
DevOps Tool is an application that helps automate the software development process. DevOps tool also enables teams to automate most of the software development processes like build, conflict management, dependency management, deployment, etc. and helps reduce manual efforts.
- Introduction to DevOps Tools
- What is DevOps Tools
- Features of DevOps Tools
- DevOps Security Tools
- Security Tool – OSSEC & OWASP Zed Attack Proxy (ZAP)
- LogRhythm SIEM & Venafi Trust Protection Platform
- Charles Proxy & Burp Proxy
- CyberArk,Snort & JBoss Data Virtualization
- Benefits Of DevOps Security Tools
- Conclusion
Introduction to DevOps Tools:
DevOps tools are a combination of advancement and operations programming design practices that aim to combine programming improvement with programming operation. The first standard for DevOps development is just too strict. DevOps strives for quicker development cycles, increased arrangement recurrence, and more trustworthy discharges, all while working closely with business objectives. It promotes automation and testing in the simplest ways of programming development, from incorporation, testing, and discharge to organization and foundation management.
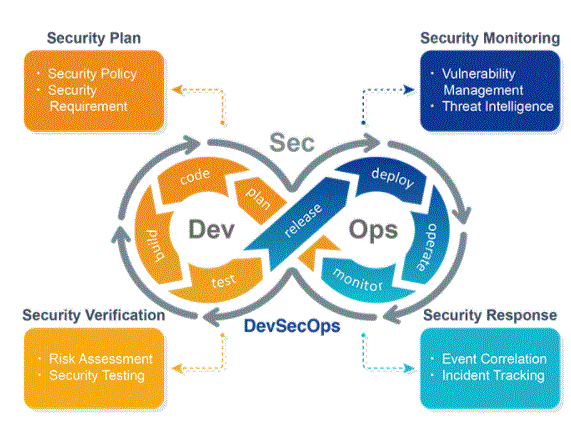
- DevOps tools are the act of operations and developers engineers working collaboratively across the whole administration lifecycle, from planning to development and support. DevOps instruments are also depicted by operational workers who employ a significant number of indistinguishable ways from engineers for their framework tasks. It doesn’t appear to be a lot of differentiation between the many framework administrator sub-disciplines.
- DevOps is that the coordinated effort amongst advancement technology and operations groups, Today it’s an important part of organizations by creating and executing DevOps culture centers IT comes about and to spare time and money because the hole amongst designers and IT operations groups closes. Similarly, because the term and culture are the newest significant number of the simplest DevOps devices these DevOps engineers use to hold out their employments proficiently and productively.
- DevOps forms, both computerized and manual, and to decide whether or not they are working to support you. you’ve got to try to do two things with these apparatuses. to start with, characterize which measurements are pertinent to the DevOps forms, for instance, the speed of sending as against testing blunders found. Second, define robotic techniques for revising concerns without human intervention. On cloud-based stages, for example, programming scaling difficulties would be handled automatically. Below are some of the most often used Develops tools.
What is DevOps Tools:
Features of DevOps Tools:
Let’s discuss below a few of the key features of DevOps:
1. Collaboration- Collaboration between the 2 departments stands at the exact base of the DevOps operations. While it does require cross-functional training and discipline also as may end in the changing of predefined roles, such collaboration ultimately results in higher efficiency and effectiveness.
2. Quantification- It is necessary to possess a scale on whose basis a practice and its effects are often judged. By quantifying the number of deployments, failures, time taken for every deployment, uptime, etc before employing DevOps, you’ll successfully judge the impact and improvement of DevOps on your work culture and environment.
3. Automation- While the developing department generally features a high level of automation, we don’t observe an equivalent with the operations side. By integrating an equivalent level of industrialization in both departments, we achieve A level of consistency and efficiency across the board that might not rather be possible.
4. Holistic- A holistic system means sulking about the whole system and therefore the ecosystem around it.
DevOps Security Tools:
1. Signal Sciences Web Protection Platform:
Signal Sciences Web Protection Platform (WPP) offers broad threat protection but at an equivalent time, it’s not one among the simplest positioned as some extent provider. the corporate from its very inception took the teachings that they’ve learned over the years to develop this platform to defend against real-world threats. it’s one of the applications which will enable a full spectrum of cybersecurity to web applications. WPP isn’t just an internet Application Firewall (WAF), but it’s far more than that.
2. Checkmarx AppSec Accelerator:
AppSec Accelerator is the Best application security managed service that will help organizations to transition to a secure SDLC model combining it with Static / Dynamic application security testing to supply the simplest possible security coverage. The tool will assist you to streamline and also to automate your application security testing. Through the tool itself, all the needed expertise is additionally provided to make sure the application’s security is successfully attained. The tool in itself enables you to rapidly build up, set up, and deploy your app sec program. it’ll also enable you to transition your Organization to an automated secure SDLC one.
- The intrusion detection system is often mentioned as a management system for both computers and networks. it’s a mixture of architected devices and software applications to detect malicious activities and violations of policies and produce a report thereon.
- An intrusion detection system may monitor a network for any abusive, unusual, or malicious activities.
- Every hostile or abusive conduct is continuously logged off. These logs are critical for security experts who need to take action or apply rules to these actions.
- IDS logs are frequently used against an abuser as evidence to justify any legal action.
Security Tool – OSSEC & OWASP Zed Attack Proxy (ZAP):
OSSEC is a host-based intrusion detection system that is free and open-source (HIDS). Log analysis, integrity testing, Windows registry monitoring, rootkit identification, time-based alerting, and active response are all performed. It detects intrusions for a variety of operating systems, including Linux, OpenBSD, FreeBSD, OS X, Solaris, and Windows. OSSEC is a centralized, cross-platform design that allows many systems to be monitored and controlled effortlessly.
OSSEC consists of most applications, a Windows agent, and an internet interface. most applications, OSSEC, are required for distributed network or stand-alone installations. it’s supported by Linux, Solaris, BSD, and Mac environments. The Windows agent is available for Microsoft Windows environments. To support the Windows Agent, most apps must be installed and configured for server mode. Web interface (deprecated), which provides a graphical interface as a separate program. It works on Linux, Solaris, BSD, and Mac platforms, much like the main program. For monitoring alerts, it is currently recommended to utilize Kibana, Splunk Graylog, or something similar.
Following are a number of the benefits of using OSSEC, allow us to now take a glance at each and each one among them:
Advantages:
- This program allows you to find all keys, certificates, and CAs continually.
- This program also allows you to continually check keys and certificates for any abnormalities and flaws.
- Allows for the automated replacement of compromised keys and certificates as soon as possible.
- It also assures the execution of key policies and certificate policies, which further strengthens security.
- It also enables certificate requests and renewals to be automated.
LogRhythm SIEM & Venafi Trust Protection Platform:
A SIEM is a crucial instrument in your security toolkit—but it’s not the sole one. to stay up with the ever-evolving threat landscape, you’ll need a SIEM with additional capabilities for network forensics, endpoint monitoring, UEBA, and incident response. LogRhythm’s unified Threat Lifecycle Management Platform is designed to expand your organization’s security requirements without the need for costly integrations or modifications. It provides real-time insight, analytics, and automation throughout your entire IT infrastructure.
LogRhythm Enterprise or LogRhythm XM can help you improve the efficiency and efficacy of your SOC. Both will improve your team’s threat detection and response skills, as well as provide full compliance assurance, security automation, and orchestration. Both are intended to be used simply right out of the box. Choose the option that is best for your company.
Following are a number of the benefits of using the Venafi Trust Protection Platform (TPP), allow us to now take a glance at each and each one among them:
Advantages:

- This tool enables you to look at DTM files and also ensures to understand the order during which they’re loaded.
- Can use any device to ascertain the analytics beacons regardless of the sort of the device.
- Allows you to tweak a page and make modifications, allowing you to emulate its behavior as if it were loaded on Production.
- It allows you to save the session of analytics traffic so that it is often sent to the concerned people later in time.
- Let’s capture the complete URL of the POST beacon so that the parser tool might be wont to split it out.
- Let’s you’re taking a glance at the headers and also the cookies attached to a given beacon at any point in time.
- Burp Proxy also can perform the automated modification of responses to facilitate testing in a better way.
- There is an opportunity to configure fine-grained interception rules enabling you to focus more on interesting interactions.
- HTML5 WebSockets are intercepted and logged during a different history than the regular HTTP messages
- Burp Proxy supports invisible proxy for clients that aren’t proxy aware, thereby enabling the testing on thick client applications and mobile applications.
Charles Proxy & Burp Proxy:
Charles is designed to be an entry-level piece of software. When you start it, it will plan to automatically set up your browser so you can get up and running right away. Begin exploring the web and watch the results shown in Charles; click on them to see what’s been recorded. You must allow permission to Charles by providing your password for Mac OS X to auto-configure your proxy settings.
If your proxy settings have been automatically set up, you will then be able to watch the events being recorded in Charles using your browser. It’s pretty powerful so that you can now view anything that’s sent and received – it allows you and goes under the hood to see who is going on.
Following are a number of the benefits of using Charles Proxy, allow us to now take a glance at each and each one of them:
Advantages:
Burp Proxy:
Burp Proxy is yet one more graphical Security Testing tool for web applications that acts as an intercepting proxy server. it’s a tool that’s written in Java and has two versions thereto – A free version that’s available for download and also a Full version which will be purchased because it may be a Professional Edition software tool. It plays the role of a person within the middle between your browser and also the target. it’s developed in specific as a comprehensive solution for web application security checks. These behaviors as a proxy scanner, and also as intruder also provide more advanced options like Spider, Repeater, Decoder, Comparer, Extender, and also Sequencer.
Following are a number of the benefits of using Burp Proxy, allow us to now take a glance at each and each one among them:
Advantages:
- One of the best advantages that tools like these bring back the table isn’t just the upkeep or the safety of these credentials but also curtails the manual effort of keeping these details updated at one place for further use.
- Not just the trouble but also reduces the time that’s otherwise spent on maintaining these accounts.
- Maintenance efforts also are managed pretty much with the tool to gauge when an account must be created or deleted.
- Any policies that require to be applied around this area are often applied in one place instead of on multiple places or multiple systems or multiple people.
- Can bring a process to the table round the Password management and therefore the like, as there’ll not be a manual intervention for these maintenance activities.
CyberArk,Snort & JBoss Data Virtualization:
CyberArk is an information security firm that focuses mostly on privileged account security. It is a complete suite of security and account management solutions that are particularly developed to ensure the security of privileged accounts and the like. One of the solutions in the aforementioned suite of products is the Privileged Password Management and Control, which was designed expressly to meet the Organization’s high compliance criteria for privileged password management.
Stronger privileged password management controls are implemented to reinforce the way businesses and organizations secure and also monitor privileged accounts. The tools from this Organization are specifically observed to be deployed within the financial industry.
Following are a number of the benefits of using CyberArk, allow us to now take a glance at each and each one among them:
Advantages:
Snort is another free and open-source security DevOps tool that is used in Network Intrusion Prevention System (NIPS) and Network Intrusion Detection System (NIDS) (NIDS). Snort is cross-platform and may be installed on Windows NT, Windows 2000, HP-UX, Solaris, OpenBSD, FreeBSD, NetBSD, Linux, MacOSX, and a variety of other UNIX varieties. it’s capable to perform protocol analysis, content search/content match, and alongside those, it also can diagnose attacks like buffer overflow, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts, and lots of more attacks.
- Minimize vulnerabilities in applications.
- Helps to implement compliance into the delivery pipeline from day one.
- Maintain and ensure compliance.
- Provides the power to reply to changes rapidly.
- Identify vulnerabilities within the early stages of the software development lifecycle. 6. Offers extra speed and agility to Security Groups.
- Helps to create a trustful relationship with organizations.
- Increase observability.
- Increase traceability.
Benefits Of DevOps Security Tools:
DevSecOps and DevSecOps Tools strive to integrate security concepts and standards across the DevOps cycle, i.e. introducing security controls at each level of the DevOps cycle, particularly during the early phases of the software development lifecycle. It also contributes to the development of a £#39; Security as Code & #39; approach by promoting flexible collaboration between security teams and release engineers.
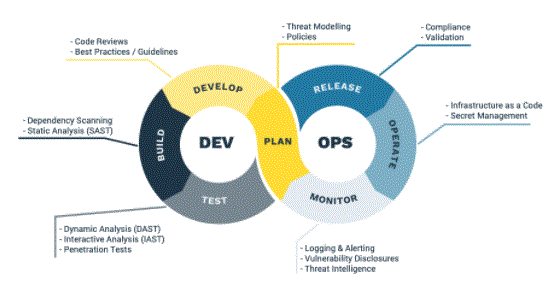
Conclusion:
In this article, we’ve seen absolutely the need for security within the space of DevOps (irrespective of the road of business that the Organizations run. With this common understanding, we’ve skilled the varied options that we had at hand and also understood their advantages when deployed in your DevOps pipeline. Hope you’ve got all the knowledge that you simply seek from this text itself.





