
Rex command in splunk is used for field extraction in the search head. This command is used to extract the fields using regular expressions. This command is also used for replacing or substitute characters or digits in the fields by the sed expression.
- Introduction to Splunk Rex
- Rex command examples
- Rex and Erex Commands
- Rex Description
- Usage
- Fields in Splunk
- How are fields created?
- Many ways of extracting fields in Splunk during search-time
- Benefits of Splunk Rex
- Conclusion
Introduction to Splunk Rex:
Splunk is a software that enables one to monitor, search, visualise and analyse machine-generated data (for example app logs, data from websites, initial repositories) to large data using a web interface. It is an advanced software that identifies and searches log files stored in the system or similar, in addition, fast and powerful software. Splunk closes gaps where a single log management software or security information product or single event management product can not control itself.
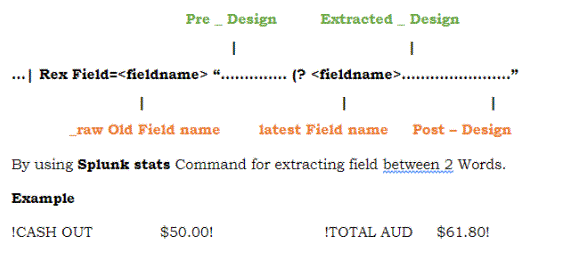
Splunk ‘rex’ command:
The Splunk command given will execute the fields using standard group expressions or instead of field characters using UNIX (sed) broadcast editor expressions. If the field is not specified then a standard sentence _raw field will be used, which will have a working stroke.

- … | | rex field = ccnumber mode = sed “s / (\\ d -) / XXXX-XXXX-XXXX- / g”
- … | | rex field = savedsearch_id “(? \ w +); (? \ w +); (? \ w +)
Rex command examples:
1. Use
Use to match regex with a series of numbers and replace the unknown unit with one unit. During this example the primary three sets of mastercard numbers are going to be created anonymously. \ D should be avoided in speech using the backslash (\) character.
2. cypher field values using
Remove “user”, “app” and “SavedSearchName” from “savedsearch_id” within the hardware.log events. Once field content is savedsearch_id = bob; search; my_saved_search this syntax command rex exits user = bob, app = search, and SavedSearchName = my_saved_search.
- | rex [field = ] ()
- For those who would like to use the Rex command, and would like learning resources, please use websites like https://regex101.com/ to improve your progress.
- To specify what the name of your new field will be called in Splunk, use the following syntax:
- | rex [field = ] (? ”regex”)
Rex and Erex Commands:
After deleting fields, you may find that some fields contain specific data that you would like to control, use for statistics, or display itself. You can use the Rex and Rex commands to help you.
Rex
Rex command is perfect in these cases. With active regex information, you can use the Rex command to create a new field for any existing field you defined earlier. This new field will appear in the sidebar of the field in the Search & Reporting App to be used as any other excluded field.
Syntax
Erex
Many Splunk users have gained the advantage of using Regex field output, encryption values, and the ability to minimise effects. Instead of reading Regex’s “entry and exit”, Splunk provides an erex command, which allows users to generate regular expressions. Unlike Splunk rex and regex commands, erex does not require Regex information, and instead allows the user to define conflicting examples and examples of data to be matched.
Syntax
| erex examples = ”
- rex [field = ]
- ( [max_match = ] [offset_field = ]) | (mode = suspended )
- Required arguments
- You must specify or mode = sed.
- regex-expression
- Syntax: “”
- Definition: a standard PCRE expression that describes info to be compared and extracted from a such as location. Quotation marks square measure needed.
- mode
- Syntax: mode = sed
- Definition: Specify to point that you just square measure exploitation the sed word (UNIX stream editor).
- sed-speech
- Syntax: “”
- Definition: once mode = sed, specify that you just can modify the unit of character (s) or replace characters (y) within the same common sentence. No different sed commands apply. Quotation marks square measure needed. Sed mode supports the subsequent flags: the world (g) and ordinal event (N), wherever N is that the range of characters within the character unit.
- Arguments of your alternative
- field
- Syntax: field =
- Definition: the sector from which you would like to extract info.
- Default: _green
- great_s nice similarity
- Syntax: max_match =
- Definition: Controls the amount of times a regex is matched. If larger than one, the ensuing fields square measure fields with multiple values. Use zero to specify an unlimited match. several of an equivalent applies to the perennial use of the total pattern. If your regex contains a bunch of images which will match multiple times among your pattern, solely the last cluster of images used for many of an equivalent. gDefault: 1
- offset field
- Syntax: offset_field =
- Definition: Creates a field that displays bound values in a forum argument, supporting the quality expression laid out in the regex expression. As an example, if the rex expression says “(? . )” the primary 10 characters of the sector argument square measure are matched. Offset field shows tenchars = 0-9. The offset range forever uses zero (0) within the 1st place. For a lot of examples, see Examples.
- Default: No default
Rex Description:
Use this command to exclude fields exploitation common cluster expressions, or substitute or modify characters in situ exploitation sed expressions. The rex command is the same because the worth of a such as field versus traditional non-target expression and removes teams named when corresponding word fields.
When mode = sed, the given sed expression accustomed replace or replace characters is applied to the chosen field worth. This sed-syntax is additionally accustomed to cipher sensitive information throughout the index. find out about exploitation used to form information anonymously in information Recovery by Manual. Use the rex command to exit the search time field or modify the character unit and exchange characters.
Syntax
The required syntax is highlighted.
- Use the rex command to exclude fields using common cluster expressions, or modification or modification characters in situ using sed expressions.
- Use the regex command to get rid of results that don’t match the traditional spoken expression.
- Ordinary expressions
- Splunk SPL uses common perl-related expressions (PCRE).
- When using common expressions in search, you wish to listen to however characters like pipe (|) and backslash (\) square measure handled. See SPL and customary expressions within the Search Manual.
- For general data concerning common expressions, see Splunk Enterprise common expressions within the data Manager Manual.
- Sed speeches.
- When using the rex command in sed mode, you have got 2 options: replace (s) or replace character (y).
- The syntax for using sed to alter (s) text in your information is: “s / / / ”
- maybe a common expression for PCRE, which may embody recording teams.
- maybe a character unit to switch regex matching. Use \ n for backgrounds, wherever “n” may be a single digit.
- Is g to switch all matches, or variety that may replace the desired match.
- The syntax for using sed to switch characters says: “y / / /”
- This replaces characters like and characters in.
Usage:
The rex command may be a streaming command. See Command varieties.
- Fields turbo charges your search by allowing you to customise and tailor your search. For example, consider the following SPL
- index = web sourcetype = integrated_access_date> = 500 response_time> 6000
- SPL above searches for a web-based index that may have web access logs, with source type equal to access_combined, large or 500-degree (indicating server side error) and answer_time greater than 6 seconds (or 6000 milliseconds) . This type of flexibility in data testing will not be possible with simple text search.
Fields in Splunk:
- index
- host
- source
- source
- _the time
- _komba
- splunk server
- Reflected output uses a lot of disk space.
- The reference output is invariant. i.e. if you change the configuration of any indexed output, the entire index needs to be reconstructed.
- There is a performance effect as the References do extra work during the index.
- Instead, you should use search time quotes. Schema-on-Read is, in fact, the supernatural power of Splunk that you will not find in any other forum for compiling logs. Schema-on-Write, which requires you to define fields before Indexing, is what you will find on most logging platforms (including ElasticSearch). With the Schema-on-Read that Splunk uses, it cuts and sells data during searches without the persistent correction made in the indexes. This also provides great flexibility as you define how fields should be extracted.
How are fields created?
There is good news here. Splunk creates multiple fields automatically. The process of creating fields from raw data is called extraction. Automatically Splunk releases multiple fields during index time. Most notable are:
You can configure Splunk to generate additional fields during index time based on your data and the issues you specify. This process is also known as adding custom fields during the index. This is achieved by setting up props.conf, transforms.conf and fields.conf. Note that if you are using Splunk in a distributed area, props. conf and transforms. conf resides in the Indexers (also known as Search Peer) while the fields.conf resides in the Search Topics. And if you use Heavy Forwarder, props. conf and transforms. conf stays there instead of Indexers.
Although reference timing may seem appealing, you should try to avoid it for the following reasons.
- Using Field Extractor utility in Splunk Web
- Using the Forums menu in Splunk Web Settings
- Using configuration files
- Applying SPL commands
- rex
- take out
- multikv
- place
- xmlkv / xpath
- kv form
Many ways of extracting fields in Splunk during search-time:
There are several ways to clear fields during a search. These include the following.
For Splunk neophytes, using a Field Extractor app is a good start. However, as you get more information about field extraction, you will begin to realise that Field extractor does not always come up with common expressions that work very well. Eventually, you will start using the power of rex command and standard expressions, which we will look at in more detail now.
Rex is an SPL (Search Processing Language) command that extracts fields from raw data based on a pattern you specify using common expressions. The command takes the search results as input (i.e. the command is written after the pipeline in SPL). It is similar to the normal speech pattern for each event and saves the value in the field you specify.
Benefits of Splunk Rex:
Data Entry
Splunk can import various data formats: JSON, XML and random machine data such as the web and application logs. Random data may be modelled into data user configuration where required.
Data Identification
Imported data is identified by Splunk so they can quickly search and inquire about different situations
Data Search
Splunk search involves using coded data for metrics, predicting future trends and identifying patterns in data.
Using Notifications
Sprunk notifications can be used to launch emails or RSS feeds if there are certain conditions obtained from analytical data.
Dashboards
Splunk dashboards can display search results in the form of charts, reports, and pivots, etc.
Data Model
Reference data can be modelled into one or more specific data sets domain information. This leads to easy navigation by end users who analyse the business conditions without learning the language technology to process the search used by Splunk.
Conclusion:
We have tried to clarify what Splunk can do as a standalone software and where its use can be. We also tried to understand how to use the Splunk rex command to extract data or replace data using common expressions.
As we saw above, Splunk is a management tool with Big Data analysis. Undoubtedly it holds the position of the market leader, but somehow its high price makes it inaccessible to many organisations. However, if you are looking for a job in this field, you are heading in the right direction.
Many large IT organisations need people associated with this field. You may feel a bit challenged to find jobs through this forum, but if you belong to any organisation, you will see your rapid growth with your own eyes. So, no doubt you can find great opportunities by reading this forum. Good luck with your work.





