
Hardware devices can only operate as intended because of firmware, which is specific software built in the device. It acts as a link between the hardware and higher-level software of the device by providing low-level control for its particular hardware. Firmware is often found in gadgets like embedded systems, routers, and cellphones. It is crucial to the functionality and performance of contemporary electronics. Frequent firmware updates can address issues, increase security, and improve operation.
1. What’s firmware, and how does it differ from software?
Ans:
Firmware is a technical form of software bedded into tackle bias, furnishing low-position control for the device’s specific tackle. Unlike regular software, which can be fluently modified or streamlined, firmware frequently requires a more complex process to change. It resides in the non-volatile memory, similar to ROM, EEPROM, or flash memory, ensuring it persists indeed when the device is powered off.
2. Describe the typical process of developing and testing firmware.
Ans:
Developing firmware involves several stages demand analysis, design, rendering, testing, and deployment. Initially, masterminds gather conditions and design the firmware armature to meet specific tackle functionalities. Coding is done in low-position languages like C or assembly, considering tackle constraints. Testing is critical and involves unit tests, integration tests, and confirmation on factual tackle to ensure stability and performance.
3. What are the main challenges in firmware development?
Ans:
- Firmware development faces unique challenges due to its close commerce with tackle, taking a deep understanding of tackle armature.
- Resource constraints, similar to limited memory and processing power, demand effective and optimized law.
- Debugging can be complex, frequently challenging technical outfits to diagnose issues at the tackle position.
- Also, ensuring trustability and robustness is pivotal, as firmware failures can lead to complete device malfunction.
- Comity across different tackle variations and the need for thorough testing under various conditions further complicate the development process.
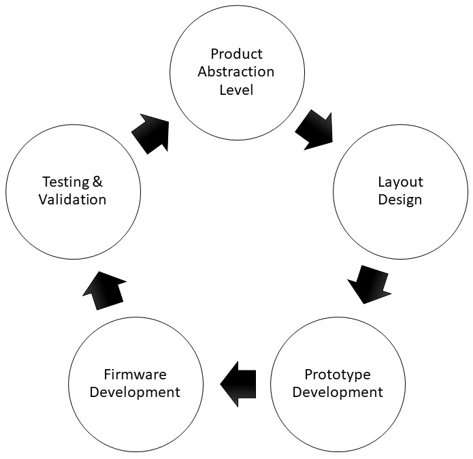
4. Explain the significance of power operation in firmware design.
Ans:
- Power operation in firmware design is essential to extend the battery life and effectiveness of movable and bedded bias.
- Effective power operation involves enforcing strategies similar to sleep modes, power gating, and dynamic frequency scaling.
- Firmware controls these mechanisms to reduce power consumption during idle ages or under low workloads.
- This is particularly critical in battery-powered bias, where conserving energy directly impacts users’ experience and device life.
5. How do you ensure firmware security during development?
Ans:
Ensuring firmware security involves espousing multiple strategies throughout the development lifecycle. Code review and static analysis help identify and amend vulnerabilities beforehand in the coding process. Employing secure coding practices and clinging to assiduity norms alleviate common security pitfalls. Encryption and secure charge mechanisms cover the firmware from unauthorized variations and insure integrity.
6. Can you Discuss the part of bootloaders in firmware?
Ans:
Bootloaders play a critical part in firmware as they’re the first law executed when a device powers on. They initialize tackle factors, set up the necessary terrain, and load the main firmware or operating system into memory. Bootloaders frequently include individual and recovery features, allowing for firmware updates and troubleshooting without taking an external programming device. They must be robust and secure, as they ensure the device’s correct incipiency and can prevent unauthorized firmware from being loaded.
7. What tools and surroundings are generally used for firmware development?
Ans:
- Firmware development generally involves intertwined development surroundings( IDEs) like Keil, IAR Bedded Workbench, or decline with plugins for specific microcontrollers.
- Compilers similar to GCC for ARM or MPLAB XC for PIC microcontrollers restate the firmware law into machine language.
- Debugging tools like JTAG, SWD, and ICE(In-Circuit Parrots) are essential for real-time debugging and testing on tackle.
- Interpretation control systems like Git manage law changes and collaboration among inventors.
- Simulators and parrots replicate the tackle terrain, easing original testing before deployment on factual bias.
8. What’s the difference between polling and intrude-driven I/ O?
Ans:
| Aspect | Polling I/O | Interrupt-Driven I/O |
|---|---|---|
| Process | CPU continuously checks I/O device status. | I/O device sends an interrupt signal to CPU. |
| CPU Efficiency | Inefficient, wastes CPU time. | More efficient, CPU can perform other tasks. |
| CPU Utilization | Constantly engaged with checking devices. | Engaged only when an interrupt occurs. |
| Use Case | Simple systems, predictable I/O needs. | Complex systems, unpredictable I/O needs. |
| Implementation | Easier to implement. | Requires more complex implementation. |
9. What’s the part of a watchdog timekeeper in firmware?
Ans:
A watchdog timekeeper is a tackle point used to automatically reset a system if the software becomes unresponsive or hangs. Firmware regularly resets the watchdog timekeeper within a destined interval, indicating regular operation. However, the watchdog triggers a system reset to restore functionality If the firmware fails to reset the timekeeper due to a crash or horizonless circle. This medium is pivotal for ensuring the trustability and stability of bedded systems, particularly in critical operations.
10. How do you approach remedying firmware issues?
Ans:
Debugging firmware involves a systematic approach to identifying and resolving issues. The original way includes reproducing the problem constantly and segregating the defective module or law member. Tools like JTAG debuggers and oscilloscopes help trace the prosecution inflow and examiner tackle signals. Assaying logs, using breakpoints, and stepping through law give perceptivity into the firmware’s geste. Debugging frequently requires examining tackle relations, checking for timing issues, and vindicating memory operation.
11. What’s memory- counterplotted I/ O, and how is it used in firmware?
Ans:
- Memory—counterplotted I/ O is a system in which the control registers of tackle peripherals are counterplotted to specific memory addresses.
- This allows the CPU to read from and write to these addresses using standard memory instructions, easing tackle control.
- In firmware, memory-counterplotted I/ O simplifies commerce with peripherals like GPIO, timekeepers, and communication interfaces.
- Firmware inventors define pointers to these addresses, enabling direct manipulation of tackle settings and data transfer.
12. Describe the significance of real-time operating systems( RTOS) in bedded firmware.
Ans:
- Real-time operating systems( RTOS) are pivotal in bedded firmware for managing concurrent tasks with precise timing conditions.
- An RTOS provides deterministic geste, ensuring tasks meet their deadlines, which is essential for real-time operations.
- It offers features like task scheduling,inter-task communication, and resource operation, simplifying the development of complex systems.
- By handling task prioritization and intrude operation, an RTOS improves system responsiveness and trustability.
13. How do you ensure the trustability of firmware updates?
Ans:
Ensuring the trustability of firmware updates involves several critical ways. First, using secure bootloaders to corroborate the authenticity and integrity of the update package prevents unauthorized variations. Employing a fail-safe medium, similar to a binary bank or A/ B partitioning, allows the system to return to the former firmware interpretation if the update fails. Testing the update process entirely on various tackle variations and configurations minimizes pitfalls.
14. What’s the purpose of using DMA( Direct Memory Access) in bedded systems?
Ans:
Direct Memory Access( DMA) is used in bedded systems to discharge data transfer tasks from the CPU, allowing for more effective and brisk data running. DMA regulators can move data directly between peripherals and memory without CPU intervention, reducing the processor’s workload and freeing it up for other tasks. This is particularly helpful for high-speed data transfer operations like audio streaming, videotape processing, and detector data accession.
15. How do you manage memory in constrained bedded systems?
Ans:
Managing memory in constrained bedded systems involves optimizing both law and data storehouses to fit within limited coffers. Ways include:
- Using compelling data structures.
- Minimizing the use of global variables.
- Using static memory allocation where possible.
Law optimization strategies, similar to inlining critical functions and using lower data types, help reduce memory footmarks. Memory operation also involves careful segmentation of memory areas for different purposes, such as mound, mound, and buffer allocations, to support fragmentation.
16. What are the standard protocols used for firmware communication with peripherals?
Ans:
- Standard protocols for firmware communication with peripherals include I2C, SPI, UART, and CAN.
- I2C(Inter-Integrated Circuit) is a multi-master,multi-slave protocol used for short-distance communication, frequently for detectors and small peripherals.
- SPI( periodical supplemental Interface) provides high-speed communication with multiple biases using separate timepieces and data lines.
- UART( Universal Asynchronous Receiver- Transmitter) is used for periodic communication, ideal for longer distances and debugging purposes.
- CAN( Controller Area Network) is a robust protocol used in automotive and artificial operations for dependable data transfer between multiple bumps.
17. Explain the conception of’ bare-essence’ programming in bedded systems.
Ans:
Bare- essence’ programming refers to writing firmware directly on the tackle without using an operating system. This approach involves directly managing the tackle coffers, including memory, timekeepers, and peripherals, through low-position programming. Bare-essence programming offers lesser control and effectiveness, which is pivotal for systems with strict real-time conditions and resource constraints.
18 What strategies do you use for debugging timing issues in bedded systems?
Ans:
Debugging timing issues in bedded systems involves several strategies. Using oscilloscopes or sense analyzers allows for precise dimension and visualization of signal timing and synchronization. Enforcing individual law that toggles GPIO legs at crucial points in the firmware can give perceptivity into prosecution timing. Profiling tools and erected-tackle timekeepers help identify backups and measure function prosecution times.
19. What considerations are there when designing firmware for low-power bias?
Ans:
- Designing firmware for low-power bias involves optimizing both tackle and software to minimize energy consumption.
- Ways include using low-power modes and sleep countries to reduce power operation during idle ages and opting for energy-effective peripherals and factors.
- Firmware should manage power-empty operations precisely, cataloging them to do when advanced power countries are formerly needed.
- Effective coding practices, similar to minimizing CPU operation and optimizing data transfers, help reduce overall power consumption.
20. Can you explain how to apply firmware for a new tackle platform?
Ans:
- Enforcing firmware for a new tackle platform starts with understanding the tackle specifications and armature.
- The original method included setting up the development environment, similar to toolchains and IDEs, and configuring the figure system for the target platform.
- The next step involved developing or conforming a bootloader to initialize the tackle and load the main firmware.
- Writing low-position motorists for peripherals(e.g., GPIO, UART, I2C) is pivotal for tackling commerce.
21. What’s the significance of modularity in firmware design?
Ans:
Modularity in firmware design enhances maintainability, scalability, and reusability by breaking down the firmware into lower, tone-contained modules. Each module encapsulates a specific functionality, allowing for more accessible updates and variations without affecting the entire system. This approach promotes law exercise across different systems, as well- defined modules can be integrated into new designs with minimum changes.
22. How do you approach optimizing firmware for performance?
Ans:
Optimizing firmware for performance involves several strategies aimed at reducing prosecution time and resource operation. Sketching the law to identify backups helps concentrate optimization sweats on the most critical areas. Ways similar to circle unrolling, minimizing function calls, and using practical algorithms and data structures ameliorate prosecution speed. Memory access patterns should be optimized to reduce inactivity, and caching mechanisms can be abused for constantly penetrated data.
23. What’s the significance of using unpredictable keywords in bedded C?
Ans:
- The unpredictable keyword in bedded C is used to inform the compiler that a variable’s value may change at any time, precluding the compiler from optimizing out necessary reads or writes to that variable.
- This is particularly important for memory-counterplotted I/ O registers, global variables modified by intrude service routines( ISRs), and flags participated between the main program and ISRs.
- By declaring a variable as unpredictable, you ensure that every access to it results in a factual memory read or write, maintaining the willed geste of the law. Failing to use unpredictably rightly can lead to changeable and delicate-to-diagnose bugs in bedded systems.
24. How do you applyinter-process communication( IPC) in bedded systems?
Ans:
Enforcinginter-process communication( IPC) in bedded systems can be achieved using several mechanisms handed by an RTOS or through custom results. Common styles include communication ranges, semaphores, and mailboxes, which grease data exchange and synchronization between tasks. Shared memory can be used for high-speed data transfer, with careful operation to avoid race conditions. Using pipes or sockets can enable communication between processes running on the same or different systems.
25. What are the standard power operation ways in bedded systems?
Ans:
- Standard power operation methods in bedded systems include dynamic power scaling, where the CPU’s voltage and frequency are acclimated and grounded on workload to conserve energy.
- Sleep and buttress modes are employed to put the device into a low-power state when idle, waking up only for significant events.
- Supplemental power gating widely turns off unused tackle factors to save power.
- Effective use of timekeepers and interrupts minimizes CPU exertion, reducing power consumption.
- Firmware can also employ power profiling tools to identify and optimize power-empty law sections.
26. How do you ensure data integrity in firmware?
Ans:
- Ensuring data integrity in firmware involves several strategies, including enforcing checksums or cyclic redundancy checks( CRC) to describe data corruption during transmission or storehouse.
- Using error-correcting canons( ECC) for memory operations helps identify and correct bit crimes.
- Employing infinitesimal operations and mutexes ensures safe access to participated coffers, precluding race conditions and data corruption.
- Periodic confirmation of critical data structures and state information can describe anomalies beforehand.
- Logging and covering system countries give perceptivity into implicit integrity issues.
27. How do you handle interrupts in bedded systems?
Ans:
- Interrupts are critical in bedded systems for handling asynchronous events, allowing the processor to respond instantly to external or internal signals.
- Effective intrude handling involves jotting intrude Service Routines( ISRs) that are terse and executed snappily to minimize quiescence.
- Prioritizing interrupts ensures that critical events are addressed first, using mechanisms like intrude nesting or precedence situations.
- ISRs should avoid complex sense and instead set flags or use buffers to handle data, postponing expansive processing to the central program circle.
28. How do you handle firmware interpretation control and updates?
Ans:
Firmware interpretation control is managed using interpretation control systems like Git, which track changes, manage law branches, and grease collaboration among inventors. Proper versioning conventions, similar to semantic versioning, help track firmware releases and updates. For firmware updates, secure styles are essential, including vindicating update authenticity using cryptographic autographs and ensuring integrity checks.
29. Explain the significance of the const keyword in bedded C programming.
Ans:
- The const keyword in bedded C programming indicates that a variable’s value is constant and can not be modified after initialization.
- This helps prevent unintended changes to critical data, enhancing law trustability and safety.
- Using const allows the compiler to place these variables in read-only memory, potentially optimizing memory operation and guarding against accidental writes.
- It also enables the compiler to perform fresh optimizations, similar to removing spare memory accesses.
30. What are the benefits and challenges of using C in firmware development?
Ans:
- Using C in firmware development offers benefits similar to object-acquainted programming, which allows for better law association, reusability, and conservation.
- Features like classes, heritage, and polymorphism enable more modular and scalable law.
- C also provides vital type-checking and inline functions, which can lead to optimized and safer laws.
- Still, challenges include increased memory operation and implicit performance outflow compared to C, which is pivotal in resource-constrained surroundings.
31. How do you handle concurrency in bedded systems?
Ans:
Handling concurrency in bedded systems involves using synchronization mechanisms to manage access to participated coffers and help race conditions. Ways include using mutexes and semaphores to ensure that only one task accesses a resource at a time. Critical sections cover law parts that manipulate participated data. Event flags and communication ranges enable safe communication between functions.
32. What’s the significance of a memory chart in bedded systems?
Ans:
A memory chart in bedded systems is pivotal for defining the layout of memory spaces, including ROM, RAM, supplemental registers, and special function registers. It provides a clear structure for where law, data, and tackle control registers live, ensuring proper access and operation. Memory maps help in addressing tackle-specific constraints, like aligning data to memory boundaries and optimizing access pets.
33. What’s the part of timekeepers in bedded systems?
Ans:
- Timekeepers in bedded systems play a pivotal part in managing time-dependent tasks and events.
- They’re used for generating periodic interrupts to perform regular tasks, similar to reading detectors, toggling LEDs, or streamlining displays.
- Timekeepers enable precise detention generation, which is pivotal for timing-sensitive operations.
- They grease palpitation-range modulation( PWM) for motor control, signal generation, and communication protocols.
34. What’s the significance of unit testing in firmware development?
Ans:
- Unit testing is essential in firmware development for vindicating that individual factors, or units, of the firmware function rightly.
- By segregating each unit, similar to a function or module, inventors can describe and fix bugs beforehand in the development process.
- Unit tests help ensure that changes to the law don’t introduce new crimes, supporting retrogression testing.
- They also serve as attestation, clarifying the anticipated geste of the law.
- Automated unit testing enables nonstop integration practices, perfecting development effectiveness and low quality.
35. How do you approach designing firmware for a new microcontroller?
Ans:
Designing firmware for a new microcontroller starts with understanding the tackle specifications, including the CPU armature, peripherals, memory layout, and power conditions. The original setup involves configuring the development terrain, including toolchains and IDEs. Writing low-position motorists for peripherals like GPIO, UART, and timekeepers is pivotal for introductory functionality. Developing a precise modular armature with well-defined interfaces between factors facilitates scalability and conservation.
36. What strategies do you use for optimizing firmware for speed?
Ans:
- Optimizing firmware for speed involves several strategies, including law profiling, to identify backups and critical paths.
- Practical algorithms and data structures reduce computational complexity.
- Inline functions and circle unrolling can drop function call outflow and ameliorate circle performance.
- Memory access patterns should be optimized to minimize quiescence, using cache and prefetching mechanisms where possible.
- Minimizing the use of global variables and optimizing intrude service routines( ISRs) ensures responsive and effective operation.
37. How do you ensure firmware trustability in safety-critical operations?
Ans:
- Ensuring firmware trustability in safety-critical operations involves enforcing robust error discovery and correction mechanisms.
- Ways like checksums and cyclic redundancy checks( CRC) validate data integrity.
- Spare systems and fail-strongboxes, similar to binary-core processing and watchdog timekeepers, help recover from failures.
- Thorough testing, including stress testing, boundary testing, and fault injection, identifies implicit issues under various conditions.
38. What’s the significance of estimation in bedded systems?
Ans:
Estimation in bedded systems ensures that detectors and selectors operate within specified delicacy and performance parameters. It involves confirming the system’s response to match a known standard or reference, compensating for variations in manufacturing, environmental conditions, and aging. Estimation routines may be executed during product, at incipiency, or periodically during operation.
39. How do you apply communication protocols in firmware?
Ans:
Enforcing communication protocols in firmware involves developing motorists and libraries that cleave to the specifications of the chosen protocol, similar to I2C, SPI, UART, or CAN. This includes configuring the tackle interfaces, setting up communication parameters(e.g., baud rate, data format), and handling data transmission and events. Protocol-specific error running and inflow control mechanisms ensure dependable communication.
40. What’s the purpose of the Firmware development?
Ans:
- The purpose of firmware development is to produce low-position software that directly interacts with tackle factors to control and manage their functions.
- Firmware acts as a conciliator between tackle and advanced-position software, ensuring that the tackle operates as intended and provides necessary services to operations.
- It initializes tackle during charge-up, handles device-specific operations, and manages communication protocols.
- Robust and effective firmware enhances device performance, trustability, and functionality.
41. What are the conditions for erecting a bedded system?
Ans:
- Erecting a bedded system requires a clear understanding of the operation and its specific conditions, including functionality, performance, and environmental conditions.
- Essential factors include a microcontroller or microprocessor, memory( both RAM and ROM), input/ affair interfaces, and power operation circuits.
- Proper selection of detectors, selectors, and communication modules grounded on the operation needs is critical.
- Developing dependable and effective firmware to control, tackle, and manage tasks is a crucial part of the process.
42. What are the characteristics of a microprocessor?
Ans:
- A microprocessor is characterized by its capability to perform computation and sense operations, execute instructions from memory, and control input/ affair operations.
- It generally has a central processing unit( CPU) that includes a computation sense unit( ALU), a control unit, and various registers.
- Microprocessors calculate on external memory and peripherals, taking fresh factors to complete the system.
- They’re designed for general-purpose use, making them adaptable for various operations.
43. What are the characteristics of a microcontroller?
Ans:
A microcontroller is a compact intertwined circuit designed for specific control operations, integrating a CPU, memory, and peripherals on a single chip. It features bedded memory, including flash for program storehouse and RAM for data handling, along with I/ O anchorages for uniting with external bias. Microcontrollers are optimized for low power consumption and cost-effectiveness, making them ideal for bedded systems.
44. What are the necessary factors of a microprocessor?
Ans:
The necessary factors of a microprocessor include the central processing unit( CPU), which comprises the computation sense unit( ALU) for performing computation and sensing operations and the control unit for costing, decrypting, and executing instructions. Registers are used for quick data storehousing and manipulation. A timepiece creator provides timing signals to attend operations—the address and data motorcars grease communication with external memory and peripherals.
45. What are microcontrollers?
Ans:
- Microcontrollers are compact integrated circuits designed to control specific functions within a bedded system.
- They integrate a CPU, memory( both RAM and ROM/ Flash), and various peripherals like timekeepers, GPIO anchorages, and communication interfaces on a single chip.
- Microcontrollers are optimized for power effectiveness, cost-effectiveness, and real-time control, making them suitable for operations in consumer electronics, automotive systems, artificial control, and more.
- They frequently include erected- in analog- to- digital transformers( ADCs) and digital- to- analog transformers( DACs) for uniting with detectors and selectors.
46. What are the different types of software and firmware?
Ans:
- The software can be distributed into system software and operation software.
- System software includes operating systems, which manage tackle coffers and provide services for operation software and mileage programs that perform conservation tasks.
- Operation software comprises programs designed for end-users, such as word processors, web cybersurfers, and games.
- Firmware, on the other hand, is specialized software bedded directly into tackle factors to control their functions.
47. What’s the part of storehouse classes in C programming?
Ans:
Storage classes in C programming define the compass, visibility, and continuance of variables and functions within a program. The primary storehouse classes are bus, register, static, and extern. Bus is the dereliction for original variables, limited to the block in which they’re defined. Register suggests storing variables in CPU registers for faster access. Stationary extends the continuance of variables to the entire program duration, conserving their value between function calls while also limiting their compass if used inside a function.
48. What’s the purpose of firmware motorists?
Ans:
Firmware motorists serve as the conciliator between the tackle factors of a bedded system and the operation software. They give a standardized interface to the tackle, abstracting the complications of direct tackle manipulation. Motorists manage tackle initialization, configuration, and control, handling tasks similar to reading detector data, controlling selectors, and communicating with other biases via interfaces like I2C, SPI, and UART.
49. What are stationary variables?
Ans:
- Stationary variables in C programming have a patient continuance, retaining their value across multiple function calls or throughout the program prosecution.
- When declared inside a function, a static variable maintains its value between conjurations of that function, enabling state retention.
- When declared at the train compass, they’re accessible only within that train, furnishing encapsulation and avoiding picking conflicts with other lines.
- Stationary variables are initialized only formerly, with uninitialized static variables defaulting to zero.
50. What are mound bus variables?
Ans:
- Mound bus variables frequently appertained to as original variables, are automatically allocated on the mound when a function is called and deallocated when the function returns.
- They’ve block compasses, meaning they’re only accessible within the function or block in which they’re declared.
- These variables are initialized each time the function is invoked, ensuring they don’t retain values between function calls.
- Bus variables are influential for temporary data storehouse due to their automatic allocation and deallocation, and they contribute to the function’s reentrancy, allowing multiple functions calls to operate singly without snooping with each other’s original data
51. What are league-created memory mound bus variables?
Ans:
The conception of leak- created memory generally refers to memory leaks, a situation where allocated memory isn’t duly deallocated, leading to wasted memory coffers. In the environment of mound bus variables, memory leaks are generally not a concern because these variables are automatically deallocated when the function exits. Still, if a function allocates memory stoutly( using malloc or analogous) and fails to free it before returning, this can result in a memory leak.
52. How does SPI communication work?
Ans:
SPI( periodical supplemental Interface) is a coetaneous periodical protocol for data transmission between microcontrollers and supplemental bias. It operates in a master-slave configuration, where the master initiates communication and controls the timepiece signal( SCK). Data is transferred in full duplex mode, meaning it can be moved and entered contemporaneously through separate lines, MOSI( Master Out Slave In) and MISO( Master In Slave Out).
53. What are transfer buffers and shift registers in SPI communication?
Ans:
- In SPI communication, transfer buffers and shift registers are integral factors that grease data transfer.
- Transfer buffers temporarily hold the data to be transferred or entered, ensuring smooth data inflow and proper timing.
- Shift registers, on the other hand, are used to serially shift data bits in and out of the microcontroller and supplemental bias.
- When data is transmitted, the master’s shift register shifts out data bits onto the MOSI line, while contemporaneously, the enslaved person’s shift register shifts in these bits.
54. What’s the difference between full and partial duplex communication in SPI?
Ans:
- Full duplex communication in SPI( periodical supplemental Interface) allows contemporaneous data transmission and events between the master and slave bias.
- This means data can flow in both directions at the same time, exercising separate data lines( MOSI and MISO).
- In discrepancy, half-duplex communication uses a single data line for both transmission and event, indicating that data can only move in a single direction at once.
- Full duplex is brisk and more effective for high-speed data exchanges, while half-duplex can simplify wiring and be sufficient for lower-demanding operations.
55. What’s the purpose of a timepiece leg in SPI communication?
Ans:
The timepiece leg( SCLK) in SPI communication synchronizes data transfer between the master and slave bias. The master generates the timepiece signal, which dictates the timing of data bits being transmitted and entered. Each timepiece palpitation enables the transfer of one bit of data, ensuring that both biases are accompanied in their operations. The timepiece leg is pivotal for maintaining the integrity and timing of data exchanges, particularly in high-speed dispatches.
56. What’s the timepiece phase in SPI communication?
Ans:
The timepiece phase in SPI communication refers to the timing relationship between the timepiece signal( SCLK) and the data lines( MOSI and MISO). It determines when data is tried and shifted out in relation to the timepiece edges. There are two timepiece phase settings: CPHA = 0 and CPHA = 1. With CPHA = 0, data is tried on the leading( first) edge and shifted out on the tracking( alternate) edge of the timepiece palpitation.
57. What’s the purpose of RDAS and general zilch in assiduity systems?
Ans:
An RTOS( Real- real-time operating System) in artificial systems provides deterministic timing and scheduling capabilities essential for operations taking precise and predictable responses, similar to robotization, robotics, and control systems. It ensures that high-prescendence tasks meet their deadlines, managing coffers efficiently in time-critical surroundings. General Zilch, like Linux or Windows, offers a broader range of features, including multitasking, memory operation, and expansive motorist support, making it suitable for operations where real-time constraints are less strict.
58. What do Linux and Windows motorists do?
Ans:
- Linux and Windows motorists act as interposers between the operating system and tackle bias, enabling the no to communicate with and control tackle factors.
- Motorists restate OS commands into tackle-specific operations, managing device initialization, data transfer, and intrude running.
- In Linux, motorists are frequently integrated into the kernel or loaded as modules, furnishing support for a wide range of tackle.
- Windows motorists follow an analogous model, with a structured motorist development terrain and instrument processes to ensure comity and stability.
59. What’s multitasking?
Ans:
- Multitasking is the capability of an operating system to execute multiple tasks or processes coincidentally, enhancing system effectiveness and responsiveness.
- In bedded systems, multitasking allows different firmware factors, such as detector readings, communication protocols, and user interface updates, to run contemporaneously.
- An RTOS facilitates multitasking by managing task precedences, scheduling, and environment switching, ensuring that critical tasks admit timely CPU access.
- Multitasking improves resource application and system output, enabling more complex and responsive operations.
60. What’s the stylish programming language for firmware development?
Ans:
The stylish programming language for firmware development is frequently C due to its effectiveness, low-position tackle access, and comprehensive support across microcontroller platforms. C provides fine-granulated control over system coffers, enabling precise timing and optimization necessary for bedded operations. Its portability and expansive libraries make it an adaptable choice for various tackle infrastructures. Assembly language may be used for critical performance sections, while C can offer object-acquainted features where complexity operation is demanded.
61. What’s the purpose of writing firmware?
Ans:
Firmware is written to control the tackle of a device and to give low-position control for the device’s specific functions. It acts as the conciliator between the device tackle and advanced-position software operations, ensuring that tackle factors perform their intended tasks. Firmware initializes tackle factors, manages coffers, and handles device-specific protocols. It’s essential for the correct operation of bias, similar to bedded systems, consumer electronics, and artificial machines.
62. What’s the purpose of the SPI protocol?
Ans:
- The periodical supplemental Interface( SPI) protocol is used for short-distance communication between a controller device and one or further slave bias.
- It provides a high-speed, full-duplex, coetaneous data transfer system, making it ideal for operations taking fast data exchange.
- SPI is generally used to connect microcontrollers to peripherals similar to detectors, memory bias, and display regulators.
- The protocol’s simplicity and effectiveness, characterized by its use of four cables( MISO, MOSI, SCLK, and SS), allow for straightforward perpetration and minimum outflow.
63. What’s the difference between a traditional API and an ultramodern API?
Ans:
- Traditional APIs frequently calculate on aged communication protocols and formats, similar to Cleaner( Simple Object Access Protocol) and XML, which can be circumlocutory and complex.
- They generally bear detailed specifications and strict contract delineations.
- Ultramodern APIs, on the other hand, typically use REST( Emblematic State Transfer) principles, using HTTP and JSON or XML for featherlight and mortal- readable data exchange.
- Ultramodern APIs emphasize simplicity, scalability, and ease of use, frequently supporting tone-descriptive dispatches and stateless relations.
64. What’s the purpose of motorist APIs?
Ans:
Motorist APIs give a standardized interface for software operations to interact with and tackle bias. They abstract the complications of tackle operations, allowing inventors to control bias without demanding to understand the detailed workings of the tackle. Motorist APIs handle tasks similar to transferring commands to the device, managing data transfers, and handling interrupts or crimes. By offering a harmonious interface, motorist APIs enable software portability and ease of development across different tackle platforms.
65. What are the parameters of storehouse classes?
Ans:
- Compass Determines the visibility of a variable within the law, similar to an original or global compass.
- Continuance Indicates how long a variable remains active in memory, ranging from automatic( original variables) to static( patient throughout the program’s prosecution).
- Relation Specifies the visibility of a variable across multiple lines, similar to internal( static) or external relation.
- Storage position Defines where the variable is stored, which can be by registers( register storehouse class) or in memory( automatic or stationary storehouse classes).
66. What’s the difference between a traditional API and an ultramodern API?
Ans:
- Traditional APIs are generally designed around rigid, protocol-specific structures similar to Cleaner and XML-RPC, taking detailed specifications and frequently complex setups.
- They tend to be less flexible and more challenging to integrate with ultramodern web technologies.
- Ultramodern APIs are generally peaceful, using HTTP and featherlight data formats like JSON. They emphasize simplicity, scalability, and ease of use, with stateless relations and tone-descriptive dispatches.
- Ultramodern APIs are designed to be more adaptable to different platforms, including web, mobile, and IoT, promoting easier integration and faster development cycles.
67. What’s the purpose of motorist APIs?
Ans:
Motorist APIs serve as an abstraction subcaste between the tackle and operation software, allowing inventors to interact with tackle factors through formalized function calls. They simplify the process of controlling tackle by furnishing easy-to-use interfaces that handle complex tackle operations, similar to initialization, configuration, data transfer, and intrude operation. This abstraction enables software to be more movable and tackle-independent, reducing development time and trouble.
68. What are the parameters of storehouse classes?
Ans:
Storage classes in C and C define the compass, visibility, and continuance of variables and functions. The primary storehouse classes are bus, register, static, and extern. The bus keyword, which is implicit for original variables, indicates automatic storehouse duration. The register keyword suggests that the variable should be stored in the CPU register for faster access. The static keyword extends the continuance of variables to the duration of the program and restricts the visibility of functions to the train compass.
69. What’s Flashing?
Ans:
- Flashing refers to the process of installing or streamlining the firmware on a microcontroller or bedded device.
- This involves writing the firmware binary into the device’s flash memory, which is a type ofnon-volatile storehouse.
- The process generally requires a tackle programmer or an in-system programming( ISP) interface and software tools to load the firmware image.
- Flashing ensures that the device runs the rearmost interpretation of the firmware, incorporating new features, bug fixes, and security updates.
70. Could you describe Firmware armature?
Ans:
- Firmware armature consists of several layers, generally including the tackle abstraction subcaste( HAL), device motorists, middleware, and operation law.
- The HAL provides a livery interface to interact with the underpinning tackle, abstracting tackle-specific details.
- Device motorists manage the operations of peripherals, similar to detectors, communication interfaces, and selectors.
- Middleware includes libraries and services that support the operation, similar to train systems, communication heaps, and real-time operating systems( RTOS).
71. What’s meant by middleware testing?
Ans:
Middleware testing involves vindicating the functionality, performance, and trustability of the middleware factors in a bedded system. Middleware serves as a central subcaste that provides services similar to data operation, communication protocols, and device abstraction. Testing ensures that these services perform rightly under various conditions and interact seamlessly with both the operation subcaste and the underpinning tackle.
72. How does firmware communicate to the electronic bias to perform its operations?
Ans:
Firmware communicates with electronic bias through tackle interfaces and communication protocols. It uses device motorists to control and interact with peripherals, similar to detectors, selectors, and communication modules. For illustration, the firmware might use I2C or SPI protocols to communicate with detectors, UART for periodic communication, and GPIO legs for direct control of digital signals.
73. How do you validate your firmware previous to installation?
Ans:
- Validating firmware previous to installation involves a thorough testing process, including unit tests, integration tests, and system tests.
- Simulation and emulation tools can replicate the target tackle terrain, allowing for expansive testing without physical bias.
- Functional testing ensures that the firmware meets the specified conditions and behaves as anticipated.
- Performance testing evaluates the firmware’s effectiveness and responsiveness under various conditions.
74. What does DMA address to deal with?
Ans:
- Direct Memory Access( DMA) addresses deal with the direct transfer of data between memory and peripherals without CPU intervention.
- DMA regulators manage these transfers by addressing specific memory locales and supplemental registers.
- This allows for effective data movement, freeing up the CPU to perform other tasks and perfecting system performance.
- DMA is generally used in operations taking high-speed data transfers, similar to audio and video streaming, detector data accession, and communication interfaces.
75. What are the advantages of bedded systems?
Ans:
Bedded systems offer several advantages, including devoted functionality, which ensures optimized performance for specific tasks. Their small size and low power consumption make them ideal for movable and battery-operated bias. Bedded systems are cost-effective due to their simplified tackle and software, which can reduce manufacturing and functional costs. They give actual- time processing capabilities, essential for operations taking precise timing and control.
76. Define intrude quiescence. How are you going to minimize it?
Ans:
- Intrude quiescence is the time detention between the generation of an intrude by a supplemental and the launch of the corresponding intrude service routine( ISR).
- Minimizing intrude quiescence involves several strategies, similar to optimizing ISR law to execute snappily and efficiently, thereby reducing the time spent handling each intrude.
- Configuring intrude precedences ensures that critical interrupts are serviced instantly.
- Using a fast timepiece speed and effective intrude regulators can also help. Reducing the number of nested interrupts and turning off unnecessary interrupts during critical sections further minimizes quiescence.
77. What’s a semaphore?
Ans:
- A semaphore is a synchronization medium used in bedded systems to manage access to participated coffers and coordinate task prosecution.
- It consists of a counter that tracks the vacuity of a resource, with tasks incrementing or decrementing the counter when penetrating or releasing the resource.
- Double semaphores( mutexes) control single resource access while counting semaphores handle multiple cases of a resource.
- Semaphores help race conditions by ensuring that only one task can pierce the resource at a time.
78. What Are Some Of The Most Common crimes set up In Bedded Systems?
Ans:
Common crimes in bedded systems include buffer overflows, which occur when data exceeds buffer capacity, leading to memory corruption and implicit security vulnerabilities. Mound overflows are when the call mound exceeds its limit, causing changeable geste or system crashes. Memory leaks are affected by indecorous memory operation, leading to reduced available memory over time. Timing issues, similar to missed deadlines in real-time systems, can beget malfunction.
79. Why Is a Horizonless Loop Necessary In Bedded Systems?
Ans:
A horizonless circle is necessary for bedded systems to keep the main program running continuously, as these systems generally operate without termination. This circle allows the system to constantly check and respond to inputs, perform tasks, and manage events. Within the horizonless circle, the system can enter low-power countries when idle, waking up only for significant events or periodic tasks. The horizonless circle ensures that the system remains responsive and functional, fulfilling its intended functions indefinitely.
80. What Is A Software Update?
Ans:
A software update involves modifying the firmware or software running on a bedded system to facilitate functionality, fix bugs, enhance security, or add new features. Enforcing secure update mechanisms ensures that only authenticated and vindicated updates are applied, precluding unauthorized variations. A well-designed update process includes rollback capabilities to revert to the former interpretation in case of failures.
81. How are motorcars employed in bedded systems to communicate?
Ans:
- Motorcars in bedded systems are used to transfer data between different factors, similar to the CPU, memory, and peripherals.
- Common types of motorcars include I2C, SPI, UART, and CAN, each suited for specific communication prerequisites.
- Variables like complexity, distance, and data rate determine the machine of choice.
- For illustration, I2C is used for short-distance communication between chips, while CAN is used in automotive operations for its robustness.
82. chapeau are some most frequently encountered difficulties while dealing with interruptions?
Ans:
- Dealing with interruptions in bedded systems can be challenging due to several factors.
- Intrude quiescence, or the time taken to respond to an intrusion, must be minimized to ensure the timely prosecution of critical tasks.
- Priority operation is pivotal, as inaptly prioritized interrupts can lead to task starvation or missed deadlines.
- Shared resource access requires careful running to avoid race conditions and data corruption.
- Nested interrupts, where an intrude occurs within another intrude tutor, complicate the control inflow and increase the threat of mound overflow.
83. What are 32-bit and 64-bit microcontrollers, and are 8-bit microcontrollers still in use?
Ans:
32-bit and 64-bit microcontrollers have wider data motorcars, registers, and memory address spaces compared to 8-bit microcontrollers, enabling them to handle more complex calculations and larger data sets. They’re generally used in operations taking advanced performance, similar to advanced automotive systems, IoT bias, and artificial robotization. Despite the advantages of 32-bit and 64-bit MCUs, 8-bit microcontrollers are still extensively used due to their simplicity, lower cost, and lower power consumption.
84. How do I optimize firmware for limited tackle coffers?
Ans:
Optimizing firmware for limited tackle coffers involves several strategies. Effective coding practices, similar to minimizing the use of global variables and using original variables, help reduce memory operation. Stationary memory allocation prevents fragmentation and ensures predictable memory consumption. Using optimized algorithms and data structures improves computational effectiveness. Code size can be reduced through compiler optimizations, similar to enabling optimization flags and removing gratuitous laws.
85. the Difference between RAM and ROM in an environment of firmware.?
Ans:
- RAM And ROM serve different purposes in firmware.
- RAM is unpredictable memory used for temporary data storehouses, including mound, mound, and runtime variables, which are lost when power is removed.
- It allows read and write operations and is pivotal for dynamic data handling during firmware prosecution.
- ROM, on the other hand, isnon-volatile memory used to store the firmware law and constant data, retaining its contents indeed when power is out.
- It’s generally read-only during regular operation, ensuring the integrity of the firmware.
86. Explain unpredictable keyword firmware development.?
Ans:
- The unpredictable keyword in firmware development indicates that a variable’s value can change suddenly, precluding the compiler from optimizing down accesses to that variable.
- This is pivotal for variables associated with tackle registers, participated data by intrude service routines( ISRs), or flags modified by other vestments.
- With unpredictable, the compiler might assume the variable stays the same and optimize out necessary reads or writes, leading to incorrect geste.
- Using unpredictability ensures that every access to the variable is performed as written in the law, maintaining the willed operation and trustability of the firmware.
87. Discuss the challenges when developing firmware for resource-constrained bias.
Ans:
- Developing firmware for resource-constrained bias involves managing limited memory, recycling power, and energy coffers.
- Optimizing law size and prosecution speed is critical, frequently taking the use of practical algorithms and data structures.
- Memory operation becomes complex, as inventors must avoid fragmentation and ensure that critical data is always accessible.
- Power operation ways, similar to sleep modes and dynamic voltage scaling, are necessary to extend battery life.
88. Explain finite impulse response( FIR) sludge?
Ans:
A Finite Impulse Response( FIR) sludge is a type of digital sludge used in signal processing. It relies on a finite number of former input values to induce its affair, hence the name. The sludge’s response to an impulse input is limited to a finite duration, as determined by the sludge’s portions. These portions, which define the sludge’s characteristics, are fixed and don’t change over time.
89. What’s double softening fashion in firmware development?
Ans:
Double buffering is a fashion used in firmware development to enhance data recycling effectiveness, particularly in systems taking smooth and nonstop data transfer, similar to plate rendering or audio streaming. It involves using two memory buffers to hold data. One buffer is diligently used by the processor to read or write data, while the other buffer is being prepared or filled. Once the active buffer’s operations are complete, the places of the buffers are shifted, allowing continued data inflow and minimizing quiescence.
90. Explain error-correcting canons( ECC).
Ans:
Error-correcting canons( ECC) are ways used in digital communication and storehouse systems to describe and correct crimes that occur during data transmission or storehouse. ECC adds spare data, known as equality bits, to the original information. When data is entered or read, the system uses these equality bits to check for and correct crimes. Common ECC styles include Hamming canons, Reed- Solomon canons, and cyclic redundancy checks( CRC).




