
Network troubleshooting involves diagnosing and resolving issues within a computer network to ensure smooth and efficient operation. It encompasses identifying problems related to connectivity, performance, security, and reliability. This process typically involves analyzing network logs, using diagnostic tools, testing connectivity, and implementing solutions to address identified issues.
1. What constitutes a network?
Ans:
A network comprises interconnected devices or nodes capable of communication and resource sharing. These devices can range from computers to servers, routers, and switches, forming systems that transmit data locally or across vast distances. Effective networking protocols ensure the smooth exchange of information and the reliability of connections within the network.
2. What are the details of the OSI model and its various layers?
Ans:
- The Physical Layer manages the physical connections.
- The Data Link Layer facilitates node-to-node communication and error handling.
- The Network Layer oversees data packet routing.
- The Transport Layer ensures end-to-end communication.
- The Session Layer, orchestrating application sessions.
- The Presentation Layer handles data translation.
- The Application Layer provides network services to applications.
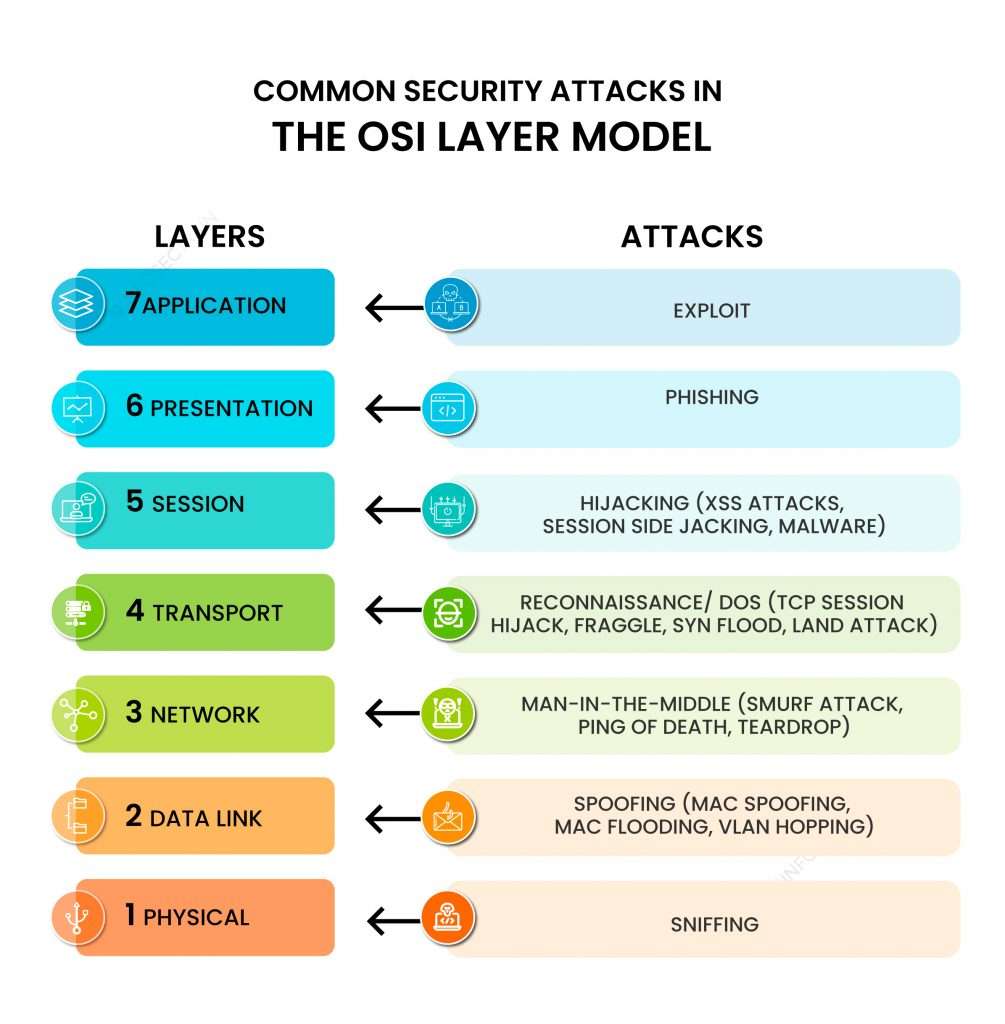
3. What is the significance of TCP/IP in networking?
Ans:
TCP/IP (Transmission Control Protocol/Internet Protocol) represents a suite of protocols governing data transmission across the Internet and various computer networks. This suite encompasses protocols such as TCP, IP, UDP, ICMP, and others, managing addressing, routing, and reliable data delivery. Its widespread adoption is fundamental to the functioning of the Internet, enabling diverse devices to communicate seamlessly.
4. What are the distinctions between LAN, WAN, and MAN?
Ans:
LANs (Local Area Networks) cover limited geographical areas, often confined to a building or campus. WANs (Wide Area Networks) span vast distances, interconnecting LANs across cities or continents. MANs (Metropolitan Area Networks) bridge the gap between LANs and WANs, serving larger areas like cities or metropolitan regions. Each type of network serves different connectivity needs, impacting performance, speed, and cost.
5. Define an IP address and explain the differences between IPv4 and IPv6.
Ans:
| Aspect | IPv4 | IPv6 |
|---|---|---|
| Address Format | 32-bit address in dotted-decimal notation (e.g., 192.0.2.1) | 128-bit address in hexadecimal notation (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) |
| Address Space | Limited address space (4.3 billion addresses) | Vastly expanded address space (340 undecillion addresses) |
| Header Length | Fixed 20-byte header | Variable-length header (minimum 40 bytes) |
| Address Configuration | Typically uses DHCP for address assignment | Supports stateless address autoconfiguration (SLAAC) and DHCPv6 for address assignment |
6. What is the role of a subnet mask in networking?
Ans:
A subnet mask segments an IP address into network and host sections, dictating which part identifies the network and which part identifies the device. Through this segmentation, devices ascertain whether another device resides on the same local network or a distinct one. This helps optimize network performance and enhances security by managing traffic effectively.
7. What function does a gateway serve in a network?
Ans:
A gateway acts as an entry and exit point for a network and connects it to other networks or the Internet. It functions as a conduit between disparate networks, facilitating data packet routing and enabling communication. By translating protocols and addressing schemes, a gateway ensures seamless interoperability among different network architectures.
8. What is the purpose of DNS and what role does it play in networking?
Ans:
- DNS (Domain Name System) translates human-readable domain names (e.g., www.example.com) into numerical IP addresses, enabling computers to identify one another on the network.
- This decentralized directory service maps domain names to IP addresses for seamless network communication.
9. What is DHCP and how does it operate?
Ans:
DHCP (Dynamic Host Configuration Protocol) automates the assignment of IP addresses and network configurations to devices on a network. DHCP streamlines network setup and management by eliminating manual configuration, particularly in large-scale deployments. This automation enhances efficiency and reduces the risk of IP address conflicts among devices.
10. What are the differences in functionality between a switch and a router?
Ans:
- A switch, operating at the OSI model’s data link layer (Layer 2), links devices within a LAN.
- It forwards data packets solely to the intended recipient based on MAC addresses. Conversely, a router, functioning at the network layer (Layer 3), connects multiple networks.
- It routes data packets between networks using IP addresses and makes routing decisions based on routing tables.
11. What is ARP, and how does it function?
Ans:
- ARP (Address Resolution Protocol) facilitates translating IP addresses to MAC (Media Access Control) addresses within a local network.
- When a device seeks to communicate with another on the same network, it sends an ARP request containing the target device’s IP address.
- The device with the corresponding IP address responds with its MAC address, enabling communication.
12. Describe the significance of a firewall in network security.
Ans:
A firewall is a network security mechanism that oversees and regulates both incoming and outgoing network traffic based on predefined security parameters. It acts as a barrier separating a trusted internal network from external, untrusted networks like the Internet. Filtering traffic thwarts unauthorized access attempts, malicious attacks, and data breaches.
13. What are VLANs, and why are they implemented?
Ans:
- VLANs (Virtual Local Area Networks) represent logical groupings of devices within a broader physical network.
- VLANs are configured to communicate as if they were part of the same physical network, regardless of their actual physical location. They bolster network performance, security, and management.
- They achieve this by segmenting traffic, controlling broadcast domains, and enforcing security protocols.
14. What is the role of a proxy server in network operations?
Ans:
A proxy server serves as an intermediary between clients and servers, directing client requests to the appropriate server and returning the server’s response to the client. Its applications include caching frequently accessed content, filtering web traffic, optimizing performance, and safeguarding privacy by concealing the client’s IP address. Additionally, it can enhance security by monitoring and controlling access to the network.
15. Define NAT and elucidate its role in network communication.
Ans:
- NAT (Network Address Translation) modifies packets’ source or destination IP addresses as they traverse a router or firewall.
- This enables devices within a local network with private IP addresses to communicate with internet devices using a single public IP address.
- NAT plays a pivotal role in conserving public IP addresses and fortifying network security by concealing internal network structures.
16. What is the concept of port forwarding?
Ans:
Port forwarding entails redirecting incoming network traffic from one IP address and port number combination to another. Frequently employed in network configurations, it permits external access to specific services or devices on a private network by mapping external ports to internal IP addresses and ports. This process is essential for enabling remote access to applications like gaming servers and web services hosted on local networks.
17. What is the role of a load balancer in enhancing network performance?
Ans:
A load balancer disperses incoming network traffic across multiple servers or resources to optimize resource utilization, enhance responsiveness, and fortify fault tolerance. By distributing the workload evenly, a load balancer prevents any single server from becoming overwhelmed, elevating overall network performance and reliability. Additionally, it can provide redundancy, ensuring uninterrupted service even if one or more servers fail.
18. What is a VPN and how does it operate?
Ans:
- VPN (Virtual Private Network) extends a private network across a public network like the Internet, enabling users to securely access and transmit data as if directly connected to the private network.
- VPNs encrypt data traffic to ensure confidentiality and integrity while obfuscating the user’s IP address for enhanced privacy.
19. What is the Difference between IDS and IPS in network security.
Ans:
IDS (Intrusion Detection System) scrutinizes network traffic for signs of suspicious activity or security breaches, generating alerts upon detecting potential threats. On the other hand, IPS (Intrusion Prevention System) actively intervenes by blocking or mitigating detected threats in real time, furnishing proactive protection against malicious activities.
20. What is the distinction between half-duplex and full-duplex communication?
Ans:
- In half-duplex communication, data transmission transpires in both directions but not simultaneously.
- Devices take turns transmitting and receiving data, resulting in slower communication rates.
- Conversely, full-duplex communication permits simultaneous data transmission in both directions, facilitating swifter and more efficient communication between devices.
21. What is the essence of network troubleshooting and why is it significant?
Ans:
Network troubleshooting involves systematically identifying, diagnosing, and resolving issues impacting a computer network’s performance, connectivity, or security. It’s akin to detective work, aiming to uncover the root cause of network problems and restore smooth operations while minimizing downtime and optimizing performance to support organizational goals.
22. What is the step-by-step process involved in troubleshooting network issues?
Ans:
- Problem Identification: Gather information about symptoms like connectivity issues or slow performance.
- Data Collection: Collect data on network configurations, recent changes, and affected devices or services.
- Analysis: Utilize diagnostic tools to pinpoint potential causes of the issue.
- Hypothesis Formulation: Develop educated guesses about the root cause based on available information.
- Testing: Conduct experiments to validate or refute the hypothesis.
- Solution Implementation: Apply fixes or workarounds to address the identified problem.
- Verification: Confirm that the implemented solution effectively resolves the issue.
23. How do you determine the scope of a network problem?
Ans:
Determining the scope of a network problem involves:
- Assessing its impact on network functionality.
- Identifying affected devices or services.
- Understanding its implications for users and business operations.
- This helps effectively prioritize troubleshooting efforts and resource allocation.
24. What tools are utilized for network troubleshooting?
Ans:
- Ping and traceroute for connectivity testing and diagnosing network path issues.
- Network monitoring tools for real-time performance monitoring and anomaly detection.
- Packet sniffers are used to capture and analyze network traffic patterns.
- Configuration management tools for tracking device configurations and changes.
25. What is your approach to gathering information for diagnosing network problems?
Ans:
Interviewing users or stakeholders to understand symptoms and recent changes. Reviewing network documentation, including diagrams and configurations. Utilizing network monitoring tools to collect data on performance and traffic patterns. Conducting tests like ping tests and packet captures to gather diagnostic information. This comprehensive method ensures that all relevant data is considered for effective troubleshooting.
26. What is the importance of documentation in network troubleshooting?
Ans:
- Record network configurations, changes, and troubleshooting procedures for future reference.
- Provide a historical record of network issues, resolutions, and lessons learned.
- Facilitate knowledge sharing and collaboration among team members.
- Ensure consistency and accuracy in network management and troubleshooting efforts.
27. What criteria do you use to prioritize network issues for resolution?
Ans:
- Impact on business operations and critical services.
- The severity and potential risks associated with the problem.
- Resource availability, including personnel, time, and equipment.
- Dependencies and interrelationships with other network components or services.
28. What is the necessity of testing after implementing a solution?
Ans:
- Verify that the solution effectively resolves the identified problem.
- Ensure the solution only introduces new issues.
- Validate the stability and reliability of the network after changes.
- Confirm the problem doesn’t recur under normal conditions.
29. Identify some prevalent causes of network congestion.
Ans:
- Bandwidth limitations or oversubscription.
- Network infrastructure bottlenecks, such as overloaded switches.
- Misconfigured or inefficient network protocols.
- Security threats like DDoS attacks.
- Heavy traffic from applications or multimedia streaming.
30. What strategies do you employ to address sluggish network performance?
Ans:
Optimizing network configurations and traffic management. Upgrading hardware like routers or switches. Implementing Quality of Service mechanisms. Analyzing and mitigating sources of congestion. Regular monitoring and tuning of performance parameters. Utilizing caching or content delivery networks to reduce bandwidth consumption.
31. What are the common reasons behind network downtime?
Ans:
- Hardware failures, such as malfunctioning routers or switches.
- Software issues, like bugs or misconfigurations in network devices.
- Network congestion or limitations in bandwidth.
- Power outages or electrical disturbances.
- Human errors, such as accidental configuration changes.
- Security breaches or cyber-attacks.
32. What strategies do you use to mitigate issues related to packet loss?
Ans:
Analyze network traffic patterns to pinpoint congested areas. Adjust network configurations to minimize packet loss, such as refining Quality of Service (QoS) parameters. Upgrade network hardware, like routers or switches, to handle increased traffic. Deploy error detection and correction mechanisms, such as Forward Error Correction (FEC). Regularly monitor network performance and promptly resolve any issues leading to packet loss.
33. What could be the underlying causes of intermittent network connectivity problems?
Ans:
- Wireless interference from nearby networks or electronic devices.
- Signal attenuation or limitations in wireless coverage.
- Malfunctioning network cables or connectors.
- Conflicts in software or compatibility issues.
- Overheating or hardware deterioration in network devices.
34. How do you troubleshoot DNS resolution issues?
Ans:
- Confirm the availability and responsiveness of DNS servers.
- Validate DNS server configurations and settings.
- Test DNS resolution using tools like nslookup or dig.
- Investigate potential forwarding or caching problems in DNS.
- Explore network connectivity issues affecting DNS resolution.
- Examine DNS logs for anomalies or error messages.
35. What is your methodology for diagnosing DHCP-related problems?
Ans:
Verifying the operational status and responsiveness of DHCP servers. Reviewing DHCP server settings, such as IP address pools and lease durations. Testing the allocation and renewal of DHCP leases. Addressing network connectivity problems that affect DHCP communication. Scrutinizing DHCP server logs for indications of problems. Investigating DHCP client configurations and preferences. Assessing DHCP relay setup if DHCP requests traverse multiple network segments. Resolving conflicts in IP addresses or issues stemming from lease exhaustion.
36. What steps would you take to resolve IP address conflict issues?
Ans:
Identify conflicting IP addresses through tools like ARP tables or DHCP server logs. Manually assign distinct IP addresses to affected devices. Adjust DHCP server configurations to minimize IP address conflicts. Review network device settings to ensure proper IP address assignments. Employ IP address management (IPAM) solutions to monitor and regulate IP address allocations.
37. What are the potential causes of network loops and how can they be prevented?
Ans:
Misconfigurations or failures in Spanning Tree Protocol (STP). VLAN setup errors leading to broadcast storms. Problems in duplex settings between network devices. Accidental creation of physical loops due to improper cable connections. Instances of multicast or broadcast storms overwhelm network resources. Software glitches or bugs in network devices. Inadequate practices for network monitoring and management.
38. What is your approach to troubleshooting wireless network issues?
Ans:
- Assessing wireless signal strength and coverage areas. Identifying sources of interference, such as neighbouring wireless networks or electronic equipment.
- Reviewing configurations of wireless access points, including channel assignments and transmit power levels.
- Updating firmware and drivers for wireless devices. Conducting surveys of the site to evaluate wireless network performance and coverage.
39. What are the typical symptoms that indicate failing network hardware?
Ans:
- Increased frequency of network downtimes or outages.
- Reduced network performance or data transfer rates.
- Instances of packet loss or heightened latency.
- Intermittent connectivity problems.
- Alerts or notifications are signalling hardware issues.
- Unexpected system shutdowns or restarts.
40. How do you go about troubleshooting network cable issues?
Ans:
Physically examine cables for signs of damage, wear, or improper termination. Use a cable tester or multimeter to check cable continuity. Ensure cables are correctly connected and seated. Verify cable specifications and compatibility with network devices. Network diagnostic tools like Time Domain Reflectometer (TDR) are employed to test cable performance. Replace defective cables or connectors with new ones.
41. Outline your process for diagnosing problems with network switches.
Ans:
When diagnosing network switch issues, I follow a structured process:
- I physically inspect the switch, checking for any visible damage or abnormalities.
- I review switch logs for error messages or warnings and, if necessary, update the switch’s firmware to address known issues.
- I perform hardware diagnostics to identify any faults, and if required, I replace the switch or reroute traffic to minimize downtime.
42. What steps do you take to assess the functionality of a network adapter?
Ans:
- Assessing the functionality of a network adapter involves several steps:
- I check the Device Manager for any error codes or warnings related to the adapter.
- I physically inspect the adapter for signs of damage or wear. Then, I connect it to a known working network and test its connectivity.
- I ensure the adapter has the latest drivers installed and verify the LED indicators’ link status.
43. What indicators suggest a failing router, and what troubleshooting methods can be used?
Ans:
- Indicators of a failing router include intermittent connectivity issues, slow performance, frequent downtime, hardware errors, and overheating. Troubleshooting methods include:
- Updating the router’s firmware.
- Checking for hardware faults such as faulty components.
- Monitoring network traffic for anomalies.
- Examining router logs for error messages.
44. What methods do you use to determine if a network interface card (NIC) is malfunctioning?
Ans:
To determine if a network interface card (NIC) is malfunctioning, I check the Device Manager for any error codes or warnings associated with the NIC. I then conduct a physical inspection of the NIC to look for any visible signs of damage or wear. Next, I connect the NIC to a known working network and test its connectivity. Additionally, I ensure that the NIC has the latest drivers installed and verify the link status LED indicators. If issues persist, I may perform a loopback test to diagnose the problem further.
45. What are the common causes of TCP/IP configuration errors?
Ans:
- Incorrect IP addressing.
- Subnet mask discrepancies.
- Default gateway misconfiguration.
- DNS server problems.
- IP address conflicts.
- DHCP server complications.
- Firewall interference.
46. What steps do you take to address IP address conflict issues?
Ans:
Addressing IP address conflict involves identifying devices with conflicting IP addresses using tools like ARP tables or DHCP server logs. I manually assign unique IP addresses to affected devices to resolve disputes and adjust DHCP server settings to prevent future conflicts. Additionally, I may conduct a network audit to identify and rectify misconfigurations contributing to IP address conflicts.
47. What steps do you take to rectify issues with incorrect subnet masks?
Ans:
To rectify problems with incorrect subnet masks, I verify the subnet mask configuration on the affected devices and correct any inaccuracies. I ensure the subnet mask matches the network topology and IP addressing scheme. Additionally, I review DHCP server settings to ensure they are correctly configured to assign the correct subnet mask to client devices.
48. What troubleshooting methods can be used to resolve incorrect DNS settings?
Ans:
Troubleshooting methods for resolving incorrect DNS settings involve several steps. First, I verify the DNS server settings configured on the device to ensure they are accurate. Next, I use tools like nslookup or dig to test DNS resolution and identify errors or misconfigurations. I review router or DHCP server configurations if needed to ensure they correctly assign DNS server addresses to client devices.
49. What approach do you take to investigate issues stemming from an incorrect default gateway?
Ans:
- Investigating issues stemming from an incorrect default gateway involves several steps.
- First, I check the default gateway configuration on the affected device to confirm the incorrect setting.
- I then correct the default gateway address to ensure proper routing and connectivity.
50. How do you diagnose problems related to DHCP lease renewals?
Ans:
- Diagnosing problems related to DHCP lease renewals involves several steps. First, I verify the DHCP server settings, including lease durations and pool sizes, to ensure they are configured correctly.
- Next, I monitor DHCP server logs for any errors or warnings related to lease renewals.
- I then check network connectivity and perform DHCP lease tests to confirm proper lease allocation and renewal processes.
- If needed, I may manually adjust DHCP server settings or renew leases to resolve any issues with DHCP lease renewals.
51. What are the common causes of duplicate IP addresses?
Ans:
Duplicate IP addresses commonly arise from various sources, including misconfigured DHCP servers, manual IP assignments overlapping with DHCP allocations, malfunctions in DHCP server operations, miscommunications among network administrators, and devices being moved or replaced without updating IP configurations.
52. What troubleshooting approaches can be used for incorrect VLAN configurations?
Ans:
- Troubleshooting incorrect VLAN configurations entails multiple steps.
- If issues persist, I examine VLAN tagging settings on network interfaces and policies for VLAN assignment.
- Finally, I utilize VLAN monitoring tools to detect traffic anomalies and misconfigurations.
53. Identify signs indicative of a network security breach.
Ans:
Signs of a network security breach encompass abnormal network traffic patterns, unauthorized access attempts, unexpected system behaviours or errors, alterations in the system or user account settings without authorization, unexplained data exfiltration, and alerts from intrusion detection systems or security monitoring tools.
54. Discuss troubleshooting methods for unauthorized access to the network.
Ans:
Troubleshooting methods for unauthorized network access involve reviewing access logs and audit trails to pinpoint the origin of unauthorized access attempts. Additionally, I bolster security with more robust authentication methods like two-factor authentication, update access control lists (ACLs) and firewall rules to restrict access, conduct security audits to uncover vulnerabilities, and educate users on security best practices.
55. What strategies do you use to mitigate the effects of a DDoS attack?
Ans:
Mitigating the impact of a DDoS attack entails deploying DDoS mitigation tools and services, such as specialized hardware appliances or cloud-based protection. Configuring network devices to filter and block malicious traffic, implementing rate limiting and traffic shaping policies, and collaborating with internet service providers (ISPs) to curb the attack at the network edge are crucial measures.
56. What steps do you take to address network issues related to malware or viruses?
Ans:
Strategies to combat malware or virus-related network issues encompass deployment and maintenance of up-to-date antivirus and antimalware software, implementation of network segmentation to contain infections, regular vulnerability assessments and patch management, user education on safe computing practices, and utilization of email filtering and web content filtering solutions to forestall malware infections.
57. What are the potential signs of a compromised firewall, and what actions should be taken?
Ans:
Signs indicating a compromised firewall include unexpected changes to firewall configurations, unauthorized access to firewall management interfaces, elevated network traffic originating from or directed to suspicious IP addresses, and alerts from intrusion detection systems (IDS) or security monitoring tools. Remedial actions may include auditing firewall configurations, reviewing access logs, and instituting additional security measures like stronger authentication and access controls.
58. What troubleshooting methods do you use for network intrusion detection systems (IDS)?
Ans:
Troubleshooting network intrusion detection systems (IDS) involves:
- Analyzing IDS alerts and event logs to identify potential security threats.
- Refining IDS rules and signatures to minimize false positives and enhance detection accuracy.
- Scrutinizing network traffic patterns and anomalies.
- Regularly testing and maintaining IDS sensors and monitoring systems.
59. What steps do you take to enhance network security post-security incident?
Ans:
- Reinforcing network security after security incidents entails conducting a thorough post-incident review and analysis to ascertain the incident’s root cause.
- Subsequently, security enhancements such as network segmentation, access controls, and encryption are implemented.
- It is imperative to update security policies and procedures, provide additional security training and awareness programs for employees, and regularly review and update security measures to counter emerging threats.
60. What factors contribute to wireless signal interference?
Ans:
Wireless signal interference stems from factors such as physical obstacles (e.g., walls, buildings, and structures), electromagnetic interference from electronic devices (e.g., microwaves, cordless phones, and Bluetooth devices), overlapping wireless networks on the same channel, environmental conditions (e.g., weather and humidity), and radio frequency interference from nearby sources (e.g., radio towers and power lines).
61. Describe your approach to troubleshooting poor wireless signal strength.
Ans:
I follow a systematic process when tackling poor wireless signal strength. Initially, I surveyed the physical surroundings to pinpoint potential sources of interference or obstructions. Then, I assess the positioning and setup of wireless access points (APs) to optimize coverage. Diagnostic tools aid in measuring signal strength and identifying dead zones. Furthermore, I verify firmware updates and fine-tune wireless configurations such as channels and transmission power.
62. What potential issues could arise with wireless network authentication?
Ans:
Wireless network authentication may encounter various challenges, including incorrect authentication settings, mismatched security protocols between client devices and access points, expired or invalid credentials, and authentication server issues. Troubleshooting entails validating authentication settings, ensuring compatibility between client devices and access points, confirming credential validity, and examining authentication server logs for anomalies.
63. What process do you follow to diagnose problems related to wireless network encryption?
Ans:
Identifying problems related to wireless network encryption involves:
- Confirming encryption settings (e.g., WPA2, AES) on both access points and client devices.
- Verifying passphrase accuracy.
- Checking for compatibility issues among devices.
64. What are the common causes of wireless network disconnections?
Ans:
Wireless network disconnections can stem from various factors, such as interference from other wireless devices or electronic equipment, signal attenuation due to distance or physical barriers, outdated firmware or drivers, and network congestion. Troubleshooting entails assessing signal strength and quality, adjusting antenna orientation, updating firmware and drivers, and optimizing network settings such as channel selection and transmission power.
65. What steps do you take to troubleshoot issues with wireless access points?
Ans:
Resolving issues with wireless access points involves several steps. Initially, I verified the power supply and network connectivity to the access point to ensure proper functioning. Then, I reviewed configuration settings, including SSID, security configurations, and channel selections. Subsequently, I analyzed client connectivity and signal strength using diagnostic tools and investigated any reported issues or error messages.
66. What steps do you take to address issues with remote access connections?
Ans:
- Addressing issues with remote access connections begins with verifying network connectivity and confirming the operational status of the remote access server.
- Next, I review client settings, including VPN configuration and network credentials.
- I inspect firewall and router configurations to ensure that VPN traffic is permitted and investigate any error messages or logs associated with connection attempts.
- If challenges persist, troubleshooting may involve examining network infrastructure, updating firmware, or seeking assistance from network administrators or service providers.
67. What troubleshooting methods can be used for VPN connectivity problems?
Ans:
Troubleshooting methods for VPN connectivity problems entail confirming VPN client settings, verifying network connectivity, and scrutinizing VPN server logs for error messages. Ensuring the correct configuration of VPN protocols and encryption settings and investigating potential firewall or routing obstacles blocking VPN traffic is essential. Diagnostic tests or packet captures may be performed to pinpoint the underlying cause of connectivity issues.
68. How do you resolve issues with VPN authentication?
Ans:
Addressing issues with VPN authentication involves:
- Validating user credentials.
- Ensuring compatibility between VPN client and server authentication methods.
- Checking for account lockouts or expired passwords.
- I review authentication server logs for discrepancies and investigate authentication settings or configurations for inconsistencies.
69. What steps do you take to address problems with VPN tunnel establishment?
Ans:
To resolve issues with VPN tunnel establishment, I verify VPN configurations on both client and server ends, ensuring alignment between VPN protocols and encryption settings. I examine network connectivity between endpoints and troubleshoot firewall and routing configurations to confirm VPN traffic allowance. Additionally, adjusting VPN settings or consulting network administrators or service providers may be necessary if issues persist.
70. What steps do you take to ensure that VPN encryption is functioning correctly?
Ans:
- Reviewing VPN policies.
- Updating firmware or software.
- Seeking guidance from security professionals to ensure compliance with encryption standards and best practices.
71. What factors contribute to poor VoIP call quality?
Ans:
Many factors can contribute to diminished VoIP call quality, encompassing insufficient network bandwidth, congestion, packet loss, jitter, latency, improper QoS configurations, codec discrepancies, router or firewall configurations, and inadequate hardware or infrastructure. Addressing these issues often involves optimizing the network setup and ensuring appropriate resource allocation.
72. What troubleshooting approaches can be used for dropped VoIP calls?
Ans:
Troubleshooting dropped VoIP calls involves a systematic approach. Initially, I evaluate network conditions to identify potential causes such as congestion, packet loss, or latency. Then, I scrutinize VoIP device setups and firmware updates for compatibility and stability. Furthermore, I analyze call logs and diagnostic tools to detect patterns or irregularities associated with dropped calls.
73. What methods do you use to diagnose delays in VoIP call transmission?
Ans:
- Diagnosing delays in VoIP call transmission necessitates analyzing network conditions, including latency, jitter, and packet loss.
- I utilize network monitoring tools to assess real-time performance metrics and identify anomalies. Moreover, I inspect call signalling and routing paths to locate potential bottlenecks or inefficiencies.
- If delays persist, prioritizing VoIP traffic, adjusting QoS settings, or optimizing network configurations can enhance call transmission.
74. What is your strategy for resolving echo or noise on VoIP calls?
Ans:
Resolving echo or noise on VoIP calls requires identifying and mitigating potential causes such as acoustic echo, network latency, electrical interference, or hardware malfunctions. I commence by verifying VoIP device configurations and ensuring proper network settings. Subsequently, I assess network conditions and conduct diagnostic tests to pinpoint sources of echo or noise.
75. What steps do you take to diagnose problems with VoIP hardware?
Ans:
In diagnosing VoIP hardware issues, I comprehensively assess device setups, firmware updates, and network connectivity. Physical connections, power sources, and hardware components are inspected for damage or malfunction indications. Additionally, diagnostic tools are utilized to evaluate device functionality and performance. If hardware issues are detected, repair or replacement of faulty components may be pursued to restore VoIP functionality.
76. What tools do you utilize for network monitoring and management?
Ans:
- Network monitoring and management are facilitated through various tools, including network monitoring software (e.g., Nagios, PRTG Network Monitor), packet sniffers (e.g., Wireshark), bandwidth analyzers, Syslog servers, and SNMP monitoring tools.
- These tools enable real-time monitoring of network performance, traffic analysis, device management, and troubleshooting of network issues.
77. How do you configure alerts for network performance issues?
Ans:
Configuring alerts for network performance issues entails setting thresholds for key performance metrics such as bandwidth utilization, latency, packet loss, and device availability. Monitoring tools are configured to trigger alerts upon surpassing predefined thresholds, indicating potential network issues. Alerts are dispatched via email, SMS, or SNMP traps to notify administrators of problems necessitating attention promptly.
78. What is your process for analyzing network traffic patterns?
Ans:
Analysis of network traffic patterns involves scrutinizing data flows, protocols, and communication patterns within the network. Network monitoring tools and packet analyzers capture and analyze network traffic, identifying trends, anomalies, and potential security threats. Historical traffic data analysis aids in pattern recognition and forecasting future network demands, facilitating proactive network management and optimization.
79. How do you ensure network compliance with industry standards and regulations?
Ans:
- Regular audits of network configurations, security policies, and access controls are conducted to ensure network compliance with industry standards and regulations.
- Industry-specific compliance requirements such as HIPAA, GDPR, or PCI DSS are reviewed, and necessary controls are implemented to attain compliance.
- This entails enforcing encryption protocols, access controls, logging, and monitoring measures to safeguard sensitive data and ensure regulatory adherence.
80. What metrics do you monitor to evaluate network health and performance?
Ans:
Metrics monitored to assess network health and performance encompass bandwidth utilization, latency, packet loss, jitter, device availability, error rates, and throughput. Additionally, network traffic patterns, application performance, and user experience are observed to evaluate overall network performance and identify areas for improvement. These metrics aid in proactive network management, troubleshooting, and capacity planning to sustain optimal network health and performance.
81. What is the significance of documentation in network troubleshooting, and what essential information should it contain?
Ans:
- Documentation is a cornerstone of network troubleshooting, offering a vital repository for network configurations, topologies, and historical changes.
- It ensures consistency and accuracy throughout troubleshooting endeavours, fosters knowledge sharing among team members, and expedites issue resolution by providing insights into past incidents.
- Network documentation encompasses crucial information such as network diagrams, device configurations, IP addressing schemes, VLAN configurations, routing protocols, security policies, and change management records.
82. What steps do you take to maintain the accuracy and currency of network documentation over time?
Ans:
Upholding the accuracy and relevance of network documentation demands regular updates and reviews. This entails promptly recording changes as they occur, maintaining an up-to-date record of network configurations, and revising documentation to mirror current network states. Automation tools and network management systems aid in capturing real-time network alterations, while routine audits and reviews uphold documentation precision over time.
83. What components should be included in a comprehensive network troubleshooting report?
Ans:
- A comprehensive network troubleshooting report should include a description of the issue, diagnostic steps taken, findings, identified root causes, remediation actions, and recommendations to prevent similar issues.
- Additionally, it may include timestamps, affected network components, severity classifications, and the issue’s impact on network operations.
84. What methods do you use to effectively convey network issues and their resolutions to stakeholders with varying levels of technical knowledge?
Ans:
Effectively communicating network issues and resolutions to stakeholders with varying technical expertise necessitates tailoring the communication to suit the audience. Detailed reports featuring technical specifications, diagrams, and logs may be appropriate for technical stakeholders. Conversely, simplified explanations, visual aids, and layman’s terms can help convey the essence of the issue and its resolution to non-technical stakeholders.
85. What is an example of a situation where thorough documentation significantly expedited the resolution of a network issue?
Ans:
- Thorough documentation significantly expedites issue resolution by furnishing a historical record of past incidents and troubleshooting actions.
- In one case, detailed documentation of network configurations helped quickly identify and rectify a misconfigured router interface
- This streamlined troubleshooting minimized downtime and promptly restored network connectivity.
86. What is the role of network segmentation in enhancing security and performance, and what is your approach to implementing it?
Ans:
Network segmentation bolsters security and performance by segmenting the network into distinct segments or VLANs, each governed by its security protocols and access controls. My strategy for implementing network segmentation entails conducting a comprehensive assessment of network requirements, devising segmented architectures tailored to security and performance prerequisites, implementing segmentation policies through VLANs or firewall rules, and continuously monitoring and refining segmentation configurations.
87. How do you troubleshoot challenges in virtualized network environments, particularly those utilizing SDN?
Ans:
Tackling troubleshooting challenges in virtualized network environments, particularly those employing SDN, requires a deep comprehension of virtualization technologies and controllers. My approach involves:
- Scrutinizing virtual network configurations.
- Monitoring SDN controller logs.
- Leveraging SDN-specific troubleshooting tools to identify and address issues.
88. When troubleshooting network issues in hybrid cloud environments, what obstacles may arise, and how do you overcome them?
Ans:
Troubleshooting network issues in hybrid cloud environments can face challenges like connectivity issues between on-premises and cloud resources, platform compatibility, and managing distributed architectures. Overcoming these requires comprehensive monitoring, cloud-specific tools, collaboration with service providers, and adherence to best practices.
89. What strategies do you use to manage the complexities of troubleshooting network issues that involve various vendor technologies and platforms?
Ans:
- Managing the complexities of troubleshooting network issues involving diverse vendor technologies and platforms necessitates a systematic approach.
- This involves researching vendor-specific documentation, utilizing support resources and forums, collaborating with vendor representatives, and maintaining a diverse skill set to navigate different technologies effectively.
- Additionally, standardizing troubleshooting procedures and documentation formats aids in streamlining the process.
90. What approaches have you used to tackle complex network issues that span diverse technologies and interconnected systems?
Ans:
Strategies employed to troubleshoot complex network issues spanning interconnected systems and diverse technologies encompass conducting meticulous root cause analyses, utilizing network diagnostic tools and protocols, implementing network traffic analysis, collaborating with cross-functional teams, and leveraging vendor support resources. Documenting troubleshooting steps and lessons learned also contributes to knowledge sharing and enhances future troubleshooting endeavours.






