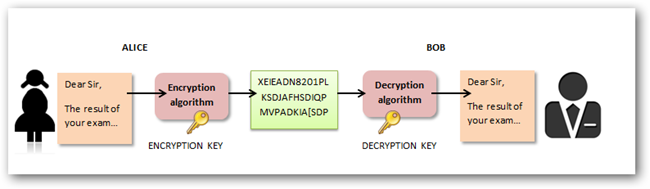
Encryption is the process of encoding information.This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext.Only authorized parties can decipher a ciphertext back to plaintext and access the original information.Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key, but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often utilized in military messaging. Since then, new techniques have emerged and become commonplace in all areas of modern computing.Modern encryption schemes utilize the concepts of public-key and symmetric-key.Modern encryption techniques ensure security because modern computers are inefficient at cracking the encryption.
What is Data Encryption in Network Security?
Noted antivirus and endpoint security experts at Kaspersky define encryption as “… the conversion of data from a readable format into an encoded format that can only be read or processed after it’s been decrypted.”
They go on to say that encryption is considered the basic building block of data security, widely used by large organizations, small businesses, and individual consumers. It’s the most straightforward and crucial means of protecting information that passes from endpoints to servers.
Considering the elevated risk of cybercrime today, every person and group that uses the internet should be familiar with and incorporate basic encryption techniques, at the very least.
How does encryption work?
Let’s try to solve the above riddle.
If you move two steps forward (+2) from each character in the encrypted text “wms,” you’d see that each successive character turns out to become “you”. This +2 is the “key” here—used to encrypt the answer and decrypt the puzzle. Now go ahead and apply the +2 key on English alphabet A-Z to decipher Qcaspgrw gq gknmprylr.
The answer is: Security is important.
Modern encryption tools work in a similar fashion but use more complex keys to encode and decode data based on some standard algorithms. Only people, or systems, with the key to the algorithm used can decipher the encrypted data.
A four-bit key uses 2^4 or 16 combinations while a 256-bit key uses 2^256 or 1.1 x 10^77 combinations for ciphering text, making it stronger.
Symmetric vs. asymmetric encryption
Symmetric encryption: Symmetric encryption uses a single key to encrypt as well as decrypt data. The key needs to be shared with all authorized people.
Asymmetric encryption: Also called public key cryptography, asymmetric encryption uses two separate keys—one public (shared with everyone) and one private (known only to the key’s generator). The public key is used to encrypt the data and the private key helps to decrypt it.
Asymmetric encryption
The 4 common encryption methods
There are different encryption methods based on the type of keys used, key length, and size of data blocks encrypted. Here we discuss some of the common encryption methods.
1. Advanced Encryption Standard (AES)
Advanced Encryption Standard is a symmetric encryption algorithm that encrypts fixed blocks of data (of 128 bits) at a time. The keys used to decipher the text can be 128-, 192-, or 256-bit long. The 256-bit key encrypts the data in 14 rounds, the 192-bit key in 12 rounds, and the 128-bit key in 10 rounds. Each round consists of several steps of substitution, transposition, mixing of plaintext, and more. AES encryption standards are the most commonly used encryption methods today, both for data at rest and data in transit.
2. Rivest-Shamir-Adleman (RSA)
Rivest-Shamir-Adleman is an asymmetric encryption algorithm that is based on the factorization of the product of two large prime numbers. Only someone with the knowledge of these numbers will be able to decode the message successfully. RSA is often used in digital signatures but works slower when large volumes of data need to be encrypted.
3. Triple Data Encryption Standard (TripleDES)
Triple Data Encryption Standard is a symmetric encryption and an advanced form of the DES method that encrypts blocks of data using a 56-bit key. TripleDES applies the DES cipher algorithm three times to each data block. TripleDES is commonly used to encrypt ATM PINs and UNIX passwords.
4. Twofish
Twofish is a license-free encryption method that ciphers data blocks of 128 bits. It’s considered the successor to the Blowfish encryption method that ciphered message blocks of 64 bits. Twofish always encrypts data in 16 rounds regardless of the key size. Though it works slower than AES, the Twofish encryption method continues to be used by many file and folder encryption software solutions.
Use cases of encryption
Your data can either be in-transit or at-rest. Data in either of these forms needs to be encrypted according to its sensitivity.
Online payments: PCI-DSS standards mandate payment card data (stored as well as in-transit forms) to be encrypted using algorithms such as AES-256.
Data in the cloud: In public and hybrid cloud models, your data resides at a third-party data center. Any attack on co-tenants can result in your data getting exposed too. Encrypting your data in the cloud prevents hackers from being able to read it correctly. Your cloud provider will also not be able to pry on your data if you alone have the encryption key. Check with your cloud provider to understand what security measures it offers.
Databases: Encrypting databases help to restrict external hackers as well as insiders from seeing specific organizational data. Transparent database encryption (TDE) is a popular database encryption technique that helps to encrypt all “data at rest” in one go.
Emails: Email encryption helps to protect sensitive information sent through email channels. Public key encryption methods along with digital certificates are usually the methods used for securing email communications.
Steps to implement an effective encryption strategy
Building and implementing an encryption strategy is a collaborative effort between your IT, operations, and management teams. Here are some steps that’ll help you build an effective encryption strategy.
Classify data: You need to identify what data to encrypt. Understand and classify different types of data you transmit and store—card details, customer names and emails, company sales data, intellectual property data, and more—based on sensitivity, use, and regulatory impact.
Identify the right encryption tools: In most cases, you wouldn’t need to implement a separate encryption software. Encryption features are present in commonly used apps and security tools such as email security, payment gateways, and cloud security software. But for encrypting databases or sensitive individual files, you might need separate encryption tools.
Encyrption options in MEO
Encryption options in MEO file encryption software (Source)
Implement strong key management practices: If your keys fall into the wrong hands, your data security is at stake. You need to keep an inventory of all your encryption keys, along with information on who has access to them and how and when the keys have been used. Key management solutions help you to store and manage encryption keys.
Understand the limitations of encryption: Encryption does not help you prevent or detect cyberattacks. It only ensures that hackers will not be able to read your data. Hence, along with encrypting data, it is also important to implement other strong cybersecurity and intrusion detection measures such as anti-virus solutions and firewalls.
Why Do We Need Encryption?
If anyone wonders why organizations need to practice encryption, keep these four reasons in mind:
- Authentication. Public key encryption proves that a website’s origin server owns the private key and thus was legitimately assigned an SSL certificate. In a world where so many fraudulent websites exist, this is an important feature.
- Privacy. Encryption guarantees that no one can read messages or access data except the legitimate recipient or data owner. This measure prevents cybercriminals, hackers, internet service providers, spammers, and even government institutions from accessing and reading personal data.
- Regulatory Compliance. Many industries and government departments have rules in place that require organizations that work with users’ personal information to keep that data encrypted. A sampling of regulatory and compliance standards that enforce encryption include HIPAA, PCI-DSS, and the GDPR.
- Security. Encryption helps protect information from data breaches, whether the data is at rest or in transit. For example, even if a corporate-owned device is misplaced or stolen, the data stored on it will most likely be secure if the hard drive is properly encrypted. Encryption also helps protect data against malicious activities like man-in-the-middle attacks, and lets parties communicate without the fear of data leaks.
The Three Important Types of Encryption Techniques
There are several data encryption approaches available to choose from. Most internet security (IS) professionals break down encryption into three distinct methods: symmetric, asymmetric, and hashing. These, in turn, are broken down into different types. We’ll explore each one separately.
What is the Symmetric Encryption Method?
Also called private-key cryptography or a secret key algorithm, this method requires the sender and the receiver to have access to the same key. So, the recipient needs to have the key before the message is decrypted. This method works best for closed systems, which have less risk of a third-party intrusion.
On the positive side, symmetric encryption is faster than asymmetric encryption. However, on the negative side, both parties need to make sure the key is stored securely and available only to the software that needs to use it.
What is the Asymmetric Encryption Method?
Also called public-key cryptography, this method uses two keys for the encryption process, a public and a private key, which are mathematically linked. The user employs one key for encryption and the other for decryption, though it doesn’t matter which you choose first.
As the name implies, the public key is freely available to anyone, whereas the private key remains with the intended recipients only, who need it to decipher the messages. Both keys are simply large numbers that aren’t identical but are paired with each other, which is where the “asymmetric” part comes in.
What is Hashing?
Finally, there’s hashing. Hashing generates a unique signature of fixed length for a data set or message. Each specific message has its unique hash, making minor changes to the information easily trackable. Data encrypted with hashing cannot be deciphered or reversed back into its original form. That’s why hashing is used only as a method of verifying data.
Many internet security experts don’t even consider hashing an actual encryption method, but the line is blurry enough to let the classification stand. The bottom line, it’s an effective way of showing that no one has tampered with the information.
ADVANTAGE OF USING ENCRYPTION TECHNOLOGY
1. You Can Use It Across a Variety of Devices
One of the top advantages of modern encryption technology is that you can apply it to all or most of the tech devices you use. Data on an iPhone gets encrypted by default as long as you lock it with a password or the Touch ID feature. On an Android phone, it’s easy to walk through an encryption process within the Security menu of the Settings section. Some Android devices also have encryption enabled when you purchase them.
There are free and paid options for encrypting your computer, too. Depending on your needs, companies offer full hard disk or file-based encryption. Also, don’t overlook the choices available for encrypting the content on an SD card or thumb drive. Since some many possibilities exist for people who want to encrypt their data, it’s worth at least researching to see which methods are most appropriate for you. Internet traffic should also be encrypted. Most secure VPN providers always use the 256-bit encryption protocol.
Multi-device encryption is also becoming more important as SMS marketing becomes more prevalent. A study by Grandview Research estimates that the market for SMS marketing is growing by 20.5% a year from 2019 to 2025. A growing number of companies are using text messages to reach their customers.
2. It Could Help You Avoid Regulatory Fines
Depending on your given industry or the specific policies set forth by your employer, encryption technology for data protection may become mandatory rather than optional. For example, in the health care sector, patient privacy laws require keeping information encrypted. Organizations receive significant fines for noncompliance.
In one case occurring in June 2018, the University of Texas’s MD Anderson Cancer Center received a $4.3 million penalty for violating the Health Insurance Portability and Accountability Act, more commonly known as HIPAA. The trouble began in 2012 when a thief stole a laptop containing 30,000 patient records from an employee’s home. That same year, as well as in 2013, there were two separate instances of more data loss via misplaced USB drives.
The devices containing the data were not encrypted. The judge that ruled in the case brought up that glaring oversight when he issued the fine. In health care, as well as other industries that often handle sensitive information, regulatory fines are genuine concerns. Besides how these incidents cut into an organization’s profits, bad publicity could give people second thoughts about doing business with companies that don’t responsibly store data.
3. It Helps You Stay Safer When Working Remotely
Companies are now more frequently requiring workers to solely use encrypted devices due to incidents like these. That’s not surprising, considering how other technological advances make it easier for employees to stay productive from anywhere.
However, according to a 2018 North American report published by Shred-It, the majority of business leaders believe data breach risks are higher when people work remotely. More specifically, 86% of C-Suite executives and 60% of small-business owners hold that view. Whether you work remotely all the time or just occasionally, data encryption helps you stop information from falling into the wrong hands.
4. It Supports Data Integrity
Something else to keep in mind about encryption technology for data protection is that it helps increase the integrity of the information alone. Indeed, encryption alone does not guarantee this, but it’s something you can and should use as part of an overall strategy. If you trust the data, it’s easier to use confidently to make business decisions.
Statistics show that poor data quality is a primary reason why 40% of all business initiatives fail to achieve their targeted benefits. High-quality information can help you learn more about your customers, track trends and otherwise find out things you might otherwise miss. Companies often deploy techniques like data cleansing to improve quality, and that’s a good start.
Data encryption could help ensure that only authorized parties access a firm’s information for analysis. It also decreases the likelihood of a hacker successfully tampering with data, and those actions going unnoticed.
5. Data Encryption Is a Privacy Safeguard
Consider the information you have stored on your smartphone or computer, and you can probably understand why encryption keeps your identity secure along with your data. On a smartphone, for example, encryption apps can make it virtually impossible, or at least exceptionally challenging, for any unauthorized person to access your information. In several instances, law enforcement officials have had difficulty investigating phone data on encrypted devices.
For everyday users that won’t typically worry about their phones becoming evidence, data encryption can stop sensitive details from unknowingly going live on the internet. Once hackers compromise information such as email addresses, the rightful owners may not know what’s happened until months pass.
To get an idea of how massive data breaches can become, think about the recent case where more than 770 million email addresses and passwords were exposed to a hacking forum. The cybersecurity researcher who discovered it pointed out that the information likely came from many individual data breaches rather than one gigantic compromise.
Even so, the sheer number of the exposed email/password combinations is enough to highlight how effective hackers can be at obtaining information. It’s also frightening that hackers are getting more creative regarding the ways they use seized data. Some of them impersonate doctors after taking the information associated with medical licenses. Others nab frequent flier miles and use them to make unauthorized flight ticket purchases.
6. Data Encryption Could Provide a Competitive Advantage
Since data encryption applies both to information at rest and in transit, it provides consistent protection that could lead to peace of mind for the people who handle information.
Research shows that a growing percentage of businesses know that creating an encryption plan is essential. A 2019 study presented by Ponemon Institute found that, during the fiscal year 2018, 45% of the companies polled reported having an overall encryption strategy applied consistently across their organizations. Slightly less (42%) mentioned having a limited encryption strategy used for certain applications or types of data.
Only 13% said they did not have a strategy at all. That research suggests that if your enterprise fails to prioritize encryption, it could lag compared to competitors. The good news is that the encryption software market is growing.
A market forecast from Grand View Research assessed the encryption software market and gave a projection for the period from 2019-2025. The firm expects a combined annual growth rate (CAGR) of 16.8% for the specified timeframe, with on-premise options being in the majority as cloud-based options steadily grow.
7. Using Encryption Technology for Data Protection Could Increase Trust
Even when not required to encrypt data due to privacy regulations, some companies choose to do so to show their clients they take privacy seriously. Making that assertion is particularly important due to the eroding trust many people have in the internet.
According to the 2019 CIGI-Ipsos Global Survey on Internet Security and Trust, 53% of respondents said they were more concerned about online privacy now than a year ago. The same survey indicated that nearly half of those polled (49%) said that their distrust of the internet made them disclose less personal information online. Surprisingly, only 19% of people surveyed said they used more encryption to increase safety.
Those findings open an opportunity for companies to bolster consumer trust by explicitly stating how they encrypt customer data. Although end-users need to take responsibility as well, enterprises can solidify their reputations by emphasizing a commitment to incorporating the latest encryption technologies into their operations.





