
IBM DataPower® Gateway helps organizations meet the security and integration needs of a digital business in a single multi-channel gateway. It provides security, control, integration and optimized access to a full range of mobile, web, application programming interface (API), service-oriented architecture (SOA), B2B and cloud workloads.The new DataPower Gateway IDG X2 physical appliance delivers up to 2X the performance of IBM DataPower Gateway (IDG) with next generation hardware architecture. It also provides a flash drive with 2X higher capacity than IDG and 2X 10GbE network ports. IDG X2 accelerates application responsiveness and increases workload capacity, which is critical for higher performance and/or for running additional tenants with governance and a lower TCO.
1. What does IBM data power?
Ans:
IBM data power is the Service-oriented architecture tool, this helps organization to meet pre-built security and integrating digital business needs.This tool also helps to accelerate an XML and web service deployments in single platform.
2. What does uses of IBM data power?
Ans:
The following are important benefits of using the IBM data power :
- Enhances reliability of IMS transactions for an IMS commit mode.
- Supports the distributed caching with IBM data power to provide the improved response time and better application performances.
- Improve security intelligence and compliance by integrating with the QRadar security information and security management platform.
- Simple to use and secured B2B integration.
3. How does implement Dynamic routings in IBM data power?
Ans:
When using dynamic routing, you must update all URLs in an extended markup language (XML) file. An XSLT file should be used to process this. This will read the URL from XML files based on customised conditions and set the XSLT variable var: //service/routing-URL.
4. What does default log size in log targets? What happens that log size reached?
Ans:
The log size is set to 500 kilobytes by default. The system will upload the log file to the TP server when it reaches the maximum size. Assume that if the upload is successful, the system appliances will automatically delete the log file to free up space.
5. What does XML manager and why does need it?
Ans:
The XML manager is a basic network configuration system that aids in load balancing and allows access to remote servers.The following are the advantages :
- XML manager sometimes acts as XML parser to provide a threat and security.
- This also helps in implementing caching process.
- XML manager to configure user-agent.
6. Give three popular algorithms used for encryption process?
Ans:
Triple DES algorithm : This employs three distinct individual keys of 56 bits each.The total key length is approximately 168 bits, but experts may use the 112 bits to strengthen keysets.
RSA algorithm : this is the public key data encryption algorithm and is a standard for an encrypting data over the internet.
AES algorithm :this is extremely 128-bit key form algorithm.This algorithm also uses keys of 192 and 256 bits for the heavily used for encryption process.
7. How does gauge the strength of key, what does parameter used?
Ans:
The algorithm should be available to public, but the key values should be a confidential;- A Key size parameters.
- Performance and response time to perform an encryption and decryption process.
- Mathematical proofs used for the standardization and offers security.
8. What does different modes through which can connect to IBM datapower?
Ans:
There are the three different modes available to connect an IBM data power :
- GUI or graphical user interface : This helps user to make use of graphical user interface components. CLI, or command line integration, is used to generate command line arguments to perform encryption.
- XML management interface : This is available in form of XML files to perform a load balancing and encryption processes.
Q9. Why does XSLT used in IBM data power?
Ans:
- XSLT is the programming language and therefore gives an added flexibility and power when creating a PNX.
- When collaborating with several institutions, just one copy of the regulations is required. When there are variations between institutions, use if-else statements.
- Some normalization rules can be extremely long and complex.The power of XSLT allows for significant simplification of logic.
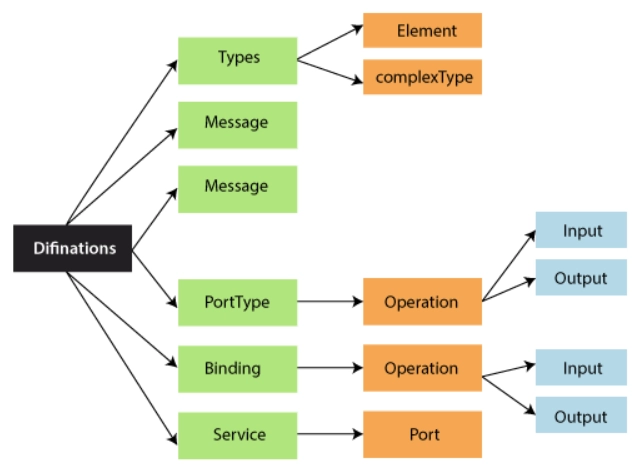
10.What does components of WSDL?
Ans:
- WSDL definitions
- WSDL port and operations
- WSDL types
- WSDL message
- WSDL binding.
11. What does roles and responsibilities of the IBM data power professional?
Ans:
- To gather requirements from a respected clients.
- Help to prepare design documentation.
- Present a design document to the client for approval task.
- Configure services in software development environment.
- Perform a testing and troubleshooting of data process services.
- Migrate data services from the development team to test and transmission to a production environment.
12)What does processing rule?
Ans:
Every data process service should have the certain type of policies and each policy should have a processing rules.
The important factors can be included are :
- Request a process rule to manage request messages.
- Response to process rule to handle or manage a request messages.
- Error rules are used to manage the error scenarios.
13. What does different services that have used in Data power?
Ans:
- Web service proxy
- Multiprotocol gateway
- XML firewall.
14. What does actions have used in the processing policy?
Ans:
AAA, SLM, match, transform, Result, Sign , Verify , Encrypt , Decrypt .
15. Why do you need a log target when the data power already has a default logging mechanism?
Ans:
Log target in a data power is used to capture important messages which are posted by the several objects and services that are running on application. One more important thing about log target is Users make use of this file to retrieve a specific objects or events, and also get a log information.16. What does trust store?
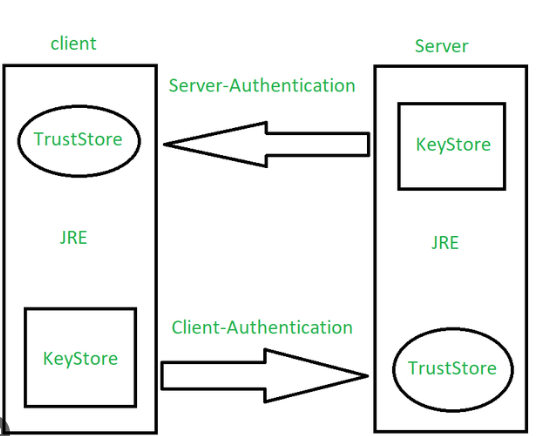
Ans:
A trust store contains a certificates from the other parties that can expect to communicate with, or from Certificate Authorities that trust to identify the other parties.
For example, Google (chrome) contains the certificates of many companies or websites. Whenever browse that site the browser automatically checks a site for its certificate from a store and compares it.
17. What does different modes of archival? Explain each mode ?
Ans:
Rotate : Rotate a log file when the maximum size is reached. The appliance creates the copy of the file and starts a new file.The appliance retains archived copies up to ta specified number of rotations.When both the log file size and the rotation count reach their maximum,the appliance removes the oldest file and duplicates the current one.
Upload : Upload a log file when the maximum size is reached.The appliance uploads file using the pecified the upload method.
18.What does cryptography? Why does need it?
Ans:
Cryptography is the science and practice of securing communication and information by encoding it in a way that only authorized parties can access and understand the data, while preventing unauthorized access or tampering. It implicates the use of mathematical algorithms and techniques to transform plaintext (the original data) into ciphertext (the encrypted data) and vice versa.
19. What does weakness of symmetric key cryptography ?
Ans:
- The biggest obstacle in successfully deploying the symmetric-key algorithm is necessity for a proper exchange of private keys. This transaction must be completed in the secure manner.
- If face-to-face meeting, which proves a quite impractical in many circumstances when taking the distance and time into account, cannot be possible to be exchange private keys.
- The exchange of keys becomes even more complex if one believes that security is compromised in the first place because of the need for a secret data exchange.
20) What is the advantage of Datapower over Message Broker?
Ans:
- Asymmetric keys must be many times longer than a keys in symmetric-cryptography in order to the boost security.
- While longer keys generated by other algorithms usually prevent brute force attacks from succeeding in any meaningful amount of time, these computations become more computationally intensive.
- >These longer keys can still vary in an effectiveness depending on computing power available to attacker.
21. What does difference between object type and object name?
Ans:
- Object Type, specify a type of object. This filter restricts log messages to only messages generated by a selected object.
- Whereas, Object name specifies a name of an existing object of selected type.
22) What does value timestamp format in log target for?
Ans:
Value Timestamp Format in the log target configuration specifies a format in which timestamps are recorded in the logs. DataPower allows to log various events and activities for monitoring, troubleshooting, and analysis purposes. Timestamps in logs are the crucial for understanding when specific events occurred, enabling administrators to correlate events and troubleshoot the issues effectively. Timestamp Format: Syslog
23. Why is a log target necessary when DataPower has a built-in default logging system?
Ans:
To record the messages posted by different appliance-running objects and services, a log target is required. Use the log targets to obtain the particular event or object log information.
24. Why does need a digital signature?
Ans:
Digital signatures act as the verifiable seal or signature to confirm the authenticity of sender and the integrity of the message. Users who wish to verify identity when sending the protected message can encrypt information with private key.
The recipient can then decrypt message with the sender’s public key in order to confirm sender’s identity and the integrity of message.
25. How can I receive email alerts for a specific log statement when an object’s status changes?
Ans:
It is done by setting up an Event triggers. Event triggers perform an actions only when triggered by a specified message ID or event code in this case the system goes up/down With this filter,it is possible to create the log target that collects only results of the specified trigger action.For example, to trigger generation of an error report when a certain event occurs use save error-report command and transfer to SMTP target format to send as email alert.
26.What does difference between object filter and event filter?
Ans:
- Object filters restrict the writing of log messages to a specific log target to only those log messages for a specific object. Object filters are based on the classes of objects.
- >With this filter, can create a log target that collects only log messages generated by a particular instances of specified object classes.
- Event Filter restricts the log messages that can be written to the log target to only those that have configured event codes. It is feasible to construct a log target that only gathers log messages for a given set of event codes using this filter.
27. What does IBM DataPower Gateway?
Ans:
IBM DataPower Gateway is the purpose-built security and integration platform for a mobile, cloud, application programming interface (API), web, and Business-to-Business (B2B) workloads.
28. Explain features of IBM DataPower Gateway?
Ans:
DataPower Gateway offers the features like an XML/JSON processing, security policies, traffic monitoring, protocol transformation, and service level monitoring.
29. What does difference between AAA policies and AAA actions in DataPower?
Ans:
AAA (Authentication, Authorization, and Accounting) policies define the conditions for access control, whereas the AAA actions specify what to do when conditions in the policy rule match.
30. What does Multi-Protocol Gateway in DataPower?
Ans:
The Multi-Protocol Gateway feature in the DataPower allows to expose services using the multiple protocols simultaneously, like HTTP, FTP, and MQ, while abstracting the complexities of protocols from a service consumers.
31). Explain XML Firewall in DataPower?
Ans:
XML Firewall in DataPower is used for a securing XML-based messages. It protects the against XML-specific attacks, enforces security policies, and performs a schema validation.
32.What does different types of processing policies in DataPower?
Ans:
DataPower supports the various processing policies like request, response, and error processing policies. Request policies handle the incoming messages, response policies handle the outgoing messages, and error policies handle errors that occur during the processing.
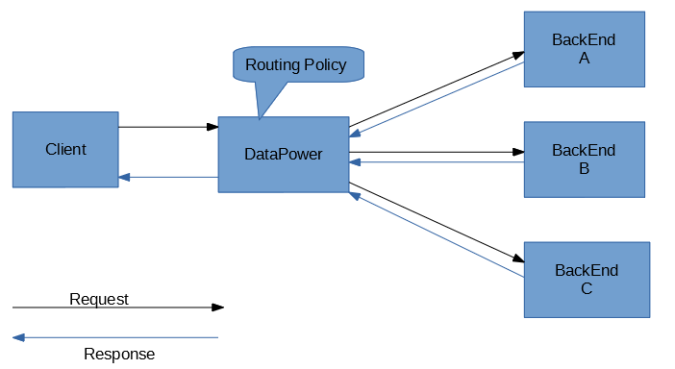
33. How does DataPower handle message routing and forwarding?
Ans:
DataPower uses the various routing protocols and policies to route and forward messages. For instance, it can use the rules based on content, headers, or protocols to determine the destination of the message.
34. What does role of DataPower in API management?
Ans:
DataPower plays the crucial role in API management by enforcing the security policies, handling the protocol conversions, rate limiting, logging, and monitoring, ensuring an APIs are secure, performant, and reliable.
35. Explain service level monitoring in DataPower?
Ans:
Service level monitoring in DataPower involves the tracking the performance and health of services. It monitors the various metrics such as response time, error rates, and throughput, allowing an administrators to ensure that services meet their defined a service level agreements (SLAs).
36. How does handle errors in DataPower processing policies?
Ans:
Errors in DataPower can be handled using an error processing policies. These policies define an actions to take when errors occur, such as logging the error, transforming it, or routing a message to a specific destination for the further analysis.
37. What does AAA in the context of DataPower?
Ans:
AAA stands for an Authentication, Authorization, and Accounting. In DataPower, AAA refers to policies and actions used to be control access to resources, authenticate users, authorize actions, and log user activities for an auditing purposes.
38.How is IBM DataPower deployed, and what distinguishes its deployment model from that of a Traditional Enterprise Service Bus (ESB)?
Ans:
| Feature | IBM DataPower | Traditional ESB | |
| Deployment Approach |
Appliance-based |
Software-based middleware. | |
| Hardware | Specialized hardware appliance | Runs on standard servers. | |
| Performance Optimization | Hardware acceleration | Generally relies on server capabilities. |
39. Explain DataPower in web service security.
Ans:
DataPower provides the various security features, including XML and non-XML threat protection, message encryption, and authentication. It can enforce the security policies, validate messages, and protect against the common web service security vulnerabilities.
40.How does DataPower handle message transformation and routing?
Ans:
DataPower uses the XSLT and other transformation languages for a message transformation. It supports the multiple routing protocols, such as HTTP, FTP, JMS, and MQ, allowing it to route messages to backend services based on the content, URL, or other criteria.
41. What does difference between Multi-Protocol Gateway (MPGW) and XML Firewall?
Ans:
MPGW is used for a routing, transformation, and bridging between the different protocols and services, while XML Firewall focuses on a securing and filtering messages based on the XML content, enforcing security policies.
42)How does DataPower handle load balancing?
Ans:
DataPower can distribute the incoming requests to backend servers based on the various load-balancing algorithms. It monitors the server health and can automatically route traffic to be healthy servers.
43. What does DataPower domains,and why does important?
Ans:
DataPower domains are the logical containers for managing configurations, services, and policies. They allow for a better organization and isolation of resources, making it simpler to manage and maintain a DataPower device.
44.Explain the difference between the DataPower firmware and DataPower appliances?
Ans:
- DataPower firmware refers toa software that runs on DataPower devices.
- DataPower appliances are physical hardware devices that can be run this firmware.
45. What does purpose of Crypto Objects in DataPower?
Ans:
Crypto Objects in the DataPower are used for encryption, decryption, and secure key management. They are essential for a securing messages and data transmitted through device.
46. What does difference between IBM DataPower and message broker?
Ans:
The IBM DataPower Gateway is the security and integration platform. WebSphere Message Broker from an IBM was an enterprise service bus (ESB) that has reached end of life and is no longer sold or be supported. WebSphere DataPower Gateway is really beneficial if trying to integrate a two or more systems.
47. What does DataPower tool?
Ans:
IBM DataPower is not just tool but a family of a pre-built, pre-configured hardware appliances designed to simplify, secure, and accelerate XML, Web Services, and API deployments while an extending a SOA infrastructure. These appliances are specifically tailored for the processing XML and non-XML data in service-oriented architecture (SOA) environments.
48. What does DataPower middleware?
Ans:
IBM DataPower is classified as middleware. Middleware is software that which serves an intermediary layer, allowing different software applications or components to communicate and exchange data. In case of DataPower, it serves as a specialized middleware solution designed to handle the various tasks related to data transformation, security, and integration within service-oriented architecture (SOA) or API-driven environment..
49. What does XML Firewall in DataPower?
Ans:
The XML Firewall processes the XML requests and responses over HTTP or HTTPS. The XML Firewall uses single protocol and contains a processing policy with the set of request, response, two-way, and error rules. Its configuration defines a listening host-port pairs and general threat protection.
50.What does Soma in DataPower?
Ans:
The XML Management Interface of DataPower appliance can be set up for different. endpoints: Appliance Management Protocol (AMP) SOAP Configuration Management (SOMA), and SOAP Configuration Management.
51. What does quiesce in DataPower?
Ans:
Locate Quiesce section. In Timeout field, enter a time to wait before the operation starts. Optional: In Delay field, enter a time to wait before the quiesce request is initiated. Click Quiesce.
52. What does SLM action in DataPower?
Ans:
An SLM action specifies a control procedure for transactions that exceed the threshold. As part of any control procedure, the action writes the event to the log for each transaction that exceeds the threshold. Defining an SLM schedule. An SLM schedule the specifies a time frame to enforce the policy.
53. What does failsafe mode in DataPower?
Ans:
Failsafe mode activates after an errors and provides the subset of diagnostic commands. The appliance activates limited forms of failsafe mode after a data router fails to start the number of times or when intrusion is detected.
54. What does access control list in DataPower?
Ans:
An access control list (ACL) is associated with the specific DataPower® service. An ACL grants access to a service to only addresses that are defined by allow clause. All the other addresses are denied access. A Candidate addresses are evaluated sequentially against every clause in the ACL.
55. What does SSL Offloading in DataPower?
Ans:
SSL Offloading refers to a process of terminating SSL/TLS encryption at DataPower appliance, allowing it to handle the decrypted traffic internally. This reduces computational load on a backend servers and enhances performance.
56. How does DataPower handle security in Web services?
Ans:
DataPower ensures a security in Web services through features are XML threat protection, authentication, authorization, encryption, and digital signatures. It acts as security gateway, filtering out a malicious content and securing communication channels.
57. How does DataPower handle message routing and transformation?
Ans:
DataPower uses the policies to define message processing logic. It can route the messages based on content, apply transformations using the XSLT or other formats, and enrich messages by adding or modifying a headers and payload content.
58. Explain Error Handling in DataPower?
Ans:
Error handling in DataPower is creating policies to deal with different kinds of errors that could happen while processing messages. Custom error messages, logging, and message redirection to specific error-handling services are examples of this.
59. What does WebSphere DataPower?
Ans:
The IBM WebSphere DataPower SOA Appliances are a line of network devices designed with ease of use and purpose that streamline, enhance security, and quicken the deployment of XML and Web Services while expanding SOA infrastructure. DataPower Appliances contain more specialized hardware components, including the ASIC-based IPS, custom encrypted RAID drives, and (optional) hardware security modules.
60. What does DataPower Probe?
Ans:
DataPower Probe is used for the monitoring and analyzing appliance performance and traffic. It provides the valuable insights into system usage, allowing an administrators to optimize configurations for a better efficiency.
61. How does troubleshoot issues in DataPower?
Ans:
Troubleshooting in a DataPower involves reviewing log files, utilizing probes, analyzing an error messages, and using WebGUI and CLI interfaces. It also includes the understanding traffic patterns and examining configuration settings for a potential issues.
62. What does optimizations have to implemented for performance improvement?
Ans:
Load balancing, caching, and optimizing an XSLT transformations. Mention techniques like a result tree fragments, memoization, and proper indexing for a databases.
63. Describe the complex integration problem faced and how does solved it using DataPower?
Ans:
Provide the detailed account of the problem, analysis, and specific DataPower features or configurations are used to resolve the issue. Emphasize a problem-solving skills and impact of the solution.
64. Explain differences between the DataPower MPGW and a Web Application Firewall (WAF)?
Ans:
A DataPower Multi-Protocol Gateway (MPGW) is used for a processing and routing messages between the different protocols, whereas a Web Application Firewall (WAF) is specifically designed for a securing web applications against various attacks. While DataPower can include a some security features, a WAF focuses exclusively on the web application security.
65. Describe the benefits of using DataPower with Docker?
Ans:
Containerizing DataPower with the Docker or managing it with Kubernetes can provide the benefits such as scalability, ease of deployment, version control, and resource management. Docker and Kubernetes help to streamline the deployment and orchestration of a DataPower instances in a containerized environment.
66. How does achieve high availability and load balancing with DataPower appliances?
Ans:
To achieve high availability and load balancing, multiple DataPower appliances can be deployed in a redundant configuration. Use a load balancer in front of these appliances to evenly distribute incoming traffic. DataPower can also use its own features for high availability, such as multi-node domains and clustering.
67. Explain DataPower crypto objects?
Ans:
Crypto objects in a DataPower are used for managing cryptographic keys and certificates. They facilitate securethe communication by providing encryption and decryption capabilities. Crypto objects can be used in the SSL profiles, cryptographic profiles, and the other DataPower configurations to secure data in transit. /p>
68. What does considerations when implementing a custom policies in DataPower?
Ans:
When implementing the custom policies in DataPower, consider a factors such as performance, reusability, and maintainability. Be mindful of the message sizes, memory usage, and complexity of custom logic. Leveraging reusable objects and coding the best practices can help manage custom policies effectively.
69. Explain DataPower integration with API management platforms?
Ans:
DataPower can be integrated with the API management platforms like IBM API Connect to provide the comprehensive API management and security. DataPower acts as gateway, handling security, transformation, and routing, while an API management platforms handle API creation, documentation, monitoring, and analytics.
70. How does optimize the performance of DataPower for high-throughput applications?
Ans:
Performance optimization in the DataPower involves the various techniques such as caching, load balancing, SSL acceleration, and using an XML threat protection. Additionally, and can fine-tune settings in various processing rules and policies to ensure best performance for high-throughput applications.
71. Explain the considerations for securing RESTful APIs with DataPower?
Ans:
Securing RESTful APIs with the DataPower involves implementing OAuth, JWT, and the other authentication and authorization mechanisms.And should also consider input validation, threat protection, and rate limiting to protect against security threats and maintain the quality of service.
72.What is DataPower’s role in hybrid cloud and multi-cloud environments?
Ans:
In hybrid and multi-cloud environments, DataPower can serve as the bridge between on-premises systems and cloud-based resources. It can handle integration, security, and traffic management to ensure the seamless communication between the different cloud platforms and services.
73. Explain the key features and benefits of a DataPower GatewayScript?
Ans:
DataPower GatewayScript is the server-side JavaScript environment that allows to write a custom code for DataPower. It provides the flexibility to perform a complex data transformations and processing within a DataPower policies, enhancing its capabilities for handling the various integration scenarios.
74. Explain DataPower in a microservices architecture?
Ans:
In microservices architecture, DataPower can act as API gateway, managing the interactions between the microservices. It provides the security, traffic management, and transformation services, ensuring a seamless communication among microservices.
75.Describe handling high-availability configurations in DataPower?
Ans:
High-availability configurations involve the setting up redundant DataPower appliances and implementing a load balancing and failover mechanisms configuring an active-standby setups and global load balancing to ensure a continuous availability of services.
76. How does optimize DataPower policies for performance?
Ans:
Performance optimization involves the various techniques like caching, efficient use of protocols, minimizing processing steps in the policies, and leveraging hardware acceleration. Optimized policies are reducing unnecessary processing and leveraging caching mechanisms to be enhance overall performance.
77. Explain customizing error handling and logging in DataPower?
Ans:
Customized error handling by creating a specific error-handling policies that provide a meaningful error messages to the clients while logging relevant details for debugging purposes. Additionally, configured logging to be capture necessary information without impacting a performance significantly.
78. Describe challenging security problem encountered in DataPower and how does resolved it?
Ans:
Security challenge related to an XML External Entity (XXE) attacks. To mitigate it, implemented input validation, disabling an external entity processing, and employed schema validation. Regular security audits and patching also played the crucial role in resolving the issue.
79. How does handle large payloads efficiently in DataPower?
Ans:
Handling the large payloads requires the optimizing buffer sizes, leveraging streaming, and efficiently using the protocols like MTOM (Message Transmission Optimization Mechanism). Used backend pagination and asynchronous processing to be manage the large volumes of data effectively.
80. Explain integrating DataPower with the identity providers for SAML-based authentication?
Ans:
Integrated DataPower with the various identity providers using the SAML (Security Assertion Markup Language) for a single sign-on (SSO) solutions. This involved configuring the trust relationships, handling SAML assertions, and ensuring a secure communication between DataPower and the identity provider.
81. Describe a scenario where does optimized DataPower processing for a specific use case?
Ans:
In a scenario involving the heavy transformation, optimized DataPower processing by implementing a caching for frequently accessed data, leveraging reusable stylesheets, and minimizing unnecessary transformations. This significantly reduced the processing time and enhanced an overall system performance.
82. Explain implementing rate limiting and throttling in a DataPower?
Ans:
Implemented rate limiting and throttling policies to control a number of requests processed within the specified timeframe. This involved using a Quota objects, setting up a rate limits, and enforcing policies to prevent abuse and ensure a fair usage of services.
83. Describe the integration of DataPower with WebSphere MQ?
Ans:
DataPower integrates with the WebSphere MQ using MQ-specific processing policy. It enables a DataPower to interact with WebSphere MQ queues and topics, allowing the seamless communication between the DataPower services and MQ applications.
84. How does DataPower handle security vulnerabilities such as DDoS attacks?
Ans:
DataPower handles the security vulnerabilities like DDoS attacks through the features like rate limiting, connection throttling, and IP blacklisting. It can be detect abnormal traffic patterns and take a predefined actions to mitigate impact of DDoS attacks.
85. Explain DataPower Stylesheet Caching?
Ans:
DataPower Stylesheet Caching optimizes an XSLT processing by caching the compiled form of a stylesheets. Cached stylesheets are stored in the memory, reducing the processing time for a subsequent requests that use same stylesheet. This improves overall performance and reduces the CPU usage.
86. Discuss AAA in securing DataPower appliances?
Ans:
In DataPower, AAA (Authentication, Authorization, and Accounting) is critical for appliance security. It ensures that only authenticated users have access to the resources, authorises users based on roles, and tracks activities for auditing and compliance.
87. Explain how DataPower can handle the JSON Web Tokens (JWT) processing?
Ans:
DataPower can handle the JWT processing using its crypto and processing policies. It can validate a JWT signatures, decode JWT tokens, and enforce policies based on JWT claims. This capability is essential for securing an API endpoints and web services.
88.Describe the process of handling large XML payloads efficiently in DataPower.?
Ans:
DataPower can efficiently handle the large XML payloads by utilizing streaming techniques. Streaming allows the DataPower to process XML documents in chunks, which reduces memory consumption and allows for the processing of large documents that do not fit entirely in memory.
89. Explain dynamic backend server selection in DataPower?
Ans:
Dynamic backend server selection in the DataPower involves choosing an appropriate backend server based on a runtime conditions such as load, availability, or content. DataPower can dynamically select a backend servers using features like a load balancing algorithms and health checks.
90. How does DataPower handle message-level security for web services?
Ans:
DataPower ensures a message-level security for web services by implementing the standards like WS-Security. It can encrypt and sign SOAP messages,validate a security tokens, and enforce security policies defined in the WS-Security specifications,ensuring the confidentiality and integrity of messages.
91. What does disadvantages of datapower?
Ans:
- Cost : DataPower appliances can be an expensive to purchase and maintain, making them a less accessible for smaller businesses with the limited budgets.
- Complexity : DataPower configuration and management can be a complex, especially for beginners or those unfamiliar with appliance.
- Vendor Lock-In : DataPower ties users to the IBM’s ecosystem. Once integrated into a system, transitioning away from a DataPower can be challenging due to the need for extensive reconfiguration and re-engineering.
92. What does advantages of datapower?
Ans:
- Security : DataPower provides the robust security features, including an encryption, digital signatures, threat protection, access control, and firewall capabilities.
- Integration Capabilities : DataPower acts as comprehensive integration platform, enabling a seamless communication between the diverse systems, protocols, and data formats.
- Performance Optimization : DataPower accelerates a data processing and optimizes performance by implementing a caching mechanisms, compression techniques, and efficient routing algorithms.
93. What does applications of IBM datapower?
Ans:
- API Management : DataPower can be used as API Gateway to manage, secure, and monitor APIs.
- Service-Oriented Architecture (SOA) Integration : DataPower enables the seamless integration between disparate systems in a SOA environments..
- Web Services Security : It can authenticate a clients, encrypt and sign SOAP messages, validate security tokens, and protect against to common web services vulnerabilities, ensuring secure communication between services.
94. Why does IBM Datapower?
Ans:
Most of the time, DataPower firmware is utilized to execute an electronic messaging operations. As enterprise service bus, it can modify and route communications and safeguard web services interfaces and architecture behind them from threats. It assists in integrating a any two apps by treating them as services. It’s a platform and language agnostic.
95. What does Characteristics Of WebSphere DataPower?
Ans:
Combined policy requirement and progressed security allows the solitary entry to highlight, ensure and utilize predictable security arrangements across the business channels, diminishing functioning expenses and enhancing security.A solitary multi-channel passage platform that is more secure, incorporated, controls and streamline conveyance of remaining workloads across the different channels like: API, mobile, web, SOA, B2B and cloud.
96.What does difference between DataPower and traditional ESB (Enterprise Service Bus)?
Ans:
DataPower is designed for a high-speed, low-latency, and secure processing of XML and non-XML data. It is used at the edge of the network. In contrast, ESBs are the more comprehensive, handling the various integration needs and often used within organization’s network.






