
An embedded system is actually a combination of hardware and software considering any computer system. It mainly helps to configure the system as programmable or fixing some better feature which improves its capability. It also helps for designing some of the specific function(s) considering any computer system which is larger than usual. There are a lot of electronics instruments which are mainly popular due to identifying the proper location and helping people to find out to reach a destination with that location identifier. Embedded system main helps to identify a possible location in Industrial varieties machines, automobiles, equipment of medical, cameras, airplanes, toys, house equipment, etc.
Now, if you are looking for a job that is related to the Embedded System then you need to prepare for the 2020 Embedded System Interview Questions. It is true that every interview is different as per the different job profiles. Here, we have prepared the important Embedded System Interview Questions and Answers which will help you get success in your interview.
1. What Are The Different Adder Circuits You Studied?
Ans:
Adders are generally of five types:
- Ripple Carry Adder: The Ripple carry adder(RCA) consists of a building block named Half Adder(HA) which is cascaded to form a Full Adder(FA). These building blocks HAs and FAs are also the building blocks of all types of adders. The n full adders are cascaded to form n bit RCA. The full adder has three input pins(input Ai, input Bi, carrying Ci) and two output pins(Sum and Ci+1). Its equations are:
- Sum=Ai^Bi^Ci
- Ci+1=Ai.Bi+Bi.Ci+Ai.Ci
- Carry Lookahead Adder: The Carry Lookahead Adder(CLA) reduces the delay like that in RCA. Let
- Gi=Ai.Bi, and Pi=Ai^Bi, then Ci+1=Gi+Pi.Ci.
The expressions for Sum and Ci+1 are then defined completely in terms of input pins rather than wait for input carry to appear.
- Carry Select Adder: The carry select adder uses duplicate modules for each combination of input carry(i.e. 1 and 0). The multiplexers then select the appropriate sum and carry output according to the carry output of the preceding stages.
2. What is the difference between microcontrollers and microprocessors?
Ans::
A CPU, memory, and peripherals are all combined on a single chip in microcontrollers. They are designed for specific tasks and often used in embedded systems. Microprocessors, on the other hand, are standalone CPUs used in general-purpose computing devices.
3. How do you select a microcontroller for a specific embedded system application?
Ans:
Selecting a microcontroller for a specific embedded system application: Choose a microcontroller based on factors such as processing power, memory requirements, I/O capabilities, communication interfaces, power efficiency, cost, and development ecosystem compatibility.
4) Explain the basic components of an embedded system.
Ans:
Basic components of an embedded system: An embedded system typically consists of a microcontroller/microprocessor (CPU), memory (RAM and ROM), input devices (sensors), output devices (actuators), communication interfaces, and sometimes additional hardware components like analog-to-digital converters (ADCs) or display modules.
5) What is the importance of interrupt handling in embedded systems?
Ans:
Importance of interrupt handling in embedded systems: Interrupts enable the microcontroller to respond promptly to critical events. They allow the system to pause the main program’s execution and handle time-sensitive tasks or events, such as real-time input/output, without wasting CPU cycles.
6) How can power usage in an embedded system be optimised?
Ans:
To optimize power consumption, use low-power components, implement sleep modes when idle, disable unused peripherals, use efficient algorithms, and minimize clock frequencies when possible. Additionally, optimize code to reduce unnecessary CPU usage.
7) Describe the variations between RAM and ROM in an embedded system.
Ans:
- RAM (Random Access Memory) is volatile, used for temporary data storage during program execution, read/write capable, and loses data when power is removed.
- ROM (Read-Only Memory) is non-volatile, used for permanent data/code storage, read-only, and retains data even without power.
8) What is the role of an ADC (Analog-to-Digital Converter) in embedded systems?
Ans:
Role of an ADC (Analog-to-Digital Converter) in embedded systems: ADC converts analog signals from sensors to digital data, allowing the microcontroller to process and utilize real-world information, such as temperature, light, or pressure.
9) How would you interface an external memory device with a microcontroller?
Ans:
Interfacing an external memory device with a microcontroller: Connect address, data, and control lines between the microcontroller and the memory device. Software drivers manage read/write operations to access data stored in the external memory.
10) Explain the concept of a watchdog timer in embedded systems.
Ans:
Concept of a watchdog timer in embedded systems: The watchdog timer monitors system health and must be reset periodically by software. If the software fails to reset it due to a crash or freeze, the watchdog timer triggers a reset to recover the system.
11) What are boot loaders used for and how do they operate?
Ans:
The boot loader initializes the system and loads the main application/firmware from non-volatile memory (e.g., Flash). It ensures a known starting state and allows firmware updates or setup before executing the main application.
12) Describe the process of signal conditioning in embedded hardware design.
Ans:
Signal conditioning involves modifying an analog signal from a sensor or source to make it suitable for processing by the microcontroller. This process may include amplification, filtering, level shifting, noise reduction, and analog-to-digital conversion. The conditioned signal is then digitized and processed by the microcontroller for various applications.
13) What are the key considerations when designing a low-cost embedded system?
Ans:
Key considerations when designing a low-cost embedded system:
- Select cost-effective components and microcontrollers with just enough features for the application.
- Minimize the number of external components and peripherals.
- Optimize power consumption to reduce operating costs.
- Utilize free or open-source software tools and development environments.
14) How do you ensure signal integrity in high-speed embedded systems?
Ans:
Ensuring signal integrity in high-speed embedded systems:
- Use controlled impedance traces and match the transmission line characteristics to minimize signal reflections and noise.
- Properly terminate signals to reduce reflections and ringing.
- Implement ground and power planes to provide stable reference voltages and reduce noise.
15) Explain the steps involved in testing and debugging an embedded hardware design.
Ans:
Steps involved in testing and debugging an embedded hardware design:
- Unit testing
- Integration testing
- Functional testing
- Performance testing
- Hardware debugging
- Software debugging
- System validation
16) What Are Set-Up Time & Hold Time Constraints? What Do They Signify? Which One Is Critical For Estimating Maximum Clock Frequency Of A Circuit?
Ans:
- Suppose your flip-flop is a positive edge triggered. The time for which data should be stable prior to a positive edge clock is called setup time constraint.
- Time for which data should be stable after the positive edge of the clock is called as a hold time constraint.
- If any of these constraints are violated then flip-flop will enter in a metastable state, in which we cannot determine the output of flip-flop.
- There are two equation:
- Tcq + Tcomb> Tskew + Thold
- Tcq + Tcomb<Tskew +T – Tsetup
There is a time delay when data enters the flip-flop and data comes at output of flip flop.The tomb is the logic delay between two flip flops.Askew is the delay of the clock to flip flop: suppose there are two flip flop if clock reaches first to source flip flop and then after some delay to destination flip flop, it is positive skew and if vice versa then negative skew.so if you take 2 eq you will see that setup time is the determining factor of the clock’s time period.
17) Give A Circuit To Divide Frequency Of Clock Cycle By Two?
Ans:
You can divide the frequency of a clock by just implementing T Flip flop.Give clock as clock input and tie the T input to logic 1.
18) How Do You Detect If Two 8-bit Signals Are Same?
Ans:
XOR each bit of A with B (for eg A[0] xor B[0] ) and so on. the o/p of 8 xor gates are then given as i/p to an 8-i/p nor gate. if o/p is 1 then A=B.
19) Give Two Ways Of Converting A Two Input Nand Gate To An Inverter?
Ans:
One way is shorting the two inputs of the NAND gate and passing the input.truth table:A B output1 1 00 0 1The second way is passing the input to only one input(say A) of the NAND gate. Since the other input(say B) is floating, it is always a logical one.truth table:A B output1 1 00 1 1
20) Design A Divide-by-3 Sequential Circuit With 50% Duty Cycle?
Ans:
Take a smiths counter with 3 f/f’s that is to say with 6 states(2*3) now double the i/p clock frequency to the counter the o/p of the 3rd f/f is divide by 6 of the i/p with 50% duty cycle so effectively u got to divide by 3 freq with 50% duty cycle
21) Give The Truth Table For A Half Adder. Give A Gate Level Implementation Of The Same?
Ans:
TRUTH TABLE FOR HALF ADDER:A B SUM CARRY0 0 0 00 1 1 01 0 1 01 1 0 1IMPLEMENTATION:
- For SUM, The two inputs A and B are given to the XOR gate.
- For Carry, The two inputs A and B are given to AND gate.
22) What type of registers contains an INTEL CPU?
Ans:
Special function registers like accumulator, program controller (PC), data pointer (DPTR), TMOD and TCON (timing registers), 3 register banks with r0 to r7, Bit addressable registers like B.
23) Differentiate the microprocessor and microcontroller?
Ans:
As now you are fundamentally familiar with what is a microcontroller And microprocessor, it is easy to recognize the significant contrasts between a microcontroller and microprocessor.
- The key difference in both of them is the presence of external peripherals, where microcontrollers have RAM, ROM, EEPROM embedded in it while we have to use external circuits in case of microprocessors.
- As all the peripherals of the microcontroller is on a single chip it is compact while the microprocessor is bulky.
- Microcontrollers are made by using complementary metal oxide semiconductor technology so they are far cheaper than microprocessors. In addition, the applications made with microcontrollers are cheaper because they need lesser external components, while the overall cost of systems made with microprocessors is high because of the high number of external components required for such systems.
- The processing speed of microcontrollers is about 8 MHz to 50 MHz, but in contrast processing speed of general microprocessors is above 1 GHz so it works much faster than microcontrollers.
- Generally, microcontrollers have a power-saving system, like idle mode or power saving mode so overall it uses less power, and also since external components are low overall consumption of power is less. While in microprocessors generally there is no power saving system and also many external components are used with it, so its power consumption is high in comparison with microcontrollers.
24) What is a Preprocessor?
Ans:
Preprocessor is a Program That processes its input data to produce output that is used as input to another program. The output is said to be a preprocessed form of the input data, which is often used by some subsequent programs like compilers. The amount and kind of processing done depends on the nature of the preprocessor.
- Some Pre-processors Are Only Capable Of Performing Relatively Simple Textual Substitutions And Macro Expansions, while others have the power of full-fledged programming languages.
- A Common Example From Computer programming is the processing performed on source code before the next step of compilation. In some computer languages (e.g., C and PL/I) there is a phase of translation known as preprocessing. It can also include macro processing, file inclusion, and language extensions.
25) Which is better: a char, short, or int type for optimization?
Ans:
Where possible, it is best to avoid using char and short as local variables. For the types char and short the compiler needs to reduce the size of the local variable to 8 or 16 bits after each assignment. This is called sign-extending for signed variables and zero extending for unsigned variables.
- It is implemented by shifting the register left by 24 or 16 bits, followed by a signed or unsigned shift right by the same amount, taking two instructions (zero-extension of an unsigned char takes one instruction).
- These shifts can be avoided by using int and unsigned int for local variables. This is particularly important for calculations that first load data into local variables and then process the data inside the local variables.
- Even if data is input and output as 8- or 16-bit quantities, it is worth considering processing them as 32-bit quantities
26) What are inline functions?
Ans:
The ARM compilers support inline functions with the keyword __inline.
- These results in each call to an inline function being substituted by its body, instead of a normal call.
- This results in faster code, but it adversely affects code size, particularly if the inline function is large and used often.
27) Why do we need virtual device drivers when we have physical device drivers?
Ans:
Device drivers are basically a set of modules/routines so as to handle a device for which a direct way of communication is not possible through the user’s application program and these can be thought of as an interface thus keeping the system small providing for minimalistic additions of code if any.
- Physical device drivers can’t perform all the logical operations needed in a system in cases like IPC, Signals, and so on…
- The main reason for having virtual device drivers is to mimic the behavior of certain hardware devices without it actually being present and these could be attributed to the high cost of the devices or the unavailability of such devices.
- These basically create an illusion for the users as if they are using the actual hardware and enable them to carry out their simulation results.
- Examples could be the use of virtual drivers in case of Network simulators, also the support of virtual device drivers in case a user runs an additional OS in a virtual box kind of software.
28) What is Dirac delta function and its Fourier transform and its importance?
Ans:
- Dirac delta function is a continuous-time function with unit are and infinite amplitude at t=0.
- The Fourier transform of Dirac delta function is 1.
- Using Dirac delta as an input to the system, we can get the system response. It is used to study the behavior of the circuit. We can use this system behavior to find the output for any input.
29) Differentiate testing and verification?
Ans:
Verification is a front end process and testing is a post-silicon process. Verification is to verify the functionality of the design during the design cycle. Testing is to find manufacturing faults.
- a &= ~BIT3;
- }
- Some people prefer to define a mask together with manifest constants for the set and clear values. This is also acceptable. The element that I’m looking for is the use of manifest constants, together with the |= and &= ~ constructs
30) #define cat(x,y) x##y concatenates x to y. But a cat(cat(1,2),3) does not expand but gives preprocessor warning. Why?
Ans:
In this case the cat(x,y) is the macro which is defined by using the preprocessor directive , this will be substituted only at the place where it is called in this example it happens like this
cat(1,2)##3 which will once again become 1##2##3
here if we use ## in between we can join or concatenate only two variables that why it gives a preprocessor warning.
31) What is DMAC in ES?
Ans:
Direct memory access (DMA) is a feature of computer systems that allows certain hardware subsystems to access main system memory (random-access memory) independent of the central processing unit (CPU). DMA is also used for intra-chip data transfer in multi-core processors.
32) What is the need for DMAC in ES?
Ans:
- Direct memory access is mainly used to overcome the disadvantages of interrupt and program controlled I/O.
- DMA modules usually take control over from the processor and perform the memory operations and this is mainly because to counteract the mismatch in the processing speeds of I/O units and the processor. This is comparatively faster.
- It is an important part of any embedded systems, and the reason for their use is that they can be used for bursty data transfers instead of single-byte approaches.
- It has to wait for the systems resources such as the system bus in case it is already in control of it.
33) What is the Endianness of a system and how do different systems communicate with each other?
Ans:
- Endianness basically refers to the ordering of the bytes within words or larger bytes of data treated as a single entity.
- When we consider a several bytes of data say for instance 4 bytes of data, XYZQ the lower byte if stored in a Higher address and others in successively decreasing addresses, then it refers to the Big Endian and the vice versa of this refers to Little Endian architecture.
- Intel 80×86 usually follows Little Endian and others like IBM systems follow Big Endian formats.
- If the data is being transmitted care has to be taken so as to know as to which byte, whether the higher or the lower byte is being transmitted.
- Hence a common format prior to communication has to be agreed upon to avoid wrong interpretation/calculations.
- Usually, layer modules are written so as to automate these conversions in Operating systems.
34) How are macros different from inline functions?
Ans:
- Macros are normally used whenever a set of instructions/tasks have to be repeatedly performed. They are small programs to carry out some predefined actions.
- We normally use the #define directive in case we need to define the values of some constants so in case a change is needed only the value can be changed and is reflected throughout.
- define mul(a,b)(a*b)
The major disadvantage of macros is that they are not really functions and the usual error checking and stepping through of the code does not occur. Inline functions are expanded whenever it is invoked rather than the control going to the place where the function is defined and avoids all the activities such as saving the return address when a jump is performed. Saves time in case of shortcodes.
- Inline float add(float a, float b)
- {
- Return a+b;
- }
35) What could be the reasons for a System to have gone blank and how would you Debug it?
Ans:
Possible reasons could be:
- PC being overheated.
- Dust has been accumulated all around.
- CPU fans not working properly .
- Faulty power connections.
- Faulty circuit board from where the power is being drawn.
- Support Drivers not being installed.
Debugging steps which can be taken are:
- Cleaning the system thoroughly and maintaining it in a dust-free environment. Environment that is cool enough and facilitates easy passage of air should be ideal enough.
- By locating the appropriate support drivers for the system into consideration and having them installed.
36) Explain interrupt latency and how can we decrease it?
Ans:
- Interrupt latency basically refers to the time span an interrupt is generated and is being serviced by an appropriate routine defined, usually the interrupt handler.
- External signals, some conditions in the program or by the occurrence of some event, these could be the reasons for generation of an interrupt.
- Interrupts can also be masked so as to ignore them even if an event occurs for which a routine has to be executed.
- Following steps could be followed to reduce the latency
- ISRs being simple and short.
- Interrupts being serviced immediately
- Avoiding those instructions that increase the latency period.
- Also by prioritizing interrupts over threads.
- Avoiding the use of inappropriate APIs.
37) How to create a child process in linux?
Ans:
- Prototype of the function used to create a child process is pid_t fork(void);
- The fork is the system call that is used to create a child process. It takes no arguments and returns a value of type pid_t.
- If the function succeeds it returns the pid of the child process created to its parent and the child receives a zero value indicating its successful creation.
- On failure, a -1 will be returned in the parent’s context, no child process will be created, and errno will be set.
- The child process normally performs all its operations in its parents context but each process independently of one another and also inherits some of the important attributes from it such as UID, current directory, root directory, and so on.
38) Significance of watchdog timer in Embedded Systems.
Ans:
- Watchdog timer is basically a timing device that is set for a predefined time interval and some event should occur during that time interval else the device generates a time out signal.
- One application where it is most widely used is when the mobile phone hangs and no activity takes place, in those cases watchdog timer performs a restart of the system and comes to the rescue of the users.
- It is used to reset to the original state whenever some inappropriate events take place such as too many commands being given at the same time or other activities that result in malfunctioning of the GUI. It is usually operated by counter devices.
39) If you buy some RTOS, what are the features you look for in?
Ans:
- Deterministic operating system having guaranteed worst-case interrupt latency and context-switch times.
- Documentation provides for the minimum, average, and maximum number of clock cycles required by each system call.
- Interrupt response times should be very minute.
- Context switch time should be very low.
- Compatibility with several plugin devices.
- Overall it should be very reliable.
40) Why is java mostly used in embedded systems?
Ans:
- Java was mainly designed and conceptualized for code that can work on different platforms without any hassles and also for being secure enough so as to not harm or corrupt other modules of code.
- Features like exception handling, simple syntax and Automatic Garbage collection all work in its favor as the language for use in ES’s.
- Also that it is widely used in the form of Java applets makes it very popular confining it to the limits of JVM. It is Dynamic in nature.
- Its use is also being exploited in enterprise systems in the form of J2EE, J2SE, J2ME in case of mobile applications.
41) Differentiate between mutexes vs semaphores.
Ans:
- Semaphores is a synchronization tool to overcome the critical section problem.A semaphore S is basically an integer variable that apart from initialization is accessed only through atomic operations such as wait() and signal().Semaphore object basically acts as a counter to monitor the number of threads accessing a resource.
- A mutex is also a tool that is used to provide deadlock free mutual exclusion. It protects access to every critical data item. If the data is locked and is in use, it either waits for the thread to finish or awakens to release the lock from its inactive state.
42) What is the need for having multibyte data input and output buffers in case of device ports?
Ans:
It’s normally the case that some devices transfer the output either in a bursty or a sequential manner and also during input entry. If we take the example of keyboards, all the data entered is stored in a buffer and given at a time or one character at a time. In case of networking there may be several requests to access the same resource and all these are queued in a buffer and serviced in the order they are received. Hence to avoid the input/output units from getting overloaded with requests, we use multibyte buffers.
43) What is read modify write technique?
Ans:
- Read modify write is a technique used to access the ports.
- Here is a single instruction, all three actions are combined.
- Here initially the data is read from the port then modified .
- At last the value is written back on the port.
- This feature saves many lines of code and makes the process easier.
44) In which addressing mode is the DPTR register used?
Ans:
- Data pointer register is used in the indexed addressing mode.
- It is used in accessing data from the look-up table entries stored in ROM.
- SYNTAX: MOVC A, @A+DPTR
- Here c means the code (shows data elements are stored in code space of ROM).
- The contents of A are added to 16-bit DPTR to form the 16-bit address of the needed data.
45) Which registers are used for register indirect addressing mode if data is on-chip?
Ans:
- R0 and R1 are the only registers used for register indirect addressing mode.
- These registers are 8 bit wide.
- Their use is limited to accessing only internal RAM.
- When these registers hold addresses of RAM, they must be preceded by a @ sign.
- In the absence of this sign, it will use the contents of the register than the contents of memory location pointed by the same register.
46) Of the 128-byte internal RAM, how many bytes are bit addressable?
Ans:
- Only 16 bytes of the 128 bytes of RAM are bit addressable.
- The bit addressable RAM locations are 20H to 2FH.
- They are addressed as 0 to 127 (decimal) or 00 to 7F.
- Also the internal RAM locations 20 to 2FH are both byte and bit addressable.
- These 16 bytes can be by single bit instructions using only direct addressing mode.
47) Explain the parallel address space.
Ans:
- The two physically separate memories using the same addresses from the parallel address space.
- Here the two memories are accessed using different access modes.
- This parallel addressing is generally used in 8052(enhanced version of 8051) having extra 128 bytes of RAM with addresses 80 to FFH and memory is called as upper memory.
- This distinguishes it from lower 128 bytes 00to 7FH.
- To access lower bytes direct addressing mode is used and for higher bytes, indirect addressing mode is used.
48) Which port in 8051 performs a dual role?
Ans:
- The port 3 can be used as a simple input /output port or provides signals like interrupts.
- P3.0 and p3.1 are used for serial communication.
- P3.2 and P3.3 are used as external interrupts.
- P3.4 and P3.5 are used for timers.
- P3.6 and P3.7 are used as read-write signals of external memory.
49) Explain high-end embedded processor.
Ans:
- The microcontroller & processor can be interchangeably used here.
- It forms a general purpose processor.
- High-end stands for a system of greatest power.
- Here when a microcontroller cannot do a specific task the processor does the same with higher power
- Example: ADM 64
50) Which 8051 version is using UV-EPROM?
Ans:
- Ultraviolet EPROM is used in version 8751.
- Here it becomes easier to erase the data using uv rays.
- It takes around 20 minutes to erase the data.
- To overcome this shortcoming flash ROM versions of 8751 available.
51) Which 8051 version uses Flash ROM?
Ans:
- Atmel Corporation is manufacturing flash ROM
- The 89C51 chip of Atmel is using flash ROM.
- Here no Rom eraser is needed.
- The erasing process is done by the PROM burner itself.
- To avoid use of PROM burner the 8052 version support in-system programming.
52) In which registers the immediate values cannot be directly loaded?
Ans:
- The general purpose registers named A,B, R0-R7 can not accept the immediate data.
- To indicate an immediate value pound sign is used before it.
- These registers accept 8-bit data preceding a pound sign.
- There are registers present in 8051 used to store data temporarily.
53) What are the pros and cons of using assembly in embedded systems?
Ans:
Pros of using assembly language in embedded systems:
- These programs are hardware-oriented.
- The code is portable as long as the same processor is used.
- The execution of instructions is fast.
- Insertions and deletions can be made easily.
Cos of using assembly language:
- The programs are long and can get complicated.
- The programs are not easily run on systems smaller in size.
- The code cannot be run on systems of different processor designs.
- There is no provision of a System Development Kit.
54) What are some automated tools to test embedded systems?
Ans:
Some automated tools for testing embedded systems are Parasoft, Tessy, TestPlant, and Klocwork.
55) How are unions useful in embedded systems?
Ans:
Unions are used in embedded systems for applications that have different modes of operation. Then the data that is specific to a model can be placed in a structure, and these structures can be placed in a union. This helps in-memory optimization.
56) What is interrupt latency in embedded systems?
Ans:
An interrupt latency is a latency that occurs while handling the interrupts. It is the amount of time that elapses between the arrival of an external interrupt and the processing of the interrupt.
57) What are actuators in embedded systems?
Ans:
An actuator is a device that is used to control the movements of systems and machines. It uses sources of power like electric current or hydraulic fluid. After receiving a control signal, it converts the signal’s energy into mechanical motion.
58) What is the reentrant function in embedded systems?
Ans:
A reentrant function is used in embedded systems for executing multiple tasks together without any data corruption issues. This function can be paused at any time and restarted again based on the requirements. It protects local data and preserves global data by creating a local copy of that data. It must not call functions that are non-reentrant.
59) Explain What Are The Different Qualifiers In C?
Ans:
- Volatile: A variable should be declared volatile whenever its value could change unexpectedly. In practice, only three types of variables could change:
- Memory-mapped peripheral registers
- Global variables modified by an interrupt service routine
- Global variables within a multi-threaded application
- Constant: The addition of a ‘const’ qualifier indicates that the (relevant part of the) program may not modify the variable.
60) Explain What Are The 5 Different Types Of Inheritance Relationship?
Ans:
5 level types are as under:
- single: B derived from A.
- multilevel: derived from B and B derived from A.
- multiple: C derived from A and B.
- Hierarchical: B derived from A and C derived from A.
- hybrid: combination of the above types.
61) Explain What Will This Return Malloc(sizeof(-10))?
Ans:
- It will return a 4-byte address value.
- Because -10 is a signed integer(varies from compiler to compiler).
62) Explain Can Structures Be Passed To The Functions By Value?
Ans:
Yes, structures can be passed to functions by value. Though passing by value has two disadvantages:
- The charges by the calling function are not reflected.
- It’s slower than the pass by the reference function call.
63) Explain Can We Have Constant Volatile Variable?
Ans:
Const and volatile keywords should not be used together because both are opposite in nature. A variable is declared as “const” means it’s value is not able to be changed but if it is declared as “Volatile” then it is not under control.
64) Explain What Are The Different Storage Classes In C?
Ans:
Four types of storage classes are there in c.
- Auto
- Register
- Static
- Extern or Global
65) Explain What Is Forward Reference W.r.t. Pointers In C?
Ans:
Pointer used to refer to value a into int a=10 to memory add this value and 10 is added p value-added this data in memory location for p.
66) How Is Function Itoa() Written In C?
Ans:
- #include<stdlib.h>
- #include<stdio.h>
- int main()
- {
- int n = 6789;
- char p[20];
- itoa(n,s,10);
- printf(“n=%d,s=%s”,n,s);
- return 0;
- }
67) How To Define A Structure With Bit Field Members?
Ans:
You can define struct bit field members with Dot operators.
EXAMPLE:
- #include <stdio.h>
- int main()
- {
- Struct bit_field
- {
- Int x.4; // it allocates only 4 bits to x
- Char C.6; // it allocates only 6 bits to C;
- };
- return 0;
- }
68) What Is The Difference Between Fifo And The Memory?
Ans:
Fifo(First In Last Out) is a memory structure where data can be stored and retrieved (in the order of its entry only). This is a queue, whereas Memory is a storage device that can hold data dynamically or at any desired location and can be retrieved in any order.
69) Is It Necessary To Start The Execution Of A Program From The Main() In C?
Ans:
“Normally you are at liberty to give functions whatever names you like, but “main”‘ is special – your program begins executing at the beginning of main. This means that every program must have a main somewhere.”
70) What Is An Anti Aliasing Filter? Why Is It Required?
Ans:
Anti-aliasing filter reduces errors due to aliasing. If a signal is sampled at 8 kS/S, the max frequency of the input should be 4 kHz. Otherwise, aliasing errors will result. Typically a 3.4kHz will have an image of 4.6 kHz, and one uses a sharp cut off filter with a gain of about 1 at 3.4kHz and gain of about 0.01 at 4.6 kHz to effectively guard against aliasing. Thus one does not quite choose max frequency as simply fs/2 where fs is the sampling frequency. One has to have a guard band of about 10% of this max and chooses max signal frequency as 0.9*fs/2.
71) How To Implement A Fourth Order Butterworth Lp Filter At 1khz If Sampling Frequency Is 8 kHz?
Ans:
A fourth order Butterworth filter can be made as a cascade of two-second order LP filters with a zeta of 0.924 and 0.383. One can use a bilinear transformation approach for realizing second order LP filters. Using this technique described well in many texts, one can make two second-order LP filters and cascade them.
72) Is 8085 An Embedded System?
Ans:
It’s not an embedded system…because it will be a part of an embedded system and it does not work on any software.
73) What Is The Role Of Segment Register?
Ans:
In the x86 processor architecture, memory addresses are specified in two parts called the segment and the offset. One usually thinks of the segment as specifying the beginning of a block of memory allocated by the system and the offset as an index into it. Segment values are stored in the segment registers. There are four or more segment registers: CS contains the segment of the current instruction (IP is the offset), SS contains the stack segment (SP is the offset), DS is the segment used by default for most data operations, ES (and, in more recent processors, FS and GS) is an extra segment register. Most memory operations accept a segment override prefix that allows the use of a segment register other than the default one.
74) What Type Of Registers Contains An (intel) Cpu?
Ans:
Special function registers like accumulator, Program controller(PC),data pointer(DPTR), TMOD and TCON (timing registers),3 register banks with r0 to r7, Bit addressable registers like B.
75) What Is the PLC System?
Ans:
Programming logical control system
76) What Is The Use Of A Volatile Keyword?
Ans:
- The C’s volatile keyword is a qualifier that tells the compiler not to optimize when applied to a variable. By declaring a variable volatile, we can tell the compiler that the value of the variable may change any moment from outside of the scope of the program. A variable should be declared volatile whenever its value could change unexpectedly and beyond the comprehension of the compiler.
- In those cases it is required not to optimize the code, doing so may lead to erroneous results and load the variable every time it is used in the program. Volatile keyword is useful for memory-mapped peripheral registers, global variables modified by an interrupt service routine, global variables accessed by multiple tasks within a multi-threaded application.
77) Can A Variable Be Both Const And Volatile?
Ans:
The const keyword makes sure that the value of the variable declared as const can’t be changed. This statement holds true in the scope of the program. The value can still be changed by outside intervention. So, the use of const with a volatile keyword makes perfect sense.
78) Can A Pointer Be Volatile?
Ans:
If we see the declaration volatile int *p, it means that the pointer itself is not volatile and points to an integer that is volatile. This is to inform the compiler that pointer p is pointing to an integer and the value of that integer may change unexpectedly even if there is no code indicating so in the program.
79) What Is Size Of Character, Integer, Integer Pointer, Character Pointer?
Ans:
- The size of the character is 1 byte.
- The size of the integer is 4 bytes.
- The size of integer pointer and character is 8 bytes on a 64-bit machine and 4 bytes on a 32-bit machine.
80) What Is Null Pointer And What Is Its Use?
Ans:
The NULL is a macro defined in C. Null pointer actually means a pointer that does not point to any valid location. We define a pointer to be null when we want to make sure that the pointer does not point to any valid location and not to use that pointer to change anything. If we don’t use the null pointer, then we can’t verify whether this pointer points to any valid location or not.
81) What Is Void Pointer And What Is Its Use?
Ans:
The void pointer means that it points to a variable that can be of any type. Other pointers point to a specific type of variable while void pointer is a somewhat generic pointer and can be pointed to any data type, be it standard data type(int, char etc) or user-defined data type (structure, union, etc.). We can pass any kind of pointer and reference it as a void pointer. But to dereference it, we have to type the void pointer to correct the data type.
82) What Is ISR?
Ans:
An ISR(Interrupt Service Routine) is an interrupt handler, a callback subroutine which is called when an interrupt is encountered.
83) What Is Return Type Of Isr?
Ans:
ISR does not return anything. An ISR returns nothing because there is no caller in the code to read the returned values.
84) Can We Use Any Function Inside ISR?
Ans:
We can use functions inside ISR as long as that function is not invoked from other portions of the code.
85) Can We Use Printf Inside Isr?
Ans:
Printf function in ISR is not supported because the print function is not reentrant, thread-safe and uses dynamic memory allocation which takes a lot of time and can affect the speed of an ISR up to a great extent.
86) Can We Put Breakpoint Inside Isr?
Ans:
Putting a breakpoint inside ISR is not a good idea because debugging will take some time and a difference of half or more second will lead to different behavior of hardware. To debug ISR, definitive logs are better.
87) Can Static Variables Be Declared In A Header File?
Ans:
A static variable cannot be declared without defining it. A static variable can be defined in the header file. But doing so, the result will be having a private copy of that variable in each source file which includes the header file. So it will be wise not to declare a static variable in the header file unless you are dealing with a different scenario.
88) Is Countdown To Zero Loop Better Than Count_up_loops?
Ans:
Countdown to zero loops are better. Reason behind this is that at loop termination, comparison to zero can be optimized by the compiler. Most processors have instructions for comparing to zero. So they don’t need to load the loop variable and the maximum value, subtract them, and then compare to zero. That is why countdown to zero loops is better.
89) Can we call any function inside ISR?Explain them with example.
Ans:
Yes, you can call a function within the ISR but it is not recommended because it can increase the interrupt latency and decrease the performance of the system. If you want to call a nested function within the ISR, you need to read the datasheet of your microcontroller because some vendors have a limit to how many calls can be nested.
- One important point needs to be remembered that the function that is called from the ISR should be re-entrant. If the called function is not re-entrant, it could create issues.
For example,
If the function is not reentrant and supposes that it is called by another part of the code beside the ISR. So the problem will be invoked when the ISR calls the same function which is already invoked outside of the ISR?
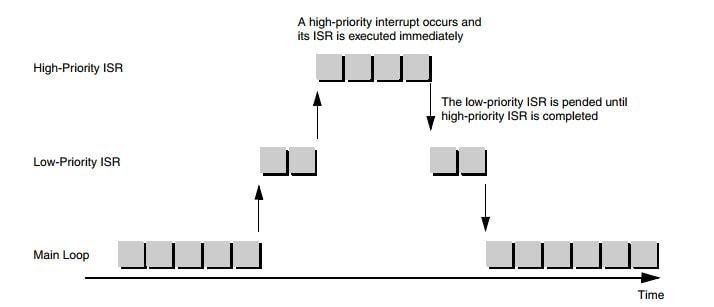
90) What is a nested interrupt?
Ans:
In a nested interrupt system, an interrupt is allowed to any time, and anywhere even an ISR is being executed. But, only the highest priority ISR will be executed immediately. The second highest priority ISR will be executed after the highest one is completed.
The rules of a nested interrupt system are:
- All interrupts must be prioritized.
- After initialization, any interrupts are allowed to occur anytime and anywhere.
- If a low-priority ISR is interrupted by a high-priority interrupt, the high-priority ISR is executed.
- If a high-priority ISR is interrupted by a low-priority interrupt, the high-priority ISR continues executing.
- The same priority ISRs must be executed by time order
If you want to learn STM32 from scratch, you should follow this course “Mastering Microcontroller with Embedded Driver Development“. The course contains video lectures of 18.5-hours length covering all topics like, Microcontroller & Peripheral Driver Development for STM32 GPIO, I2C, SPI, USART using Embedded C.

91) What is NVIC in ARM Cortex?
Ans:
The Nested Vector Interrupt Controller (NVIC) in the Cortex-M processor family is an example of an interrupt controller with extremely flexible interrupt priority management. It enables programmable priority levels, automatic nested interrupt support, along with support for multiple interrupt masking, whilst still being very easy to use by the programmer.
- The Cortex-M3 and Cortex-M4 processors the NVIC supports up to 240 interrupt inputs, with 8 up to 256 programmable priority levels
92) Can we change the interrupt priority level of the Cortex-M processor family?
Ans:
Yes, we can.
93) Why is “C” language mostly preferred than assembly language?
Ans:
- C helps programmers focus on the structure of the code rather than the low-level demands of the CPU. They can organize code into components, such as functions and files and they have ways of managing the complexity of a project; without thinking about the nitty-gritty of issues such as how function calls work.
- Since C is a portable language, code can be organized into general-purpose libraries that can be used on any platform, often with no modification. It is a great weapon against ‘reinventing the wheel.
94) What is the start-up code?
Ans:
A start-up code is called prior to the main function, it creates a basic platform for the application. It is a small block of code that is written in assembly language.
There are the following parts of the start-up code.
- Declaration of the Stack area.
- Declaration of the Heap area.
- Vector table.
- Reset handler code.
- Other exception handler code.
95) What are the start-up code steps?
Ans:
Start-up code for C programs usually consists of the following actions, performed in the order described:
- Disable all interrupts.
- Copy any initialized data from ROM to RAM.
- Zero the uninitialized data area.
- Allocate space for and initialize the stack.
- Initialize the processor’s stack pointer.
- Create and initialize the heap.
- Enable interrupts.
- Call main.
96) What is meant by structure padding?
Ans:
- In the case of structure or union, the compiler inserts some extra bytes between the members of structure or union for the alignment, these extra unused bytes are called padding bytes and this technique is called padding.
- Padding has increased the performance of the processor at the penalty of memory. In structure or union data members aligned as per the size of the highest bytes member to prevent the penalty of performance.
Note: Alignment of data types mandated by the processor architecture, not by language.
97) What is endianness?
Ans:
The endianness is the order of bytes to store data in memory and it also describes the order of byte transmission over a digital link. In the memory data store in which order depends on the endianness of the system, if the system is big-endian then the MSB byte store first (means at lower address) and if the system is little-endian then LSB byte store first (means at lower address)
98) What is big-endian and little-endian?
Ans:
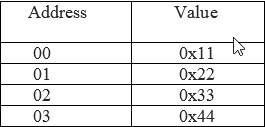
Suppose, 32 bits Data is 0x11223344.

Big-endian
The most significant byte of data stored at the lowest memory address.
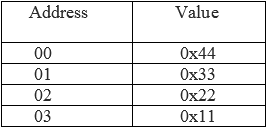
Little-endian
The least significant byte of data stored at the lowest memory address.
99) What is static memory allocation and dynamic memory allocation?
Ans:
According to C standard, there are four storage duration, static, thread (C11), automatic, and allocated. The storage duration determines the lifetime of the object.
The static memory allocation:
Static Allocation means, an object has an external or internal linkage or declared with static storage-class. It’s initialized only once, prior to program startup and its lifetime is throughout the execution of the program. A global and static variable is an example of static memory allocation.
The dynamic memory allocation:
- In C language, there are a lot of library functions (malloc, calloc, or realloc,..) which are used to allocate memory dynamically. One of the problems with dynamically allocated memory is that it is not destroyed by the compiler itself; that means it is the responsibility of the user to deallocate the allocated memory.
- When we allocate the memory using the memory management function, they return a pointer to the allocated memory block and the returned pointer is pointing to the beginning address of the memory block. If there is no space available, these functions return a null pointer.
100) What Is A Inode?
Ans:
In computing, an inode is a data structure on a traditional Unix-style file system such as UFS. An inode stores basic information about a regular file, directory, or other file system object.



