound into the kinds of Cryptography, how about we comprehend cryptography in a fundamental manner.
A demonstrated strategy through which the information is safely traded between two gatherings utilizing a key that is known to the source and recipient alone (scrambled by the shipper and decoded by the beneficiary). This was additionally evolved as days passed to expand the odds of somebody breaking utilizing a savage power assault. Presently the most regularly utilized kind of keys are Symmetric and lopsided.
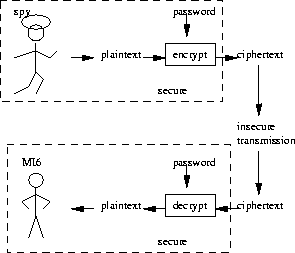
Symmetric key encryption has a solitary key for both encryption and unscrambling of the information. This is quicker anyway has a disadvantage from a security outlook as the Keys are to be kept mystery during transmission to a collector by a few confided in modes or instruments. It doesn’t govern off the odds of block attempt to unscramble the message.
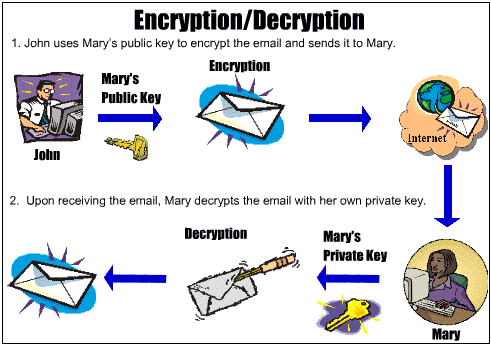
With all the above drawback, deviated key encryption (otherwise called public-key calculations) came into the image and uses two keys (cited as open and private key) for encryption and unscrambling. Here, the shipper will scramble the message with the public key and the recipient can utilize their private key to decode something similar. Assuming anybody is attempting to block the information, the encoded message will simply see confused information. Here the weight of communicating the way in to the shipper in a protected way is diminished as the public key can be imparted to anybody and private key is gotten by the beneficiary
Cryptography execution should be possible at different layers and the sending intricacy changes in like manner.
Full Disk Encryption (FDE) :
You can for the most part see this sort of set up on your PC on the off chance that you are utilizing Windows 10. You would have asked why a blue screen is requesting a secret word before you enter your organization LAN accreditations (AD Credential).
This is only Bit storage, a FDE ability gave by Microsoft packaged OS. This guarantees the whole circle is scrambled and thusly guaranteeing the information put away in your PC hard drive are secure in most pessimistic scenarios, for example, PC getting lost or burglary.
This is the most straightforward and practical structure to get your information encoded yet has its own portion of cons related with it. FDE doesn’t offer any choices of empowering a granular degree of encryption and is extremely reliant upon the SED (Self Encrypting Drive) sort of drives.
Document Level Encryption :
As the name recommends, File Level Encryption is accumulating at a record level and can go extremely granular to give the concerned person to get a solitary document in a more powerful way.
A typical model that you can relate is the Shared Drive or Share Folder where you are saving your documents in an office. While many think that the information saved by the individual must be gotten to by him/her, this isn’t the reality. Information can be perused/duplicated by any individual who approaches and at times the administrators who have full access can even overwrite the information.
This specific issue can be defeated utilizing record level encryption which can assist with ensuring both organized and unstructured kind of information by utilizing particular specialists that will be introduced by the OS that you are utilizing. The drawback of this kind additionally emerges from similar specialists as they have limited to a specific kind of OS and not all custom OS that is sent.
Information base Encryption :
In my perspectives, this is the main kind of encryption as this arrangements with DB that conveys every one of your information.
For your better creative mind, kindly take your telephone reinforcement put away in some information base which is gotten utilizing an alternate sort of encryption instrument that is more appropriate for Database
A typical one that is presently broadly suggested is TDE (Transparent Data Encryption) that offers encryption at the record level and meets different administrative necessity like PCI DSS
While there are a great deal of up-sides of utilizing this encryption type, this has certain functional and specialized limit
Functional Constraint – Since Database vacation is profoundly significant, DB administrators guarantee that they would rather not have too many extravagant things on the DB that might potentially affect the presentation and crash the framework.
Specialized Constraint – TDE doesn’t encode information on the way or use and scrambles segments or tables of a data set, leaving setup records, logs, and so forth decoded.
Application Layer Encryption:
This is by a long shot the most grounded technique for encryption and the most tedious one to empower. Application-level encryption offers an undeniable degree of safety with the encryption and unscrambling occurring at the application layer which implies that the information can be encoded prior to communicating or getting put away.
While variations of utilization layer encryption can decrease the effect on the Database, the disadvantage to this sort is inclining further toward the functional front as you want more devoted improvement exertion and assets to have the application level encryption empowered.
- Algorithm – Set of numerical principles utilized in encryption and decoding.
- Cryptography – Science of mystery composing that empowers you to store and communicate information in a structure that is accessible just to the expected people.
- Cryptosystem – Hardware or programming execution of cryptography that changes a message to ciphertext and back to plaintext.
- Cryptanalysis – Practice of getting plaintext from ciphertext without a key or breaking the encryption.
- Ciphertext – Data in encoded or incoherent organization.
- Encipher – Act of changing information into a unintelligible arrangement.
- Decipher – Act of changing information into a clear arrangement.
- Key – Secret arrangement of pieces and guidelines that oversees the demonstration of encryption and decoding.
- Key clustering – Instance when two diverse keys produce the equivalent ciphertext from the equivalent plaintext.
- Keyspace – Possible qualities used to build keys Plaintext Data in coherent configuration, additionally alluded to as cleartext.
Important Cryptography Terms :-
- Symmetric and Asymmetric key Cryptography
- Private and Public Key Exchange
- RSA Key Exchange
Cryptographic Algorithms Types :-
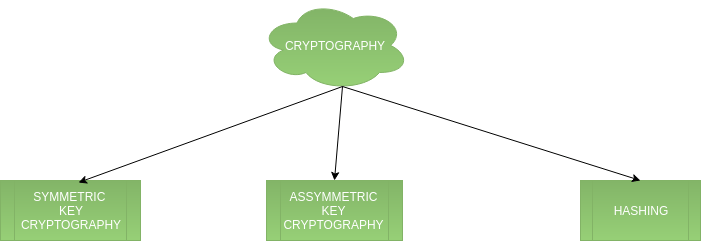
Symmetric and Asymmetric key Cryptography :
The two essential kinds of encryption are symmetric and lopsided key encryption.
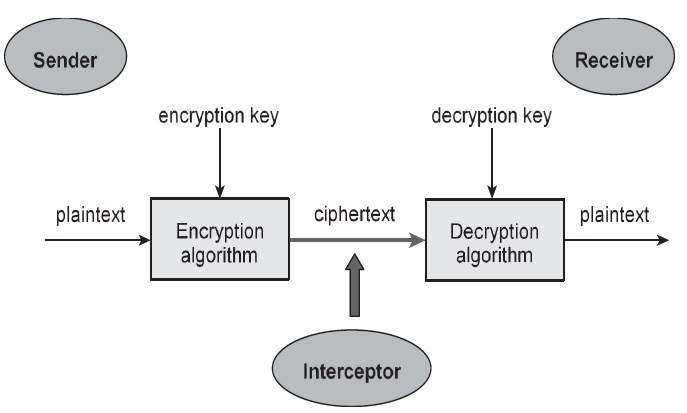
Symmetric Key Encryption – It implies both source and collector utilize a similar mystery key to scramble and decode the information. A mystery key, which can be a number, a word, or simply a line of irregular letters, is applied to the message of a message to change the substance with a certain goal in mind. This may be pretty much as straightforward as moving each letter by various spots in the letter set.
However long both shipper and beneficiary know the mystery key, they can scramble and unscramble all messages that utilization this key. The downside to symmetric key encryption is there is no safe method for dividing the key among various frameworks. Frameworks that utilization symmetric key encryption need to utilize a disconnected strategy to move the keys starting with one framework then onto the next. This isn’t pragmatic in a huge climate, for example, the Internet, where the customers and servers are not situated in a similar actual spot. The strength of symmetric key encryption is quick, mass encryption. Shortcomings of symmetric key encryption are key conveyance, adaptability, restricted security (secrecy just) and The way that it doesn’t give non-renouncement, which means the source’s personality can be demonstrated.
Instances of symmetric calculations are DES (information encryption standard), 3DES, AES (Advanced Encryption Standard), IDEA (International Data Encryption Algorithm), Twofish, RC4 (Rivest Cipher 4)
Asymmetric (or public) key cryptography – It was made to address the shortcomings of symmetric key administration and appropriation.Any individual who realizes the mystery key can decode the message, so it is essential to maintain the mystery key secure. Uneven encryption utilizes two related keys known as a key pair. A public key is made accessible to any individual who should send you an encoded message. A second, private key is kept mystery, so just you know it. Any messages (message, twofold records, or reports) that are encoded by utilizing the public key must be unscrambled by utilizing the matching private key.
Any message that is encoded by utilizing the private key must be unscrambled by utilizing the matching public key. This implies that you don’t need to stress over ignoring public keys the Internet as they are naturally accessible to anybody. An issue with hilter kilter encryption, in any case, is that it is more slow than symmetric encryption. It needs undeniably seriously handling capacity to both scramble and unscramble the substance of the message.
The connection between the two keys in awry key encryption depends on complex numerical recipes. One strategy for making the key pair is to utilize factorization of indivisible numbers. Another is to utilize discrete logarithms. Lopsided encryption frameworks depend on single direction works that go about as a secret entrance. Basically the encryption is single direction in that a similar key can’t unscramble messages it encoded. The related private key gives data to make decoding practical. The data about the capacity is remembered for the public key, while data about the hidden entryway is in the private key.
Any individual who has the private key knows the secret entrance work and can register the public key. To utilize hilter kilter encryption, there should be a strategy for moving public keys. The regular procedure is to utilize X.509 computerized authentications (additionally referred to just as testaments). An endorsement is a document of data that distinguishes a client or a server, and contains the association name, the association that gave the testament, and the client’s email address, nation, and public key.
Private and Public Key Exchange :
Key trade likewise called as key foundation, is strategy to trade cryptographic keys between clients, utilizing a cryptographic calculation. Assuming that the code is a symmetric key code, both will require a duplicate of a similar key. On the off chance that a topsy-turvy key code with general society/private key property, both will require the other’s public key.
Preceding any gotten correspondence, clients should set up the subtleties of the cryptography. In certain cases this might require trading indistinguishable keys (on account of a symmetric key framework). In others it might require having the other party’s public key. While public keys can be transparently traded (their relating private key is kept mystery), symmetric keys should be traded over a solid correspondence channel.
Previously, trade of such a key was amazingly irksome, and was enormously facilitated by admittance to get channels like a political pack. Clear text trade of symmetric keys would empower any interceptor to promptly get familiar with the key, and any scrambled information.
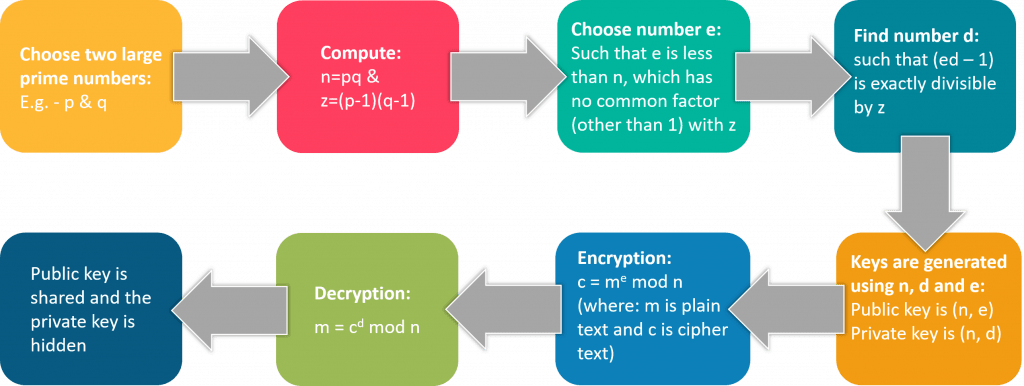
RSA Key Exchange :
The Rivest-Shamir-Adleman (RSA) calculations accessible from RSA Data Security, Inc., are the most generally utilized public key cryptography calculations. For RSA key trade, secret keys are traded safely online by encoding the mystery key with the planned beneficiary’s public key. Just the planned beneficiary can decode the mystery key since it requires the utilization of the beneficiary’s private key. Thusly, an outsider who catches the encoded, shared mystery key can’t unscramble and utilize it. The underneath figure outlines the fundamental RSA key trade process.
The RSA key trade process is utilized by a few security innovations to ensure encryption keys. For instance, EFS utilizes the RSA key trade cycle to secure the mass encryption keys that are utilized to encode and unscramble records.
What are the elements of cryptographic keys?
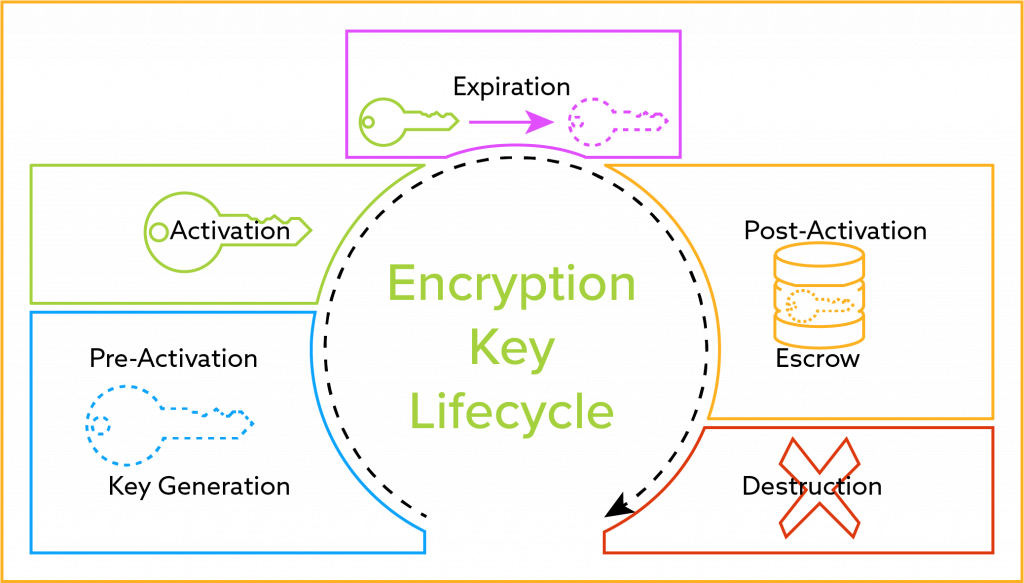
Utilization of cryptographic keys is currently an ordinary BAU prerequisite as numerous administrative bodies have begun to uphold the principles to agree assuming they are managing any classified or PII information. A few normal capacities are featured. The properties of the related key (for example type, length, crypto-period) will rely upon its expected capacity.
Data Encryption Key :
As we read in the above segments, Data classification can be secured utilizing either a symmetric key or an uneven key. Symmetric calculations like 3DES (at present not suggested by numerous individuals of the norms) and AES have key lengths changing somewhere in the range of 128 and 256 pieces, and a commonplace uneven calculation is RSA with a vital length between 1,024 (deplored and not suggested now) and 4,096 pieces. Symmetric encryption keys might be either transient or static relying upon the utilization case with a crypto-period generally in the scope of a day to a year, though lopsided keys are normally having an extraordinary key length (over 1 year). Annihilating a key can be resolved provided that the information encoded is not any more required. On the off chance that the equivalent is required, the keys should be held for the period until in the event that the information can be annihilated and won’t require unscrambling.
Authentication Key :
Without getting a lot into the justification for why this is existing, the fundamental wording of validation is utilized to give confirmation about the other significant component in the CIA group of three which is the honesty of the related information and is frequently combined with symmetric encryption. This is finished utilizing the tried keyed-hash message confirmation code (HMAC) system, which works with a symmetric key. Utilizing the SHA-2 calculation, the run of the mill key length can differ up to 512 pieces and possibly vaporous or static, however ordinarily has a short lifetime. There are sure encryption calculations that give validation without the need to a different verification key.
Digital Signature Key :
Likewise with validation, advanced marks give confirmation about the trustworthiness of its related information. It goes above and beyond to incorporate the idea of non-disavowal too through approving the mark. This requires an unbalanced calculation like RSA (key length 4,096 pieces is favored these days) or ECDSA. The private key lifetime as we saw can be for a more extended span, however the relating public key has an endless lifetime, as it very well might be important to check the mark at any self-assertive point later on.
Key Encryption Key :
KEK is utilized for wrapping the mystery key to guarantee the key is secure during moving utilizing a confirmed encryption component to guarantee its CIA group of three is met. Encryption key sort shifts from one application to another kind. The key utilized for this encryption is generally static thus the key life is likewise long haul (its motivation being to help continuous updates to the key that is being shipped) and the length will straightforwardly rely upon the calculation being utilized.
Master Key :
An expert key as the name says is the significant key in the key order. It is a symmetric key that is utilized to encode various subordinate keys. Key length and the existence cycle is typically the most grounded utilized and is very much ensured either in a confirmed equipment security module (HSM).
Root Key :
A root key is a highest key in a Public Key Infrastructure (PKI) order, which is utilized to confirm and sign advanced declarations of an association. The key age occurs through an interaction called as Key Ceremony where the whole movement is seen by a few people to guarantee the key is shielded from the time it is produced and is normally secured in HSM like Master Key. The greater part of the root keys are awry key-pair with a length ordinarily now at 4,096 pieces relying upon the computerized signature calculation utilized. Root key lifetime is longer and will convey the most administration strategy encompassing it.
What Are the Applications of Cryptography?
Cryptography tracks down use in numerous areas, going from wellbeing in installment entrances, to get informing stages like WhatsApp. A couple of those applications are as per the following –
1. SSL/TLS Encryption: Perusing the web is secure today principally on the grounds that cryptography has permitted you to encode your information stream. Beginning from program ID to server validation, encryption and cryptography, by and large, have worked on web based perusing.
2. Advanced Signatures: With advanced agreements acquiring conspicuousness, the world was in the need of a protected channel to go basic archives through. Cryptography gives a layer of verification so you can be sure with respect to the beginning, secrecy, and honesty of your archives.
3. Safe Online Banking: Internet banking administrations and installment applications would be an idea in retrospect, notwithstanding encryption of information. Cryptography has empowered confirmation frameworks to check the character of specific people prior to permitting them to hold exchanges and assist with decreasing Mastercard extortion simultaneously.
4. Secure Chatting Services: Informing applications like WhatsApp, Telegram, and Signal have now embraced a start to finish encryption convention, which ensures that nobody other than the source and beneficiary can peruse the messages. This is a tremendous move forward from SMS days, where security was dependably a shot in the dark. On account of cryptography, there are a plenty of correspondence stages to utilize.
5. Encoded Emails: With a tremendous measure of private data going through your inbox, having a protected technique for correspondence is an outright need. On account of encryption calculations like PGP (Pretty Good Privacy), your messages are currently encoded consistently.
6. Digital money: With blockchain innovation, digital money has seen a cosmic expansion in financing costs is as yet one of the present generally pursued exchange markets. A totally decentralized, secure, and carefully designed framework has tracked down its direction into the present computerized circle, on account of cryptography. With such countless various roads where cryptography has observed its place, its execution is particular. In the following segment on ‘what is cryptography’, you will see how to proceed with it.
Conclusion :-
CVE-2020-0601 is an exemplary model, of designers ignoring something which ought to have been self-evident, either on account of an absence of comprehension of the basic calculation that they are executing or basically through sheer oversight. As is frequently the situation with Crypto, the issue is with the execution and not with the hidden math. Normally, It is penetrated into designers that they ought not execute their own crypto however should utilize something acknowledged as a standard that has endured everyday hardship. Consider the possibility that the reference execution is itself imperfect as is by all accounts the case on this event. This is when regularly utilized terms like Defense in Depth and Zero Trust stop to be maxims and really may begin to mean something!






