
- What is Ethical Hacking?
- Advantages Of Ethical hacking
- Ethical hacking process
- What are Hacking Tools?
- Conclusion
What is Ethical Hacking?
Moral Hacking is an approved act of bypassing framework security to recognize potential information breaks and dangers in an organization. The organization that possesses the framework or organization permits Cyber Security architects to perform such exercises to test the framework’s protections. Along these lines, dissimilar to noxious hacking, this interaction is arranged, endorsed, and all the more critically, legitimate.
Moral programmers intend to explore the framework or organization for flimsy parts that malevolent programmers can take advantage of or annihilate. They gather and examine the data to sort out ways of reinforcing the security of the framework/organization/applications. Thusly, they can further develop the security impression so it can more readily endure assaults or redirect them.

- The unexpected ascent in the interest for moral hacking that is being seen is an aftereffect of innovative advances that lead to numerous dangers in the innovation circle on the planet. A moral programmer fills in as an association by shielding their framework and its data from unlawful programmers as digital assaults and digital psychological oppression is extraordinarily developing.
- Understanding and getting acquainted with moral hacking involves digging into the mind and procedures of the programmers and in this way figuring out how to infiltrate into the frameworks through distinguishing and assessing weaknesses in the product and PC organizations. Seeking after moral hacking can increase the value of an association, whenever rehearsed and practiced productively and accurately.
Advantages Of Ethical hacking :-
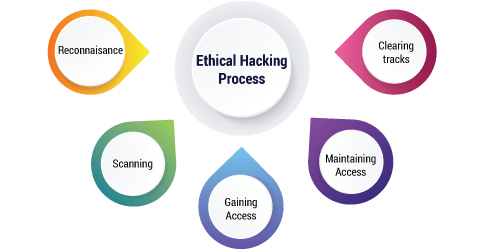
Ethical hacking process :-
Reconnaissance – It is the chief stage where the Hacker endeavors to assemble information about the target. It fuses Identifying the Target, finding the genuine’s IP Address Range, DNS records, Network, etc.
Scanning – In this stage, the programmer starts to successfully test a genuine machine or association for shortcomings that can be manhandled. It fuses the use of mechanical assemblies like dialers, network mappers, sweepers, port scanners, and shortcoming scanners to really take a look at data.
Gaining Access – In this stage, the programmer designs the diagram of the association of the goal with the help of data accumulated during perception and checking. The programmer has finished with distinguishing and checking the association and presently reasons that they have a couple of choices to get to the association.
Maintaining Access – It is the connection where the programmer has viably gotten entrance into a structure. By gaining admittance, the programmer acquaints a couple of optional entries with go into the system when he wants access in this had structure later on. Metasploit is the leaned toward contraption in this cycle.
Clearing Tracks – This interaction is essentially a deceptive action. It has to do with the eradication of logs of the large number of activities that happen during the hacking connection.
Reporting – It is the last advance of completing the moral hacking process. In this the Ethical Hacker totals a report with his revelations and the work that was done, for instance, the instruments used, shortcomings found, the accomplishment rate, and the undertaking measures.
What are Hacking Tools?
Hacking Tools are PC projects and scripts that help you find and take advantage of shortcomings in PC frameworks, web applications, servers and organizations. There are an assortment of such apparatuses accessible on the lookout. Clients can without much of a stretch download hack devices for moral hacking. Some of them are open source while others are business arrangement.
Following is a handpicked rundown of Top 20 Best Ethical Hacking Tools, with their famous Features and site connects to download hack devices. The hacking gadgets list contains top hacking devices both open source(free) and commercial(paid).
- Dead exact weakness identification with the special Proof-Based Scanning Technology.
- Negligible design required. Scanner consequently recognizes URL revise rules, custom 404 mistake pages.
- REST API for consistent reconciliation with the SDLC, bug global positioning frameworks and so forth
- Completely versatile arrangement. Check 1,000 web applications in only 24 hours.
1. Netsparker :
Netsparker is a simple to utilize web application security scanner that can naturally observe SQL Injection, XSS and different weaknesses in your web applications and web administrations. It is accessible as on-premises and SAAS arrangement.
Features :
- Filters for all variations of SQL Injection, XSS, and 4500+ extra weaknesses
- Distinguishes more than 1200 WordPress center, subject, and module weaknesses
- Quick and Scalable – creeps a huge number of pages without interferences
- Incorporates with famous WAFs and Issue Trackers to support the SDLC
- Accessible On Premises and as a Cloud arrangement.
2. Acunetix :
Acunetix is a completely robotized moral hacking arrangement that mirrors a programmer to keep one stride in front of noxious gatecrashers. The web application security scanner precisely checks HTML5, JavaScript and Single-page applications. It can review complicated, validated webapps and issues consistence and the board provides details regarding a wide scope of web and organization weaknesses.
Features :
- This network security programming has inbuilt respectability observing.
- This is one of the most incredible SIEM devices which assists you with dealing with your memory stick stockpiling
- It has an instinctive UI and dashboard.
- SolarWinds contains incorporated consistence detailing apparatuses.
- It has a unified log assortment.
- The apparatus can find and react to dangers quicker.
3. SolarWinds Security Event Manager:
SolarWinds Security Event Manager is an apparatus that assists you with further developing your PC security. This application can consequently distinguish dangers, screen security approaches, and ensure your organization. SolarWinds permit you to monitor your log documents effortlessly and get moment alarms if anything dubious occurs.
Features :
- It offers both TCP and ICMP network way examination.
- This application can make a txt logfile.
- Upholds both IP4 and IPV6.
- Recognize way changes and give you a warning.
- Permits constant testing of an organization.
4. Traceroute NG
Traceroute NG is application that empowers you to examine network way. This product can recognize IP addresses, hostnames, and parcel misfortune. It gives precise examination through order line interface
Features :
- It is one of the most outstanding hacking instruments that can recognize more than 3000 web application weaknesses.
- Check open-source programming and specially fabricated applications
- A simple to utilize Login Sequence Recorder permits the programmed filtering
- Audit weakness information with worked in weakness the board.
- Effectively give wide assortment of specialized and consistence reports
- Identifies Critical Vulnerabilities with 100 percent Accuracy
- Robotized creep and output
- It is probably the best programmer instruments which gives progressed examining component to manual analyzers
- State of the art examining rationale
5. Burp Suite:
Burp Suite is a valuable stage for performing Security Testing of web applications. Its different programmer devices work consistently together to help the whole pen testing process. It ranges from introductory planning to investigation of an application’s assault surface.
Features :
- It is one of the most mind-blowing programmer apparatuses that upholds dynamic and detached analyzation of numerous conventions
- Component of ARP harming to sniff on an exchanged LAN between two hosts
- Characters can be infused into a server or to a customer while keeping a live association
- Ettercap is fit for sniffing a SSH association in full duplex
- It is perhaps the best programmer devices that permits sniffing of HTTP SSL got information in any event, when the association is made utilizing intermediary
- Permits making of custom modules utilizing Ettercap’s API
6. Ettercap:
Ettercap is a moral hacking apparatus. It upholds dynamic and uninvolved analyzation incorporates Features for organization and host investigation.
Features :
- More cards/drivers upheld
- Support a wide range of OS and stages
- New WEP assault: PTW
- Support for WEP word reference assault
- Support for Fragmentation assault
- Further developed following velocity
7. Aircrack:
Aircrack is truly outstanding, trustable, moral hacking apparatuses on the lookout. It breaks weak remote associations. This hacking machine instrument is controlled by WEP WPA and WPA 2 encryption Keys.
Features :

- This organization hacking device examines nearby organizations just as the Internet
- Free and open-source hack device
- Irregular or document in any arrangement
- Trades results into many organizations
- Extensible with numerous information fetchers
- Gives order line interface
- This hacking programming deals with Windows, Mac, and Linux
- No requirement for Installation
8. Furious IP Scanner:
Furious IP Scanner is open-source and cross-stage moral hacking instrument. It filters IP locations and ports.
Features :
- Strong, simple to-utilize network legal sciences programming
- LiveAction mechanizes the catch of the organization information needed to rapidly explore security alarms
- Programming and incorporated apparatus arrangements
- Bundle insight joins profound investigation
- This organization hacking apparatus gives quick goal of organization and security issues
- Simple to utilize Intuitive work process
- Master and responsive specialized help
- On location organization for machines
- Obligation to our clients and our items
9. LiveAction:
It is one of the most mind-blowing hacking apparatuses for moral hacking. It execution issues and lessens security hazard with the profound perceivability given by Omnipeek. It is one of the most mind-blowing hacking applications that can analyze network gives quicker and better with LiveAction parcel insight.
Features :
- It is one of the most amazing internet hacking devices which is trusted all around the world
- No equipment to purchase or make due
- This hack framework programming is a versatile, start to finish answer for all parts of IT security
- Weakness information safely put away and handled on a n-layered design of burden adjusted servers
- It sensor gives persistent perceivability
- Information dissected progressively
- It can react to dangers in a continuous
10. QualysGuard:
Qualys monitor assists organizations with smoothing out their security and consistence arrangements. It additionally incorporates security into their advanced change drives. It is one of the most amazing programmer apparatuses that actually looks at the presentation weakness of the internet based cloud frameworks.
Features :
- Permits to test dynamic conduct of running web applications to recognize security weaknesses
- Keep in charge of your output by getting applicable data and insights initially
- Incorporated Program Management
- Trend setting innovations, like concurrent slither proficient level testing to fledgling security analyzers
- Effectively illuminate the board on weakness moving, consistence the executives, and hazard oversight
11. WebInspect:
WebInspect is robotized dynamic application security testing that permits performing moral hacking strategies. It is one of the most incredible hacking instruments which gives extensive unique examination of intricate web applications and administrations.
Features :
- Open-Source stage
- Multi-Platform Support
- This hacking programming permits using numerous gadgets in a similar framework
- Using blended gadget types in a similar framework
- It upholds dispersed breaking organizations
- Upholds intuitive respite/continue
- Upholds meetings and reestablish
- Underlying benchmarking framework
- Incorporated warm guard dog
- Upholds programmed execution tuning
12. Hashcat:
Hashcat is one of the most outstanding strong secret phrase breaking and moral programmer devices. It is one of the most outstanding programmer programs which can assist clients with recuperating lost passwords, review secret word security, or simply discover what information is put away in a hash.
Features :
- Multicore and multi-GPU support assists with improving equipment
- Simple to modify
- Basic Password Loading
- Plan refined assignments for computerized undertaking wide secret word
- Fix powerless passwords issues by compelling secret phrase resets or locking accounts
- It permits numerous reviewing OSes
13. L0phtCrack:
L0phtCrack 6 is helpful secret phrase review and recuperation instrument. It recognizes and surveys secret phrase weakness over nearby machines and organizations.
Features :
- Full time-memory compromise apparatus suites, including rainbow table age
- It Support rainbow table of any hash calculation
- Support rainbow table of any charset
- Support rainbow table in crude document design (.rt) and minimized record design
- Calculation on multi-center processor support
- GPU speed increase with various GPUs
- Runs on Windows OS and Linux
- Brought together rainbow table record design on each upheld OS
- Order line UI
- Illustrations UI
14. Rainbow Crack:
RainbowCrack is a secret phrase breaking and moral hacking device generally utilized for hacking gadgets. It breaks hashes with rainbow tables. It utilizes time-memory tradeoff calculation for this reason.
Features :
- IKECrack is a device that permits performing Cryptography errands
- Starting customer sends encryption choices proposition, DH public key, irregular number, and an ID in a decoded parcel to the passage/responder
- It is one of the most outstanding hacking programs uninhibitedly accessible for both individual and business use. In this way, it is ideal decision for client who needs a possibility for Cryptography programs
15. IKECrack:
IKECrack is an open source verification break apparatus. This moral hacking apparatus is intended to savage power or word reference assault. It is one of the most incredible programmer instruments that permits performing cryptography assignments.
Features :
- GUI based and extremely simple to utilize
- It has strong and viable filtering motor
- Upholds for recording Login grouping
- Detailing in both HTML and RTF designs
- It is one of the most mind-blowing hacking programs that checks for north of 25 kinds of web weaknesses
- Bogus Positives and Negatives discovery support
- It upholds Python and Ruby
- Extensible utilizing modules or modules in Python, Ruby, C# or VB.NET
16. Sboxr:
Sboxr is an open source hacking programming. It is web application weakness testing. It is one of the most outstanding hacking sites intended to be adjustable with the goal that clients can make their custom security scanners utilizing it.
Features :
- It is planned so that it is fast, hugely equal, particular, login savage forcer
- The primary point of this programmer programming is to help as many administrations which permit distant confirmation
- It is one of the most outstanding internet hacking devices that permits to perform Thread-based equal testing and Brute-power testing
- Adaptable client input. It very well may be indicated in an assortment of ways
- All the assistance module exists as an autonomous .mod document.
- No alterations are expected to the center application to expand the upheld rundown of administrations for beast compelling
17. Medusa :
Medusa is one of the most outstanding web-based animal power, rapid, equal secret key saltines moral hacking instrument. This hacking tool compartment is likewise broadly utilized for moral hacking.
Features :

Conclusion :-
With the increment in innovation, a large portion of the business lean towards moral hacking to protect their organizations with the assistance of Ethical Hacking apparatuses. The above-recorded apparatuses are the best 10 moral hacking instruments to search for in future. On the off chance that you wish to turn into a moral programmer and fabricate a promising vocation in online protection, check our Cyber Security Course presented by Sandford Universities.






