
Penetration testing, commonly known as pen testing, is a pivotal proactive security assessment methodology employed by organizations to evaluate the robustness of their IT infrastructure, networks, and applications. This approach involves emulating real-world cyber attacks to uncover potential vulnerabilities that could be exploited by malicious entities. The process typically follows a systematic approach, commencing with reconnaissance and information gathering, progressing to vulnerability identification and exploitation, and culminating in comprehensive reporting.
1. What is penetration testing, and why is it important?
Ans:
A simulated cyberattack is used in penetration testing to examine computer systems for vulnerabilities that might be exploited. Penetration testing is used to supplement a web application firewall in the web application security. It’s crucial because it evaluates the possible consequences of security breaches, finds security flaws in a system’s defenses that attackers may exploit, and confirms the efficacy of security measures that are already in place.
2. Explain the different types of penetration testing?
Ans:
- Three types of penetration testing exist: black-box, white-box, and slate-box. Black-box testing emulates an external attack, devoid of prior knowledge about the system.
- White-box testing provides the tester with a complete understanding of the structure, including network plates, source law, and IP addressing information, offering a thorough assessment of internal security.
- Grey-box testing is a combination of both, where the tester has partial knowledge of the system. Each type offers unique advantages and is chosen based on the specific pretensions of the test.
3. What are some common tools used in penetration testing?
Ans:
Depending on the type of test they’re doing, penetration testers employ a range of tools. Nmap for network mapping, Metasploit for vulnerability analysis, Wireshark for packet analysis, Burp Suite for web operation testing, and OWASP ZAP for security scanning are a few examples of broad tools. These tools support vulnerability correlation, attack execution, and post-exploitation operations. Penetration testers must know how to use the tools and be conversant with them.
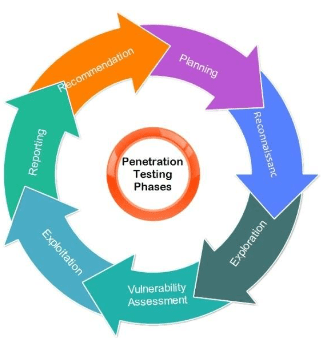
4. Describe the phases of a penetration test.
Ans:
- A penetration test typically consists of five phases: planning, scanning, gaining access, maintaining access, and analysis/reporting. Planning involves defining the test’s scope and objectives.
- Surveillance is the phase where information about the target is collected. Scanning involves relating live hosts, open anchorages, and services.
- Gaining access refers to exploiting vulnerabilities to enter the system. Maintaining access involves ensuring a patient presence in the exploited system.
- Eventually, analysis and reporting involve collecting findings, vulnerabilities, exploited systems, and recommended countermeasures.
5. How can one stay updated with the latest security vulnerabilities?
Ans:
Staying streamlined with the most security vulnerabilities is pivotal for a penetration tester. This can be achieved by regularly checking sanctioned vulnerability databases like the National Vulnerability Database( NVD) or CVE List, following security forums and newsletters, sharing in security conferences, and being active in the cybersecurity community. Using automated tools to check for the rearmost vulnerabilities and subscribing to RSS feeds from trusted security news sources are also effective strategies.
6. What’s the difference between a vulnerability assessment and penetration testing?
Ans:
| Aspect | Vulnerability Assessment | Penetration Testing | |
| Purpose |
Identifying and quantifying vulnerabilities present in IT infrastructure, networks, and systems. |
Simulating real-world cyber attacks to assess the security posture of systems and networks. | |
| Methodology | Scanning systems and networks for known vulnerabilities, misconfigurations, and weaknesses. | Attempting to exploit identified vulnerabilities in a controlled manner to simulate various attack scenarios. | |
| Scope |
Identifying vulnerabilities without actively exploiting them. |
Actively exploiting vulnerabilities to assess the effectiveness of security controls and incident response. | |
| Outcome | Report highlighting identified vulnerabilities, severity levels, and recommendations for remediation. | Detailed findings on exploited vulnerabilities, potential damage, and recommendations for enhancing security. |
7. How is sensitive information discovered during a penetration test handled?
Ans:
Handling sensitive information discovered during a penetration test requires strict adherence to ethical guidelines and legal conditions. It’s essential to maintain confidentiality and ensure that all sensitive data is securely handled and reported only to the authorized labor force. This involves using translated storehouse and communication channels for sensitive data, following a predefined exposure process, and ensuring that all data is duly disposed of after the test.
8. What is social building, and how can protection against it be ensured?
Ans:
Social building is a control strategy that abuses human mistakes to pick up private data and get to resources. It depends on mental control, deceiving people into breaking typical security strategies. To watch against it, organizations ought to execute solid security approaches, conduct normal security mindfulness preparation, uphold the guidelines of the slightest benefit, and energize a culture of skepticism and confirmation.
9. How might one handle critical helplessness encountered during a test?
Ans:
In a notable entrance test, a significant SQL injection vulnerability was discovered, potentially allowing an attacker to access the entire database, including sensitive user data. The steps taken to identify the vulnerability, including the specific payload used, were promptly documented. Following ethical guidelines, the issue was confidentially reported to the organization’s security team, providing detailed findings and recommended mitigations.
10. What is the noteworthiness of the OSI demonstrated in infiltration testing?
Ans:
- The OSI (Open Frameworks Interconnection) show is a conceptual system utilized to get it arranged intelligently in seven layers: physical, information interface, arrange, transport, session, introduction, and application.
- For entrance analyzers, understanding the OSI show is significant since it makes a difference in distinguishing potential vulnerabilities at each layer and creating fitting procedures for testing.
- For this case, arrange layer vulnerabilities might tend to have distinctive apparatuses and methods compared to application layer vulnerabilities.
- Information on the OSI demonstrates that it helps in viable communication with arranged directors and designers when announcing and moderating vulnerabilities.
11. How should one approach testing web applications for security vulnerabilities?
Ans:
Testing web applications for security vulnerabilities includes an efficient approach that begins with data gathering to get to the application’s engineering and innovation stack. At that point, continued with robotized filtering, utilizing apparatuses like OWASP Destroy and Burp Suite to distinguish potential vulnerabilities. Manual testing takes after to abuse distinguished vulnerabilities, centering on common issues like SQL infusion, XSS, CSRF, and record transfer vulnerabilities.
12. What is an “untrue positive” in infiltration testing, and how should it be handled?
Ans:
- A wrong positive in entrance testing alludes to a detailed defenselessness that, upon assist examination, is not really exploitable or does not pose a genuine risk to the framework.
- Untrue positives can devour critical time and assets if not dealt with productively. To oversee them, first confirm the discoveries utilizing manual testing procedures to affirm whether the powerlessness is veritable.
- If it’s decided to be an untrue positive, report the discoveries and the confirmation prepare to illuminate the advancement or security group, guaranteeing they center on genuine vulnerabilities.
- Diminishing untrue positives is pivotal for maintaining the validity of the testing process.
13. what a “turn” is in entrance testing?
Ans:
In penetration testing, pivoting refers to using a compromised system to launch attacks on other systems within the same network. This technique allows testers to access segments not directly reachable from the attacker’s initial entry point, helping identify advanced vulnerabilities that could be exploited in a real-world attack.
14. How should vulnerabilities found during entrance tests be prioritized?
Ans:
- Prioritizing vulnerabilities found amid an infiltration test includes assessing the potential effect and exploitability of each helplessness.
- Variables such as the ease of abuse, the level of get-to required, the complexity of the assault, and the potential effect on secrecy, astuteness, and accessibility are considered.
- Vulnerabilities are regularly positioned utilizing a seriousness scale (e.g., basic, tall, medium, moo) based on these variables.
- This prioritization makes a difference in organizations apportioning their assets successfully, tending to the most basic vulnerabilities to begin with to decrease the general chance of the system.
15. What are a few common strategies for dodging location amid an entrance test?
Ans:
Avoiding location during an entrance test includes utilizing stealth strategies to mirror progressed attackers. This incorporates throttling assault endeavors to maintain a strategic distance from activating rate limits or cautions, utilizing intermediary chains or VPN administrations to cloud the beginning of the assault, utilizing encryption to dodge payload location, and leveraging less boisterous assault vectors such as CSRF or SSRF.
16. What’s the difference between symmetric and asymmetric encryption in penetration testing?
Ans:
- Symmetric encryption employs the same key for both encryption and unscrambling, making it quick and reasonable for scrambling expansive volumes of information.
- Deviated encryption employs a match of keys (open and private) where one key scrambles the data, and the other decodes it, including an additional layer of security but at the taken toll of speed.
- In entrance testing, understanding these encryption sorts is pivotal when assessing the security of information transmission and capacity.
- For occasion, interference or decoding information can abuse vulnerabilities in the Execution of these encryption methods.
17. How do entrance analyzers utilize the Miter ATT&CK framework?
Ans:
The MITRE ATT&CK framework is a comprehensive guide to attacker strategies and techniques, helping penetration testers understand and simulate real-world attack scenarios. Aligning testing methods with this framework ensures thorough assessments of known attack vectors and techniques. It also facilitates clear communication of findings and recommendations to security teams, enhancing the effectiveness of the testing process.
18. What is the significance of scripting in entrance testing?
Ans:
- Scripting is crucial in infiltration testing for mechanizing tedious errands, customizing assaults to fit each target’s interesting setting, and handling information proficiently.
- Scripting dialects like Python, Bash, or PowerShell empower analyzers to rapidly create or adjust scripts to exploit vulnerabilities, parse yield from other instruments, and robotize the checking and misuse handling.
- This does not merely increment the test’s productivity but, moreover, permits more advanced testing procedures that can adjust to the complexities of advanced systems and applications.
19. How does arranged division influence entrance testing?
Ans:
Network division, the hone of separating an organization into smaller, sensible subnetworks, altogether impacts entrance testing by constraining the scope of an assault surface. The division acts as a control component, so indeed, if an aggressor compromises one fragment, it’s challenging to rotate to other parts of the organization. Amid entrance testing, this requires the analyzer to utilize progressed strategies and techniques to overcome division controls.
20. What part does physical security play in infiltration testing?
Ans:
Physical security is a fundamental angle of infiltration testing, frequently ignored in favor of advanced dangers. Unauthorized physical access to gadgets can bypass indeed the most advanced cybersecurity measures. Infiltration analyzers, in some cases, conduct physical security evaluations, counting endeavors to get to limited ranges, social building assaults against the workforce, and assessing the security of physical gadgets against altering.
21. How is the security of cloud-based administrations evaluated in an entrance test?
Ans:
- Assessing the security of cloud-based administrations requires an understanding of cloud engineering and the shared duty show.
- Infiltration analyzers center on misconfigurations, insufficient get-to controls, and disgraceful information capacity hones that might lead to information breaches.
- Devices and strategies are chosen based on the particular cloud stage (AWS, Purplish blue, GCP) and incorporate both computerized looks and manual testing to distinguish vulnerabilities.
- Furthermore, analyzers must follow to the cloud provider’s arrangements for infiltration testing to maintain a strategic distance from lawful issues or benefit disruption.
22. What is the importance of an out-of-band assault in infiltration testing?
Ans:
An out-of-band (OOB) assault is critical in infiltration testing as it includes procedures that utilize distinctive systems or conventions to execute or recover the comes about of the assault, regularly bypassing conventional security measures. This sort of assault can illustrate how information can be exfiltrated or commands executed without coordinating interaction with the helpless framework over its essential communication channel.
23. How is an infiltration test conducted on a versatile application?
Ans:
- Mobile app penetration testing involves gathering app information, performing static analysis with tools like MobSF, and conducting dynamic analysis to observe runtime operations.
- Analyzers, too, center on the app’s information capacity and transmission security, looking for vulnerabilities like uncertain information capacity, frail encryption, and inappropriate session handling.
- Emulators or physical gadgets are utilized to associate with the application in different situations, recreating real-user scenarios.
- The test concludes with a comprehensive report specifying vulnerabilities and giving remediation guidance.
24. Clarify how to test for SQL infusion vulnerabilities.
Ans:
Testing for SQL infusion vulnerabilities includes endeavoring to embed or “infuse” SQL commands into input areas, inquiry parameters, or API endpoints to see if the backend database executes those commands. This can uncover whether an application legitimately sanitizes its inputs. Devices like SQLMap can computerize this handle, recognizing injectable focuses. Manual testing might include making particular payloads to bypass input approval components.
25. What techniques should be employed when performing an entrance test?
Ans:
When conducting infiltration tests, established methodologies such as OWASP for web applications, PTES for general penetration testing, and ISSAF for a more detailed approach are adhered to. These frameworks provide a structured and thorough process, encompassing pre-engagement intelligence gathering, vulnerability analysis, exploitation, post-exploitation, and reporting.
26. Depict how to test for Cross-Site Scripting (XSS) vulnerabilities.
Ans:
- Testing for Cross-Site Scripting (XSS) vulnerabilities involves injecting JavaScript into web applications to assess browser execution, typically in input fields or URL parameters.
- The point is to recognize places where client input is not legitimately sanitized or gotten away, permitting scripts to run.
- Both intelligent and put-away XSS vulnerabilities are looked for after, with analyzers utilizing a combination of manual procedures and mechanized devices like XSSer to reveal potential issues.
- Successful testing moreover includes checking for Substance Security Arrangement (CSP) usage that can relieve XSS risks.
27. How can the legitimacy and ethics of infiltration testing exercises be guaranteed?
Ans:
Ensuring that entrance testing exercises are legitimate and moral includes getting express, composed consent from the substance that claims the target framework sometime recently starting any testing. This authorization should lay out the scope of the test, counting what frameworks can be focused on, testing strategies endorsed, and any other pertinent lawful or operational limitations. All through the test, followed the agreed-upon scope to maintain a strategic distance from unauthorized access to frameworks or information.
28. What is fuzzing, and how is it utilized in entrance testing?
Ans:
- Fuzzing is a testing procedure that involves naturally sending a wide range of inputs to a framework to trigger an unforeseen behavior or crash, showing potential defenselessness.
- In infiltration testing, fuzzing is utilized to distinguish security shortcomings in program applications or frameworks without knowing their inner workings.
- It is especially compelling for revealing buffer flood, XSS, SQL infusion, and arrange string vulnerabilities.
- Entrance analyzers utilize different fuzzing devices and systems to robotize the handle, methodically testing with twisted or arbitrary information to find vulnerabilities that attackers might abuse.
29. How can one remain updated with the most recent security tools and techniques?
Ans:
Staying upgraded with the most recent security apparatuses and procedures involves a combination of ceaseless learning and community engagement. Participating in security gatherings, conferences, webinars, and workshops, as well as following legitimate security blogs and bulletins, is essential. Engaging with the open-source community and contributing to security projects provides insights into developing trends and tools.
30. What is the contrast between a ruddy group and an entrance testing team?
Ans:
- The essential distinction between a ruddy group and an entrance testing group lies in their scope, goals, and approach.
- A ruddy group conducts a full-spectrum, multi-layered assault recreation that outlines to a degree how well a company’s individuals, systems, applications, and physical security controls can withstand an assault from a real-life foe.
- In differentiation, an infiltration testing group centers more than just on distinguishing vulnerabilities in the organization’s computerized framework and applications, frequently with a characterized scope and without the component of astonishing or the comprehensive approach of a ruddy team.
31. Clarify the handle of benefit acceleration in entrance testing.
Ans:
- Privilege acceleration is the handling process of misusing a defenselessness in a framework or application to gain unauthorized access to assets that are regularly confined to the application or client.
- There are two sorts of benefit acceleration: vertical and level. Vertical (or benefit height) acceleration includes gaining higher-level benefits, such as regulatory rights, from a lower-favored account.
- Level heightening includes accessing another user’s assets at the same benefit level. In entrance testing, this preparation is significant for illustrating the effect of defenselessness by showing how an assailant may pick up lifted access, subsequently permitting the distinguishing proof and relief of noteworthy security dangers inside the system.
32. When might bypassing a Web Application Firewall (WAF) be necessary during a test?
Ans:
In one circumstance, a Web Application Firewall (WAF) effectively blocked common penetration testing techniques and tools. To bypass the WAF, intensive inquiries were conducted to determine the WAF’s execution and known weaknesses. Subsequently, testing payloads were customized to be less detectable by the WAF’s pattern recognition algorithms. This involved breaking down attack vectors into smaller, less noticeable components and using obfuscation techniques to conceal malicious payloads.
33. What are a few moral considerations to keep in mind during penetration testing?
Ans:
- Ethical considerations in entrance testing are vital to maintaining belief, legitimacy, and polished skill. First, getting express written consent from the legitimate proprietor of the frameworks and information recently tested is basic to guarantee legitimacy.
- Characterizing a clear scope to dodge unauthorized testing on frameworks not included in the engagement is vital. It’s too imperative to regard information security, guaranteeing any delicate data obtained amid the test is taken care of and detailed safely.
- Finally, capable divulgence is key; vulnerabilities must be detailed in a way that permits the organization to remediate them sometime soon after they are uncovered freely, if at all, to dodge supporting potential attackers.
34. What steps should be taken if a zero-day vulnerability is found in a penetration test?
Ans:
Discovering zero-day vulnerabilities requires a cautious and capable approach. Initially, the vulnerability should be reported in detail, including how it was discovered, its impact, and potential exploitation methods. This information is crucial for developing a fix or workaround. The vulnerability should then be promptly reported to the client or the software vendor, following responsible disclosure practices. This typically involves providing them with a reasonable period to address the issue before any public disclosure is made.
35. How does an infiltration analyzer survey the viability of an Occurrence Reaction (IR) team?
Ans:
Assessing the viability of an Occurrence Reaction (IR) group includes recreating real-life assault scenarios that trigger security episodes, subsequently enacting the IR team’s reaction. The entrance analyzer carefully watches and records how rapidly the IR group recognizes and reacts to the occurrence, its methods for confining and relieving dangers, and its capacity to collect and analyze information related to the assault.
36. What is a turn assault, and how is it utilized in infiltration testing?
Ans:
- A rotated assault in infiltration testing is a procedure for gaining more profound insight by misusing a framework or arranged portion that the analyzer has already compromised.
- Once the introductory get-to is picked up, the compromised framework serves as a launchpad for more profound assaults into the arrangement, permitting the analyzer to “rotate” and misuse other frameworks that were not straightforwardly available from the starting section point.
- This method is significant for mimicking how an aggressor seems to move along the side inside an organization, bypassing internal security controls and getting to profitable targets.
37. Depict the preparation of conducting a remote organized infiltration test.
Ans:
Conducting a remote organized infiltration test includes a few key steps. At first, the analyzer performs surveillance to distinguish remote systems and their characteristics, such as Benefit Set Identifiers (SSIDs) and security conventions utilized (WEP, WPA, WPA2, WPA3). Utilizing specialized devices, the analyzer, at that point, endeavors to abuse vulnerabilities in these conventions or destitute setups, such as powerless passwords or the utilization of obsolete encryption.
38. Explain the concept of a honeypot in cybersecurity and its significance to entrance testing.
Ans:
A honeypot in cybersecurity is a decoy system, network, or dataset intentionally made vulnerable to attract attackers and study their methods. Designed to mimic real systems with valuable data, honeypots are closely monitored environments where attackers’ actions can be observed without risking the actual organization. In penetration testing, honeypots help gather tactics, techniques, and procedures (TTPs) used by attackers, enhancing the tester’s ability to simulate realistic attack scenarios.
39. How should testing differ for cloud-based vs. conventional web applications?
Ans:
A unique consideration for the cloud environment is multi-tenancy, dynamic scalability, and shared assets while testing a cloud-based application. In order to customize the infiltration testing technique, first survey the cloud benefit show (IaaS, PaaS, and SaaS), focusing on points of view such as the cloud provider’s API security, arrangement management, and information capacity isolation. Cloud applications need to be tested for misconfigurations in cloud-specific administrations, unlike traditional web apps where the framework is inactive.
40. What part does social building play in infiltration testing?
Ans:
- Social building plays a noteworthy part in entrance testing as it reenacts the human component of cyber dangers, highlighting how human behavior can lead to security breaches.
- This approach includes strategies like phishing, pretexting, teasing, and tailgating to control people into unveiling private data, allowing unauthorized access, or performing activities that compromise security.
- In entrance testing, social building tests the adequacy of an organization’s security mindfulness preparation and the strength of its workers to such strategies.
- By distinguishing vulnerabilities in human behavior, organizations can tailor their preparation programs to better protect against these non-technical dangers, making social building a vital portion of comprehensive security assessments.
41. How can compliance with information security laws be guaranteed amid an infiltration test?
Ans:
Ensuring compliance during infiltration tests involves: legal compliance review, obtaining explicit client permission, minimizing data exposure, securely handling sensitive information, encrypting data in transit and at rest, securely reporting findings related to personal data, making recommendations for improving data security measures, and securely deleting or returning accessed data post-test in accordance with legal obligations.
42. How is a chance evaluation performed in the context of infiltration testing?
Ans:
- Performing a chance evaluation in the context of infiltration testing includes distinguishing, analyzing, and assessing the dangers related to the vulnerabilities found during the test.
- The preparation begins by distinguishing esteem-based resources inside the organization and mapping potential dangers to these resources.
- Each powerlessness found during the entrance test is then analyzed to determine its possible effect on secrecy, keenness, and accessibility. This includes considering the probability of abuse and the potential harm or misfortune that might result.
- At that point, the dangers are prioritized based on their seriousness, helping the organization successfully designate assets for remediation endeavors.
43. Clarify the significance of the chain of guardianship in the setting of infiltration testing.
Ans:
Maintaining a chain of custody in penetration testing is crucial for ensuring the integrity and non-repudiation of evidence collected, which is essential for legal proceedings. It involves creating a detailed and documented record of the evidence collection, handling, analysis, and access. This meticulous documentation helps to confirm that the evidence has not been tampered with or altered, thereby ensuring its reliability in court.
44. Differentiate between infiltration testing and ruddy teaming.
Ans:
Penetration testing and red teaming are both critical elements of an organization’s security assessment process, yet they serve distinct purposes. Penetration testing is a targeted, objective-driven approach to identify and exploit specific vulnerabilities within defined parameters. Conversely, red teaming employs a broader, adversarial approach to test an organization’s detection and response capabilities across various vectors, including physical, technical, and social aspects, often without the knowledge of the defense teams.
45. Balancing thorough penetration testing with operational constraints in the target environment?
Ans:
- Balancing the need for careful infiltration testing with operational imperatives includes clear communication, exact scoping, and timing considerations. First, work closely with the client to understand their operational prerequisites and establish clear boundaries for the test to avoid disturbing basic administrations.
- This incorporates concurring on testing windows amid low-traffic periods or on disconnected duplicates of generation frameworks when conceivable.
- Utilizing non-disruptive testing methods and prioritizing vulnerabilities permits for proficient distinguishing proof of basic security issues without a critical effect on operational soundness.
46. What is the contrast between white box, dark box, and grey box infiltration testing?
Ans:
- White box entrance testing, moreover known as clear box testing, includes full divulgence of the target system’s environment and framework to the analyzer. This approach permits a comprehensive evaluation since the analyzer has access to source codes, design graphs, and accreditations.
- Dark box testing gives no earlier information on the inside workings of the target framework, recreating an outside attacker’s viewpoint and centering on vulnerabilities that can be misused without inside getting to.
- Grey box testing is a cross-breed approach where constrained information around the framework is shared with the analyzer, striking an adjustment between the profundity of white box testing and the authenticity of dark box testing.
47. How are discoveries from an entrance test archived and reported?
Ans:
Infiltration test reports detail vulnerabilities, their impacts, and recommended fixes. They typically start with an executive summary, which outlines key findings and risks in a manner accessible to non-technical stakeholders. Following this, each vulnerability is described in detail, including the method of discovery, evidence supporting the finding, potential impact, exploitability, and specific mitigation recommendations. The report often concludes with an overall assessment of the organization’s security posture and additional suggestions for improving defenses.
48. How should one approach testing Web of Things (IoT) gadgets for vulnerabilities?
Ans:
Testing IoT devices for vulnerabilities requires a comprehensive approach that addresses various aspects of the device’s ecosystem. Start by mapping the IoT environment to identify potential entry points and understand the interaction between devices. Evaluate physical security to ensure the device is protected from tampering. Test the firmware for vulnerabilities, focusing on code weaknesses and update mechanisms.
49. What is the significance of a Ruddy Group workout in comparison to standard entrance testing?
Ans:
- Red Team exercises are advanced, comprehensive simulations designed to assess an organization’s response to real-world cyberattacks.
- Unlike standard penetration testing, which focuses on specific vulnerabilities, Red Team exercises simulate full-scale attacks on digital and physical defenses.
- This approach evaluates security policies, incident response plans, and employee awareness in ways standard tests do not.
- By mimicking real threat actors’ tactics, techniques, and procedures (TTPs), Red Team exercises offer valuable insights into security performance and areas for improvement.
50. What is XPath Infusion in infiltration testing?
Ans:
XPath Infusion is an assault that targets applications that use XPath inquiries to recover information from XML databases. By infusing noxious XPath code into an investigation, an assailant can control it to bypass confirmation, obtain unauthorized information, or test the structure of the XML database. Infiltration analyzers recreate XPath Infusion assaults to distinguish and illustrate how assailants seem to abuse XPath vulnerabilities, emphasizing the significance of input approval and secure coding practices.
51. Clarify Web Application Filtering with w3af in pen-testing.
Ans:
w3af (Web Application Assault and Review System) is an open-source web application security scanner. Infiltration testing is utilized to distinguish vulnerabilities in web applications, such as SQL infusion, XSS (Cross-Site Scripting), and CSRF (Cross-Site Ask Fraud). w3af computerizes the preparation of identifying security blemishes, permitting analyzers to center on abusing vulnerabilities to survey their effect.
52. Clarify reflected XSS Vulnerability.
Ans:
- Reflected Cross-Site Scripting (XSS) happens when an application regularly gets noxious input from a client through a URL or shape accommodation and reflects that input to the user’s browser without legitimate sanitization.
- This powerlessness permits assailants to execute scripts in the setting of the victim’s session, possibly taking treats, session tokens, or other delicate data.
- Entrance analyzers illustrate this defenselessness by creating malevolent URLs or inputs that uncover how assailants may misuse it.
53. What is Capturing Execution in pen-testing?
Ans:
Hijacking execution alludes to methods utilized by aggressors and infiltration analyzers to divert the stream of Execution inside an application or framework regularly to execute subjective or pernicious code. This can include misusing vulnerabilities such as buffer floods, unreliable work calls, or misconfigurations. Entrance analyzers utilize Execution capturing to illustrate the potential effect of such vulnerabilities, highlighting the need for secure coding hones and legitimate security controls.
54. Write a few focuses on SEH Overwrite Exploits.
Ans:
- SEH (Organized Special case Taking care of) Overwrite Misuses target a Windows security instrument that handles exemptions and mistakes.
- By overwriting the SEH chain with pernicious code, an aggressor can take control of the application’s execution stream.
- Entrance analyzers utilize SEH overwrite strategies to recognize buffer flood vulnerabilities that may be misused to execute self-assertive code.
- This emphasizes the significance of bounds checking and memory administration in computer program development.
55. What is POP POP RET in entrance testing?
Ans:
POP POP RET is a technique used to exploit buffer overflow vulnerabilities and bypass certain protections like Structured Exception Handling (SEH). This method involves crafting a specific sequence of instructions, typically two POP instructions followed by a RET instruction, to manipulate the execution flow of a program. By carefully placing this sequence in the exploit, an attacker can redirect the program’s execution to code controlled by the attacker.
56. What is implied by DNS Observation in infiltration testing?
Ans:
DNS Surveillance includes gathering data from almost a target’s DNS (Space Title Framework) framework, such as space names, subdomains, and related IP addresses. Entrance analyzers utilize DNS observation devices and methods to outline the target’s organizing framework, recognize potential focuses of passage, and get the organizational structure. This data is pivotal for arranging and encouraging entrance testing exercises and for identifying vulnerabilities that might be exploited.
57. What are porting open exploits?
Ans:
Porting open abuses includes adjusting existing abuse codes to work against diverse forms of computer programs or in distinctive situations that are different from those initially expected. Infiltration analyzers frequently harbor open abuses to illustrate how known vulnerabilities can be misused in client situations, emphasizing the significance of convenient fixing and upgrades. This preparation requires understanding basic defenselessness, the target environment, and the capabilities of the misuse code.
58. What is XAMPP?
Ans:
- XAMPP is a free and open-source cross-platform web server arrangement stack bundle created by Apache Companions. It comprises the Apache HTTP Server, MariaDB database, and translators for PHP and Perl scripts.
- XAMPP is utilized to recreate a web server to test websites locally on a developer’s machine.
- In entrance testing, XAMPP can be utilized to secure a nearby environment and test and abuse web application vulnerabilities without affecting live environments.
59. What is SSL Stripping in entrance testing?
Ans:
SSL Stripping is an assault method where an assailant mediation and adjusts the communication between a client and a site to minimize the association from secure HTTPS to decoded HTTP. This permits the assailant to see and change the information transmitted, possibly taking touchy data. Infiltration analyzers recreate SSL Stripping assaults to illustrate the significance of executing security measures like HSTS (HTTP Strict Transport Security) and guaranteeing secure connections.
60. What is token Impersonation?
Ans:
Token Pantomime is a strategy utilized in entrance testing and hacking to misuse benefits related to verified client sessions. By taking or manufacturing confirmation tokens, an assailant or analyzer can mimic a genuine client, picking up unauthorized get-to frameworks and information. This strategy highlights the significance of secure session administration, vigorous confirmation components, and normal observing for odd exercises to avoid unauthorized get-tos and information breaches.
61. What is Pass the Hash in entrance testing?
Ans:
Pass the Hash (PtH) is used in penetration testing to access a site or service by leveraging a hashed version of a user’s password. This approach abuses authentication systems that use hashes for credential verification. Attackers grab the hash and use it to authenticate as the legitimate user, bypassing the requirement to guess the password, thereby providing illegal access to network resources.
62. What are Socks4a and Intermediary Chains?
Ans:
Socks4a and Intermediary Chains allude to strategies utilized to anonymize the source of web activity, and bypass organized confinements. Socks4a is a convention for intermediary servers, empowering clients to course their organized bundles through an intermediary server, which covers up their IP address. Intermediary Chains include:
- Connecting a few intermediary servers.
- Permitting arrange activity to jump from one intermediary to another.
- Making it more troublesome to follow back to the unique source.
63. What is Information Execution Anticipation in infiltration testing?
Ans:
- Data Execution Avoidance (DEP) is a security include that anticipates the Execution of code from non-executable memory districts, pointing to security against buffer flood assaults. In entrance testing, DEP is assessed to decide how it impacts the misuse of vulnerabilities.
- Analyzers may endeavor to bypass DEP through methods such as Return-Oriented Programming (ROP) to effectively misuse a framework, subsequently illustrating the requirement for extra layers of security past DEP.
64. What is USSD Inaccessible Control?
Ans:
USSD (Unstructured Supplementary Benefit Information) Inaccessible Control alludes to misusing USSD codes, which are regularly utilized for versatile phone communication with benefit suppliers, to execute unauthorized commands on a portable gadget. This can incorporate activities like wiping the gadget or checking the IMEI number. In infiltration testing, this defenselessness might be investigated to survey the security of versatile gadgets and systems against USSD-based attacks.
65. What is EternalBlue SMB Inaccessible Windows Part Pool Corruption?
Ans:
EternalBlue is an abuse created by the NSA and spilled by the Shadow Brokers that targets the Microsoft SMB (Server Message Piece) convention. It misuses a defenselessness in Windows’ SMBv1 usage, causing further Windows bit pool debasement. This abuse was outstandingly utilized in the WannaCry ransomware assault. In infiltration testing, EternalBlue can be used to illustrate the potential effect of not fixing known vulnerabilities and the significance of crippling obsolete conventions like SMBv1.
66. Clarify Undercover assaults with Meterpreter?
Ans:
Incognito is a module inside the Meterpreter payload that permits the pantomime of client login tokens on Windows frameworks. This method is utilized in infiltration testing to heighten benefits and reach limited areas of the organization by “taking” the personalities of logged-on clients or directors without requiring their passwords. In secret assaults, abuse Windows’ token dealing to bypass conventional verification mechanisms.
67. What is Broken Get to Control Vulnerability?
Ans:
- Broken Get to Control alludes to security shortcomings where a client can bypass authorization to get to records, information, or functionalities without legitimate authorizations.
- In entrance testing, distinguishing broken get-to-control includes endeavoring to misuse these vulnerabilities to get to unauthorized data or perform unauthorized activities, highlighting the requirement for vigorous confirmation and authorization checks in applications.
68. Clarify Cryptographic Disappointments in Infiltration Testing.
Ans:
Cryptographic Disappointments, already known as “Delicate Information Presentation,” happen when applications fail to ensure touchy information through legitimate encryption strategies both at rest and in travel. In infiltration testing, this includes distinguishing and abusing shortcomings in encryption usage, such as utilizing frail calculations, default keys, or inappropriate key administration, to access touchy data.
69. What is Unreliable Plan Vulnerability?
Ans:
Insecure Plan is a category of powerlessness that emerges from imperfections in the computer program plan, which may lead to security issues. This incorporates lost security controls or highlights that are not strong enough to anticipate assaults. In entrance testing, distinguishing uncertain plans includes analyzing the engineering and plan choices of a framework to discover vulnerabilities that may be abused due to the nonappearance of satisfactory security measures.
70. What is a Security Misconfiguration vulnerability?
Ans:
- Security Misconfiguration happens when security settings are characterized, executed, or maintained improperly, leading to pointless dangers.
- This can incorporate default accreditations, pointless administrations, open ports, or wordy mistake messages.
- In infiltration testing, misusing security misconfigurations includes recognizing and leveraging these oversights to detect unauthorized access or data, emphasizing the significance of customary security audits and setup audits.
71. What is an Obsolete Component’s vulnerability?
Ans:
The outdated Component’s Helplessness alludes to the security shortcomings displayed in the program due to the utilization of obsolete or unsupported libraries and components. These components may contain known vulnerabilities that have been settled in afterward forms. Aggressors can misuse these vulnerabilities to carry out different assaults, counting information breaches, dissent of benefit, or picking up unauthorized get to.
72. What is Recognizable Proof and Verification of Disappointments vulnerability?
Ans:
Identification and Confirmation Disappointments Defenselessness happens when frameworks come up short of legitimately executing confirmation and distinguishing proof components, permitting assailants to compromise passwords, keys, or session tokens. This powerlessness can lead to unauthorized get to and possibly full framework compromise. Remediation includes:
- Implementing solid verification and distinguishing proof controls.
- Normal security reviews.
- Teaching clients about secure practices.
73. What is Program and Information Astuteness Disappointments vulnerability?
Ans:
Software and Information Judgment Disappointments Powerlessness emerges when an application comes up short of ensuring the astuteness of computer programs and information. This can lead to unauthorized changes, incorporation of evil code, or information debasement. It regularly comes about from a lack of approval for information astuteness, the need for code marking, or deficient utilization of cryptographic hashes.
74. What is Server-Side Ask Imitation vulnerability?
Ans:
- Server-Side Ask Fraud (SSRF) Powerlessness happens when an assailant can impact a server-side application to make demands in an unintended area, frequently bypassing get-to controls and collaborating with inner administrations.
- SSRF can lead to delicate information presentation, inside framework mapping, or encourage assaults against the inner arrange.
- Relief procedures incorporate approving and sanitizing all user-supplied input, actualizing strict get-to controls, and fragmenting inside systems to constrain the effect of such attacks.
75. What is Outline Infusion vulnerability?
Ans:
Frame Infusion Powerlessness permits an attacker to infuse pernicious HTML or JavaScript code into a webpage in the form of an outline. This can lead to phishing assaults, session capturing, and other forms of misuse by deceiving clients or capturing touchy data. Relief includes:
- Executing Substance Security Approach (CSP) headers.
- Guaranteeing that user-supplied input is legitimately approved and encoded.
- Utilizing frame-busting scripts to avoid unauthorized framing.
76. What is URL Redirection vulnerability?
Ans:
URL Redirection Powerlessness happens when an application diverts clients to a URL based on unvalidated user-supplied input. Aggressors can abuse this to redirect clients to phishing or malevolent websites, possibly driving to credential robbery or malware contamination. Anticipation incorporates approving all redirection targets against an allowlist, guaranteeing that diverts are performed server-side, and dodging the utilization of client input in divert decisions.
77. What is entrance testing Dropbox?
Ans:
Penetration Testing Dropbox is a physical or virtual gadget conveyed in a target arrangement to give the infiltration analyzer further access. It acts as a dependable balance, permitting analyzers to safely interface and perform other testing exercises without being onsite. These gadgets are prepared with a range of apparatuses and designed for secure access. It’s vital for entrance analyzers to have unequivocal authorization and to clearly characterize the scope of utilization for a Dropbox to maintain a strategic distance from lawful and moral issues.
78. What is Outline Infusion vulnerability?
Ans:
Frame Infusion Powerlessness (Rehashed) includes malevolent substance being infused into a webpage through an outline. This assault can betray clients into collaboration with the outline as if it were a portion of the authentic location, compromising client security. Mitigations incorporate utilizing CSP headers, approving client input, and utilizing frame-busting procedures to anticipate unauthorized substance embedding.
79. What is URL Redirection vulnerability?
Ans:
- This helplessness, moreover known as an open divert, happens when a web application or server is controlled to redirect clients to an outside, untrusted URL without legitimate approval.
- Assailants abuse this imperfection to divert casualties to phishing destinations or malware-laden pages, frequently by inserting the pernicious URL in emails or other messages, showing up as if it’s from a trusted source.
- To moderate this hazard, engineers ought to actualize strict approval checks on all user-submitted URLs, guaranteeing diverts as they are allowed, trusted goals.
80. What is infiltration testing Dropbox?
Ans:
- An infiltration testing Dropbox is a physical or virtual gadget sent inside a target-arranged environment to encourage entrance testing exercises. It acts as a decent footing for the analyzer, prepared with the different instruments and scripts required for the evaluation.
- Dropbox is regularly small and unnoticeable and effortlessly integrates into the arrangement without raising doubt, permitting analysts to conduct security appraisals remotely.
- Its essential purpose is to reenact an attacker’s nearness inside the arrangement, testing inside guards and the viability of interruption discovery frameworks.
81. Can Infiltration Testing Be Automated?
Ans:
Yes, penetration testing can be automated using specialized tools to detect vulnerabilities in systems, networks, and applications. While automated tools excel at identifying common issues like misconfigurations and outdated software, some complex vulnerabilities require human intuition. Thus, a combination of automated tools and manual testing ensures comprehensive penetration testing.
82. What are the commonly focused on ports amid entrance testing?
Ans:
Commonly focused on ports amid entrance testing incorporate TCP ports 80 (HTTP) and 443 (HTTPS) for web administrations, 22 (SSH) for secure shell get to, 21 (FTP) for record exchanges, 25 (SMTP) for mail, 23 (Telnet) for decoded farther communications, 3389 (RDP) for Windows inaccessible desktop administrations, and 445 (SMB) for Windows arrange record sharing. These ports are habitually focused since they are frequently open for genuine administrations and can be portals to pick up unauthorized access if they are not legitimately secured.
83. What kind of entrance testing can be done with the Diffie Hellman exchange?
Ans:
- Penetration testing with the Diffie-Hellman trade can center on cryptographic convention execution vulnerabilities.
- Analyzers might assess the quality of the keys created, check for powerless or hard-coded prime numbers, and evaluate the defenselessness to man-in-the-middle assaults during the key trade stage.
- The objective is to guarantee that the Execution of the Diffie-Hellman key trade-in applications provides secure and private communication channels safe from spying and interception.
84. What is Salute Mary’s work (Armitage) in infiltration Testing?
Ans:
The Salute Mary work in Armitage, a graphical cyber assault administration device for Metasploit, is a one-click assault strategy that computerizes the preparation of examining and abusing known vulnerabilities in target frameworks. It endeavors to recognize and utilize each pertinent misuse against the target, pointing to a speedy and fruitful compromise. Whereas compelling in a few scenarios, it needs the artfulness and watchfulness of focusing on assaults, possibly driving to recognized interruptions and superfluous arranged traffic.
85. What are the capacities of a full-fledged Windows Rootkit?
Ans:
A full-fledged Windows rootkit ordinarily points to accomplish stealth, tirelessness, and favored get-to. Its capacities may incorporate stowing away pernicious forms, records, or registry keys; capturing attempts and altering framework calls; keylogging; crippling security computer programs; building up backdoors for farther get to; and controlling framework logs to conceal its nearness.
86. What are the capacities of the Java applet popup in infiltration testing?
Ans:
- In entrance testing, a Java applet popup can be utilized to misdirect the client into giving consent or executing noxious code.
- This procedure might abuse Java vulnerabilities or essentially use the belief set in Java to perform activities like drive-by downloads, capturing touchy data, or setting up a decent footing on the user’s framework.
- Successful utilization of a Java applet in infiltration testing illustrates the requirement for exacting input approval, secure coding hones, and client mindfulness training.
87. Differentiate between powerlessness and an exploit.
Ans:
- Defenselessness is a shortcoming or imperfection in a framework, application, or convention that can be utilized to compromise security. It might be due to a destitute Plan, coding mistakes, or misconfigurations.
- On the other hand, a vulnerability is a particular piece of code, strategy, or strategy utilized by aggressors to take advantage of helplessness, gain unauthorized access, or cause harm.
- Whereas vulnerabilities are potential security issues, misuses are the means by which these shortcomings are effectively abused.
88. What is a risk modeling system?
Ans:
A risk modeling framework is an organized approach utilized to distinguish, evaluate, and prioritize potential dangers to a framework. It includes understanding the system’s engineering, recognizing security goals, identifying possible risks, and deciding mitigations. Danger modeling makes a difference in proactively tending to security vulnerabilities and is a basic portion of the secure advancement lifecycle.
89. Clarify the benefits and disadvantages of Linux OS and Microsoft Windows for web application Testing.
Ans:
Linux OS offers a wide range of open-source security devices and a customizable environment. It is regularly considered more secure and steady for web application testing. Its command-line interface is exceedingly proficient for scripting and robotization. In any case, it might have a more extreme learning bend for those new to Unix-based frameworks. Microsoft Windows, with its broad client base, offers a recognizable environment for numerous users and compatibility with a wide range of testing apparatuses.
90. What are the Strategies for recognizing and guarding against Rootkits?
Ans:
- Detecting and guarding against rootkits includes utilizing specialized apparatuses that filter for irregularities that rootkits might deliver, such as contrasts in framework calls comes about or errors in crude disk information versus API-reported data. Keenness checking of framework records and memory, behavioral examination, and heuristic discovery are too compelling.
- Guarding against rootkits incorporates keeping frameworks and security programs up to date, utilizing strict access controls, and minimizing the attack surface by impairing unnecessary administrations. Customary framework checking and the utilization of trusted equipment are also pivotal defense strategies.






