
If you are preparing for FortiWeb Interview, then you are at the right place. Today, we will cover some mostly asked FortiWeb Interview Questions, which will boost your confidence. FortiWeb is a web application firewall (WAF) that protects web applications and APIs from attacks that target known and unknown exploits and helps maintain compliance with regulations. Therefore, FortiWeb professionals need to encounter interview questions on FortiWeb for different enterprise FortiWeb job roles. The following discussion offers an overview of different categories of interview questions related to FortiWeb to help aspiring enterprise FortiWeb Professionals.
1. What is FortiWeb?
Ans:
Web application firewalls, or WAFs, are the source of FortiWeb, a firewall service that shields web applications housed on web servers from malicious attacks. Application security is provided by FortiWeb, which employs correlated and multi-layered detection algorithms. Large corporations, small and medium-sized businesses, and service providers can all access the FortiWeb hardware and virtual machine platforms.
2. How can a server that hosts web applications be secured?
Ans:
- To safeguard a server hosting an online application, such as webmail, utilize a web application firewall profile.
- Constraints and signatures are two types of parameters that are used when creating web application firewall profiles.
- The action can be configured to monitor, block, or allow once these options are enabled.
3. How does FortiWeb integrate into the overall architecture?
Ans:
- Although FortiWeb can be set up as a one-arm-to-suit architecture, it is more frequently placed in a line to intercept and redistribute all incoming client connections to servers. FortiWeb is capable of TCP and HTTP-specific firewalling.
- Because FortiWeb is not intended to secure non-HTTP/HTTPS web applications, it can be installed inside a firewall, like FortiGate, which concentrates on protocol security for other protocols, like SSH and FTP. After being used, FortiWeb can be configured on the central computer using a web browser or terminal emulator.
4. Explain what FortiWeb’s HPKP is.
Ans:
Activating FortiWeb adds HTTP Public Key Pinning (HPKP). A header is sent to the server’s response header field when processing client requests. The client gains access to the server by using the exclusive cryptographic public key specified in the inserted header. Designating a public key for web server access reduces the likelihood of Man-in-the-Middle (MITM) attacks involving forged certificates and compromised CAs.
5. What is Stapling by OCSP?
Ans:
- The alternative method of OCSP (Online Certificate Status Protocol) stapling, which FortiWeb supports, involves the certificate holder periodically contacting OCSP servers to inquire about the revocation status of a server’s certificate and attaching the time-stamped response to the initial SSL/TLS handshake between clients and servers.
- This shifts the resource burden of verifying a certificate’s revocation status from the client to the certificate presenter, lowering the overall number of queries to OCSP servers.
6. How Credential is Stuffing protected against by FortiWeb?
Ans:
FortiWeb now prevents attackers from using credential stuffing. When Credential Stuffing Defense is enabled, a web server login attempt’s username and password are processed in the database to determine whether or not a username and password pair was leaked. FortiGuard is needed to utilize this feature.
7. Differentiate between FortiWeb Web Application Firewall and FortiGate Next-Generation Firewall.
Ans:
| FortiWeb Web Application Firewall | FortiGate Next-Generation Firewall |
|---|---|
| Specialized in protecting web applications from various web-based attacks, including SQL injection, cross-site scripting (XSS), and other OWASP Top Ten vulnerabilities. | Offers comprehensive network security, including firewalling, intrusion prevention, VPN, antivirus, and application control, with a broader focus on all types of network traffic. |
| Primarily deployed in front of web applications, acting as a dedicated security layer for protecting against web-based attacks. | Deployed at the network perimeter, providing security for the entire network infrastructure, including web, email, and other application traffic. |
8. Describe the constraints of the HTTP protocol.
Ans:
There are now seventeen additional HTTP protocol limitations in the latest FortiWeb versions. Eight more have been added to regulate the particular HTTP/2 header fields. These are:
- Preface to Illegal Connection
- Type of Illegal Frame
- Unlawful Frame Reports
- First Window Dimensions
- Size of Header Compression Table
- Size of Header List
- Dimensions of the Frame
- Count of Active Streams
9. Describe the exceptions to the HTTP constraint.
Ans:
For each of the five additional HTTP constraints, the appropriate set of constraint exceptions is added:
- Redundant headers in HTTP
- Maximum Name Length for the URL Parameter
- Maximum Length of URL Parameter Value
- Invalid Character in the Name of a Parameter
- Illegal Character in the Value Parameter
It is possible to apply exceptions to HTTP constraints to packets with specified source IP addresses.
10. What’s Site Publishing all about?
Ans:
Exchange ActiveSync enables Android clients to connect to Microsoft Exchange servers through site publishing. The only way to authenticate clients is through HTTP Basic Authentication; even if a site-publishing rule is set up for Exchange ActiveSync, single sign-on, authentication cookies, and Kerberos authentication are not supported.
11. What is Geo IP?
Ans:
The Geo IP database is a specialized database that was added to improve FortiWeb’s GEO IP to pinpoint IPv6 address locations precisely. The GEO IP database can be uploaded sparingly. FortiWeb uses the FortiGuard Distribution Servers to update the database automatically. The database uploading interface can be used by hand for deployments without an Internet connection.
12. What exactly is cookie poisoning?
Ans:
The new cookie security policy includes cookie poisoning options that let administrators put up extra defenses against cookie-based assaults. For instance, we can add security features or encrypt cookies sent by a backend server.
13. What is the tracking of users?
Ans:
The updated user-tracking function enables us to monitor a user’s sessions, record a username for use in communication, and log messages from attacks. This functionality allows us to establish a time window in which FortiWeb filters requests containing a session ID from a timed-out session, thus preventing a session fixation attack.
14. How do members of the server pool configure Advanced SSL?
Ans:
- SSL and TLS versions are supported for connections between FortiWeb and a certain server pool member when the operating mode is set to reverse proxy.
- These cover SSL/TLS offloading and communications between FortiWeb and the server pool member for real transparent proxy and WCCP modes.
15. What is threat scoring?
Ans:
The threat scoring function: Instead of focusing on a single signature infraction, organizations can set up their signature policies to take punitive action based on many violations on any client. A client’s violation of a signature in the threat-scoring area adds to the overall threat score—fortiWeb acts when the total threat score surpasses the designated maximum value. The computation is based on HTTP transactions or sessions or TCP sessions; we can define the total threat scores.
16. What are the dashboards for Status and Policy Status?
Ans:
- The number of connections made so far and the number of connections made in a second for each policy are shown in the System Resources widget on the dashboard.
- The number of active connections and connections per second broken down by policy are shown in the Policy Sessions widget and Policy Status dashboard.
- In addition to counts for individual rules, the graphs in the Real-Time Monitor widget on the Status dashboard show total counts for HTTP throughput, attack events, and HTTP hits.
17. What is a block of periods?
Ans:
Traffic that violates a policy is subject to Period Block, which is the action that FortiWeb conducts when the operating mode is visible in the offline protection or inspection. FortiWeb tries to block clients for the Block Period when they violate the policy.
18. What is DoS?
Ans:
- A distributed denial-of-service (DDoS) assault, also known as a service denial (DoS) attack, aims to take control of a web server and prevent its intended customers from accessing its resources.
- In a denial-of-service attack, many sessions are opened at different OSI layers and keep them open for as long as you can to overwhelm the server by using up all of its sockets. Instead of using any browsers, most DoS attacks generate a damaging and massive volume of requests delivered to a web server using automated tools.
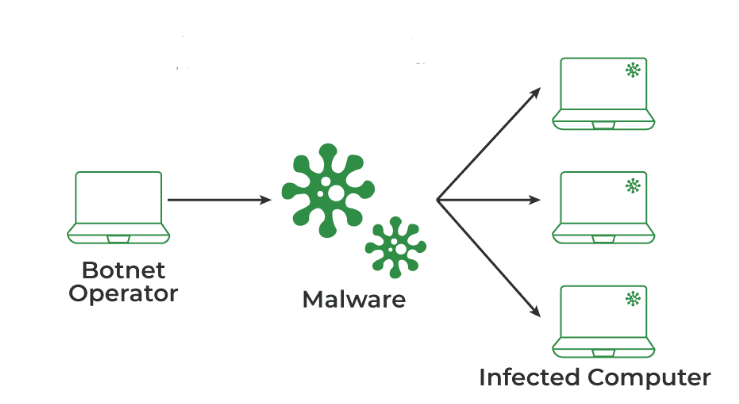
19. What’s a botnet?
Ans:
A botnet is a threat that leverages globally dispersed, already infected zombies to take over the server controlled by command on control servers. Zeus, HOIC, and LOIC are a few examples.
20. What is the opposite proxy mode?
Ans:
- Reverse proxy operation by FortiWeb provides end-to-end HTTP/2 security but requires both HTTP/2 servers and clients to be operational at the back end. Moreover, FortiWeb provides HTTP/2 protection with backend web servers that do not support HTTP/2.
- Data exchange protocols on the back end between the HTTP/1.1 servers and the HTTP/2 clients. Because of this, users can benefit from HTTP/2 without needing to update their backend web servers.
21. How does HA select the active appliance?
Ans:
If the failed appliance becomes responsive to heartbeats again, an HA pair may not return to their active and standby modes. Unless configured to override, the currently active device usually maintains its status as the active device because it will upload data more quickly than a failed and active device that has come online, assuming each has the same number of available ports. The returning device with the higher appliance setting will be chosen as the cluster’s active device if enabled.
22. What distinguishes transparent inspection mode from true transparent proxy mode?
Ans:
- True transparent and transparent proxy examinations are comparable to any feature of topology. Only a few behavioral distinctions exist between the two because of the differences in the mechanism of data interception:
- Genuinely translucent When traffic reaches any network port on a Layer 2 bridge, transparent proxies refer to the first suitable policy and let the traffic pass. For its safety profile, FortiWeb records, blocks, or even changes the infractions by the rules. Instead of using HTTPS for user authentication, this mode allows HTTP.
24. Can we delete the admin account?
Ans:
- The default administrator account is called Admin and, at first, without a password. The admin administrator account is created by default and cannot be removed. Like all root administrator accounts, the admin administrator account is comparable.
- This administrator account always has full access to all configuration settings on FortiWeb devices, including the ability to see and change any other admin account’s settings. Changes to permissions and usernames are not possible.
25. What does the active-passive style refer to?
Ans:
- FortiWeb is renowned for its active-passive design. In other words, if one device is assigned as the active device and policies are applied to all connections, the second device becomes the passive standby, which takes over as the active device if the active device fails and begins processing the assigned tasks.
- By connecting the two devices in a heartbeat pair, both active and standby devices can communicate when there is a breakdown. Heartbeat timeout = Interval in Detection x Threshold in Heartbeat Loss is the configuration used to identify failures when active devices cease responding to a heartbeat from standby devices for a predetermined time.
26. How can we duplicate the external HA setup without FortiWeb HA?
Ans:
The external setup Without utilizing FortiWeb high availability (HA)configuration synchronization makes it possible to replicate the configuration from a different FortiWeb appliance. There is no mutual synchronization involved; the synchronization is a unilateral push.
27. How can dynamic URLs and odd parameters be accommodated in auto-learning?
Ans:
Auto-learning can be used to help establish protection settings. Many of the risks that web assets confront are taught by auto-learning. Understanding the architecture of web apps and how people interact with them is also beneficial. Above all, however, auto-learning aids in customizing FortiWeb’s setup to fit online applications. By monitoring the traffic to the servers, auto-learning finds the URLs exhibiting various HTTPS or HTTP session behaviors. It carries out the following actions to determine whether the request is authentic or a possible attempt at an attack:
- Assess the attack signature request.
- Tracks web servers’ response to each request, including 500 Internal Server Errors and 401 Unauthorized.
- Monitors inputs, including cookies and URL parameters.
- Tracks the frequency of file requests by IP address and type of content.
28. How Are URL Interpreters Configure?
Ans:
When utilizing auto-learning, we need to specify how to intercept dynamic URLs that contain many factors in non-standard ways, such as the factor incorporated in the URL’s structure or separators (; or #). These interceptor plug-ins, or “URL replacers,” are a part of any web user interface.
29. What data types does FortiWeb recognize?
Ans:
By matching the parameter data types with regular expressions, FortiWeb can identify them. There are several types of regular expressions.
- Predefined: The firmware contains a collection of regular expressions. These are unchangeable and correspond to typical data types. It can be duplicated and utilized as the foundation for a bespoke data type unless via FortiGuard. Both input rules and auto-learning profiles can be used.
- Custom: A regular expression set up to identify any data patterns that the predefined set cannot identify. Auto-learning profiles cannot be used, but input rules can be modified and used.
30. What kinds of data are predefined?
Ans:
Some established data type regular expressions, such as default signatures for frequently used data types, are automatically included in FortiWeb after installation, saving us the trouble of writing them from scratch. The first ones are part of the firmware for the FortiWeb. FortiWeb may periodically download updates to its designated location if connected to the FortiGuard Security Service updates data kinds. This effortlessly offers improved and new data kinds.
31. What is the security policy with Fortinet?
Ans:
Clear, thorough, and well-defined plans, procedures, and guidelines that control who can access a company’s system and its data are called security policies. A well-crafted policy safeguards data and infrastructure, individual workers, and the company.
32. What are the key characteristics of Forti Web?
Ans:
Among the best firewall models Fortinet offers is the Fortigate with advanced threat prevention.
- Secure internet access with VPN functionality.
- Email, online, and multi-layered network security.
- Centralized management tools and an intuitive user interface.
33. What does Fortinet do with Unified Threat Management (UTM), and how does it work?
Ans:
When several security features or services are integrated into a single network device, it’s known as unified threat management or UTM. Users on your network are safeguarded by several capabilities when you utilize UTM, such as anti-spam, content filtering, email and web filtering, antivirus software, and more.
34. Describe the Fortinet security fabric idea.
Ans:
- With the ability to mitigate any potential attack vectors within an organization,
- The Fortinet Security Fabric is a security infrastructure that spans the whole network.
- FortiAPs and FortiSwitches are two more devices that the Security Fabric connects with to offer and manage secure wireless access and do what switches do best—create a network.
- Speaking of access, you may establish a zero-trust network access policy throughout your whole network by using the Fortinet Security Fabric.
35. What does FortiAnalyzer aim to achieve?
Ans:
Network security operations teams can quickly evaluate network devices, systems, and users thanks to FortiAnalyzer’s automation-driven analytics. Correlated log data and FortiGuard threat intelligence allow for the study of both recent and past occurrences.
36. What role does FortiAnalyzer play in threat reporting and analysis?
Ans:
FortiAnalyzer provides Security Fabric Analytics across all device logs with event correlation and real-time detection of Advanced Persistent Threats (APTs), vulnerabilities and Indicators of Compromise (IOC) for FortiGate NGFWs, FortiClient, FortiSandbox, FortiWeb, FortiMail and other Fortinet product.
37. What distinguishes stateful firewalls from stateless firewalls?
Ans:
- Stateful and stateless firewalls largely vary because one type tracks the state between packets while the other does not.
- Other than that, both kinds of firewalls function similarly, examining packet headers and applying the data they hold to decide whether or not a piece of communication is allowed according to preset rules.
38. How does FortiManager control Fortinet devices, and what does it do?
Ans:
An automation-driven, single-pane-of-glass management solution that is scalable, adaptable, and easy to use is offered by FortiManager Cloud. To handle SD-WAN with Fortinet NGFW, utilize the single sign-on portal. With just one console, FortiManager offers centralized, automation-driven management for your Fortinet devices.
39. What are the three functions of Fortinet’s adaptive cloud security solution?
Ans:
Fortinet’s Cloud Security Adaptive fast becoming the new norms for competing in the constantly changing digital economy are hyper-performance, hyper-convergence, and hyper-automation that can traverse increasingly scattered and dynamic networks—enhanced with sophisticated intelligence.
40. In FortiGate, what is an SSL inspection?
Ans:
Firewalls can examine encrypted communication thanks to SSL/TLS deep inspection. When you employ deep inspection, the FortiGate connects to the SSL server in an intermediary role and then decrypts and examines the information to identify and stop threats.
41. Why are FortiGuard services provided?
Ans:
- In addition to helping you comply with regulatory obligations, FortiGuard’s online security is designed to monitor and defend data and applications from web-based attack techniques.
- Critical use cases include URL filtering, DNS security, phishing, SWG, compliance, and SD-WAN.
42. Which four network security vulnerabilities should IoT systems be aware of and avoid?
Ans:
All aspects of protection, including component hardening, monitoring, firmware updates, access control, threat response, and vulnerability remediation, are included in robust IoT security.
44. List the elements that make up the Security Fabric architecture of Fortinet.
Ans:
- Full endpoint protection, email security, online application security, advanced threat prevention, management, analytics, and event management are just a few features it offers. The primary elements involved in putting the44) List the elements that make up the Security Fabric architecture of Fortinet.
- Full endpoint protection, email security, online application security, advanced threat prevention, management, analytics, and event management are just a few features it offers. A single FortiAnalyzer instance and at least two FortiGate firewalls are required to implement the Security Fabric.
45. How is high availability in Fortinet’s solutions ensured?
Ans:
FortiGate supports several HA alternatives, including auto-scaling in cloud environments, virtual router redundancy protocol (VRRP), FortiGate Clustering Protocol (FGCP), and FortiGate Session Life Support Protocol (FGSP). FGCP is the most popular HA solution.
46. What does FortiClient want to achieve?
Ans:
FortiClient offers flexible VPN connectivity options. With split tunneling, users can access the Internet remotely using VPNs without going via the corporate VPN headend, as they would with a regular VPN tunnel. The user experience is enhanced by this feature, which lowers latency.
47. In FortiGate, how can I establish a VPN?
Ans:
Set up FortiGate using an IKEv2 VPN.
- Establish the VPN’s address range. Create a new address on your FortiGate firewall by going to Policy & Objects > Addresses.
- Establish a fresh VPN user account.
- Establish a fresh IPsec tunnel.
- Draft a fresh IPv4 policy.
48. What are the various FortiGate deployment modes?
Ans:
- There are two modes of operation for a FortiGate unit: Transparent and NAT/Route.
- The FortiGate is deployed transparently between the router and the internal network.
- In this mode, the FortiGate performs security scanning on traffic and does not modify IP addresses.
49. What role does intrusion prevention play in FortiGate?
Ans:
To detect and eliminate unknown zero-day and hidden attacks, Fortinet IPS employs a tiered combination of pre-defined signatures to scan traffic for known threats. Heuristic approaches and deep packet scanning using protocol decoders are then used to scan packets for threats.
50. How does cloud application security leverage sandboxing?
Ans:
- Sandboxes are used to run code that raises questions securely without running the risk of damaging the network or host device.
- For sophisticated malware detection, a sandbox offers an additional defense against emerging security risks, such as stealthy assaults and zero-day (before unknown) malware.
- A single FortiAnalyzer instance and at least two FortiGate firewalls make up the Security Fabric.
51. What function does FortiToken serve in Fortinet’s security products?
Ans:
Set up two-factor authentication for access to secure networks and security devices using FortiToken Strong Authentication Solutions. Static passwords and other single-factor authentication solutions carry a higher risk of compromise; two-factor authentication solutions increase security and lower that risk.
52. What security features does Fortinet SASE provide to thwart threats originating from the Internet?
Ans:
- The security Features include functions including DNS filtering, deep SSL inspection, URL filtering, and Data Loss Prevention.
- The Zero-Trust Access Network (ZTNA) offers safe remote access to a company’s apps, data, and services based on well-defined access control regulations.
53. Describe SD-WAN and how FortiGate is compatible with it.
Ans:
Remote locations can connect to networks, data centers, and various clouds more readily thanks to SD-WAN.lower latency, higher performance, and more consistent connectivity. The conventional purpose of a wide-area network, or WAN, was to link users on campus or at the branch to applications housed on data center servers.
54. Which factors are most important while using hybrid cloud computing?
Ans:
Establishing the connection, choosing a shared platform, and maintaining the linked hybrid cloud environment is essential for hybrid clouds. Links. To construct a hybrid cloud, all that has to be done is link a private network to the Internet and utilize public cloud services.
55. How are filtering and application control handled by FortiGate?
Ans:
Numerous apps can produce network traffic that FortiGates can identify. What should be done with the application traffic is specified by application control sensors.
56. What does email security serve to accomplish?
Ans:
- The process of preventing illegal access, loss, or compromise to email accounts and conversations is known as email security.
- Organizations can improve the security of their email correspondence by implementing policies and using tools to defend against malicious organizations, malware, and phishing attempts.
57. How does Fortinet handle the difficulties of protecting remote work settings?
Ans:
Robust and safe communication can be provided via FortiAP, controlled remotely by a FortiGate next-generation firewall (NGFW). Wireless communication is protected across the Internet by an encrypted tunnel from the access point, and the firewall’s security policies can be applied.
58. Describe how to set up an SSL VPN on a FortiGate.
Ans:
Set up the SSL VPN configuration:
- Select SSL-VPN Settings under VPN.
- Choose wan1 under Listen on Interface(s).
- Assign port 10443 for listening.
- You can limit access to particular hosts by configuring Restrict Access and providing the addresses of the hosts permitted to join this VPN.
- Select the Server Certificate certificate.
59. What advantages does FortiSIEM offer?
Ans:
FortiSIEM combines visibility, correlation, automatic reaction, and remediation in a single, scalable solution. To efficiently release resources, enhance breach detection, and even prevent intrusions, it lessens the complexity of managing network and security operations.
60. How does Fortinet support multi-cloud security?
Ans:
- Secure, high-performance access to apps operating in multi-cloud and hybrid cloud environments is established with Fortinet Secure SD-WAN.
- Fortinet Secure SD-WAN: Uses Secure Networking to streamline multi-cloud security and cloud on-ramp for users, combining networking and security features.
61. What are the benefits of Fortinet’s security fabric?
Ans:
The network can divide network segments, automatically identify and dynamically isolate compromised devices, update rules, distribute new policies, and eliminate malware with the help of the Security Fabric. The Security Fabric covers the entire attack surface, which also gives you total network visibility.
62. What is the objective of FortiNAC in network access control?
Ans:
- Three vital features for IoT device security are made possible by Network visibility to observe every device and user as they join the network.
- Network control to limit where devices can travel on the network. Automated reaction to reduce days to seconds in response time to occurrences.
63. What is FortiGate’s response to DDoS attacks?
Ans:
FortiDDoS reduces impact while preserving corporate operations. FortiDDoS uses 100% of its capacity to stop malicious bot activity without banning bots—excellent small-packet rate detection skills. The only fully autonomous DDoS mitigation solution that doesn’t require vendor or user NOC interaction during attacks is called FortiDDoS.
64. What is FortiSwitch used for?
Ans:
- The intelligent scalability that FortiSwitch managed switches provide is essential for maintaining minimal supervision in your expanding company, educational institution, or branch office.
- Connect in a device, and FortiSwitch will determine how to function best and protect the network based on that device’s needs.
65. What function does FortiAP serve in a wireless network?
Ans:
The secure WLAN access points in the FortiAP family can be used indoors, outdoors, and remotely. They can all be controlled and secured via the well-known FortiGate web interface, with Fortinet integrated security and wireless LAN management methods.
66. How does FortiGate handle web filtering?
Ans:
A firewall shields your network from outside dangers so that computers and internal services are not exposed, while a web filter restricts access to particular kinds of online information. Web filters and conventional firewalls function at distinct OSI (Open System Interconnection) model layers.
67. What is integration in SIEM?
Ans:
- Organizations may log data monitored for potential risks and provide a more effective response when a breach happens by integrating SIEM with other systems.
- Additionally, SIEM integrations assist businesses in promptly identifying criminal behavior so they can take appropriate action before more harm is done.
68. What distinguishes a firewall from a SIEM?
Ans:
The functionality and breadth of a firewall and an SIEM are where they fundamentally diverge. A SIEM is largely concerned with log and event management, security incident detection, and response, whereas a firewall is primarily concerned with network traffic control and access management.
69. How is the Fortinet threat map implemented?
Ans:
An automated breach protection system called Threat Detection Service (TDS) keeps an eye out for attacks, vulnerabilities, and persistent threats on your network. It offers defense against valid risks, protecting client information and thwarting malware, unauthorized access, and unauthorizedly.
70. Describe how FortiGate’s dynamic routing works.
Ans:
Dynamic routing usually entails defining neighbors and peer routers that communicate their network topology and routing updates with each other instead of manually defining static routes, which could be more scalable. Popular routing protocols include distance vector, link state, and path vector.
71. How does Fortinet DDoS work?
Ans:
- FortiDDoS employs 100% inspected small-packet rate detection capabilities to stop harmful bot activity without turning off bots.
- The only fully autonomous DDoS mitigation solution that doesn’t require vendor or user NOC interaction during attacks is called FortiDDoS.
72. What security issues with industrial control systems (ICS) can Fortinet address?
Ans:
Selecting the best solutions for corporate IT infrastructures—which span everything from the data center to the network edge to the cloud—enables protection. Using technologies like FortiAP, FortiPresence, FortiSwitch, and FortiCamera, the Fortinet solution is concentrated on safeguarding the industrial zone.
73. What is Fortinet FortiGate used for?
Ans:
Fortinet FortiGate NGFWs combine the superior security features previously described with the protection of the five different types of firewalls. They can be used as hardware or software and are scalable anywhere, including campuses, data centers, distant offices, and cloud environments.
74. How does FortiDDoS defend against attacks that cause a distributed denial of service?
Ans:
FortiDDoS reduces impact while preserving corporate operations. FortiDDoS inhibits malicious bot activity without blocking bots, employing 100% inspected small-packet rate detection capabilities. The only fully autonomous DDoS mitigation solution that doesn’t require vendor or user NOC interaction during attacks is called FortiDDoS.
75. Why are directory services and user authentication necessary in a network?
Ans:
User authentication enables safe access to accounts and networks while identifying confirmed individuals. It is a security measure to prevent hackers or unauthorized users from accessing private information and resources.
76. What is a wireless access point’s purpose and role?
Ans:
A wireless access point (WAP) networking device enables wirelessly capable devices to join a wired network. Installing WAPs to link any computer or device in your network is more straightforward than using wires and cables.
77. What are the primary components of Fortinet’s Security Rating Service?
Ans:
The three primary security scores offered by the service are Security Posture, Fabric Coverage, and Optimization. This OOptimization is a concise overview of the three primary areas of security concentration inside the Security Fabric.
78. How does Forti Gate support high-performance threat detection and prevention?
Ans:
- Forti Gate enterprise firewalls use purpose-built security processors (SPUs) to provide scalable performance for advanced security services, including Threat.
- Protection, SSL inspection, and ultra-low latency for protecting internal segments and mission-sensitive situations.
79. Describe how FortiGate and FortiManager are integrated.
Ans:
Make all necessary modifications to the policies and objects in the Policy & Objects module of the FortiManager after first importing the policies from the device. Reimporting policies will be necessary to resynchronize the policies and objects after making changes directly on the FortiGate device.
80. How does FortiGate handle SSL/TLS decryption and inspection?
Ans:
After acting as a bridge to connect to the SSL server, the FortiGate examines and decrypts content to identify security risks and take appropriate action. After that, it transfers the content to the intended recipient after re-encrypting it using a certificate that FortiGate has signed.
81. Describe how FortiGate’s virtual domains work.
Ans:
- A FortiGate can be divided into two or more separate virtual units using Virtual Domains (VDOMs).
- VDOMs can offer unique security rules for every linked network and, when using NAT mode, unique configurations for VPN and routing services.
82. What does FortiToken Mobile want to achieve?
Ans:
An event-based, time-based, and OATH-compatible One Time Password (OTP) generation app for mobile devices is called FortiToken Mobile. It is the client side of Fortinet’s incredibly cost-effective, highly secure, and easy-to-use and operate solution for your strong authentication requirements.
83. What security features does Fortinet SASE provide to stave against attacks from the internet?
Ans:
FeaaS FortiOS-powered, the FortiSASE FWaaS is a cloud-based service that offers hyperscale capabilities for next-generation firewalls (NGFWs), such as DNS security, web filtering, intrusion prevention systems (IPS), and advanced threat protection (ATP).
84. What is CASB Fortinet?
Ans:
- To enforce security regulations when users use cloud-based resources, software or hardware known as a cloud access security broker (CASB) is placed between users and their cloud service.
- Remember that CASB differs from the firewalls businesses employ to monitor and filter their networks.
85. How does FortiGate support IPv6 security?
Ans:
The NAT64 security policy accepts the packet once it reaches the FortiGate internal interface. The FortiGate unit converts the packets’ source and destination addresses from IPv6 address 64:ff9b::172.20. 120.12 to IPv4 address 172.20. 120.12. address of the packets to 172.2.
86. Describe how FortiEDR contributes to endpoint security.
Ans:
As a component of the Fortinet SecOps Platform, FortiEDR proactively reduces the attack surface, guards against malware infection quickly identify and neutralizes possible threats, and uses customizable playbooks to automate response and remediation processes on both modern and legacy Windows, macOS, and Linux devices.
87. What are the main characteristics of FortiMail’s email communication security?
Ans:
Characteristics and Advantages
- AI-Powered Protection. Uses FortiGuard AI-powered Security Services developed & optimized by FortiGuard Labs.
- Protection against Zero Days. Integrates with FortiSandbox to analyze files and find zero-day threats and advanced malware.
- Protection for Microsoft 365.
88. How can Fortinet enable safe SD-WAN deployments?
Ans:
Global, cloud-first, security-conscious, and hybrid workforce organizations are all supported by Fortinet Secure SD-WAN. Our method of Secure Networking combines sophisticated routing, ZTNA application gateway, next-generation firewall (NGFW), and SD-WAN functionalities into a single operating system.
89. Explain how FortiWeb contributes to web application security.
Ans:
- FortiWeb is a web application firewall (WAF) that assists in preserving regulatory compliance by defending online applications and APIs against attacks that use known and new exploits.
- FortiWeb uses machine learning to create a model of every application, protecting it against both known vulnerabilities and unknown threats.
90. What is the objective of FortiSandbox in threat intelligence?
Ans:
FortiSandbox scans files, webpages, URLs, and network traffic to detect malicious activities, including zero-day threats. It then employs sandboxing technology to examine questionable files in a safe virtual environment.
91. How does FortiManager make managing devices in a big network easier?
Ans:
A single console to obtain insight and orchestration while managing and monitoring massive firewall setups and security policies. Use device designs and best-practice templates to install secure network technologies like SD-WAN quickly and widely.
92. What role does FortiDeceptor play in threat identification?
Ans:
- The purpose of Forti Deceptor is to proactively block external and internal threats before they cause any serious harm and to deceive, expose, and eradicate them early in the assault-kill chain.
- It can be purchased as a virtual appliance, piece of hardware, or in a ruggedized form perfect for challenging conditions.
93. How does Fortinet handle the difficulties associated with Internet of Things (IoT) security?
Ans:
With FortiNAC, our network access control product, Fortinet offers these features. FortiNAC provides the visibility, control, and automatic response required to offer security in an IoT-enabled world when fully integrated into the Security Fabric.
94. Explain how FortiDDoS defends against assaults at the application layer.
Ans:
An inline, specially designed solution called FortiDoS guards against attacks that overload a target with packets and deplete its resources, rendering the network, applications, or services inaccessible to authorized traffic.
95. How does FortiMail handle email encryption?
Ans:
- The FortiMail unit automatically uses the public key to encrypt the message when there is a policy match.
- The recipient can decrypt the message irrespective of their mail client, operating system, or user privilege.
- The recipient can read and decrypt the secure message using a browser-based mechanism.
96. Describe how FortiGate and FortiWeb work together to secure web applications.
Ans:
- FortiWeb is a web application firewall (WAF) that assists in preserving regulatory compliance by defending online applications and APIs against attacks that use known and new exploits.
- FortiWeb uses machine learning to create a model of every application, protecting it against both known vulnerabilities and unknown threats.
97. What is the goal of Fort Insight’s user and entity behavior analytics (UEBA)?
Ans:
- Analytics of User and Entity Behavior (UEBA)Fortis Insight provides total resource and data visibility by monitoring endpoint activity, resource access, and data mobility.
- It recognizes dangerous behavior and policy infractions and takes action before they result in security breaches.
98. In what ways does FortiClient assist with endpoint security?
Ans:
The Protection of AI-based next-generation antivirus (NGAV), endpoint quarantine, and application firewall, in addition to supporting cloud sandbox, USB device control, and ransomware protection, the Unified FortiClient agent offers expanded security capabilities.
99. Explain how FortiGate helps secure apps running on cloud servers.
Ans:
- Cloud security uses various protocols, each with pros and cons. SSH, IPSec, and SSL/TLS are the most widely used protocols.
- The most used protocol for online applications is SSL/TLS. It offers good security and is rather simple to set up.
100. What are Forti NAC’s salient characteristics in terms of network access control?
Ans:
Switches and wireless equipment from various suppliers can have segmentation policies implemented by changing the configurations with FortiNAC. These dynamic controls expand the Fortinet Security Fabric’s reach in heterogeneous environments.






