
A thorough security testing method called Vulnerability Assessment and Penetration Testing (VAPT) is used to find weaknesses in computer systems, networks, and applications. It entails analyzing systems for possible flaws and carefully testing them to determine how much risk they present. VAPT assists companies in proactively safeguarding their assets by locating and fixing security holes before malevolent actors may take advantage of them.
1. What is VAPT, and why is it important?
Ans:
Vulnerability Assessment and Penetration Testing, sometimes known as VAPT, is essential for locating and fixing security flaws in systems, networks, and applications. It aids organizations in proactively managing their security attitude, lowering the possibility of data breaches, and safeguarding sensitive information from unauthorized access.
2. How do you ensure that VAPT activities do not disrupt normal business operations?
Ans:
Conduct VAPT activities during off-peak hours, employ non-intrusive testing techniques, work closely with IT and business stakeholders, and have a clear rollback plan in place in case of issues to ensure they don’t interfere with regular business operations. To minimize impact, careful planning and regular communication are essential.
3. What are the common goals of vulnerability assessment and penetration testing?
Ans:
- Identify and prioritize security vulnerabilities.
- Evaluate the potential impact of these vulnerabilities.
- Assess the effectiveness of existing security measures.
- Provide actionable recommendations to enhance overall security posture.
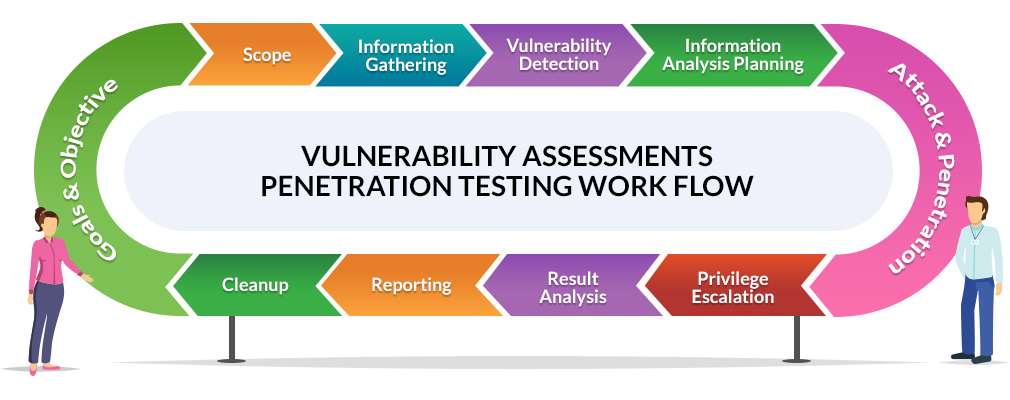
4. How do you approach scoping a VAPT engagement?
Ans:
- Establish the aims and goals of the VAPT engagement, such as compliance or threat detection, before defining the scope of the work.
- Determine which assets such as systems, networks, and apps need to be tested.
- Ascertain the necessary testing depth and methodologies (black box, white box, or grey box). Lastly, decide on the engagement’s budget, schedule, and resources.
5. What methodologies do you follow for vulnerability assessment and penetration testing?
Ans:
Standard methodologies include The National Institute of Standards and Technology (NIST), OWASP, The Open Source Security Testing Methodology Manual, and the Open Web Application Security Project (OSSTMM). These structured approaches guide the conduct of VAPT activities.
6. Could you outline the procedures involved in a typical VAPT engagement?
Ans:
The steps typically include scoping, reconnaissance, vulnerability scanning, vulnerability exploitation, post-exploitation analysis, reporting, and remediation support. Each step is essential for effectively identifying, exploiting, and addressing security vulnerabilities.
7. What are the various types of vulnerabilities you commonly encounter?
Ans:
- Injection flaws that let attackers run harmful code, like SQL injection.
- User accounts may be accessed without authorization due to Broken authentication.
- Cross-Site Scripting (XSS) is a technique where harmful scripts are injected into websites that other people are viewing.
- Insecure direct object references, in which hackers use form parameters or URL manipulation to obtain illegal data.
8. How do you prioritize vulnerabilities for remediation?
Ans:
- Assign vulnerabilities a priority based on their potential impact, exploitability, and severity.
- To score and group hazards, make use of frameworks such as the CVSS.
- Prioritize fixing serious and high-risk vulnerabilities that compromise important data or systems.
- Priorities should be periodically reviewed and updated in light of changing threat environments.
9. Could you elaborate on the idea of a “false positive” and how you handle them?
Ans:
A false positive happens when an anti-virus program misidentifies a non-existent vulnerability. To handle false positives, we carefully validate findings through manual verification, additional testing, and analysis. False positives are documented and excluded from the final report.
10. Explain the difference between vulnerability assessment and penetration testing?
Ans:
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Purpose | Identify and prioritize system vulnerabilities. | Simulate real-world attacks to exploit vulnerabilities. |
| Approach | Automated scanning for known vulnerabilities. | Manual testing with simulated attacks. |
| Scope | Broad assessment of system weaknesses. | Targeted attempt to penetrate and compromise systems. |
| Methodologies | Scanning tools, vulnerability databases. | Manual testing, exploit frameworks, social engineering. |
11. What tools do you commonly use for vulnerability scanning?
Ans:
- Nessus: Comprehensive assessments
- OpenVAS: Open-source option
- Qualys: Cloud-based capabilities
- Nmap: Network discovery and security auditing
12. Can you explain how a vulnerability scanner works?
Ans:
- A vulnerability scanner operates by systematically scanning networks, systems, or applications for known vulnerabilities.
- It sends out probes or requests to target hosts, analyzes the responses, and cross-references them against a database of known vulnerabilities to pinpoint potential security gaps.
13. How do active and passive vary from one another scanning?
Ans:
Active scanning involves sending requests or probes to target systems to elicit responses and identify vulnerabilities actively. Passive scanning, conversely, consists of monitoring network traffic and scrutinizing data without directly engaging with the target systems.
14. How do you identify vulnerabilities manually?
Ans:
Manual vulnerability identification encompasses in-depth analysis and testing of systems, networks, or applications to unearth security weaknesses. This may include scrutinizing code, analyzing system configurations, and employing manual testing methods like fuzzing and reverse engineering.
15. Can you explain how you would exploit a SQL injection vulnerability?
Ans:
- Exploiting an SQL injection vulnerability entails injecting malevolent SQL code into a web application’s input fields to manipulate the backend database.
- This could permit attackers to retrieve, modify, or delete data, bypass authentication mechanisms, or execute arbitrary commands on the database server.
16. What is cross-site scripting (XSS), and how can it be prevented?
Ans:
Cross-site scripting (XSS) is a security flaw enabling attackers to insert malicious programs onto other users’ web pages. Preventive measures include:
- Implementing stringent input validation and output encoding.
- Employing security headers such as Content Security Policy (CSP).
- Regularly updating web application frameworks and libraries.
17. How do you detect and exploit buffer overflow vulnerabilities?
Ans:
Detecting buffer overflow vulnerabilities involves utilizing fuzzing techniques and static code analysis tools. Exploiting them necessitates meticulously crafting input data to overwrite memory addresses and execute arbitrary code, potentially leading to memory corruption and code execution.
18. Explain the difference between black-box, white-box, and grey-box testing.
Ans:
Black-box testing involves examining a system or application without internal knowledge, while white-box testing involves complete comprehension of the internal structure and code. Grey-box testing blends elements of both, with testers having partial insight into internal workings but not full access.
19. Can you explain the process of privilege escalation?
Ans:
- Privilege escalation is the process of attaining higher levels of access or privileges than intended by exploiting security vulnerabilities.
- This may entail leveraging misconfigured permissions, software vulnerabilities, or insecure configurations to elevate privileges and gain unauthorized access to resources or systems.
20. How do you determine the severity of a vulnerability?
Ans:
- The severity of a vulnerability hinges on factors like its impact on confidentiality, integrity, and availability of data or systems, likelihood and ease of exploitation, and potential compliance or regulatory ramifications.
- Common vulnerability scoring systems, such as CVSS (Common Vulnerability Scoring System), are utilized to quantify vulnerability severity.
21. What factors do you consider when assessing the risk associated with a vulnerability?
Ans:
When evaluating the risk linked to a vulnerability, I take into consideration various factors. These include the potential impact on confidentiality, integrity, and availability, the likelihood of exploitation, existing security measures, the criticality of affected systems to business operations, and any regulatory or compliance obligations.
22. Can you explain the concept of the “attack surface”?
Ans:
The complete amount of a system’s vulnerabilities that an attacker can access is referred to as the “attack surface”. It covers every location an unauthorized person might attempt to access or retrieve data. Lowering the attack surface lowers the possibility of security lapses. This entails protecting network borders, software, and hardware.
23. How do you communicate the results of a VAPT assessment to non-technical stakeholders?
Ans:
- To convey VAPT findings effectively to non-technical stakeholders, I employ clear and straightforward language, focusing on the business implications and potential risks.
- I provide executive summaries, graphical representations, and actionable recommendations tailored to their comprehension level.
24. What function does risk management serve? In VAPT?
Ans:
- Risk management plays a pivotal role in VAPT by identifying, assessing, and prioritizing security risks to an organization’s assets.
- It guides decision-making processes, helping allocate resources efficiently, implement appropriate controls, and mitigate vulnerabilities to an acceptable level.
25. Can you explain the concept of remaining danger?
Ans:
The amount of risk known as residual risk is the one that persists after implementing security controls to address identified vulnerabilities. It signifies the risk that an organization accepts or retains due to factors such as cost, resource constraints, or the inability to eliminate the risk.
26. What compliance standards do you commonly encounter in VAPT engagements?
Ans:
In VAPT engagements, common compliance standards encountered include GDPR (General Data Protection Regulation), The Data Security Standard for Payment Card Industry (PCI DSS), and The Health Insurance Portability and Accountability Actgoes by the name HIPAA. In addition to ISO 27001 and NIST SP 800-53.
27. How do you ensure that VAPT activities comply with relevant regulations and standards?
Ans:
- The first step in making sure VAPT (Vulnerability Assessment and Penetration Testing) operations adhere to pertinent laws and industry standards is to fully comprehend the particular legal and regulatory requirements.
- Put into practice recognized frameworks like PCI-DSS, NIST, and ISO 27001. Provide the team with frequent compliance protocol training.
- Lastly, keep thorough records and make sure you have the required authorizations before running any testing.
28. What steps do you take to ensure client confidentiality during VAPT activities?
Ans:
- Secure Communication Channels: When exchanging sensitive information with a client, use encrypted communication tools.
- Restricted Access: Assure stringent authentication procedures and restrict authorized personnel’s access to VAPT data.
- Non-disclosure Agreements: To formally bind both parties to confidentiality requirements, execute extensive NDAs.
- Data Encryption: To protect any data gathered during penetration tests and vulnerability assessments, use encryption techniques.
29. What documentation is typically produced during a VAPT engagement?
Ans:
Documentation commonly includes a comprehensive report detailing discovered vulnerabilities, their severity levels, recommended remediation actions, evidence of exploitation, executive summaries, the methodology employed, and any compliance-related documentation stipulated by the client or regulatory bodies.
30. How do you detect and respond to security incidents during a penetration test?
Ans:
Throughout a penetration test, I maintain constant vigilance for indicators of compromise, unusual behaviour, or unauthorized activity. Upon detection of a security incident, I promptly document and report it to the relevant stakeholders, potentially suspending testing, and collaborate with incident response teams to effectively contain and mitigate the incident.
31. What steps do you take to contain a security incident?
Ans:
- Start by swiftly identifying the scope and nature of the threat.
- Isolate the affected systems from the network to prevent the issue from spreading.
- Decide on a containment strategy, balancing between immediate quick fixes and long-term solutions.
- Communicate with all relevant stakeholders and teams about the situation and actions being taken.
- Preserve evidence by making forensic copies of the affected systems.
32. How do you gather evidence during an incident response process?
Ans:
- Gathering evidence during an incident response includes collecting logs from firewalls, intrusion detection systems (IDS), servers, and applications.
- Create forensic images of the hard drives of affected systems and capture the volatile memory (RAM) to analyze running processes and network connections.
- Collect network traffic captures to identify malicious activities. Maintain detailed records of all actions, including timestamps and descriptions, and ensure a transparent chain of custody for all evidence to preserve its integrity and admissibility in court.
33. What role does threat intelligence play in incident response?
Ans:
Threat intelligence is crucial in incident response as it aids in early detection by identifying indicators of compromise (IoCs) and the tactics, techniques, and procedures (TTPs) used by attackers. It provides context about threat actors, their motivations, and methods, helping responders prioritize incidents based on threat level and potential impact. Threat intelligence supports proactive defence by enabling organizations to implement preventative measures against known threats and assists in understanding the scope and impact of incidents for a more effective response.
34. Can you explain the principles of symmetric and asymmetric cryptography?
Ans:
A single key is used by symmetric encryption for both encryption and decryption. I am making it faster due to simpler algorithms. It is ideal for encrypting large amounts of data but needs to be improved in secure key distribution and management. Asymmetric encryption, on the other hand, involves a pair of keys a public key for encryption and a private key for decryption. This method is more secure for key distribution since the private key is never shared, making it suitable for secure key exchange and digital signatures.
35. How do you select appropriate cryptographic algorithms for a given scenario?
Ans:
- Choosing cryptographic algorithms involves evaluating security requirements, such as confidentiality, integrity, and authenticity.
- Assess the algorithm’s performance and its impact on system resources.
- Ensure the algorithm meets regulatory and industry standards, like FIPS and NIST, and consider the complexity of essential generation, distribution, and storage.
- Ensure compatibility with existing systems and protocols, and select algorithms that are widely recognized and thoroughly vetted by the cryptographic community, such as AES for symmetric encryption and RSA or ECC for asymmetric encryption.
36. What is a digital signature, and how does it function?
Ans:
A cryptographic method called a digital signature is used to confirm the integrity and authenticity of digital messages or documents. The process involves creating a hash of the message or document and then encrypting this hash with the sender’s private key, resulting in the digital signature. The signed document and the digital signature are then sent to the recipient. If the hashes match, the message is confirmed to be authentic and unaltered.
37. How do you ensure the confidentiality and integrity of data in transit?
Ans:
To ensure the confidentiality and integrity of data in transit:
- Use encryption protocols like TLS/SSL.
- Implement robust authentication mechanisms, such as certificates and multifactor authentication, and utilize hashing techniques like HMAC to verify data integrity.
- Employ secure communication channels, such as VPNs, and restrict access to authorized users only.
38. What measures do you take to secure wireless networks?
Ans:
Securing wireless networks involves using strong encryption protocols like WPA3 and implementing robust authentication methods such as 802.1X. Disable SSID broadcasting and use non-default SSIDs. Apply MAC address filtering and network segmentation, and regularly update the firmware to patch vulnerabilities. Continuously monitor for unauthorized access points and unusual activity, and ensure the physical security of access points to prevent tampering.
39. Can you explain the OWASP Top Ten vulnerabilities?
Ans:
The OWASP Top Ten lists the most critical web application security risks. These include Injection flaws like SQL, NoSQL, OS, and LDAP injection; Broken Authentication issues with authentication and session management; Sensitive Data Exposure due to inadequate protection; XML External Entities (XXE) exploiting vulnerable XML processors; and Broken Access Control allowing unauthorized access.
40. How do you test for injection vulnerabilities in web applications?
Ans:
- Testing for injection vulnerabilities involves ensuring that user inputs are properly sanitized and using automated scanners like SQLmap to detect injection flaws.
- Manually inject payloads into input fields to observe responses and conduct a thorough review of the source code to identify unsafe data handling practices.
- Ensure the application uses parameterized queries or prepared statements, analyzes error messages for information disclosure, and performs comprehensive penetration testing to simulate real-world attack scenarios and strengthen security.
41. What security measures do you implement to prevent cross-site request forgery (CSRF)?
Ans:
Implement several key measures to prevent cross-site request forgery (CSRF):
- Implement.
- Use anti-CSRF tokens, which are unique for each user session and included in every form submission.
- Validate these tokens on the server side to ensure requests are legitimate.
- Employ SameSite cookies to restrict how cookies are sent with cross-site requests and use secure, HTTP-only cookies.
- Implement strong user authentication and require re-authentication for sensitive actions.
42. How do you prevent SQL injection attacks in web applications?
Ans:
Preventing SQL injection attacks involves using parameterized queries or prepared statements to separate SQL code from data, thus preventing malicious input from being executed as commands. Utilize Object-Relational Mapping (ORM) frameworks to abstract direct SQL queries. Validate and sanitize all user inputs to filter out harmful characters. Implement proper error handling to avoid disclosing database details to users.
43. How do you ensure that web applications are resistant to brute force attacks?
Ans:
Web applications are shielded from brute force attacks by enforcing the use of strong, complex passwords and require regular password changes. Implement account lockout mechanisms that temporarily deactivate accounts after several failed login attempts. Use CAPTCHA or reCAPTCHA to distinguish human users from automated scripts. Utilize multi-factor authentication to add a degree of protection. (MFA).
44. What are the common threats to network security?
Ans:
Common threats to network security include:
- Malware (viruses, worms, and ransomware).
- Phishing attacks that deceive users into revealing sensitive information.
- Distributed Denial-of-Service (DDoS) attacks that overwhelm network resources.
Man-in-the-middle (MitM) attacks intercept and alter communications, while insider threats involve malicious or negligent actions by employees. Exploiting software or hardware vulnerabilities, inadequate security configurations, or weak passwords also pose significant risks.
45. How do you secure wireless networks?
Ans:
- Securing wireless networks involves using strong encryption protocols like WPA3 and robust authentication methods such as 802.1X.
- Disable SSID broadcasting and change the default SSID to a unique name.
- Apply MAC address filtering to restrict network access to known devices.
- Continuously monitor for unauthorized access points and suspicious activity and ensure the physical security of network equipment to prevent tampering.
46. Could you elucidate the distinction between a firewall and an intrusion detection system (IDS)?
Ans:
A firewall and an intrusion detection system (IDS) serve different roles in network security. A firewall monitors and controls network traffic, including inbound and outbound, according to preset security criteria, serving as a barrier to trusted and untrusted networks. It blocks unauthorized access while allowing legitimate communication. An IDS, however, is a monitoring system that detects and alerts administrators to potential security incidents by looking for indications of malicious activity inside network traffic or policy violations.
47. How do you secure remote access to corporate networks?
Ans:
Securing remote access to corporate networks involves using Virtual Private Networks (VPNs) to encrypt data between remote users and the corporate network. Enforce robust authentication methods like multi-factor authentication (MFA) to verify user identities. Ensure remote devices comply with corporate security policies by using endpoint security solutions such as antivirus software and firewalls. Regularly update and patch remote access software to address vulnerabilities.
48. Can you explain the concept of VPN and its role in securing network communications?
Ans:
- A Virtual Private Network (VPN) creates a secure, encrypted connection over a less secure network, such as the Internet, enabling people to communicate with their gadgets as though they were directly linked to the private.
- VPNs play a crucial role in securing network communications by encrypting data transmissions and protecting sensitive information from interception and eavesdropping.
49. How do you detect and mitigate denial-of-service (DoS) attacks?
Ans:
- Detecting and mitigating denial-of-service (DoS) attacks involves employing technologies for network monitoring to find odd patterns in traffic.
- Rate limiting controls the number of requests a server can handle within a certain timeframe, and traffic filtering blocks traffic from known malicious IP addresses.
- Load balancers distribute traffic across multiple servers, reducing the impact of an attack.
- Maintain redundancy and scalability in the network infrastructure to ensure availability and collaborate with internet service providers (ISPs) for additional support and mitigation services.
50. What are the key security considerations when migrating to the cloud?
Ans:
When migrating to the cloud, consider several key security aspects—Encrypt data both in transit and at rest to protect sensitive information. Implement robust access controls and identity management to restrict access to authorized users only and use multi-factor authentication (MFA) to enhance security. Regularly audit and monitor cloud environments for suspicious activity and compliance with security policies. Ensure cloud providers comply with relevant security standards and regulations.
51. How do you secure data stored in the cloud?
Ans:
To secure data stored in the cloud, employ robust encryption for both data in transit and at rest using robust encryption protocols. Securely manage encryption keys, possibly through a cloud provider’s key management services (KMS). Regularly back up data to prevent loss and use data masking or tokenization for susceptible information.
52. Can you explain the shared responsibility model in cloud security?
Ans:
- In cloud security, the shared responsibility paradigm describes the division of security tasks between cloud service providers, including the physical data centers and underlying hardware and software.
- Customers, on the other hand, are responsible for securing their data, applications, identity and access management, and network configurations within the cloud.
- This model helps organizations understand their roles and responsibilities in maintaining cloud security.
53. What measures do you take to prevent unauthorized access to cloud resources?
Ans:
To prevent unauthorized access to cloud resources:
- Enforce strong identity and access management (IAM) policies.
- Use unique, strong passwords and require multi-factor authentication (MFA) for all accounts.
- Using the least privilege concept, assign roles and permissions.
Ensuring users have only the access necessary for their tasks. Regularly audit access permissions and revoke any unnecessary or outdated privileges.
54. How do you monitor cloud environments for security threats?
Ans:
Monitoring cloud environments for security threats involves using automated tools and best practices. Utilize cloud-native security services such as AWS CloudTrail, Azure Security Center, or Google Cloud Security Command Center to track and log activities. Review logs regularly and conduct threat hunting to identify anomalies. Ensure continuous monitoring and incident response plans are in place to address detected threats quickly.
55. Can you explain the concept of cloud security posture management (CSPM)?
Ans:
Cloud Security Posture Management (CSPM) involves tools and practices to ensure that a cloud environment’s security configuration aligns with best practices and compliance requirements. CSPM solutions continuously monitor cloud resources, identify misconfigurations, and provide remediation guidance. They help prevent security breaches by ensuring proper configurations of cloud services, managing access controls, and enforcing security policies.
56. What steps do you take to secure serverless architectures?
Ans:
- Securing serverless architectures involves several best practices.
- Conduct thorough code reviews and use static and dynamic analysis tools to ensure the security of the code deployed in serverless functions.
- Securely manage sensitive data using environment variables and avoid hardcoding secrets in the code.
- Monitor and log function activity to detect and respond to potential security incidents.
- Utilize network security measures like virtual private cloud (VPC) configurations and secure APIs with authentication and authorization mechanisms.
57. How do you manage encryption keys in a cloud environment?
Ans:
- Managing encryption keys in a cloud environment involves using critical management services (KMS) provided by the cloud provider.
- These services facilitate the secure creation, storage, and management of encryption keys.
- Implement role-based access control (RBAC) to restrict access to keys, ensuring only authorized users and services can access them.
- Monitor critical usage logs to detect unauthorized access attempts and integrate KMS with other security tools to automate key management processes and enhance security.
58. How do you handle sensitive data during a VAPT engagement?
Ans:
During a Vulnerability Assessment and Penetration Testing (VAPT) engagement, handle sensitive data with utmost care. Ensure that sensitive information encountered is encrypted both in transit and at rest. Use secure communication channels for data transfer and ensure that all testing tools and environments comply with data protection standards. Obtain explicit consent from the client before accessing or testing any systems containing sensitive data.
59. What are the legal and ethical considerations in penetration testing?
Ans:
Penetration testing must follow strict legal and ethical guidelines. To ensure legal authorization, obtain explicit written consent from the client before starting any testing activities. Protect client confidentiality by safeguarding all findings and not disclosing sensitive information to unauthorized parties. Follow ethical guidelines, such as those set by the EC-Council’s Code of Ethics or other relevant professional standards, to ensure responsible and professional conduct during testing.
60. What steps do you take to ensure the integrity of evidence collected during a penetration test?
Ans:
- Ensuring the integrity of evidence collected during a penetration test involves several steps.
- Maintain a transparent chain of custody by documenting who handled the evidence, when, and under what circumstances.
- Use write-protected storage devices to prevent tampering and ensure that evidence is collected using forensic methods to preserve its integrity.
- Securely store the evidence in a controlled environment with restricted access.
- Generate cryptographic hashes of digital evidence to detect any alterations.
61. What measures do you take to prevent future security incidents?
Ans:
- To prevent future security incidents, establish a comprehensive security strategy that includes regular Finding and fixing such vulnerabilities, use of penetration testing, vulnerability scans, and security assessments.
- Create and implement strict security guidelines and rules. I am updating them regularly.
- Provide continuous security training and awareness programs for employees to minimize human error.
- Deploy advanced security technologies like intrusion detection/prevention systems (IDPS), firewalls, and endpoint protection. Keep all software and systems updated and patched to fix known vulnerabilities.
62. How do you ensure continuous improvement in incident response capabilities?
Ans:
Continuous improvement in incident response capabilities involves conducting regular drills and tabletop exercises to test and refine response plans. Perform post-incident reviews to evaluate the effectiveness of responses and identify areas for improvement. Regularly update the incident response plan to incorporate lessons learned and emerging best practices. Provide ongoing training and certification for the incident response team to keep their skills current.
63. How do you ensure the security of cloud-based applications?
Ans:
To ensure the security of cloud-based applications, enforce robust identity and access management (IAM) policies based on the principle of least privilege. Regularly update and patch applications and underlying infrastructure. Deploy web application firewalls (WAFs) and intrusion detection/prevention systems (IDPS) to protect against attacks. Conduct regular security assessments, including vulnerability scans and penetration tests.
64. Can you explain the concept of input validation and its importance in web application security?
Ans:
- Input validation ensures that user input is correctly formatted and free from potentially harmful data before processing by the application.
- It is crucial for web application security because it helps prevent attacks like SQL injection, cross-site scripting (XSS), and buffer overflow attacks.
- By validating input, you ensure that only expected and safe data is processed, reducing the risk of executing malicious payloads.
- Implementing both client-side and server-side validation adds an extra layer of security, with client-side validation providing immediate feedback to users and server-side validation maintaining data integrity even if client-side validation is bypassed.
65. How do you protect sensitive data in web applications?
Ans:
Protecting sensitive data in web applications involves using robust encryption mechanisms for both at-rest and in-transit information. Implement secure authentication mechanisms such as multi-factor authentication (MFA) to ensure only authorized users can access sensitive information. Apply access controls based on the principle of least privilege, limiting user permissions to the necessary minimum.
66. What security headers can be used to enhance web application security?
Ans:
Several security headers enhance web application security. The Content Security Policy (CSP) header prevents XSS attacks by specifying which content sources are allowed. The Strict-Transport-Security (HSTS) header ensures browsers connect to the server over HTTPS, preventing man-in-the-middle attacks. The X-Content-Type-Options header prevents browsers from MIME-sniffing and executing malicious content. The X-Frame-Options header protects against clickjacking attacks by restricting how the site can be framed.
67. How do you prevent session fixation attacks?
Ans:
To prevent session fixation attacks:
- Generate a new session ID whenever a user authenticates, avoiding the reuse of an existing session ID.
- Implement secure cookie attributes like HttpOnly and Secure to protect session cookies from client-side scripts and ensure they are transmitted over HTTPS connections.
- Use SameSite cookie attributes to restrict how cookies are sent with cross-site requests.
68. How do you secure IoT devices on a network?
Ans:
- Securing IoT devices on a network involves changing default credentials to strong, unique passwords.
- Regularly update and patch devices to address vulnerabilities. Segment IoT devices on a separate network from critical systems and data to limit potential damage from a compromised device.
- Implement strong encryption for data transmitted between IoT devices and other systems.
- Use network security measures like firewalls and intrusion detection/prevention systems (IDPS) to monitor and control traffic to and from IoT devices.
69. How do you monitor network traffic for security threats?
Ans:
Monitoring network traffic for security threats involves using a combination of tools and techniques. Deploy intrusion detection and prevention systems (IDPS) to analyze network traffic and identify suspicious patterns. Use network traffic analysis tools to capture and inspect data packets for signs of malicious activity. Regularly review and correlate log data to detect anomalies. Establish baselines of normal network behaviour to identify deviations indicating a threat.
70. Can you explain the difference between compliance-driven and risk-driven security?
Ans:
Compliance-driven security focuses on meeting regulatory requirements, standards, and guidelines to make sure a company complies with its legal and contractual obligations. It involves implementing specific controls and procedures mandated by laws and industry standards, often with the primary goal of passing audits and avoiding penalties. Risk-driven security, on the other hand, prioritizes identifying and mitigating the most significant threats to an organization based on its unique risk profile.
71. How do you ensure that identified vulnerabilities are remediated effectively?
Ans:
To guarantee effective remediation of identified vulnerabilities:
- Establish a structured vulnerability management process.
- Assign responsibility for remediation to the appropriate teams with clear deadlines.
- Utilize patch management systems for timely application of security updates.
- Verify the effectiveness of remediation through follow-up assessments.
- Document the remediation process thoroughly for compliance and future reference, and continuously review and update remediation procedures to incorporate lessons learned.
72. How do you ensure compliance with relevant regulations in a cloud environment?
Ans:
Ensure compliance with relevant regulations in a cloud environment by first understanding specific regulatory requirements applicable to your industry and organization. Work closely with your cloud service provider to ensure that the products they supply abide by the law. Ensure their services support compliance. Implement robust access controls, encryption, and data protection measures. Regularly audit and monitor your cloud environment for compliance with regulatory standards.
73. What steps do you take to secure third-party software?
Ans:
To secure third-party software:
- Conduct a thorough security assessment, reviewing the vendor’s security practices and history of security incidents.
- Ensure the software receives regular updates and patches.
- Implement access controls to restrict permissions to the minimum required.
- Monitor the software for any signs of compromise and maintain an inventory of third-party software with associated risks.
- Establish a response plan for addressing vulnerabilities or security incidents involving third-party software.
74. How do you ensure client confidentiality during VAPT activities?
Ans:
Ensure client confidentiality during Vulnerability Assessment and Penetration Testing (VAPT) by obtaining explicit written consent and clearly defining the testing scope. Use secure communication channels and encrypted storage for all engagement-related data. Restrict authorized personnel’s access to sensitive information And anonymize client data where possible.
75. What are the legal and ethical considerations in penetration testing?
Ans:
Legal and ethical considerations in penetration testing include:
- Obtaining explicit written consent.
- Defining testing scope to avoid unauthorized access or unintended damage.
- Protecting client confidentiality by safeguarding findings.
Adhere to relevant laws, regulations, and ethical guidelines such as those outlined by professional organizations. Maintain client confidentiality and avoid disclosing sensitive information to unauthorized parties.
76. How do you ensure the integrity of evidence collected during a penetration test?
Ans:
Ensure the integrity of evidence collected during a penetration test by maintaining a clear chain of custody, using write-protected storage devices, and employing forensic methods. Store evidence securely in a controlled environment with restricted access. Generate cryptographic hashes of digital evidence to detect alterations. Document all actions taken during evidence collection for a clear audit trail.
77. What measures do you take to prevent future security incidents?
Ans:
Preventing future security incidents involves implementing a comprehensive security strategy that includes regular assessments, vulnerability scans, and penetration testing. Enforce robust security policies, provide continuous security training, and deploy advanced security technologies like intrusion detection systems. Keep all software and systems updated and patched, implement strong access controls and authentication mechanisms, and continuously monitor and log activities.
78. How do you manage encryption keys in a cloud environment?
Ans:
- Manage encryption keys in a cloud environment utilizing the cloud provider’s critical management services.
- Implement role-based access control to restrict key access to authorized users.
- Regularly rotate keys and enforce strong usage policies.
- Monitor essential usage logs for unauthorized access attempts and integrate key management with other security tools for automation.
79. Can you explain the concept of input validation and its importance in web application security?
Ans:
Input validation ensures user input is correctly formatted and free from potentially harmful data before processing, which is crucial for preventing attacks like SQL injection and cross-site scripting. Implement client-side and server-side validation for an added layer of security, providing immediate feedback to users and maintaining data integrity.
80. How do you protect sensitive data in web applications?
Ans:
Protect sensitive data in web applications using strong encryption for data in transit and at rest. Implement secure authentication mechanisms like multi-factor authentication and apply access controls based on the principle of least privilege. Follow secure coding practices, regularly audit and monitor access to sensitive data, and employ data masking or tokenization for susceptible data fields.
81. Which security headers can be employed to bolster web application security?
Ans:
- Various security headers can enhance the security of web applications. The Content Security Policy (CSP) header helps thwart XSS attacks by dictating permissible content sources.
- The Strict-Transport-Security (HSTS) header ensures that browsers connect via HTTPS, thus deterring man-in-the-middle attacks.
- The X-Content-Type-Options header prevents browsers from executing malicious content by MIME-sniffing.
- To safeguard against clickjacking attacks, the X-Frame-Options header limits how the site can be framed.
82. How can session fixation attacks be mitigated?
Ans:
- To thwart session fixation attacks, generate a new session ID upon user authentication to avoid reusing existing session IDs.
- Secure cookie attributes, such as HttpOnly and Secure, safeguard session cookies from client-side scripts and ensure transmission over HTTPS.
- Employ SameSite cookie attributes to constrain cookie transmission with cross-site requests.
- Implement session timeouts to curtail inactive session durations, thus minimizing the opportunity window for attackers.
- Employ monitoring mechanisms to detect and respond to suspicious session activities.
83. What measures are involved in securing IoT devices within a network?
Ans:
Securing IoT devices on a network encompasses several essential steps. Change default credentials to robust, unique passwords. Regularly update and patch devices to rectify vulnerabilities. Segregate IoT devices onto a separate network from critical systems and data to mitigate potential damages from compromised devices. Enforce strong encryption for data exchanged between IoT devices and other systems.
84. How can network traffic be monitored for security threats?
Ans:
Monitoring network traffic for security threats necessitates leveraging a blend of tools and techniques. Employ intrusion detection and prevention systems (IDPS) to analyze network traffic and identify suspicious patterns. Utilize network traffic analysis tools to capture and inspect data packets for signs of malicious activity. Deploy Security Information and Event Management (SIEM) systems to compile and analyze logs from various network devices and security tools.
85. Elaborate on the distinction between compliance-driven and risk-driven security approaches.
Ans:
- Compliance-driven security centers on adhering to regulatory requirements and standards to fulfill legal and contractual obligations.
- It entails implementing specific controls and procedures mandated by laws and industry standards, primarily aiming to pass audits and circumvent penalties.
- Conversely, risk-driven security prioritizes the identification and mitigation of the most critical threats based on an organization’s risk profile.
- It involves evaluating potential risks, understanding their impact and likelihood, and deploying controls to address the most significant vulnerabilities.
86. How can the effective remediation of identified vulnerabilities be ensured?
Ans:
- Establish a systematic vulnerability management process.
- Prioritize vulnerabilities based on severity, potential impact, and exploitability.
- Assign responsibility for remediation to suitable teams with well-defined deadlines.
- Utilize patch management systems to promptly apply security updates.
- Validate the efficacy of remediation through subsequent assessments.
- Thoroughly document the remediation process for compliance adherence and future reference.
87. Enumerate the principal security considerations during a migration to the cloud.
Ans:
Critical security considerations during a cloud migration encompass implementing robust access controls and authentication mechanisms, encrypting data as it’s being transported and stored, and making sure it complies with relevant laws and guidelines pertinent regulations and standards. Organizations should also evaluate the security practices of cloud service providers, delineate clear data ownership and responsibility boundaries, and institute robust monitoring and logging capabilities.
88. How can data stored in the cloud be adequately secured?
Ans:
- Employ strong encryption for information in transit and at rest.
- Implement access controls and authentication mechanisms to restrict data access to authorized users solely.
- Regularly update and patch cloud infrastructure and services to mitigate vulnerabilities.
- Leverage native cloud security features such as encryption key management and data loss prevention tools.
- Educate personnel on secure data handling practices and enforce adherence to security policies and procedures.
89. Explain the shared responsibility model in cloud security.
Ans:
The shared responsibility model in cloud security delineates responsibilities between cloud service providers (CSPs) and their customers. CSPs are accountable for securing the underlying cloud infrastructure, encompassing physical facilities, networking, and virtualization. This model aids organizations in comprehending their security obligations when utilizing cloud services, facilitating a collaborative approach to cloud security.
90. How can compliance with pertinent regulations be ensured within a cloud environment?
Ans:
To guarantee compliance with relevant regulations within a cloud environment, first, ascertain the specific regulatory requirements applicable to the industry and organization. Collaborate closely with the cloud service provider to verify the alignment of their services with compliance endeavours. Implement robust access controls, encryption measures, and data protection protocols. Regularly audit and monitor the cloud environment for compliance with regulatory standards.






