
OWASP enhances software security through community-driven efforts. It provides resources to mitigate web application vulnerabilities, fostering a safer online environment. The project focuses on common threats like injection attacks and cross-site scripting. OWASP promotes best practices for developers and security professionals alike. Its collaborative approach aims to strengthen defenses against evolving cyber threats.
1. What is OWASP?
Ans:
OWASP, or Open Web Application Security Project, is a non-profit organization dedicated to enhancing software security through resources, tools, and guidelines. It educates about prevalent security risks and advocates best practices. It is notable for maintaining the OWASP Top Ten and identifying critical web app security threats. Projects like WebGoat and ZAP provide educational and testing resources. We aim to bolster awareness and standards for global web application security.
2. Describe IPSEC.
Ans:
IPSEC stands for Internet Protocol Security, ensuring secure IP communication. It is commonly utilized in VPNs to establish secure connections over networks. IPSEC operates at the network layer of the OSI model, offering encryption and tunneling. It is vital for safeguarding data during transmission, ensuring privacy and integrity. It encompasses a suite of protocols facilitating secure communication across networks.
3. What are OWASP WebGoat and WebScarab?
Ans:
- OWASP WebGoat: An intentionally vulnerable web application for educational purposes.
- Allows users to practice identifying and exploiting security vulnerabilities in a controlled environment.
- Aimed at educating developers and security professionals about web app security flaws.
- OWASP WebScarab: A web security testing tool intercepting and analyzing HTTP/HTTPS traffic.
- Facilitates the identification and resolution of security issues in web applications.
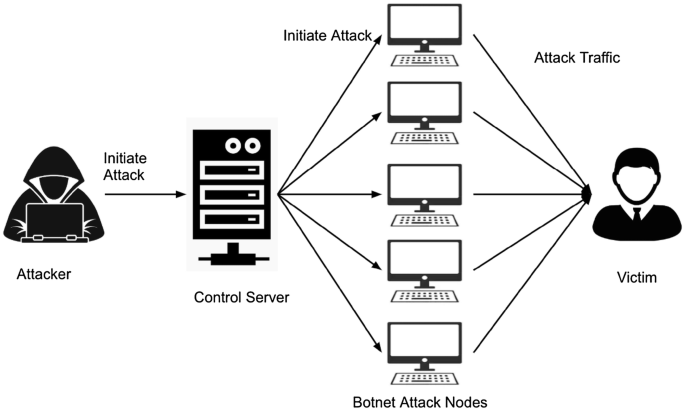
4. What is a botnet?
Ans:
A botnet is a network of compromised devices controlled remotely by a single entity. Botnets are typically employed for malicious activities such as DDoS attacks or spam dissemination. Infected devices, termed bots or zombies, execute commands from a central controller. Botnets often arise from malware infections or the exploitation of vulnerabilities. When wielded maliciously, botnets pose significant threats to network security and system integrity. Addressing botnets necessitates robust cybersecurity measures and proactive defence strategies.
5. Describe the Owasp risk rating system.
Ans:
The OWASP risk rating system evaluates security risks based on likelihood and impact. Likelihood denotes the probability of a risk materializing, while impact signifies its potential harm. Categorizes risks to prioritize security efforts, focusing on addressing critical vulnerabilities foremost. Provides a structured approach to risk assessment, aiding in resource allocation and mitigation planning. It enables organizations to allocate resources effectively and mitigate vulnerabilities efficiently.
6. What does OSI stand for?
Ans:
- OSI, or Open Systems Interconnection, is a conceptual network communication framework.
- Standardizes communication protocols to facilitate interoperability across systems and devices.
- Divides network communication into seven layers, each serving distinct functions.
- Ranges from physical transmission to application-specific interactions.
- OSI model layers interact with adjacent layers to ensure seamless data transmission.
7. What is OWASP ESAPI?
Ans:
- OWASP ESAPI, or Enterprise Security API, offers security-related functions and libraries.
- Designed to assist developers in building secure applications with standardized security practices.
- Mitigates common vulnerabilities like injection attacks and cross-site scripting.
- Provides functionalities such as input validation, output encoding, and cryptographic operations.
8. What is the Difference between symmetric and asymmetric encryption?
Ans:
| Feature | Symmetric Encryption | Asymmetric Encryption | |
| Key Usage |
Same key for encryption and decryption |
Different keys for encryption and decryption (public and private keys) | |
| Efficiency | Faster and more efficient for large volumes of data | Slower and less efficient, especially for large volumes of data | |
| Key Distribution |
Requires secure distribution of the key |
Public keys can be freely distributed; private keys must be kept secret | |
| Algorithms | Examples include AES, DES, 3DES | Examples include RSA, ECC |
9. Describe the OWASP ESAPI’s core design.
Ans:
The core design of OWASP ESAPI emphasizes reusable security components. It implements multiple layers of defence following the “security in depth” principle. It prioritizes simplicity and ease of use for developers, promoting widespread adoption. It encapsulates secure coding practices through standardized APIs and modules. Modules encompass diverse security functionalities like input validation and cryptographic operations.
10. How can forced browsing be prevented from affecting web applications?
Ans:
- Utilize secure session management techniques to track and validate user sessions effectively.
- Employ comprehensive error-handling mechanisms to prevent information leakage.
- Ensure sensitive resources are inaccessible via predictable paths or direct URLs.
- Employ server-side validation to validate and authorize requests before processing.
- Regularly monitor and analyze application access logs to promptly detect and respond to suspicious activities.
11. What is an injection in OWASP?
Ans:
- Injection in OWASP refers to inserting malicious code into a system, commonly seen in SQL or LDAP injection.
- It exploits vulnerabilities in input validation, allowing attackers to manipulate data or execute unauthorized commands.
- OWASP emphasizes mitigating injection attacks through secure coding practices and input validation.
- Proper sanitization of user input and using parameterized queries are crucial prevention measures.
12. What is broken authentication?
Ans:
Broken authentication refers to vulnerabilities that compromise the authentication process, allowing unauthorized access. Common issues include weak passwords, session management flaws, and inadequate security controls. Attackers exploit these weaknesses to hijack sessions, impersonate users, or gain unauthorized access to accounts. Mitigation involves implementing strong authentication mechanisms like multi-factor authentication and secure session management.
13. How can visitors to the OWASP website locate these vulnerabilities?
Ans:
- Users can find vulnerabilities on the OWASP website by exploring the resources provided, such as guides, tools, and documentation.
- The OWASP Top Ten list highlights the most critical web application security risks as a starting point for vulnerability awareness.
- OWASP projects like WebGoat and Juice Shop offer interactive platforms for users to practice identifying and mitigating vulnerabilities.
- The OWASP website provides documentation and articles on a wide range of topics, including common vulnerabilities and best practices.
14. Does OWASP provide any guides for web security testing?
Ans:
Yes, OWASP provides comprehensive guides for web security testing to help developers and security professionals assess and improve the security of their applications. The OWASP Testing Guide covers various web application security testing aspects, including surveillance, mapping, discovery, and exploitation. It offers detailed methodologies and techniques for identifying vulnerabilities like injection, XSS, CSRF, and authentication flaws.
15. What is the primary goal of the Web Security Testing Guide?
Ans:
- The primary goal of the Web Security Testing Guide is to provide a comprehensive resource for testing the security of web applications.
- It aims to equip security professionals and developers with the knowledge and tools to identify and mitigate common security vulnerabilities.
- The guide covers various testing methodologies, tools, and techniques for assessing the security posture of web applications.
16. What is the Mobile Security Testing Guide?
Ans:
- The Mobile Security Testing Guide is a comprehensive resource OWASP provides that assesses mobile application security.
- It aims to equip security professionals and developers with the knowledge and tools to identify and mitigate security vulnerabilities in mobile apps.
- The guide covers various testing methodologies, tools, and mobile application security testing techniques.
- It addresses common security challenges mobile apps face, such as insecure data storage, improper session management, and insecure communication.
17. What is the Z Attack Proxy?
Ans:
- The Z Attack Proxy (ZAP) is an open-source web application security testing tool developed by OWASP.
- It is designed to help security professionals identify security vulnerabilities in web applications during development and testing.
- ZAP can perform various security tests, including automated scanning, manual testing, and fuzzing.
- It provides features for intercepting and modifying HTTP requests and responses, enabling users to manipulate web application behaviour for testing purposes.
18. What is OWASP ZAP?
Ans:
OWASP ZAP (Zed Attack Proxy) is an open-source security testing tool developed by the Open Web Application Security Project (OWASP). It is designed to help security professionals identify vulnerabilities in web applications by performing automated and manual security testing. ZAP offers passive and active scanning, spidering, and fuzzing to detect vulnerabilities like XSS, SQL injection, and CSRF.
19. What is offered by OWASP ZAP for the two kinds of scanning?
Ans:
OWASP ZAP provides both passive and active scanning capabilities for identifying security vulnerabilities in web applications. Passive scanning involves analyzing the traffic between the client and server to detect potential vulnerabilities without actively interacting with the application. ZAP’s passive scanning feature can detect missing security headers, sensitive information exposure, and insecure configurations.
20. What are the features of OWASP ZAP?
Ans:
- OWASP ZAP (Zed Attack Proxy) offers a wide range of web application security testing and analysis features.
- It provides automated and manual testing capabilities, allowing users to identify vulnerabilities such as XSS, SQL injection, and CSRF.
- ZAP offers a user-friendly interface with customizable dashboards and reporting features for analyzing security findings.
- It supports scripting and automation, enabling users to create custom security tests and integrate ZAP into their development workflows.
21. How to access the features of OWASP ZAP?
Ans:
To access OWASP ZAP features, launch the application and explore its user interface. Features are organized into tabs like “Home,” “Alerts,” and “History.” Automation capabilities are available via ZAP’s API. Extensive documentation and tutorials are provided to help users utilize its features effectively. The interface also includes options for setting up scans and managing configurations, enhancing the security testing process.
22. Describe bug bounty.
Ans:
Bug bounty programs incentivize security researchers to discover and report vulnerabilities. They offer rewards such as cash, recognition, or other incentives for identified vulnerabilities. These programs serve as proactive measures for identifying and addressing security flaws before exploitation. They also encourage collaboration between organizations and the security community and contribute to improving overall security posture by addressing vulnerabilities promptly.
23. Explain cross-site scripting (XSS).
Ans:
- When malicious scripts are injected into websites that are viewed by other users, this is known as cross-site scripting (XSS).
- These programs can deface websites, take over sessions, and steal confidential data.
- Insufficient input validation is a common cause of XSS vulnerabilities.
- Implementing a Content Security Policy (CSP), output encoding, and input sanitization are examples of prevention techniques.
24. How does CSRF work, and what prevention methods?
Ans:
- Cross-site request forgery (CSRF) involves tricking a user’s browser into making unauthorized requests to a different website where the user is authenticated. Attackers exploit the user’s active session to perform malicious actions.
- Prevention methods include implementing anti-CSRF tokens, verifying the origin of requests, and using SameSite cookies.
25. What is the purpose of Content Security Policy (CSP)?
Ans:
Content Security Policy (CSP) is a security standard designed to prevent XSS attacks by specifying trusted sources for content like scripts, stylesheets, and images. It defines directives that instruct the browser on which resources are allowed to load. By enforcing these rules, CSP reduces the risk of executing malicious scripts injected through XSS vulnerabilities. Additionally, CSP helps in mitigating other web security risks by controlling resource loading and interactions.
26. What is the concept of SQL injection and how can it be mitigated?
Ans:
SQL injection is a web security vulnerability that allows attackers to execute malicious SQL queries through input fields, potentially leading to unauthorized database access or manipulation. To mitigate this risk, use parameterized queries to prevent direct SQL code execution, validate input to filter out harmful data, and apply the principle of least privilege to restrict database access. Additionally, regularly update and patch database systems to address known vulnerabilities.
27. What are the common security vulnerabilities in APIs?
Ans:
- Common security vulnerabilities in APIs include insufficient authentication and authorization mechanisms, insecure data transmission, and improper input validation.
- Additionally, APIs may suffer from vulnerabilities like injection attacks, broken authentication, and excessive data exposure.
- Proper API security measures involve implementing authentication, authorization, encryption, and thorough input validation.
28. What is a session fixation attack and how can it be prevented?
Ans:
Session fixation attacks occur when attackers set a user’s session ID to a known value, allowing them to hijack the session once the user logs in. Prevention methods include:
- It generates a new session ID upon authentication.
- They are enforcing strict session management policies.
- Regularly rotating session tokens.
29. Describe Clickjacking and prevention methods.
Ans:
Clickjacking is a technique where attackers trick users into clicking hidden elements overlaid on legitimate content. It can be prevented by using the ‘X-Frame-Options’ header, which disallows a webpage from being embedded in iframes on other sites. Implementing ‘frame-busting’ scripts can also prevent a page from being loaded in an iframe. Another method is to use the ‘Content Security Policy (CSP)’ frame-ancestors directive. Finally, ensuring a secure ‘UI design’ that avoids obscured or layered content helps prevent clickjacking attempts.
30. What is the importance of secure password storage?
Ans:
- Secure password storage protects user credentials from unauthorized access and exploitation.
- Passwords should be hashed using strong cryptographic algorithms like bcrypt or Argon2 and salting to prevent rainbow table attacks.
- Storing passwords securely helps maintain user trust, reduces the risk of data breaches, and ensures compliance with data protection regulations.
31. What is the impact of security misconfiguration and how can it be prevented?
Ans:
- Security misconfigurations can lead to breaches, exposing sensitive data.
- Attackers exploit default settings or weak configurations to gain unauthorized access.
- Prevention involves regular audits, following security best practices, and using automated tools.
- Proper configuration ensures systems are hardened against known vulnerabilities.
- Regular updates and patches also mitigate the risk of misconfiguration-related exploits.
32. What is the Difference between penetration testing and vulnerability scanning?
Ans:
- Penetration testing involves simulated attacks to identify vulnerabilities and assess their exploitability.
- Vulnerability scanning is an automated process that detects and reports weaknesses in systems or networks.
- Penetration testing goes beyond scanning by attempting to exploit vulnerabilities to assess their impact.
- Vulnerability scanning is usually broader in scope, covering a wide range of systems and applications.
- Penetration testing provides actionable insights into security posture, whereas scanning primarily identifies vulnerabilities.
33. What is the role of encryption in data confidentiality?
Ans:
Encryption transforms data into an unreadable format to ensure confidentiality. It prevents unauthorized access, even if data is intercepted. Properly implemented algorithms are mathematically secure and resistant to decryption without the key. It also helps maintain data integrity and authenticity. Encryption is crucial for protecting data at rest, in transit, and in use.
34. What is a zero-day vulnerability and what is its impact?
Ans:
A zero-day vulnerability is a flaw unknown to software developers and security vendors. Attackers exploit zero-day vulnerabilities before a fix or patch is available. This can lead to widespread security breaches, compromising data integrity and confidentiality. The impact can be severe, causing financial losses, reputation damage, and legal consequences.
35. How do security headers enhance web security?
Ans:
- Security headers provide additional layers of protection against various web-based attacks.
- They control browser behavior to mitigate risks such as XSS, Clickjacking, and MIME sniffing.
- Headers like Content Security Policy (CSP) specify which resources can be loaded on a webpage, reducing the risk of XSS attacks.
- HTTP Strict Transport Security (HSTS) enforces secure connections over HTTPS, preventing downgrade attacks.
- X-Frame-Options header prevents Clickjacking by restricting how a webpage can be embedded in an iframe.
36. What is the significance of input validation?
Ans:
- Input validation ensures that the user data entered meets the expected criteria and format.
- It prevents injection attacks, such as SQL injection and XSS, by sanitizing user inputs.
- Proper input validation also helps maintain data integrity and consistency.
- Without it, attackers can exploit vulnerabilities by injecting malicious code or data.
- Input validation is crucial for protecting against various security threats in web applications.
- Implementing robust input validation mechanisms is a fundamental security best practice.
37. What is privilege escalation in web security?
Ans:
Privilege escalation occurs when a user gains higher access privileges than intended. Attackers exploit vulnerabilities to elevate their privileges, gaining unauthorized access to sensitive resources. This can lead to data breaches, unauthorized modifications, or complete system compromise. Prevention involves implementing least privilege principles and strong access controls.
38. How can security headers be implemented in web applications?
Ans:
Security headers are HTTP response headers that enhance web security by controlling browser behavior. They help prevent attacks such as XSS, Clickjacking, and MIME sniffing. Implementing security headers involves configuring web servers or application frameworks to include them in HTTP responses. Common security headers include Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and X-Frame-Options.
39. What are the risks associated with third-party libraries in web development?
Ans:
- Third-party libraries introduce potential security vulnerabilities into web applications.
- Attackers can exploit libraries’ vulnerabilities to compromise the entire application’s security.
- Risks include outdated libraries with known vulnerabilities, malicious code injections, and supply chain attacks.
- Lack of proper vetting and monitoring of third-party dependencies can lead to security breaches.
40. What is the importance of secure coding practices?
Ans:
- Secure coding practices help mitigate vulnerabilities and reduce the risk of security breaches.
- They involve following coding standards, using secure APIs, and implementing input validation.
- Secure coding practices address common security threats like injection attacks, XSS, and buffer overflows.
- Proper error handling and logging also contribute to application security.
- Integrating security into the software development lifecycle ensures that security considerations are addressed from the outset.
41. How do security frameworks enhance web security?
Ans:
Security frameworks provide pre-built security measures, offer standardized solutions to common threats, help developers implement security best practices, and streamline the process of securing web applications. By using frameworks, developers can reduce the risk of vulnerabilities. Overall, security frameworks contribute to a more robust defence against cyber threats.
42. What is the role of HTTPS in web communication security?
Ans:
- Data sent between the client and server is encrypted using HTTPS.
- It ensures confidentiality and integrity of data.
- HTTPS also authenticates the server’s identity.
- This prevents eavesdropping, tampering, and man-in-the-middle attacks.
- HTTPS is crucial for securing sensitive information over the internet.
- It establishes a secure and encrypted connection, enhancing web communication security.
43. What is DNS spoofing and what measures can prevent it?
Ans:
- DNS spoofing involves manipulating DNS resolution to redirect users to malicious sites.
- Prevention measures include DNSSEC (Domain Name System Security Extensions).
- DNSSEC adds digital signatures to DNS records, verifying their authenticity.
- Using reputable DNS servers and implementing DNS filtering can mitigate risks.
- Regularly updating DNS software and monitoring DNS traffic are also essential.
44. What is the concept of data leakage and how can it be prevented?
Ans:
Data leakage involves the unauthorized exposure or transmission of sensitive information. Prevention measures include implementing access controls and encryption and conducting regular audits to detect vulnerabilities and gaps. Employees should also be educated about data security best practices and utilize Data Loss Prevention (DLP) solutions to monitor and prevent data leaks.
45. What is the importance of validation in web forms?
Ans:
- Validation ensures that input data meets specified criteria.
- It helps prevent injection attacks like SQL injection and XSS.
- Validating input reduces the risk of data corruption and manipulation.
- Proper validation enhances user experience by providing prompt feedback.
- It improves data integrity and overall security of web applications.
- Effective validation is essential for maintaining the integrity and security of web forms.
46. What is the threat of MITM attacks to web security?
Ans:
MITM attacks intercept and manipulate communication between two parties. Attackers can eavesdrop, tamper, or inject malicious content into data transmissions. MITM attacks pose a significant risk to sensitive information, including credentials and financial data. They can lead to data theft, unauthorized access, and compromised privacy.
47. What are the limitations of security through obscurity?
Ans:
Security through obscurity relies on hiding system details to deter attackers. However, it could be a more robust security measure on its own. Relying solely on obscurity can lead to a false sense of security. It doesn’t address underlying vulnerabilities or protect against determined attackers. Instead, a layered approach incorporating obscurity alongside robust security measures is more effective.
48. How can brute force attacks be prevented?
Ans:
- Putting in place account lockout procedures following several unsuccessful attempts to log in.
- Using CAPTCHA or reCAPTCHA challenges to differentiate humans from automated scripts.
- Employing rate limiting to restrict the number of login attempts within a specific timeframe.
- Encouraging users to choose strong, unique passwords and enforcing password complexity requirements.
- Applying multi-factor authentication (MFA) to bolster security even more.
49. What is the importance of security awareness training?
Ans:
- Security awareness training educates employees about cybersecurity risks and best practices.
- It helps employees recognize phishing attempts, social engineering tactics, and other threats.
- Training promotes a security-conscious culture within an organization.
- Educated employees are more likely to follow security policies and procedures.
- Security awareness training reduces the likelihood of human error leading to security breaches.
50. What is the principle of least privilege in web security?
Ans:
Least privilege restricts users’ access rights to only what is necessary for their roles. It minimizes the potential impact of security breaches or insider threats. By limiting privileges, organizations reduce the attack surface and mitigate risks. Implementing the least privilege requires careful access control management. Regularly reviewing and updating access permissions is crucial.
51. What is the role of security tokens in web authentication?
Ans:
A security token is a piece of data used for authentication to validate a user’s identity. Often generated by servers, tokens can be session-based or persistent. They enhance security by reducing reliance on passwords and are commonly employed in multi-factor authentication systems. Tokens can also include one-time passwords or cryptographic keys for additional security. They add an extra layer of protection against unauthorized access and ensure that only authenticated users gain access.
52. What is the role of two-factor authentication (2FA) in web security?
Ans:
- Two-factor authentication (2FA) adds extra security layers.
- Users provide two different authentication factors.
- Enhances security, reducing unauthorized access risks.
- Mitigates impacts of password breaches and phishing.
- Bolsters authentication process for web services.
53. What is the importance of secure session management?
Ans:
- It is crucial for maintaining user sessions securely.
- It involves generating, maintaining, and ending sessions securely.
- It helps prevent session hijacking and fixation attacks.
- Ensures confidentiality and integrity of session data.
- It is essential for protecting user privacy and sensitive information.
- Contributes to overall web app security.
54. What are the benefits of secure coding standards?
Ans:
- Promotes consistent and secure development practices.
- It helps developers create less vulnerable code.
- Reduces security breach and data leak risks.
- Improves code readability, maintainability, and collaboration.
- Acts as a preventive measure against common security issues.
- Enhances overall software security posture.
55. What is a buffer overflow vulnerability and how can it be exploited?
Ans:
It occurs when a program writes data beyond allocated buffers. It can overwrite adjacent memory, causing erratic behavior. It is exploited to execute arbitrary code, gain unauthorized access, or crash systems. It is critical due to potential severe security breaches. Proper input validation and buffer size checks are key in prevention. Mitigation strategies are crucial.
56. What is the significance of security logging and monitoring?
Ans:
Captures system events and actions. Monitoring aids in detecting suspicious or malicious activities. Provides an audit trail for forensic analysis and compliance. It helps identify security breaches, insider threats, and system weaknesses. Continuous monitoring improves incident response and reduces threat dwell time. It is integral to a robust security posture.
57. What is the Difference between vulnerability assessment and security audit?
Ans:
- Vulnerability assessment identifies and quantifies system vulnerabilities.
- Focuses on pinpointing weaknesses attackers could exploit.
- Security audit evaluates the correct implementation of security controls.
- Verifies compliance with policies, regulations, or standards.
- While vulnerability assessment identifies flaws, audits assess overall security posture.
- Both are essential for comprehensive security strategies.
58. What is the role of the OWASP Top Ten list in prioritizing security efforts?
Ans:
- Identifies critical web app security risks.
- Framework for prioritizing security efforts based on prevalent threats.
- It helps allocate resources effectively to mitigate high-priority risks.
- Guides developers in implementing proper security measures.
- The reference point for security testing and vulnerability management.
- Focuses organizations on addressing pressing security concerns.
59. What is the concept of a side-channel attack and what are its implications?
Ans:
It targets a system’s physical implementation, exploits leaked information through side channels, compromises cryptographic keys, passwords, or sensitive data, is hard to detect, and can bypass traditional security measures. Its implications include the potential compromise of confidential information. Mitigation requires careful design and implementation.
60. What is the role of secure configuration management?
Ans:
- It involves maintaining proper settings and configurations.
- Ensures systems are configured securely to minimize vulnerabilities.
- Reduces attack surface and strengthens overall security posture.
- Regularly reviews and updates configurations to address emerging threats.
- Enforces security policies and compliance requirements.
- Critical for maintaining security and integrity of IT infrastructure.
61. How does defense-in-depth contribute to web security?
Ans:
- Defence-in-depth involves layering numerous security measures.
- It adds redundancy, decreasing the likelihood of successful attacks.
- By erecting multiple barriers, it complicates attackers’ efforts to breach systems.
- It guarantees that others can still safeguard the system if one security measure fails.
- This strategy enhances resilience and overall security posture significantly.
- Ultimately, defence-in-depth minimizes the potential impact of security breaches.
62. Explain the concept of XSS.
Ans:
XSS is a web vulnerability where attackers inject malicious scripts. These scripts execute within victims’ browsers, posing threats. They can steal sensitive data or execute unauthorized actions. XSS is pervasive in web applications and requires careful mitigation. Effective prevention involves robust input validation and output encoding. Implementing these measures is crucial for protecting against XSS attacks.
63. How does CSRF work?
Ans:
- CSRF exploits user trust to execute unwanted actions.
- Attackers deceive browsers into performing actions without user consent.
- Users remain unaware as attackers craft malicious URLs.
- Visiting vulnerable sites triggers unintended actions.
- Preventive strategies include employing CSRF tokens.
- These measures help mitigate the risks associated with CSRF attacks.
64. Describe Clickjacking.
Ans:
Attackers overlay invisible elements on top of legitimate ones, tricking users into interacting with these hidden elements and executing malicious actions. To prevent this, use frame-busting scripts and implement X-Frame-Options headers to mitigate clickjacking risks. These measures help ensure that only authorized content is displayed and interacted with. Regularly review and test these protections to address new and evolving clickjacking techniques.
65. How does ransomware work?
Ans:
- Ransomware is malicious software that encrypts files or locks down systems, demanding payment (usually in cryptocurrency) for decryption or restoration of access.
- It typically enters a system through phishing emails or malicious downloads. Once activated, it encrypts files or systems, rendering them inaccessible until the ransom is paid.
66. What is the impact of security misconfiguration?
Ans:
- Security misconfiguration exposes system vulnerabilities.
- Default or unnecessary settings may remain enabled, inviting exploitation.
- Attackers leverage these misconfigurations to gain access.
- Regular security audits aid in identifying and rectifying misconfigurations.
- Proper configuration minimizes attack surfaces and bolsters security defences.
67. What is the concept of a side-channel attack?
Ans:
- A side-channel attack exploits unintended information leakage from a system. Rather than targeting the system directly, it observes its physical characteristics, like power consumption or timing.
- These leaks can reveal sensitive information, such as cryptographic keys or passwords. Side-channel attacks are often more subtle and can be challenging to detect compared to traditional attacks.
68. What is a zero-day vulnerability?
Ans:
A zero-day vulnerability represents a flaw within a system or software. Neither the software vendor nor users are aware of its existence. Attackers exploit these vulnerabilities before patches are developed or deployed. This poses a significant challenge as defenders need more time to prepare. Effective patching and proactive security measures are essential to counter these risks.
69. Explain the concept of phishing.
Ans:
Phishing is a cyber-attack where attackers impersonate legitimate entities to trick users into revealing sensitive information like passwords or financial data. This is commonly done through email, text messages, or fake websites. By exploiting human psychology and trust, attackers deceive users into taking actions that benefit them. The goal is to gain unauthorized access to confidential information.
70. Why is input validation important?
Ans:
- It acts as a barrier against injection-based assaults like SQL injection.
- Validating input aids in the identification and rejection of malicious data.
- Without proper validation, attackers exploit vulnerabilities with ease.
- Implementing thorough input validation reduces the risk of data corruption or compromise.
- It forms a fundamental aspect of constructing secure applications.
71. What is privilege escalation?
Ans:
Privilege escalation occurs when an attacker gains higher access privileges than intended, allowing them to execute unauthorized actions. Preventing privilege escalation involves strict access control measures. Regular audits and monitoring help detect any unauthorized changes. Implementing the principle of least privilege minimizes risks. Patching known vulnerabilities promptly mitigates potential exploits.
72. What are the risks of using third-party libraries?
Ans:
- Using third-party libraries introduces risks such as vulnerabilities and dependency issues. These libraries may have security flaws that can be exploited. Regularly updating libraries helps mitigate known vulnerabilities.
- Thoroughly vetting libraries before integration is crucial. Maintaining a minimalistic approach to dependencies reduces potential attack surfaces—regular security audits and monitoring aid in detecting vulnerabilities.
73. What is defence-in-depth?
Ans:
- Defense-in-depth is a cybersecurity strategy that employs multiple layers of defence mechanisms to protect against various threats. Instead of relying solely on one security measure, it incorporates redundancy and diversity in security controls.
- By layering defences, it creates multiple barriers that adversaries must overcome, making it more difficult for them to compromise systems.
74. What is the role of HTTPS in web security?
Ans:
HTTPS verifies the server’s authenticity to prevent man-in-the-middle attacks and ensures data integrity during transmission. SSL/TLS certificates confirm the server’s identity, providing encryption for sensitive data. Implementing HTTPS is essential for maintaining secure communications, protecting user privacy, and adhering to security standards. It also boosts user trust and confidence in the website.
75. What is DNS spoofing?
Ans:
DNS spoofing involves manipulating DNS resolution to redirect traffic to malicious sites. Attackers exploit vulnerabilities in DNS protocols or compromise DNS servers. Implementing DNSSEC helps authenticate DNS responses, preventing spoofing. Using reputable DNS servers reduces the risk of spoofing attacks. They are regularly monitoring DNS traffic and aid in detecting anomalies. Implementing strong DNS security policies strengthens defences against spoofing.
76. How to prevent data leakage?
Ans:
- Data leakage can occur through various channels, including insecure storage or transmission.
- Encrypting sensitive data before storage or transmission prevents unauthorized access.
- Implementing access controls ensures that only authorized users can access data. Regular audits and monitoring help detect and mitigate data leakage incidents. Employee training on data handling best practices mitigates accidental leakage.
77. What is the significance of validation in web forms?
Ans:
Validation in web forms ensures that user input meets specified criteria, preventing injection attacks like SQL injection and XSS. It reduces the risk of data corruption or manipulation by filtering out malicious or unintended data. Proper validation safeguards the application against vulnerabilities and maintains data integrity. By enforcing strict input rules, it enhances overall security and user trust. Additionally, it helps in improving the application’s reliability and functionality.
78. What is the threat of MITM attacks?
Ans:
- Man-in-the-middle (MITM) attacks intercept and manipulate communication between two parties.
- Attackers can eavesdrop on sensitive information or modify data in transit. Implementing HTTPS with SSL/TLS encryption mitigates MITM attacks.
- Public key infrastructure (PKI) helps authenticate communication endpoints, preventing interception.
- Network monitoring detects suspicious activity indicative of MITM attacks.
79. What is security through obscurity?
Ans:
Security through obscurity relies on secrecy of design or implementation for protection. It must be a more reliable security strategy as it doesn’t address underlying vulnerabilities. Obscuring system details doesn’t prevent determined attackers from finding vulnerabilities. Proper security measures, such as encryption and access controls, offer more robust protection. Transparency and openness in security practices promote stronger defences.
80. How can brute force attacks be prevented?
Ans:
Preventing brute force attacks involves implementing strong authentication mechanisms. Enforcing complex and frequently changing passwords mitigates brute force attempts. Implementing account lockout policies after repeated failed login attempts prevents attacks. CAPTCHA challenges add an extra layer of defence against automated attacks. Two-factor authentication (2FA) enhances security by requiring additional verification steps. Monitoring login attempts and implementing rate limiting helps detect and prevent brute force attacks.
81. Describe the different approaches used in security testing.
Ans:
- Security testing typically includes static analysis, dynamic analysis, and interactive testing. Static analysis examines the source code or binaries without running the application to detect vulnerabilities.
- Dynamic analysis tests the application while running to identify issues during execution. Interactive testing blends both methods, using manual and automated tools to evaluate the application’s performance in real-world conditions.
- These approaches collectively help in identifying different types of security threats.
82. Explain the principle of least privilege.
Ans:
- The principle limits users’ access rights to what’s necessary.
- It minimizes potential damage from misuse.
- Users or components are granted minimum access required.
- This mitigates the risk of unauthorized actions.
- Implementation enhances security by containing breaches.
83. What is a security token?
Ans:
A security token is used for authentication and identity proof, adding an extra layer of security beyond passwords. It can be physical, like a hardware token, or software-generated, such as a one-time password. Security tokens require physical possession in addition to knowing a password. Common types include hardware tokens and one-time passwords. They enhance security by requiring something the user has in addition to what they know.
84. What is a DDoS attack?
Ans:
A Distributed Denial of Service (DDoS) attack overwhelms a target system or network with excessive traffic or requests, aiming to disrupt normal operations and deny service to legitimate users. It usually involves multiple compromised devices working together, making it difficult to counteract. The sheer volume of traffic generated can exhaust resources, leading to system outages and service unavailability. Effective mitigation requires robust and scalable defenses to manage and filter the incoming traffic.
85. Why is OWASP so important?
Ans:
- OWASP (Open Web Application Security Project) is vital because it offers essential guidelines, tools, and resources for enhancing web application security.
- The OWASP Top 10 is particularly influential, highlighting critical security risks that developers and security professionals should address. OWASP’s projects and standards support organizations in identifying and mitigating common vulnerabilities and promoting best practices.
- Its community-driven approach ensures that security information remains current and relevant.
86. What are the core OWASP security principles?
Ans:
- Least Privilege: Assign only necessary permissions to limit potential damage.
- Defense in Depth: Implement multiple layers of security to protect against various threats.
- Fail Securely: Design systems to manage failures securely, avoiding data exposure.
- Separation of Duties: Prevent any individual from having complete control over all aspects of a system.
- Regular Updates: Ensure software and dependencies are updated to address new vulnerabilities.
87. What is a buffer overflow vulnerability?
Ans:
A buffer overflow occurs when excessive data corrupts adjacent memory locations, potentially leading to code execution. Attackers exploit this vulnerability to gain control over the system. Buffer overflows are frequently targeted in remote attacks. To mitigate risks, implement input validation and boundary checks. Failure to address this issue can result in severe security breaches and loss of data integrity.
88. What is the significance of security logging?
Ans:
- Security logging records system events.
- It details security-relevant activities.
- Logs aid in detecting and investigating incidents.
- They assist in forensic analysis and incident response.
- Logging enhances accountability and meets compliance.
- With it, identifying breaches is easier.
89. What is the Difference between vulnerability assessment and security audit?
Ans:
- Vulnerability assessment identifies system vulnerabilities.
- It involves scans or manual inspections.
- A security audit evaluates an organization’s overall security.
- Audits assess compliance and best practices.
- While assessments focus on vulnerabilities, audits offer holistic views.
- Both are crucial for comprehensive security strategies.
90. How does the OWASP Top Ten list help?
Ans:
The OWASP list highlights critical web security risks and guides developers and security professionals. By focusing on these risks, threats can be mitigated effectively. The list serves as a crucial guide for secure application development and raises awareness about prevalent security issues. Adhering to the OWASP Top Ten significantly improves application security and helps organizations build robust defenses.






