
Bug bounty initiatives provide a platform for talented individuals, referred to as bug bounty hunters, to detect and disclose security weaknesses within software and systems. Typically facilitated by organizations aiming to bolster their cybersecurity defenses, these programs enlist hunters to actively seek out vulnerabilities. Upon discovery, hunters report their findings to the program host, potentially receiving rewards or acknowledgment for their efforts.
1. What are the advantages of bug bounty programs above standard testing procedures?
Ans:
One of the major advantages of a bug bounty program is its potential to significantly lower the costs and time associated with penetration testing. Organizations can access a large global pool of highly qualified security researchers by crowdsourcing vulnerability discovery. These researchers are motivated by incentives to find and report as many security flaws as possible. This approach not only accelerates the identification of vulnerabilities but also often uncovers issues that traditional testing methods might miss.
2. What is control over preventing data loss?
Ans:
Data Loss Prevention (DLP) is a security measure designed to identify and prevent the improper or hazardous sharing, transferring, or use of sensitive data. It helps organizations monitor and protect confidential information across various environments, including endpoints, cloud storage, and on-premises systems. By implementing DLP solutions, companies can detect potential data breaches, enforce data handling policies, and ensure compliance with regulatory requirements.
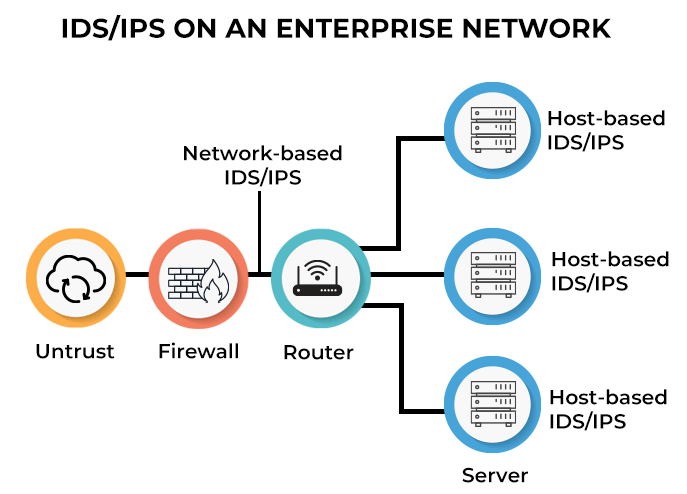
3. What distinguishes an IDS, IPS, firewall, and proxy from one another?
Ans:
An Intrusion Detection System (IDS) monitors real-time network traffic to identify suspicious patterns or potential attacks, generating alerts when such activity is detected. In contrast, a firewall filters incoming and outgoing traffic based on IP addresses and port numbers, blocking or allowing data based on pre-defined rules. An Intrusion Prevention System (IPS) also inspects real-time traffic but goes a step further by actively blocking detected attacks.
4. Define a Bug Bounty Hunter.
Ans:
- A Bug Bounty Hunter’s goal is to assist the system’s developers in resolving security flaws before they become public knowledge by finding and reporting them in system applications.
- To address the most urgent issues, penetration testers, and this knowledgeable team often collaborate. Businesses frequently implement bug bounty programs to safeguard their applications, domains, and clients’ private data. They offer “bounties” to anyone who can identify and patch a security hole.
5. What Makes a Bug Bounty Hunter Worth Hiring?
Ans:
Proactively addressing security vulnerabilities before they become public is crucial for mitigating cyber threats and protecting sensitive information. Engaging in bug bounty programs provides valuable opportunities for security researchers to identify and report vulnerabilities in software and systems. These initiatives not only offer financial incentives but also contribute significantly to strengthening cybersecurity defenses.
6. Why are bounty hunters for bugs so well-liked?
Ans:
- The gig economy includes things like bug bounty hunting. Either full-time or part-time employment is possible for this work.
- Finding and fixing bugs is a skill that anyone with a hacker mentality and an innate curiosity about computers and computer systems can acquire.
- However, from the standpoint of cybersecurity, they have to continuously monitor new threats and test protocols to effectively exploit bugs.
7. What piques interest in bug bounty programs?
Ans:
- The initial benefit, the ability to test and responsibly apply recently learned security knowledge without worrying about website owners taking revenge, was a key benefit of bug bounty programs.
- Some programs were further improved by adding monetary prizes.
- Put differently, one can receive compensation for researching a subject they are passionate about.
8. Who Signs Up for Programs to Bounty?
Ans:
Many large firms, such as Apple, Android, AOL, Digital Ocean, and Goldman Sachs, have incorporated bug bounty programs into their security strategies. These programs incentivize security researchers to find and report vulnerabilities, enhancing overall cybersecurity. The two most well-known websites that make these bug bounties possible are HackerOne and Bugcrowd. Their programs offer a structured environment for submitting vulnerabilities and receiving rewards.
9. What categories of hackers exist?
Ans:
- Crackers, often known as Black Hat Hackers, illegally breach data privacy or disrupt operations by breaking into networks to obtain unauthorized access.
- Ethical hackers, sometimes known as “white hat” hackers, gain access to systems and networks to lawfully and previously evaluate potential hazards or vulnerabilities.
- Grey Box Hackers: They evaluate a network’s or computer system’s security flaws without the owner’s consent and then alert them to it.
10. How do symmetric and asymmetric encryption differ from one another?
Ans:
| Aspect | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Single shared key for encryption and decryption | Pair of keys: public for encryption, private for decryption |
| Security and Complexity | Generally faster but requires secure key distribution | Offers greater security but is slower and computationally intensive |
| Key Length | Typically requires shorter key lengths (e.g., 128 or 256 bits) | Typically requires longer key lengths (e.g., 2048 or 4096 bits) |
| Examples of Algorithms | AES (Advanced Encryption Standard), DES (Data Encryption Standard) | RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography) |
11. How may ARP poisoning be prevented?
Ans:
- One kind of network assault that can be stopped by using these methods is ARP poisoning.
- Using packet filtering, packets with conflicting source address data can be filtered out and blocked.
- Avoiding trust relationships: Companies should create a process that relies as little as possible on relationships of trust.
- Make use of ARP spoofing software: Certain applications evaluate and authenticate data prior to transmission and prohibit any information that is spoofing.
12. What kind of hacker is ethical?
Ans:
A cybersecurity professional who looks for and fixes vulnerabilities in systems with the owner’s consent is known as an ethical hacker, or white-hat hacker. Their objective is to improve security by locating and fixing flaws before malevolent hackers may take advantage of them. Ethical hackers protect privacy, stay within authorized bounds, and adhere to legal and ethical standards. They collaborate with organizations to enhance their security measures and protect sensitive data. Their work plays a crucial role in creating a safer digital landscape.
13. Why is Python used in hacking contexts?
Ans:
Python is a popular scripting language among hackers due to its extensive use in various applications. Its extensive ecosystem of pre-assembled libraries, which offer a variety of functionality, is its greatest asset. These libraries enable efficient coding and rapid development of tools for tasks like network scanning, data manipulation, and automation. Python’s ease of use and readability further contribute to its appeal, allowing hackers to quickly write and test their code.
14. What Does Defacement and Pharming Mean?
Ans:
- Pharming: In this tactic, the attacker gains access to the user’s computer or the DNS (Domain Name System) servers with the intention of redirecting traffic to a malicious website.
- Defacement: Using this tactic, the assailant substitutes the company’s website with a different page. It includes the hacker’s name, pictures, and maybe even some text and background music.
15. Describe network protocols and explain their needs
Ans:
- A network protocol is a set of guidelines that specify how data is transmitted amongst devices connected to the same network.
- In essence, it permits communication between the linked devices in spite of variations in their internal architecture, procedures, or structures. The use of network protocols is essential to digital communications.
16. Define Network Enumeration.
Ans:
Network enumeration is the process of locating hosts and devices on a network by compiling comprehensive data about them. This process often utilizes transparent disclosure protocols, such as SNMP (Simple Network Management Protocol) and ICMP (Internet Control Message Protocol), to extract data. Additionally, network enumerators examine various ports on remote hosts to detect known services and understand the functionality of those hosts.
17. What is sniffing a network?
Ans:
Using sniffer tools to enable real-time monitoring and analysis of data streaming over PC systems is known as system sniffing. Sniffers can be used for a variety of tasks, including controlling systems and stealing data. Sniffing the network is used for both moral and immoral reasons. System administrators use these as tools for system analysis and monitoring, such as traffic bottleneck detection and avoidance. These gadgets are able to be utilized to plan and carry out cybercrime for dubious objectives, such as email, character appropriation, stealing sensitive data, etc.
18. Describe the CIA Triad.
Ans:
One well-liked information security paradigm is the CIA trio. It adheres to the three guidelines listed below:
- Confidentiality: Preserving the details unseen.
- Integrity: Preserving the accuracy of the data.
- Availability: Permitted parties always have access to information.
19. How do VA and PT differ from one another?
Ans:
- Evaluation of VulnerabilitiesTesting for penetrations.
- The process of vulnerability assessment is used to identify weaknesses in a network or application.
- The process involves identifying weaknesses that can be exploited, much like an actual attacker would.
- It is comparable to surface travel. It is searching for gold.
20. Describe a firewall.
Ans:
A firewall is a security device that controls network traffic based on predefined rules, allowing or blocking data transfers between trusted and untrusted networks. Positioned at network boundaries, it acts as a barrier to unauthorized access and potential threats. Examples of its functionality include encrypting responses to protect data, restricting email communications to internal networks to prevent leaks, and blocking the printing of sensitive information to ensure privacy.
21. What is leaking of data? How to identify and stop it?
Ans:
- A data leak is simply information about the organization’s data that is uninvited to leave.
- There are many different ways that data can leak, including emails, prints, lost laptops, illicit data transfers to public portals, portable drives, photos, and more.
- These days, data security is crucial. Thus, several measures can be taken to ensure that information isn’t compromised. These measures include restricting uploads on websites and implementing internal audits.
22. Distinguish between spoofing and phishing.
Ans:
At first glance, spoofing and phishing appear quite different. Spoofing involves misleading someone by mimicking trusted sources to infiltrate a computer or network, often deploying malware. In contrast, phishing tricks individuals into revealing sensitive information, like financial details, through deceptive communications. Essentially, spoofing is a method for delivering malicious content, while phishing is aimed at recovering confidential data from victims.
23. What is the connection between white box testing and dynamic analysis?
Ans:
In white box testing, dynamic analysis is a technique where the code is run, and its behavior is observed. It entails examining the software’s behavior during runtime to find flaws, including memory leaks, performance snags, and security holes. Dynamic analysis sheds light on how the program operates under various circumstances and with various inputs.
24. Which tools are frequently employed in white box testing for dynamic analysis?
Ans:
- Valgrind – Apache JMeter – Tools for fuzz testing (such as AFL and Peach) – Tools for code coverage (such as Istanbul and JaCoCo)
- Tools for profiling, such as VisualVM and YourKit
- These tools aid in the analysis of software’s runtime behavior, the detection of performance problems, and the confirmation that the code functions as intended under a range of circumstances.
25. What is the purpose of control flow testing, and how significant is it?
Ans:
One type of white box testing is control flow testing, which involves running various control flow paths through the software. It entails creating test cases that can perform any conceivable control flow statements, including branches, conditionals, and loops. Control flow testing aids in making sure that every component of the code is run and tested extensively.
26. What’s data flow testing, and why does it need it?
Ans:
Tracing the flow of data through the software is the main goal of data flow testing, a white box testing technique. It entails creating test cases to alter and watch how information is transferred and handled by the software. Potential data-related problems, such as uninitialized variables, variable abuse, and data corruption, can be found with the use of data flow testing.
27. Describe network security and Security testing:?
Ans:
- With the aid of software and hardware technologies, network security is fundamentally a set of guidelines and configurations designed to safeguard data and computer networks’ integrity, confidentiality, and accessibility.
- Software testing that focuses on finding holes, flaws, and possible dangers in an application’s security features is known as security testing.
- It entails a thorough evaluation of the program’s defense against theft, damage, and unwanted access to data and resources.
28. What are the Different kinds of network security
Ans:
- Network access control: The most detailed network access control regulations are in place for both users and devices to thwart attackers and infiltrations. For instance, it is possible to assign and limit access authorization to confidential data and the network as needed.
- Antivirus and antimalware software: These tools are used to continuously check for and defend against viruses, malware, and other harmful software.
29. What is the connection between white box testing and path coverage?
Ans:
Path coverage is a metric used in white box testing that quantifies the proportion of distinct paths within the code that have been run through the test scenarios. It is related to white box testing because it reveals the extent to which various execution pathways have been tested. Path coverage guarantees thorough testing of all potential program behaviors and aids in the identification of complex control flow problems.
30. Explain the impact of emerging technologies on privacy and security.
Ans:
Artificial intelligence, biometrics, and surveillance systems are examples of new technologies that significantly impact society’s security and privacy. To ease these concerns, laws that specify how new technologies should be used, give clear guidelines for collecting and storing data and ensure transparency and consent when utilizing them should be passed. It is also important to implement robust cyber security protocols to guard against any data breaches and misuses.
31. What steps address racial justice and institutionalized racism?
Ans:
- Laws and initiatives that address the root causes of systemic racism—discriminatory practices in employment, housing, education, and the criminal justice system, for instance—will aid in the fight against it.
- This might involve enacting anti-discrimination legislation, providing financing for racial justice initiatives, encouraging diversity and inclusion in institutions, and investing in underserved areas are examples of reforms.
- Furthermore, fostering dialogue, education, and information about racism and its repercussions is essential to advancing racial justice and establishing understanding.
32. What policies and initiatives might be implemented to encourage sustainable urban development?
Ans:
Prioritizing compact, mixed-use development, enhancing public transportation and infrastructure, safeguarding green areas and natural habitats, promoting energy efficiency and renewable energy sources, offering affordable housing, and ensuring equitable access to services are all important. These initiatives and policies will aid in promoting sustainable urban development. Participating in communities and interested parties in the planning process is also necessary to ensure that development fulfills the aspirations and needs of every resident.
33. Is there an ability to fix flaws quickly?
Ans:
The speed of fixing flaws depends on the issue’s complexity, available resources, and team expertise. Effective identification and response tools, such as automated monitoring and agile processes, can accelerate resolution. Regular updates and patches are crucial for efficient flaw management. Clear team communication also helps speed up fixes. A proactive approach is essential for minimizing downtime and mitigating risks.
34. What policies and initiatives could be implemented to encourage sustainable urban development?
Ans:
- Prioritizing compact, mixed-use development, enhancing public transit and infrastructure, safeguarding green areas and natural ecosystems, and utilizing renewable energy sources are all important.
- In addition to providing fair access to services and affordable housing, energy sources should be promoted.
- These initiatives and policies will aid in the promotion of sustainable urban development.
- Ensuring that development meets the needs and aspirations of all residents requires including communities and stakeholders in the planning process.
35. How to ensure access to high-quality, affordable healthcare?
Ans:
To guarantee that everyone has access to inexpensive, high-quality healthcare, measures including expanding Medicaid, regulating drug prices, investing in public health and preventative care, and supporting innovation in healthcare delivery models can all be put into place. It’s also necessary to address socioeconomic determinants of health like poverty, education, and unstable housing.
36. What steps can be taken to promote gender equality and empower women in all sectors of society?
Ans:
Gender equality and women’s empowerment in all domains of society can be advanced by policies and initiatives that address barriers to equality, such as discriminatory laws and practices, differences in work and educational prospects, and gender-based violence. This could mean enacting laws that are considerate of gender issues, providing funding for programs that support girls’ education and economic empowerment, pushing for the inclusion of women in leadership positions and decision-making groups, and opposing harmful gender stereotypes and practices.
37. What does cyclomatic complexity mean, and how is it measured?
Ans:
- Cyclomatic complexity software statistics determine the level of complexity in a program’s control flow graph.
- Using the software’s source code, it ascertains the benefits of linearly distinct pathways.
- The formula for calculating cyclomatic complexity is M = E—N + 2P, where E denotes the benefits of edges, N is the benefits of nodes, and P is the benefits of connected components.
38. What is the Halstead complexity calculation method?
Ans:
Halstead complexity is a software metric that measures a program’s complexity based on its operators and operands. The complexity is calculated using four key metrics: program difficulty (D), program volume (V), vocabulary size (n), and program length (N). Program difficulty (D) assesses the effort required to understand the program, while program volume (V) quantifies the size of the program. Vocabulary size (n) refers to the number of unique operators and operands, and program length (N) counts the total number of operators and operands.
39. What is the meaning of the maintainability index, and how is it calculated?
Ans:
A software statistic called the Maintainability Index is used to evaluate how readable and maintainable the source code of a program is. It assesses multiple elements, such as the quantity and caliber of comments, the cyclomatic complexity of the code, and the amount of lines of code. These factors are combined into a detailed formula that produces a score reflecting the code’s maintainability. A higher Maintainability Index indicates that the code is easier to read, understand, and modify.
40. What is code coverage correlation, and how is it useful for white box testing?
Ans:
- Code coverage correlation is the degree to which code coverage metrics agree with an application’s overall quality.
- White box testing is important because it establishes how well the tests are exercising the code and whether additional tests are needed to improve coverage in important areas.
- A high correlation indicates that the tests sufficiently cover the code, while a low correlation suggests potential flaws in the testing methodology.
41. What obstacles must be overcome for high levels of code coverage in white box testing?
Ans:
- Code complexity: It can be challenging to cover every case since overly complex codebases may have multiple branches and pathways.
- Insufficient unit testing: It is difficult to achieve high code coverage in the absence of thorough unit tests.
- Legacy code: Due to inadequate documentation and organization, it could be more challenging to understand and test older codebases thoroughly.
- Dependencies: Codes that heavily rely on external dependencies or third-party libraries may take more work to test completely.
42. What is testability, and how is it useful for white box testing?
Ans:
Testability measures how easy it is to test a system or component. Because it allows testers to delve deeply into the software’s core functions and ensure that every code path is adequately verified, testability is essential to white box testing. Software systems that are more testable are easier to manage, debug, and enhance, eventually producing higher-quality output.
43. What characteristics set highly testable code apart?
Ans:
- Modular design: Code that is structured into modular components is easier to test independently.
- Simplified and clear logic: Easy-to-read and understanding code makes testing more efficient.
- Few external dependencies: Code with fewer external dependencies is easier to isolate and test.
- Comprehensive documentation: Well-written documentation helps testers understand the purpose and operation of the code, which streamlines testing efforts.
44. What does code smell mean, and how does it relate to white box testing?
Ans:
A “code smell” refers to any aspect inside the source code that may indicate a potential or more significant problem. In white box testing, code smells are important indicators that guide further investigation and testing. They could draw attention to parts of the code that are poorly written, overly complex, or prone to errors, all of which could detract from the overall quality of the program.
45. What are some common code smells to watch out for when doing white box testing?
Ans:
Some code smells to watch out for during white box testing are as follows:
- Extended processes or responsibilities;
- Excessive complexity or nesting;
- Repetitive code; and
- Inadequate naming standard
46. How do test-driven development (TDD) and white box testing relate to one another?
Ans:
Tests are written for the working code when developing software using the test-driven development (TDD) technique. TDD ensures that all of the codebase’s components have matching tests, which results in outstanding test coverage for white box testing. Developers implement the code to make sure the tests pass after using tests to define the intended behavior of the code.
47. What are the advantages of TDD application in white box testing?
Ans:
- Better readability and code quality: TDD promotes programmers to write code that is more easily modular, testable, and updatable.
- Quicker feedback loop: By giving developers prompt feedback on whether the code is valid, TDD enables developers to spot problems early in the development cycle.
- Greater test coverage: TDD makes sure that every code route is tested and raises the total amount of test coverage because tests are written for the code itself.
48. How do behavior-driven development (BDD) and white box testing relate to one another?
Ans:
Behavior-driven development (BDD), an extension of theory-driven design (TDD), is concerned with how the system behaves from the perspective of its stakeholders. White box testing, a technique used by BDD, comprises developing tests in a language that non-technical stakeholders may understand in addition to technical ones. These tests guide the expected behavior of the system.
49. What benefits does the use of BDD in white box testing offer?
Ans:
- Better collaboration: BDD encourages collaboration between developers, testers, and stakeholders by specifying system behavior using a common vocabulary.
- Clearer requirements: By serving as executable specs that outline the desired behavior of the system, BDD tests eliminate ambiguity and misconceptions.
- Greater test coverage: By focusing on how the system acts from the perspective of the user, BDD tests ensure that all important features are sufficiently assessed.
50. What are some recent advancements and technological improvements in the field of white box testing?
Ans:
- Artificial intelligence (AI) and machine learning (ML): ML and AI techniques are being used to automate test case creation, optimize test coverage, and identify code flaws.
- Continuous Integration and Delivery (CI/CD): CI/CD pipelines automate the software development, testing, and deployment processes, enabling faster feedback loops and more frequent releases.
- Mutation testing: This method involves making small changes, or mutations, to the source code and then observing if the tests catch the changes. It helps assess the effectiveness of test suites.
51. Explain manage and mitigate the impact of emerging technologies on privacy and security.
Ans:
Artificial intelligence, biometrics, and surveillance systems are examples of new technologies that significantly impact society’s security and privacy. To ease these concerns, laws that specify how new technologies should be used, give clear guidelines for collecting and storing data and ensure transparency and consent when utilizing them should be passed. It is also important to implement robust cyber security protocols to guard against any data breaches and misuses.
52. Describe how to achieve racial justice and address the underlying causes of systematic racism.
Ans:
Enacting laws and programs that go at systemic racism’s underlying causes—discriminatory practices in housing, work, education, and the criminal justice system, for example—will help combat it. This could entail changes like putting anti-discrimination laws into effect, encouraging diversity and inclusion in institutions, making investments in underprivileged areas, and allocating funds for racial equity projects.
53. What laws and programs may be put in place to support sustainable urban development?
Ans:
- Compact, mixed-use development should be prioritized, public transportation and infrastructure should be improved, green spaces and natural habitats should be protected, energy efficiency and renewable energy sources should be promoted, and affordable housing and fair access to services should all be provided.
- These policies and initiatives will help to promote sustainable urban development. Involving communities and stakeholders in the planning process is also essential to guarantee that development satisfies the needs and ambitions of all locals.
54. How to guarantee reasonably priced, top-quality medical care?
Ans:
Policies like universal healthcare coverage, Medicaid expansion, drug price regulation, investment in public health and preventive care, and encouragement of innovation in healthcare delivery models can all be implemented to ensure that everyone has access to affordable, high-quality healthcare. Reducing gaps in access and outcomes also requires tackling social determinants of health like poverty, education, and unstable housing.
55. What actions can be taken to empower women in all spheres of society and advance gender equality?
Ans:
- Policies and efforts that address barriers to equality, such as discriminatory laws and practices, unequal access to education and employment opportunities, and gender-based violence, can promote gender equality and women’s empowerment in all spheres of society.
- This could entail enacting laws that are sensitive to gender issues, funding initiatives that empower women economically and for girls’ education, encouraging women to take on leadership roles and be represented in decision-making groups, and combating damaging gender stereotypes and customs.
56. What is meant by the criminal justice system’s fairness and efficiency?
Ans:
The criminal justice system’s ability to handle cases quickly and effectively, distribute resources, and produce desired results like lower crime and recidivism rates is referred to as efficiency. Conversely, fairness refers to the system’s unbiased treatment of every person, regardless of their background, social standing, or other unique personal traits.
57. What are the best strategies for helping displaced people and addressing the worldwide refugee crisis?
Ans:
Nations can use various strategies to help displaced people and handle the worldwide refugee problem. These include humanitarian aid delivery, assistance with relocation initiatives, peaceful conflict resolution, tackling the underlying causes of displacement—poverty and persecution—and international collaboration and burden-sharing among states.
58. What ensures future food security while advancing sustainable agriculture?
Ans:
- Adopting techniques that reduce environmental impact, preserve natural resources, and uphold farming systems’ long-term sustainability are all part of promoting sustainable agriculture.
- This entails encouraging agroecology, funding the study and advancement of sustainable agricultural methods, aiding smallholder farmers, and enacting laws and regulations that reward eco-friendly behavior.
59. What steps can be taken to stop fake news and misinformation from spreading online?
Ans:
- To combat the spread of disinformation and fake news on the Internet, a combination of technology solutions, media literacy education, fact-checking activities, and regulatory measures is needed.
- Platforms may improve their algorithms for content filtering, highlight reliable sources, and give consumers the means to recognize and report misleading information.
- Furthermore, teaching people critical thinking techniques and media literacy might enable them to distinguish between trustworthy and untrustworthy sources.
60. What raises awareness of mental health issues and improves service access?
Ans:
Reducing stigma, stepping up public education and awareness campaigns, increasing access to affordable and culturally sensitive mental health services, integrating mental health into primary healthcare systems, and funding mental health research and infrastructure are all important ways to raise mental health awareness and improve access to mental healthcare services.
61. What fosters harmony and resolves disputes in violent areas?
Ans:
Diplomatic negotiations, peacebuilding projects, conflict resolution training, support for transitional justice mechanisms, and addressing the underlying causes of conflict, such as poverty, inequality, and political grievances, are some of the strategies for promoting peace and resolving conflicts in areas affected by violence and instability. Sustainable peace also requires encouraging inclusive communication and mechanisms of reconciliation among parties involved in conflict.
62. What advances financial literacy and wise decision-making?
Ans:
- Encouraging financial literacy entails giving people the knowledge and tools they need to make wise financial decisions.
- Integration of the school curriculum, community seminars, online resources, and collaborations with financial institutions can all help achieve this.
- Better financial well-being and economic empowerment can result from educating people about debt management, investing, saving, and budgeting.
63. What improves political accountability, transparency, and representation?
Ans:
- In order to improve transparency, accountability, and representation in the political system, a mix of electoral reforms, institutional adjustments, and public engagement programs are needed.
- This entails putting campaign financing laws into effect, fortifying anti-corruption measures, encouraging openness in public decision-making, and raising public engagement through tools like citizen assemblies and direct democracy.
64. What actions may be taken to stop pandemics and other global health emergencies in the future?
Ans:
Stronger public health infrastructure, improved early detection and response capabilities, investments in vaccine development and distribution systems, improved international cooperation and information sharing, and addressing underlying factors like deforestation, urbanization, and global travel patterns that contribute to disease spread are all necessary to prevent and respond to future pandemics and global health crises.
65. What fosters entrepreneurship and innovation for economic growth and job creation?
Ans:
Creating an environment that supports startups and small enterprises through regulations, funding sources, mentorship programs, and innovation centers is essential to promoting innovation and entrepreneurship as a means of generating economic growth and employment opportunities. Collaboration between government, business, and academia can also promote the commercialization of creative ideas, technology transfer, and research and development activities.
66. What expands access to hygiene and clean water in poor nations?
Ans:
- Putting community-based water management systems into place.
- Funding infrastructure improvements.
- Encouraging hygienic practices, education, and awareness.
- Working with local governments and organizations to ensure sustainability and long-term efficacy.
67. How to close the digital divide and ensure universal tech access?
Ans:
- Addressing the digital divide requires a comprehensive approach. This includes building and upgrading infrastructure in underserved regions to ensure reliable internet access.
- Implementing digital literacy programs is crucial for empowering individuals with the skills needed to use technology effectively. Investment in digital solutions and innovation can be stimulated by public-private partnerships. To close the access gap, inexpensive digital gadgets and internet services must be made available.
68. What promotes renewable energy and reduces fossil fuel use?
Ans:
Supportive policies, such as subsidies and incentives for renewable energy projects, investing in the development of renewable technologies, setting high goals for renewable energy, and encouraging public education and awareness of the advantages of renewable energy, can encourage the adoption of renewable energy and lessen reliance on fossil fuels.
69. Which plans of action work best for foreseeing and handling extreme weather and natural disasters?
Ans:
Investing in early warning systems and disaster preparedness measures, bolstering infrastructure resilience, supporting community-based disaster risk reduction initiatives, encouraging international cooperation and coordination, and placing a high priority on sustainable land use and urban planning are all effective ways to prevent and respond to natural disasters and extreme weather events.
70. How to include older persons and address aging population issues?
Ans:
Implementing comprehensive healthcare and social support systems, promoting healthy aging initiatives, encouraging intergenerational solidarity and inclusion, investing in age-friendly infrastructure and services, and encouraging older adults’ active participation and engagement in society are all necessary to address the challenges posed by an aging population.
71. Define and encourage fair and inclusive economic growth that benefits every member of the community.
Ans:
- Advancing inclusive and equitable economic development involves several key strategies. Implementing progressive taxation policies ensures that wealthier individuals contribute more, helping to fund public services and reduce income inequality.
- Investing in education and skill development equips individuals with the tools needed for better job opportunities and economic mobility. Supporting small and medium-sized businesses fosters entrepreneurship and creates diverse economic opportunities.
72. What urgent environmental problems need fixing?
Ans:
- Environmental problems, including deforestation, pollution, climate change, loss of biodiversity, and resource depletion, are urgent concerns facing the planet.
- To address these concerns, strong climate action plans must be implemented, sustainable land and water management practices promoted, clean energy technology adopted, transition to circular economies facilitated, and international cooperation facilitated.
73. How to promote sustainable production and consumption?
Ans:
Promoting sustainable consumption and production patterns involves enacting laws like eco-labeling, boosting recycling and resource efficiency, supporting sustainable procurement practices, raising consumer awareness and education, and offering financial incentives to businesses that integrate sustainable practices throughout their supply chains.
74. What strategies protect ecosystems and biodiversity?
Ans:
Establishing protected area networks, encouraging habitat restoration and conservation initiatives, opposing the illegal wildlife trade, incorporating biodiversity considerations into land use planning and development projects, and involving local communities in conservation efforts are all necessary to protect biodiversity and preserve ecosystems.
75. What ensures ethical use of biotechnology and gene editing?
Ans:
Establishing regulatory frameworks and guidelines, encouraging public discourse and engagement, promoting transparency and accountability in research and development, and considering ethical implications and potential risks before deploying these technologies are all necessary to ensure the responsible and ethical use of emerging technologies like gene editing and biotechnology.
76. What actions may be taken to strengthen communities’ resilience and foster social cohesion?
Ans:
- Governments and organizations can fund community-building initiatives, such as neighborhood associations and cultural events, to strengthen social cohesion and create resilient communities by fostering a sense of connection and belonging.
- Encouraging communication and mutual understanding between various groups, putting inclusive policies into practice, and giving everyone access to opportunities for employment and education
77. What steps may be taken to promote social cohesiveness and increase the resilience of communities?
Ans:
- To improve social cohesion and establish resilient communities by encouraging a sense of connection and belonging, governments and organizations can provide funding for community-building projects like neighborhood associations and cultural events.
- Encouraging intergroup communication and understanding, implementing inclusive policies, and providing equal access to economic and educational opportunities
78. Explain static analysis and how it relates to white box testing.
Ans:
One method of white box testing that examines the code without actually running it is called static analysis. It involves looking for any potential issues, such as grammatical errors, coding convention violations, security flaws, and performance issues, in the source code, bytecode, or binary code. Static analysis helps find defects early so developers can fix them before the code runs.
79. What are the tools that are commonly used in static analysis white box testing?
Ans:
- A few often used tools for static analysis in white box testing include:
- SonarQu – Checkstyle – PMD – FindBugs – Coverity – ESLint – ReSharper
- These tools provide automated source code analysis for identifying various issues.
- FindBugs – Coverity – PMD – SonarQu – Checkstyle
- ReSharper-ESLint
- These instruments offer automated examination of source code to spot different kinds of problems and apply coding guidelines, assisting developers in writing more streamlined and reliable code.
80. What promotes eco-friendly travel with minimal community impact?
Ans:
Governments and tourism stakeholders can implement laws and initiatives that prioritize environmental conservation, support local economies, and encourage responsible tourism practices. This will promote sustainable tourism and reduce its negative effects on the environment and local communities. This entails controlling tourism-related activities, encouraging community-based tourism projects, and instructing travelers on environmentally friendly travel methods.
81. How to foster cohabitation and communication among diverse groups?
Ans:
Fostering tolerance, respect, and understanding between various religious and cultural groups is essential to promoting peaceful coexistence and conversation. Initiatives for interfaith and intercultural communication, the advancement of religious liberty and equality, and the treatment of the underlying causes of religious and cultural resolving disputes and putting laws protecting minority rights into effect.
82. Which strategies work best to stop contemporary slavery and human trafficking?
Ans:
- Effectively combatting human trafficking and modern slavery, a multifaceted strategy comprising prevention, prosecution, protection, and collaboration is needed.
- This includes putting anti-trafficking laws and policies into effect, helping victims, bringing traffickers to justice, and working with foreign partners to address the underlying causes of trafficking and bolster anti-trafficking initiatives.
83. How to make supply chains more ethical and sustainable?
Ans:
Governments, corporations, and civil society organizations must work together to promote moral and environmentally responsible supply chains that uphold human rights and environmental regulations. Implement supply chain transparency measures, carry out moral evaluations and audits, promote just labor standards, care for the environment, and hold businesses responsible for immoral or unsustainable actions.
84. Define the underlying causes of poverty and inequality in developing nations to be addressed.
Ans:
- To effectively tackle the underlying causes of poverty and inequality in developing nations, a comprehensive strategy encompassing economic, social, and political aspects is necessary.
- This strategy includes investments in infrastructure, healthcare, and education.
- Additionally, inclusive economic growth and job creation are encouraged, governance and corruption issues are resolved, and marginalized populations are given the opportunity to participate in decision-making processes.
85. What are some common types of vulnerabilities that bug bounty hunters frequently discover?
Ans:
- Cross-Site Scripting (XSS)
- SQL Injection
- Server-Side Request Forgery (SSRF)
- Remote Code Execution (RCE)
- Authentication Bypass
- Information Disclosure
86. What techniques can be used to detect and exploit insecure deserialization vulnerabilities?
Ans:
Fuzzing input data to trigger unexpected behavior. Crafting malicious payloads to manipulate serialized data. Analyzing error messages or stack traces for clues. Reverse engineering serialized objects to understand their structure. Exploiting known vulnerabilities in deserialization libraries. Monitoring network traffic for suspicious deserialization activity.
87. How does Bug Bounty Methodology Work?
Ans:
Researchers identify vulnerabilities in software or systems. They report findings to the organization hosting the program. The organization validates and addresses reported vulnerabilities. Rewards or recognition are provided to successful bug hunters. Continuous feedback and collaboration improve security posture. Program cycles may repeat for ongoing security improvement.
88. What are the Different Types of Bugs?
Ans:
- Security bugs: vulnerabilities that compromise security
- Functional bugs: issues affecting the intended functionality
- Performance bugs: problems impacting system efficiency
- Usability bugs: issues affecting user experience
- Compatibility bugs: errors arising from system interactions
- Regression bugs: reintroduced issues after software updates
89. Is a Bug Bounty Program suitable for all Businesses?
Ans:
- Depends on the organization’s security maturity and goals
- Can be beneficial for companies with a strong security culture
- Offers a proactive approach to identifying and fixing vulnerabilities
- Requires resources for managing bug reports and rewards
- May not be suitable for organizations with limited resources or security awareness
- Requires clear guidelines and communication to be effective
90. Explain the Network Intrusion Detection System.
Ans:
Monitors network traffic for suspicious activity or patterns. Analyzes packets to detect known attack signatures. May use anomaly detection to identify unusual behavior. Can be deployed at network perimeter or within internal networks. Provides alerts or triggers responses to potential intrusions. Helps organizations detect and respond to cybersecurity threats in real-time.






