
Saviynt is a premier identity governance and administration (IGA) platform designed to help organizations manage and secure digital identities. It provides advanced solutions for identity management, access governance, application governance, risk, and compliance (GRC), and cloud security. Saviynt streamlines access provisioning, enforces compliance, and mitigates risks by offering a comprehensive view of user access across various systems and applications.
1. What is identity governance and administration (IGA) and its significance?
Ans:
Identity Governance and Administration (IGA) encompasses the policies, procedures, and technologies organizations use to manage digital identities and their access to resources. It combines identity management, access management, and governance to ensure appropriate access and security within an organization. IGA solutions help enforce security policies, streamline compliance efforts, and mitigate risks associated with unauthorized access.
2. Explain the role of Saviynt in the context of IGA?
Ans:
Saviynt plays a pivotal role in IGA by offering a comprehensive platform that integrates identity governance, application access governance, and cloud security management. Saviynt’s solutions enable centralized management of identities, access rights governance, and compliance enforcement across hybrid IT environments. By automating identity lifecycle management, access certifications, and role-based access control (RBAC), Saviynt enhances security, operational efficiency, and regulatory compliance.
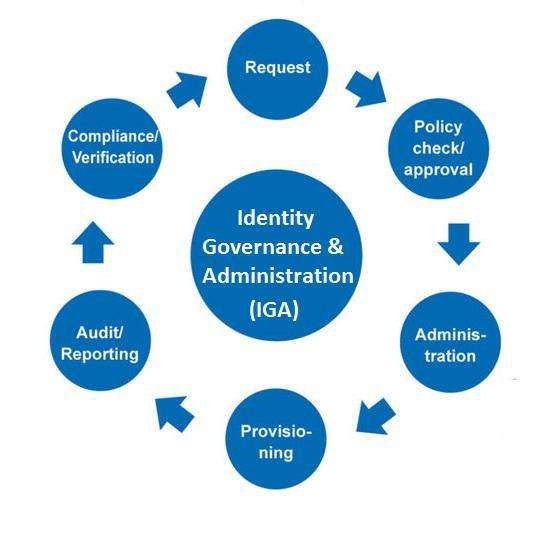
3. What are the key features and capabilities of Saviynt’s IGA platform?
Ans:
- The key features and capabilities of Saviynt’s IGA platform include robust identity lifecycle management, automated access request workflows, role management, entitlement management, and privileged access management (PAM).
- Saviynt provides extensive connectors for seamless integration with various applications, identity providers, and directories.
- Its analytics and reporting capabilities offer insights into access risks and compliance status, empowering organizations to bolster their security posture and make informed decisions.
4. How does Saviynt help organizations manage identity lifecycle management?
Ans:
- Saviynt assists organizations in managing identity lifecycle management by automating processes related to onboarding, provisioning, de-provisioning, and access recertification.
- It integrates seamlessly with HR systems and IT directories to synchronize employee lifecycle events with access rights, ensuring timely and appropriate access to resources throughout their tenure.
- This automation reduces administrative overhead, enhances operational efficiency, and minimizes risks associated with improper access.
5. Describe the difference between authentication and authorization in the context of IGA.
Ans:
| Aspect | Authentication | Authorization |
|---|---|---|
| Definition | Verification of identity | Determination of access rights |
| Purpose | Ensures user is who they claim to be | Determines what resources the user can access |
| Process | Involves validating credentials (e.g., passwords, biometrics) | Involves granting permissions based on user roles and policies |
| Context in IGA | Initial step in security processes | Follows authentication to control resource access |
| Examples | Logging in with a username and password | Accessing specific files, applications, or data |
6. What are the main components of Saviynt’s access request and approval workflow?
Ans:
Saviynt’s access request and approval workflow include components such as access request submission, automated approval routing based on predefined policies, and notifications to stakeholders. Customizable workflows accommodate organizational hierarchies and compliance requirements. Saviynt automates access provisioning based on RBAC and entitlements, ensuring efficient and auditable access management processes.
7. How does Saviynt support role-based access control (RBAC) in enterprise environments?
Ans:
- Saviynt supports role-based access control (RBAC) by enabling organizations to define roles that are aligned with job functions and responsibilities. It offers tools for role mining, engineering, and modeling to establish a structured approach to access management.
- Saviynt’s RBAC capabilities ensure users receive access permissions based on their roles, simplifying access management complexity and enhancing security through least privilege principles.
8. Explain the concept of entitlement management and how Saviynt addresses it.
Ans:
- Entitlement management involves defining and managing detailed access permissions and privileges across an organization’s IT environment.
- Saviynt addresses entitlement management by centralizing access rights management across applications, data, and infrastructure.
- It provides automated entitlement reviews, access certifications, and policy enforcement to ensure users only access necessary resources.
9. What is the importance of compliance management in IGA, and how does Saviynt facilitate it?
Ans:
Compliance management is critical in IGA to meet regulatory requirements and internal policies for access control and data protection. Saviynt supports compliance management through automated access certifications, segregation of duties (SoD) policies enforcement, and detailed access activity auditing. It offers predefined compliance frameworks and controls to streamline audits and ensure access management aligns with regulatory standards.
10. How does Saviynt integrate with various identity providers and directories?
Ans:
Saviynt seamlessly integrates with various identity providers and directories to streamline identity and access management across hybrid IT environments. Through connectors and APIs, it supports integration with cloud platforms, on-premises applications, HR systems, and IT directories. Saviynt’s integration capabilities synchronize identities, enforce consistent access policies, and extend governance and security controls across diverse IT landscapes.
11. What experience is there with implementing or managing Saviynt solutions?
Ans:
- Implementing Saviynt solutions has been extensive, focusing primarily on Identity Governance and Administration (IGA).
- This involved collaborating closely with organizations to assess their identity management needs, configure Saviynt’s platform to align with their business processes and ensure seamless integration with existing IT infrastructures.
- Critical tasks included leveraging Saviynt’s capabilities in access certification, role management, and compliance reporting to enhance security and regulatory compliance.
12. What steps are involved in configuring Saviynt for a new client?
Ans:
- Configuring Saviynt for a new client typically involves several essential steps.
- First, it is crucial to understand the client’s organizational structure, compliance requirements, and current identity management systems.
- Next, configuring connectors to synchronize identity data from various sources such as HR systems, Active Directory, and other applications ensures accurate user provisioning and de-provisioning.
13. How does Saviynt handle access governance and segregation of duties (SoD)?
Ans:
Saviynt excels in access governance and Segregation of Duties (SoD) through its robust role-based access control (RBAC) model and continuous compliance monitoring. It enables organizations to define roles, map them to entitlements, and conduct regular access reviews to identify and remediate any violations of SoD policies. Automated risk scoring and remediation workflows further enhance compliance efforts, ensuring adherence to regulatory standards such as SOX, GDPR, and HIPAA.
14. What role does Saviynt play in managing privileged access management (PAM)?
Ans:
Regarding Privileged Access Management (PAM), Saviynt plays a critical role in securing access to privileged accounts and sensitive resources. It integrates with PAM solutions to manage and monitor privileged sessions, enforce least privilege principles, and provide comprehensive audit trails. Role-based access to privileged functions and session recording capabilities bolster security measures, reducing the risk of unauthorized access and insider threats.
15. Describe a challenging deployment or integration project you worked on with Saviynt.
Ans:
- One particularly challenging deployment project involved integrating Saviynt within a complex IT environment comprising both cloud-based and on-premises applications.
- The project required extensive connector customization to ensure seamless data synchronization and identity lifecycle management across hybrid environments.
- Addressing scalability concerns and optimizing performance while maintaining stringent security protocols posed significant challenges, which we successfully mitigated through meticulous planning and collaboration with stakeholders.
16. How does Saviynt address the complexities of managing identities in hybrid IT environments?
Ans:
- Saviynt addresses the complexities of managing identities in hybrid IT environments by offering unified visibility and control across cloud, on-premises, and hybrid infrastructures.
- It supports hybrid identity models, integrates with major cloud platforms and directory services, and provides flexible deployment options (cloud, on-premises, hybrid).
- This enables organizations to manage identities centrally, enforce consistent access policies, and streamline compliance across diverse IT landscapes.
17. Explain the role of connectors in Saviynt’s solution architecture.
Ans:
Connectors in Saviynt’s solution architecture facilitate seamless integration with various identity sources, applications, and IT systems. They enable automated provisioning and de-provisioning of user accounts, synchronization of entitlements and attributes, and real-time data updates. Connectors are configurable to meet specific integration requirements, ensuring interoperability and data consistency across the enterprise ecosystem.
18. How are performance issues addressed in Saviynt’s IGA platform?
Ans:
Troubleshooting performance issues in Saviynt’s IGA platform involves systematic diagnosis and optimization. Initial steps include analyzing system logs, monitoring resource utilization (CPU, memory, disk I/O), and identifying any bottlenecks in data processing or connectivity. Tuning configuration settings, optimizing database queries, and reviewing network configurations may be necessary to improve overall system responsiveness and mitigate performance degradation.
19. What approach is used for designing access control policies with Saviynt?
Ans:
- Understanding organizational roles and responsibilities.
- Defining granular entitlements.
- Aligning policies with regulatory requirements.
It starts with conducting access risk assessments, defining role hierarchies, and implementing segregation of duties rules. Automated policy enforcement, access certification campaigns, and continuous monitoring ensure policy adherence and proactive risk mitigation.
20. What are the security considerations when implementing Saviynt’s IGA solutions?
Ans:
- Safeguarding sensitive identity data.
- Ensuring secure authentication and authorization mechanisms.
- Implementing encryption for data in transit and at rest.
Access controls should be rigorously configured to prevent unauthorized access, and audit trails should be maintained for compliance and forensic purposes. Regular security assessments, patch management, and employee training are essential to maintaining a robust security posture against evolving threats.
21. How does Saviynt ensure scalability and performance in large enterprise deployments?
Ans:
Saviynt ensures scalability and performance in large enterprise deployments through a distributed architecture that supports horizontal scaling across multiple servers and data centers. This architecture is designed to efficiently manage high volumes of identity data, user transactions, and access requests. Advanced caching mechanisms optimize data retrieval and processing speed, reducing latency.
22. Explain the role of risk-based analytics and reporting in Saviynt.
Ans:
Risk-based analytics and reporting are integral to Saviynt, providing organizations with insights into access risks and compliance status. By analyzing user access patterns and calculating risk scores based on factors like behavior and entitlements, Saviynt prioritizes access reviews and compliance efforts. Detailed reporting capabilities offer visibility into compliance posture, audit trails, and regulatory adherence.
23. How does Saviynt support auditing and logging for compliance purposes?
Ans:
- Saviynt supports auditing and logging essential for compliance by capturing detailed logs of all user activities, access requests, approvals, role modifications, and system configurations.
- These audit logs are securely stored and accessible for forensic analysis, compliance audits, and regulatory reporting. Saviynt ensures data integrity and confidentiality through encryption, access controls, and tamper-evident logging, meeting rigorous compliance requirements across industries.
24. Describe a scenario where you customized Saviynt to meet specific client requirements.
Ans:
Customizing Saviynt’s functionality to meet specific client needs involves tailoring workflows, role definitions, and access policies to align with unique organizational processes and regulatory requirements. This customization includes integrating Saviynt with proprietary applications, implementing specific role hierarchies based on client structures, and configuring automated workflows to streamline access reviews and certifications in accordance with industry-specific compliance standards.
25. How does Saviynt handle identity governance in DevOps and CI/CD pipelines?
Ans:
Saviynt supports identity governance in DevOps and CI/CD pipelines by integrating IAM into automated deployment processes. It enables organizations to manage identities, enforce access controls, and monitor permissions across development, testing, and production environments seamlessly. Integrations with DevOps tools automate provisioning and de-provisioning based on predefined roles and policies, ensuring security and compliance throughout the software development lifecycle without impeding agility.
26. What are the regulatory compliance standards that Saviynt helps organizations adhere to?
Ans:
- Saviynt helps organizations comply with diverse regulatory standards such as GDPR, SOX, HIPAA, PCI-DSS, and industry-specific regulations.
- It offers pre-built compliance frameworks, control mappings, and audit reports to facilitate alignment with regulatory requirements.
- Continuous compliance monitoring ensures consistent enforcement of access policies and controls, helping organizations mitigate compliance risks and demonstrate adherence during audits.
27. How does Saviynt assist organizations in managing access certification campaigns?
Ans:
- Saviynt assists organizations in managing access certification campaigns through automated processes that enable certifiers to review user entitlements and approve or revoke access rights based on policy.
- Configurable campaigns include customizable review periods, escalation workflows, and comprehensive reporting on certification results and compliance status.
- This streamlines access governance reduces administrative overhead and maintains a secure access environment.
28. Explain the role of AI and machine learning in Saviynt’s IGA solutions.
Ans:
AI and machine learning are pivotal in Saviynt’s IGA solutions, enhancing risk assessment, anomaly detection, and decision-making. AI algorithms analyze data to detect access patterns, entitlement assignments, and user behaviors, predicting potential risks and enabling proactive threat mitigation. Machine learning models refine identity governance processes, ensuring robust security measures while optimizing operational efficiency and reducing manual effort.
29. What insights are gained from Saviynt’s user interface and dashboard?
Ans:
Saviynt’s user interface and administrative dashboard have been highly favorable. The UI is intuitive and user-friendly, offering centralized access to essential functionalities such as user provisioning, role management, access reviews, and compliance reporting. Customizable dashboards readily provide real-time insights into access governance metrics, compliance status, and audit findings. This supports informed decision-making and operational efficiency within the IGA environment.
30. How does Saviynt manage and enforce password policies across an organization?
Ans:
- Saviynt integrates with directory services and offers robust password management capabilities to manage and enforce password policies across organizations.
- Administrators can define and implement centrally password complexity rules, expiration policies, and multi-factor authentication settings.
- Self-service password reset functionalities enhance user convenience while reducing help desk workload.
31. What role does Saviynt play in managing identities for contractors and third-party vendors?
Ans:
- Saviynt plays a vital role in managing identities for contractors and third-party vendors by extending identity governance beyond employees.
- It allows organizations to define roles and entitlements specific to external parties, ensuring appropriate access to systems and data based on contractual agreements.
- Automated provisioning and de-provisioning workflows, access certification campaigns, and continuous monitoring of external identities help maintain compliance with organizational policies and regulatory requirements.
32. Describe a scenario where you had to handle a security incident using Saviynt’s tools.
Ans:
Handling a Security Incident with Saviynt’s Tools: During a security incident, Saviynt’s tools are crucial for rapid response and risk mitigation. For example, if unauthorized access is detected, Saviynt’s access certification and risk analytics swiftly identify affected accounts and entitlements. Automated workflows facilitate immediate access revocations or role changes to contain the incident.
33. How does Saviynt help organizations with identity governance in mergers and acquisitions?
Ans:
Saviynt supports organizations in mergers and acquisitions by facilitating seamless integration of identity governance processes. It enables the consolidation of user identities, roles, and access rights from multiple entities into a unified framework. Saviynt’s capabilities in role management, access certification, and policy enforcement streamline identity governance across newly merged or acquired entities. This ensures consistent access controls, reduces compliance risks, and supports IT infrastructure integration during transitional phases.
34. What are Saviynt’s API capabilities and integration options?
Ans:
- Saviynt offers robust API capabilities and integration options to facilitate seamless interoperability with other IT systems and applications.
- APIs enable programmatic access to Saviynt’s functionalities, such as user provisioning, role management, access certification, and reporting.
- This flexibility allows organizations to integrate Saviynt with existing IT ecosystems, including HR systems, directory services, ERP solutions, and custom applications.
35. Explain how Saviynt facilitates continuous compliance monitoring and reporting.
Ans:
- Saviynt facilitates continuous compliance monitoring through real-time analysis of access activities, entitlement changes, and policy violations.
- Automated risk assessments and compliance dashboards provide ongoing visibility into adherence to regulatory requirements and internal policies.
- Saviynt generates comprehensive compliance reports, audit trails, and alerts to notify stakeholders of deviations or potential risks promptly.
36. How does Saviynt address the challenges of identity governance in IoT environments?
Ans:
Saviynt addresses the challenges of identity governance in IoT environments by extending its capabilities to manage identities associated with IoT devices. Organizations can define and manage devices’ identities, establish access controls based on device types and roles, and enforce policies governing device interactions with IT systems. Saviynt’s integration with IoT platforms and protocols enables automated provisioning, monitoring of device access rights, and compliance auditing.
37. How are Saviynt’s role mining and role engineering features utilized?
Ans:
Saviynt’s role mining and role engineering features involves leveraging data analytics to identify patterns in user access and behavior. Role mining analyzes historical data to propose optimized role structures based on least privilege principles and business needs. Role engineering allows administrators to refine role definitions, assign entitlements, and simulate role changes before implementation.
38. How does Saviynt support self-service access requests and approvals?
Ans:
- Saviynt supports self-service access requests and approvals through an intuitive portal where employees can request access to applications and resources based on predefined roles and entitlements.
- Automated workflows route requests to appropriate approvers according to policy rules and hierarchies.
- Approvers can review requests, certify access, and make informed decisions using real-time access analytics and compliance insights provided by Saviynt.
39. Explain the concept of privileged access management (PAM) in Saviynt’s ecosystem.
Ans:
- In Saviynt, Privileged Access Management (PAM) involves securing access to privileged accounts and sensitive resources through stringent controls and monitoring.
- Saviynt integrates with PAM solutions to enforce least privilege principles, manage privileged sessions, and maintain comprehensive audit trails of privileged activities.
40. What are the benefits of using Saviynt for managing cloud identities and access?
Ans:
Leveraging Saviynt for managing cloud identities and access offers several advantages. It provides centralized visibility and control over cloud-based applications and infrastructure, ensuring consistent enforcement of access policies across hybrid IT environments. Saviynt’s integrations with significant cloud platforms streamline user provisioning, access certification, and compliance reporting in cloud environments.
41. How does Saviynt assist organizations in achieving Zero Trust security principles?
Ans:
Saviynt assists organizations in attaining Zero Trust security principles by implementing comprehensive identity-centric security measures. It ensures strict verification of every access request, regardless of whether it originates from inside or outside the network perimeter. Saviynt’s continuous monitoring capabilities analyze user behavior, device health, and contextual factors to assess risk dynamically.
42. Describe a scenario where you had to optimize Saviynt’s performance for a client.
Ans:
- In a scenario where optimization of Saviynt’s performance was crucial, a thorough assessment of the client’s infrastructure and usage patterns was conducted.
- This involved fine-tuning configuration settings, optimizing database queries, and implementing caching strategies to enhance data retrieval and processing speed.
- Reviewed hardware resources and recommended scaling options to support increased workload demands.
43. How does Saviynt handle identity federation and single sign-on (SSO) integrations?
Ans:
- Saviynt facilitates identity federation and SSO integrations by supporting industry-standard protocols such as SAML, OAuth, and OpenID Connect.
- It enables seamless authentication and authorization across diverse IT systems and cloud applications.
- Saviynt acts as an identity provider (IdP) or integrates with existing IdPs to establish federated trust relationships.
44. What experience exists with Saviynt’s role-based access control (RBAC) model?
Ans:
Saviynt’s RBAC model involves designing and implementing role structures that align with organizational hierarchies and security policies. Saviynt allows granular role definition, associating them with specific entitlements and permissions based on job responsibilities and business needs. Role engineering capabilities facilitate iterative refinement of roles to achieve the least privilege access principles.
45. How does Saviynt help organizations address insider threats and data breaches?
Ans:
Saviynt helps organizations address insider threats and data breaches through proactive monitoring and behavioral analytics. It continuously evaluates user activities, detecting anomalies and suspicious behavior patterns that may indicate insider threats. Automated alerts and response workflows enable swift action to mitigate risks, such as revoking access or triggering further investigation.
46. What approach is taken for implementing governance policies in Saviynt?
Ans:
- Implementing governance policies with Saviynt involves defining clear objectives aligned with regulatory requirements and organizational goals.
- Collaborate closely with stakeholders to identify critical assets, establish access policies, and configure Saviynt to enforce these policies consistently.
- This includes defining role structures, access certification campaigns, and automated workflows for access requests and approvals.
47. What challenges arise during Saviynt implementation and their solutions?
Ans:
- Key challenges organizations may face when implementing Saviynt include complexity in defining roles, integrating with diverse IT systems, and managing change across the organization.
- To overcome these challenges, emphasize comprehensive planning, stakeholder engagement, and phased implementation strategies.
- Clear communication of benefits, extensive training programs, and leveraging Saviynt’s professional services and support resources play crucial roles in ensuring successful adoption and alignment with business objectives.
48. How does Saviynt assist with compliance audits and reporting requirements?
Ans:
Saviynt supports compliance audits and reporting requirements by providing comprehensive audit trails, compliance dashboards, and customizable reports. It captures and retains detailed logs of user access activities, entitlement changes, and policy violations, facilitating forensic analysis and regulatory audits. Automated compliance assessments against predefined frameworks and continuous monitoring capabilities help organizations maintain audit readiness and demonstrate adequate adherence to industry regulations and internal policies.
49. How is user lifecycle management handled in Saviynt?
Ans:
Saviynt’s user lifecycle management involves automating processes for user provisioning, modification, and de-provisioning throughout the user journey. Saviynt integrates with HR systems and IT directories to synchronize user data and ensure timely updates to access rights based on role changes or organizational transitions. Workflow automation streamlines approval processes, while access certification campaigns validate user entitlements to maintain compliance and security standards consistently.
50. How does Saviynt handle identity lifecycle management for non-human entities (e.g., service accounts)?
Ans:
- Saviynt manages the identity lifecycle for non-human entities by provisioning and managing service accounts, APIs, and other system identities.
- It ensures these entities have appropriate access based on predefined roles and policies, minimizing privileged access risks.
- Automated lifecycle management workflows handle account creation, periodic access reviews, and de-provisioning to prevent orphaned accounts and maintain security hygiene across IT environments.
51. Describe Saviynt’s support for federated identities and attribute-based access control (ABAC).
Ans:
- Saviynt supports federated identities by integrating seamlessly with identity providers (IdPs) using standard protocols like SAML, OAuth, and OpenID Connect.
- This enables smooth authentication and authorization across various IT systems and cloud applications, enhancing security while reducing user friction.
52. How does Saviynt assist organizations in managing access rights across geographically dispersed teams?
Ans:
Saviynt assists organizations in managing access rights across dispersed teams through centralized identity governance and access management. It provides a unified platform to define roles, policies, and access entitlements consistently across global locations. Role-based access controls streamline processes for provisioning and de-provisioning, ensuring team members have appropriate access to resources based on their roles and responsibilities.
53. Describe a scenario involving complex troubleshooting in Saviynt’s implementation.
Ans:
When troubleshooting complex issues in Saviynt’s implementation to follow a systematic approach. This involves analyzing system logs and audit trails to pinpoint the root causes of problems, such as access discrepancies or workflow failures. Collaborating closely with Saviynt’s technical support team and utilizing diagnostic tools helps identify configuration errors, database performance issues, or integration bottlenecks.
54. How does Saviynt ensure data privacy and protection in its IGA solutions?
Ans:
- Saviynt prioritizes data privacy and protection within its IGA solutions through robust security measures.
- Sensitive data is encrypted both in transit and at rest to preserve information integrity.
- Role-based access controls enforce least privilege principles, restricting access to sensitive information based on job roles and responsibilities.
- Comprehensive audit logs capture detailed user activities and access attempts, facilitating compliance with data protection regulations such as GDPR and CCPA.
55. What strategies do you employ to ensure successful user adoption of Saviynt’s IGA platform?
Ans:
- To promote successful user adoption of Saviynt’s IGA platform, strategic approaches are employed.
- This includes conducting tailored user training sessions that cater to different roles and proficiency levels.
- Practical workshops and simulations allow users to gain hands-on experience in performing everyday tasks like access requests, approvals, and reviews.
56. How are updates and trends in Saviynt’s features monitored?
Ans:
Stay current with Saviynt’s latest features, updates, and industry trends through various channels. This includes active participation in Saviynt’s training programs, webinars, and industry conferences where new features and product roadmaps are discussed. Regular engagement with Saviynt’s documentation, release notes, and user forums provides insights into platform enhancements and recommended practices.
57. How does Saviynt assist organizations in achieving GDPR compliance?
Ans:
Saviynt aids organizations in achieving GDPR compliance by facilitating robust data protection and privacy measures related to user identities and access controls. It supports GDPR requirements through features such as consent management, data subject access requests (DSAR), and breach notifications. Role-based access controls and audit capabilities ensure accountability and traceability in handling personal data.
58. What approach is used for user training and support in Saviynt?
Ans:
- The approach to user training and support for Saviynt’s IGA solutions begins with understanding user roles and specific needs.
- Tailored training programs cover essential concepts, system navigation, and best practices in identity governance and access management.
- Hands-on workshops and scenario-based simulations allow users to gain practical experience in using Saviynt’s features for provisioning, access certification, and policy enforcement.
59. How does Saviynt assist with managing access for the remote and mobile workforce?
Ans:
- Saviynt supports organizations in managing access for the remote and mobile workforce through flexible access policies and adaptive authentication mechanisms.
- It integrates seamlessly with mobile device management (MDM) solutions to enforce security policies on employee devices accessing corporate resources.
- Role-based access controls and contextual policies consider factors such as location, device health, and network environment to adjust access privileges dynamically.
60. What are the scalability considerations when deploying Saviynt in a large enterprise?
Ans:
Deploying Saviynt in large enterprises requires careful scalability considerations to accommodate growing user bases and expanding IT infrastructures. Saviynt’s distributed architecture supports horizontal scaling across multiple servers and data centers, optimizing performance and resilience. Integration with cloud platforms enables dynamic resource allocation and elastic scaling to handle fluctuations in user demand and data volumes effectively.
61. How is Saviynt integrated with custom-built applications?
Ans:
When integrating Saviynt with custom-built applications, collaborated closely with development teams to ensure seamless connectivity and data exchange. Using Saviynt’s APIs and integration frameworks, we mapped application-specific user attributes to Saviynt’s identity model. Custom connectors were developed to facilitate user provisioning, role assignments, and access certifications within the custom application.
62. How does Saviynt handle the complexities of managing identities in a multi-cloud environment?
Ans:
- Saviynt manages the complexities of identity governance in multi-cloud environments by offering centralized visibility and control over identities and access rights across cloud platforms.
- It integrates seamlessly with major cloud service providers like AWS, Azure, and Google Cloud, leveraging native APIs to synchronize user identities, roles, and entitlements.
63. What experience is there with Saviynt’s role-based access certification?
Ans:
- Saviynt’s role-based access certification processes involves designing and executing access review campaigns to validate user entitlements.
- Saviynt automates the certification process by scheduling periodic reviews based on predefined policies and role assignments. Stakeholders receive notifications to review and attest to the accuracy of user access rights.
64. How does Saviynt assist organizations in managing privileged access for critical systems?
Ans:
Managing Privileged Access for Critical Systems with Saviynt: Saviynt assists organizations in managing privileged access for critical systems through robust privileged access management (PAM) capabilities. It integrates with PAM solutions to enforce least privilege principles, monitor privileged sessions, and manage credentials securely. Role-based access controls limit access to privileged accounts based on job roles and responsibilities.
65. How are access reviews and audits conducted with Saviynt?
Ans:
Performing access reviews and audits using Saviynt involves leveraging its automated capabilities to assess user entitlements and access patterns. Saviynt conducts periodic access reviews based on defined criteria, generating detailed reports on access certifications and compliance status. Utilize Saviynt’s audit trails and analytics to identify unauthorized access attempts, segregation of duties (SoD) conflicts, and other policy violations.
66. How does Saviynt help organizations align identity governance with business objectives?
Ans:
- Saviynt helps organizations align identity governance with business objectives by enabling strategic alignment of access policies and controls.
- It starts with understanding business processes and defining critical assets and associated risks.
- Saviynt’s role engineering and simulation capabilities model access scenarios to optimize role assignments and enforce least privilege principles.
67. What approach is taken for separation of duties (SoD) policies in Saviynt?
Ans:
- Implementing Separation of Duties (SoD) policies with Saviynt involves defining granular access rules to prevent conflicts and enforce regulatory compliance.
- Saviynt’s rule library includes predefined SoD policies based on industry best practices and regulatory requirements. Collaborate with business stakeholders to map critical functions and identify sensitive roles prone to conflicts.
68. Describe a scenario where cross-departmental collaboration was essential for deploying Saviynt.
Ans:
In a collaborative scenario for a Saviynt deployment, stakeholders from various departments, including IT, security, compliance, and business units, were engaged. Workshops were conducted to collect requirements, align deployment objectives with business goals, and establish access governance policies. Clear communication and stakeholder engagement were essential for addressing departmental concerns and ensuring buy-in for the deployment.
69. How does Saviynt assist with integrating with HR systems for user provisioning and de-provisioning?
Ans:
Saviynt assists with integrating HR systems for streamlined user lifecycle management, including provisioning and de-provisioning processes. It synchronizes employee data from HR systems to maintain accurate user profiles and organizational hierarchies within Saviynt. Automated workflows trigger the provisioning of access rights based on predefined roles and policies, ensuring new hires have timely access to necessary resources.
70. What are the best practices for managing access recertification campaigns using Saviynt?
Ans:
- Best practices for managing access recertification campaigns with Saviynt involve defining clear objectives, roles, and responsibilities for stakeholders involved in the certification process.
- A regular schedule for reviews based on risk profiles and compliance requirements, leveraging Saviynt’s automation to streamline campaign execution.
- Communication strategies ensure timely notifications to reviewers, facilitating prompt review and approval of access entitlements.
71. How does Saviynt assist with managing access for third-party contractors and vendors?
Ans:
- Saviynt facilitates secure access management for third-party contractors and vendors by extending its identity governance capabilities.
- Organizations can define specific roles and access entitlements tailored to external collaborators within Saviynt’s platform.
- Through integration with identity providers and directory services, Saviynt ensures that contractors and vendors receive appropriate access permissions based on predefined policies and contractual agreements.
72. How is Saviynt integrated with SIEM systems?
Ans:
Integrating Saviynt’s Identity Governance and Administration (IGA) solutions with Security Information and Event Management (SIEM) systems involves enhancing threat detection and incident response capabilities. Saviynt integrates seamlessly with SIEM platforms to ingest identity-related data, access events, and policy violations. By correlating this information with security events from across the IT infrastructure, SIEM systems provide comprehensive visibility into potential security threats and unauthorized access attempts.
73. How does Saviynt assist with managing access for guest users and external collaborators?
Ans:
Saviynt assists organizations in managing access for guest users and external collaborators through its identity governance framework. Organizations can create temporary or limited-access accounts for guest users, controlling their permissions based on predefined policies. Saviynt’s self-service capabilities enable external collaborators to request access, which can be reviewed and approved by designated stakeholders.
74. How has Saviynt been integrated with cloud productivity suites like Office 365 or G Suite?
Ans:
- Successfully integrated Saviynt’s IGA solutions with cloud-based productivity suites such as Office 365 and G Suite to enhance identity governance and access management capabilities.
- Saviynt synchronizes user identities, roles, and access entitlements across these platforms, ensuring consistency and compliance with organizational policies.
- Integration with these productivity suites enables automated provisioning and de-provisioning of user accounts based on HR-driven events and role changes.
75. How does Saviynt help organizations automate identity lifecycle management processes?
Ans:
- Saviynt automates identity lifecycle management processes through its robust provisioning and de-provisioning workflows.
- Integration with HR systems enables automatic synchronization of employee data, triggering user account creation, role assignments, and access provisioning based on predefined policies.
- Lifecycle events such as employee onboarding, transfers, and departures are managed efficiently, ensuring timely adjustments to access privileges.
76. What is known about Saviynt’s risk-based access control?
Ans:
Saviynt incorporates risk-based access control (RBAC) capabilities to dynamically adjust access privileges based on contextual factors and risk assessments. By evaluating user attributes, device status, location, and behavior patterns, Saviynt calculates risk scores to determine appropriate access levels in real time. Adaptive authentication and authorization policies mitigate security risks by enforcing stricter controls in high-risk scenarios while allowing seamless access in low-risk situations.
77. How does Saviynt handle user authentication and authorization in hybrid IT environments?
Ans:
Saviynt handles user authentication and authorization in hybrid IT environments by integrating with identity providers (IdPs), directory services, and authentication protocols. It supports seamless authentication across on-premises and cloud-based applications, ensuring secure access management regardless of the deployment environment. Role-based access controls (RBAC) enforce least privilege principles, governing access based on user roles and responsibilities across hybrid IT infrastructures.
78. What experience is there with Saviynt’s data governance features?
Ans:
- Implementing Saviynt’s data governance features involves leveraging its capabilities to manage data access controls, data classification, and compliance requirements.
- Saviynt integrates with data repositories and platforms to enforce granular access policies based on data sensitivity and regulatory mandates. Role-based access controls (RBAC) and attribute-based access controls (ABAC) ensure that users only access data relevant to their roles and responsibilities.
79. What role does Saviynt play in managing user identities in SAP environments?
Ans:
- Saviynt plays a crucial role in managing user identities in SAP environments by integrating seamlessly with SAP systems. It synchronizes user identities, roles, and access entitlements across SAP applications, ensuring consistent access governance and compliance with SAP security standards.
- Role-based access controls (RBAC) in Saviynt align with SAP’s authorization concept, enabling organizations to enforce least privilege principles and mitigate risks associated with unauthorized access.
80. How does Saviynt assist with managing access for IoT devices and applications?
Ans:
Managing Access for IoT Devices and Applications with Saviynt: Saviynt assists organizations in managing access to IoT devices and applications through its extended identity governance capabilities. It integrates with IoT platforms and device management systems to authenticate and authorize device identities based on predefined policies. Role-based access controls (RBAC) govern access to IoT resources, ensuring that only authorized devices and applications interact with sensitive data and critical systems.
81. Describe a scenario involving customization of Saviynt’s reporting and analytics.
Ans:
In a scenario requiring customization of Saviynt’s reporting and analytics capabilities, collaboration with stakeholders was key in tailoring reporting templates and dashboards to meet specific organizational needs. Saviynt’s flexible reporting framework was utilized to configure custom metrics, filters, and data visualizations, delivering actionable insights into access governance, compliance, and risk management.
82. How does Saviynt help organizations in ensuring high availability and disaster recovery for IGA solutions?
Ans:
- Saviynt ensures high availability and disaster recovery for Identity Governance and Administration (IGA) solutions through robust architectural design and deployment strategies.
- Leveraging scalable cloud infrastructure and load-balancing techniques, Saviynt maintains service availability during peak usage and mitigates performance bottlenecks.
- Redundant data centers and failover mechanisms guarantee continuous operations in the face of hardware failures or natural disasters.
83. What strategies do you recommend for successful user adoption of Saviynt’s IGA platform?
Ans:
- Achieving successful user adoption of Saviynt’s IGA platform involves implementing comprehensive training, proactive change management practices, and continuous support initiatives.
- Conduct tailored training sessions that cater to diverse user roles, emphasizing hands-on exercises and practical scenarios to demonstrate platform functionalities and benefits.
- Engaging stakeholders early in the implementation process fosters ownership and alignment with organizational objectives.
84. How is user identity management handled with SAP ME integration in Saviynt?
Ans:
Effectively managing user identities in the context of integrating SAP Manufacturing Execution (SAP ME) with Saviynt involves seamless synchronization of user identities, roles, and access entitlements across SAP ME and other enterprise systems. Leveraging Saviynt’s connectors and integration frameworks, orchestrated automated provisioning and de-provisioning of user accounts based on HR-driven events and role changes.
85. How does Saviynt assist organizations in managing access to temporary or seasonal workforce identities?
Ans:
Saviynt assists organizations in managing access for temporary or seasonal workforce identities by offering flexible provisioning and de-provisioning workflows. Integration with HR systems automates the creation of temporary user accounts based on contract durations or project timelines. Role-based access controls (RBAC) dynamically adjust access privileges to align with job roles and responsibilities. Self-service access request portals streamline onboarding processes, enabling temporary workers to request access to required resources.
86. How are SoD policies implemented in Saviynt within manufacturing?
Ans:
- Implementing Separation of Duties (SoD) policies with Saviynt in a manufacturing environment involved defining precise access rules to prevent conflicts and ensure regulatory compliance.
- Collaborating closely with operational teams, identified critical functions and segregated roles vulnerable to conflicts in production processes.
- Saviynt’s rule library and policy engine facilitated automated SoD checks during access requests and certifications, detecting violations and suggesting mitigation measures.
87. How does Saviynt handle user authentication and authorization in IoT environments?
Ans:
- Saviynt manages user authentication and authorization in IoT environments by integrating seamlessly with IoT platforms and device management systems. It establishes secure connections and authenticates device identities based on predefined policies and certificates.
- Role-based access controls (RBAC) govern access to IoT resources, ensuring that only authorized devices and applications interact with sensitive data and critical systems.
88. Describe integrating Saviynt’s IGA solutions with custom manufacturing apps
Ans:
Integrating Saviynt’s IGA solutions with custom-built manufacturing applications involved developing tailored connectors and APIs to synchronize user identities, roles, and access entitlements seamlessly. Collaborating with development teams and mapped application-specific attributes to Saviynt’s identity model, facilitating automated provisioning and role assignments. Saviynt’s extensible architecture supported the integration of custom workflows for access requests, approvals, and certifications within manufacturing processes.
89. How does Saviynt ensure data privacy and protection in its IGA solutions for manufacturing enterprises?
Ans:
Saviynt ensures data privacy and protection in IGA solutions for manufacturing enterprises through rigorous data encryption, access controls, and adherence to global privacy regulations. Role-based access controls (RBAC) enforce least privilege principles, restricting access to sensitive manufacturing data based on user roles and responsibilities. Data masking techniques anonymize confidential information within reporting and analytics features, safeguarding sensitive data from unauthorized access.
90. What is the approach to end-user training and support for Saviynt’s IGA platform?
Ans:
The approach to training and supporting end-users in effectively using Saviynt’s IGA platform includes tailored training programs, user-friendly documentation, and proactive support initiatives. Comprehensive training sessions are held to address various user roles, focusing on hands-on exercises and practical scenarios to illustrate platform functionalities and best practices. User-friendly documentation and video tutorials are available to support self-paced learning and troubleshooting.






