
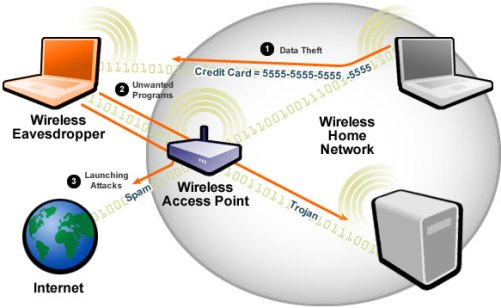
Wireless networks have become an integral part of how we conduct our businesses. They ease many processes and help us get rid of the clutter caused by hundreds of wires yet keeping wireless networks safe poses some challenges
wireless network attack
- With the widespread use of internet, we are able to conduct our business processes online and without being tied down by cables and wires. Wireless networks are one of the relatively new technologies brought to our lives by the internet technologies.
- They are easy to use, facilitate our business processes and mobilize our businesses. On the downside, wireless networks are much more vulnerable to attacks and intruders.
- Wireless attacks have become a very common security issue when it comes to networks. This is because such attacks can really get a lot of information that is being sent across a network and use it to commit some crimes in other networks. Every wireless network is very vulnerable to such kinds of attacks and it is therefore very important that all the necessary security measures are taken so as to prevent the mess that can be caused by such attacks. These attacks are normally carried out to target information that is being shared through the networks
Types of Wireless Attacks
- Wireless Attacks can come at you through different methods. For the most part you need to worry about WiFi. Some methods rely on tricking users, others use brute force, and some look for people who don’t bother to secure their network. Many of these attacks are intertwined with each other in real world use. Here are some of the kinds of attacks you could encounter:
Packet Sniffing:
- When information is sent back and forth over a network, it is sent in what we call packets. Since wireless traffic is sent over the air, it’s very easy to capture. Quite a lot of traffic (FTP, HTTP, SNMP, ect.) is sent in the clear, meaning that there is no encryption and files are in plain text for anyone to read. So using a tool like Wireshark allows you to read data transfers in plain text! This can lead to stolen passwords or leaks of sensitive information quite easily. Encrypted data can be captured as well, but it’s obviously much harder for an attacker to decipher the encrypted data packets.
Rouge Access Point:
- When an unauthorized access point (AP) appears on a network, it is refereed to as a rouge access point. These can pop up from an employee who doesn’t know better, or a person with ill intent. These APs represent a vulnerability to the network because they leave it open to a variety of attacks. These include vulnerability scans for attack preparation, ARP poisoning, packet captures, and Denial of Service attacks.
Password Theft:
- When communicating over wireless networks, think of how often you log into a website. You send passwords out over the network, and if the site doesn’t use SSL or TLS, that password is sitting in plain text for an attacker to read. There are even ways to get around those encryption methods to steal the password. I’ll talk about this with man in the middle attacks.
Man in the Middle Attack:
- It’s possible for hackers to trick communicating devices into sending their transmissions to the attacker’s system. Here they can record the traffic to view later (like in packet sniffing) and even change the contents of files. Various types of malware can be inserted into these packets, e-mail content could be changed, or the traffic could be dropped so that communication is blocked.
Jamming:
- There are a number of ways to jam a wireless network. One method is flooding an AP with deauthentication frames. This effectively overwhelms the network and prevents legitimate transmissions from getting through. This attack is a little unusual because there probably isn’t anything in it for the hacker. One of the few examples of how this could benefit someone is through a business jamming their competitors WiFi signal. This is highly illegal (as are all these attacks), so businesses would tend to shy away from it. If they got caught they would be facing serious charges.
War Driving:
- War driving comes from an old term called war dialing, where people would dial random phone numbers in search of modems. War driving is basically people driving around looking for vulnerable APs to attack. People will even use drones to try and hack APs on higher floors of a building. A company that owns multiple floors around ten stories up might assume nobody is even in range to hack their wireless, but there is no end to the creativity of hackers!
Blueooth Attacks:
- There are a variety of Bluetooth exploits out there. These range from annoying pop up messages, to full control over the a victims Bluetooth enabled device.
WEP/WPA Attacks:
- Attacks on wireless routers can be a huge problem. Older encryption standards are extremely vulnerable, and it’s pretty easy to gain the access code in this case. Once someones on your network, you’ve lost a significant layer of security. APs and routers are hiding your IP address from the broader Internet using Network Address Translation (unless you use IPv6 but that’s a topic for another day). This effectively hides your private IP address from those outside your subnet, and helps prevent outsiders from being able to directly attack you. The keyword there is that it helps prevent the attacks, but doesn’t stop it completely.
Packet Sniffing
- Packet sniffing, a network attack strategy, captures network traffic at the Ethernet frame level. After capture, this data can be analyzed and sensitive information can be retrieved. Such a network attack starts with a tool such as Wireshark. Wireshark allows you to capture and examine data that is flowing across your network. Any data that is not encrypted is readable, and unfortunately, many types of traffic on your network are passed as unencrypted data — even passwords and other sensitive data.
- FTP logon data captured behind the FTP window is shown, showing the user’s password. Having your FTP password known allows the attacker to have your level of access to your FTP site, and any secret data that may be there; on top of that, many users who use the same password for all systems on the network. Now the attacker may have access to several of your corporate systems.
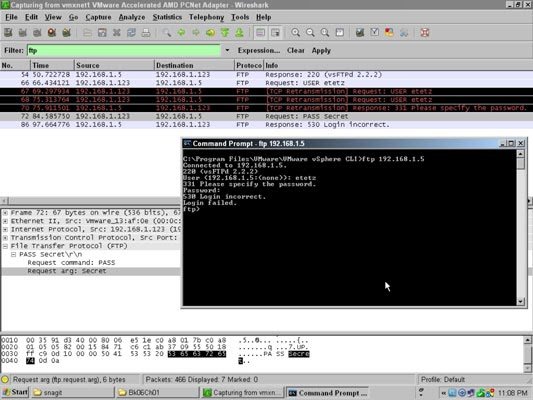
- In addition to capturing cleartext sessions, such as login traffic, an attacker can have an application that captures only specific data from a network, such as network authentication packets, which she then reviews to crack network passwords.
- If you are using switch-based network, you make packet sniffing a little tougher. On a switch-based network, the sniffer will see only data going to and from the sniffer’s own network device or broadcast traffic, unless the attacker uses a monitoring port on a switch. If you have not secured your switches and your switch configuration documentation with a strong password, you are leaving yourself open to a packet-sniffing attack.
- A packet-sniffing attack on a switch-based network happens like this: The attacker connects to a switch and uses information from that switch to locate his own MAC address. The attacker locates his MAC address via show address-database, which lets him know what port the address is seen on.
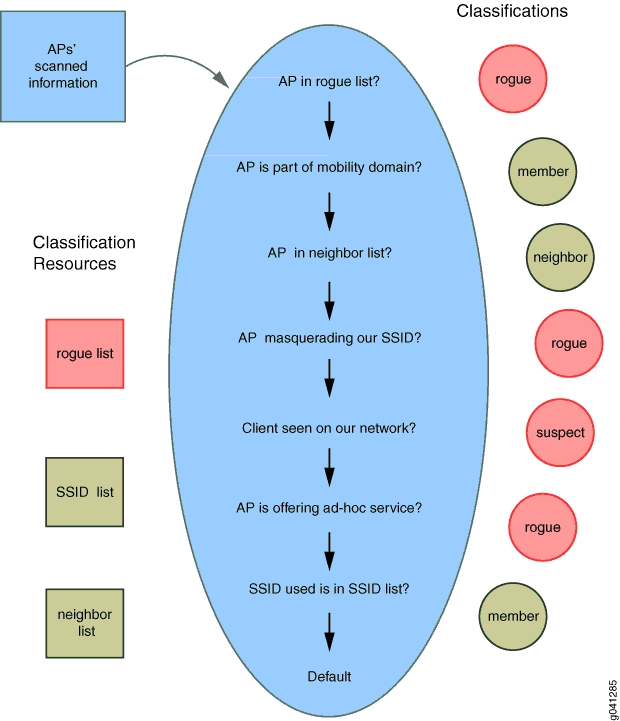
Rogue Access Point
- A rogue access point is a device not sanctioned by an administrator, but is operating on the network anyway. This could be an access point set up by either an employee or by an intruder. The access point could also belong to a nearby company.
- These are some reasons to suspect that an access point is a rogue:
- The SSID of the access point is neither your network SSID nor listed in the permitted SSID list. (See .) The access point may not be broadcasting an SSID at all. Check the SSID of an access point using any of these methods:
- From the MSS CLI,
- From Network Director, .
- From MSS,
- The access point is masquerading one of your SSIDs. Access points masquerading your SSID are rogue by default—you can, however, change that policy. See Understanding an SSID Masquerade.
- The access point is an ad-hoc access point, formed directly between two client devices. See Understanding Ad-Hoc Networks.Ad-hoc access points are rogues by default—you can, however, change that policy—see Configuring Your Ad-Hoc AP Policy.
- Network management features of the access point, such as SNMP, HTTP, and Telnet have been disabled.
- The access point’s MAC address does not appear in ARP tables.
- The access point is operating as a bridge—see Understanding Wireless Bridging .
- The access point is listed in the rogue list, where it has been added by an administrator.
Password Theft
- In this practical scenario, we are going to use Cain and Abel to decode the stored wireless network passwords in Windows. We will also provide useful information that can be used to crack the WEP and WPA keys of wireless networks.
Decoding Wireless network passwords stored in Windows
- Download Cain & Abel from the link provided above.
- Open Cain and Abel
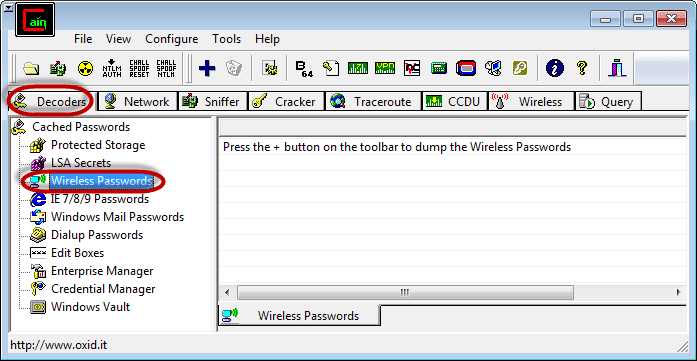
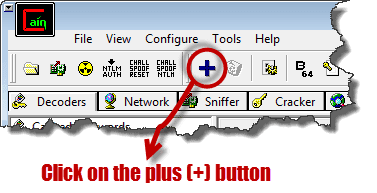
- Ensure that the Decoders tab is selected then click on Wireless Passwords from the navigation menu on the left-hand side
- Click on the button with a plus sign
- Assuming you have connected to a secured wireless network before, you will get results similar to the ones shown below
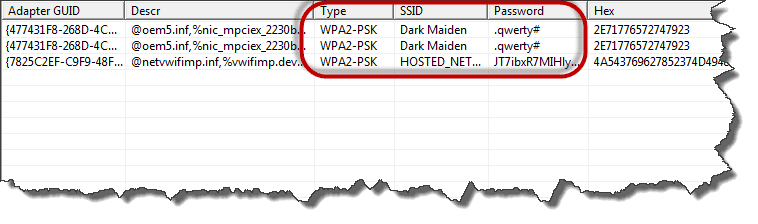
- The decoder will show you the encryption type, SSID and the password that was used.
man in the middle (MITM) attack
- A man in the middle (MITM) attack is one where the attacker (in our example, Mallory) secretly captures and relays communication between two parties who believe they are directly communicating with each other (in our example, Alice and Bob.)
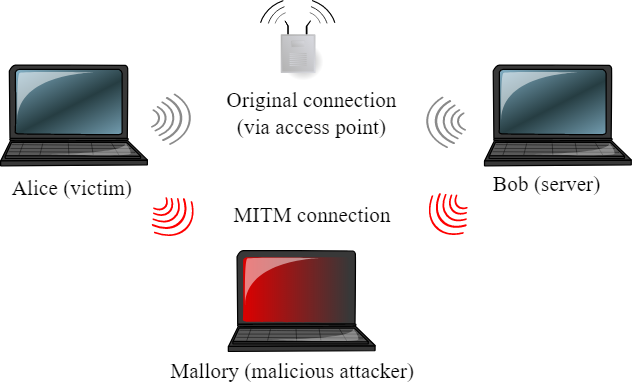
- When data is sent over a WiFi network using WPA-PSK or WPA2-PSK security, it is encrypted at Layer 2 with per-client, per-session keys, and may be decrypted only by its destination. Other clients on the same access point can capture the traffic, but can’t necessarily decrypt it – to decrypt the traffic, a malicious attacker would have had to either capture the initial handshake between client and AP (when the keys were set up), or force the client to disconnect and reconnect, and capture the new handshake between client and AP.
- The attack we’re going to try involves a different approach, using a technique known as ARP spoofing or ARP poisoning. In this experiment, Alice and Bob are connected to a WiFi hotspot, and wish to communicate with one another. Under normal circumstances, they will use ARP requests and replies to find out the physical address (MAC address) to which to direct their traffic.
Jamming
- If an attacker truly wanted to compromise your LAN and wireless security, the most effective approach would be to send random unauthenticated packets to every wireless station in the network. This exploit can be easily achieved by purchasing hardware off the shelf from an electronics retailer and downloading free software from the internet. In some cases, it is simply impossible to defend against jamming as an experienced attacker may have the ability to flood all available network frequencies.
- If the major concern relates to malicious jamming, an intrusion prevention and detection system may be your best option. At the bare minimum, this type of system should be able to detect the presence of an RPA (Rogue Access Point) or any authorized client device in your wireless network. More advanced systems can prevent unauthorized clients from accessing the system, alter configurations to maintain network performance in the presence of an attack, blacklist certain threats and pinpoint the physical location of a rogue device to enable faster containment.
Identify the Presence of the Jammer
- To minimize the impact of an unintentional disruption, it is important the identify its presence. Jamming makes itself known at the physical layer of the network, more commonly known as the MAC (Media Access Control) layer. The increased noise floor results in a faltered noise-to-signal ratio, which will be indicated at the client.
- It may also be measurable from the access point where network management features should able to effectively report noise floor levels that exceed a predetermined threshold. From there the access points must be dynamically reconfigured to transmit channel in reaction to the disruption as identified by changes at the physical layer.
- For example, if the attack occurred on an RF corresponding to channel 1, the access point should switch to channel 6 or 11 in order to avoid the attack. However, selecting a different channel does not always eliminate the issue of interference. An experienced attacker will often use all available channels in the attack. When this happens, your only option may be to physically hunt down the attacker and confront them face to face.
War driving
- Wardriving is commonly perpetrated by individuals driving around in a vehicle while using software and hardware that assists them in locating unsecured networks. The use of a vehicle is not required, and wardrivers can also scan for networks to attack when on foot, on a bicycle, or even by using aircraft. Whatever method of transportation is used, the goal is to secretly penetrate WiFI networks.
Hardware and Software Tools for Wardriving
- In order to perform WiFi driving successfully, you need to use some specialized software or hardware. There are no hard and fast rules regarding what type of devices or software are used by your friendly neighborhood wardrivers. Let’s take a look at some of the tools that are used in wardriving.
Hardware Tools for Wardriving
- There are several hardware components that are required in order to practice war driving.
A mobile device
- You need a mobile computing platform in order to conduct war driving activities. This includes laptops, tablets, smartphones, and other devices such as the Raspberry Pi. These perform overall management of the process and are used to subvert encryption.
Wireless network card and antenna
- These are a critical part of the wardriving setup. The wardriver may use the card and antenna built into their mobile device or may opt for additional hardware in order to increase their scanning power. This component provides the ability to remotely monitor the discovered networks.
GPS system
- The GPS system is used to determine the exact location of the WiFi routers that have been located. Many of the mobile devices used for wardriving have built-in GPS capabilities.
Software Tools for Wardriving
- The primary piece of software which is employed in wardriving is an application that will be used in an attempt to crack the passwords of WEP and WPA encrypted networks. There are many such programs available for use on whichever operating system you prefer. Here are a few of the more popular apps that are used by wardrivers to bypass network security, according to
Protecting Your Network From Wardrivers
- The overriding factor that makes a WiFi network attractive to a wardriving party is the lack of adequate security. A network that is securely protected will be impervious to these types of attack or at least make it so difficult to access that the attackers will find another, more easily compromised target.
- Here are some steps that you can use to protect your network and its data from wardrivers. Failure to secure your network properly leaves you open to having intruders steal your personal information or use your devices for illegal purposes.
According to security experts at McAfee, these are some of the best ways to protect your WiFi network from the risk posed by wardrivers.
- Change your router’s administrative password – The default passwords for many routers are easily available on the web. Operating your router with the default credentials makes it a trivial exercise for a hacker to gain access to your network.
- Enable encryption – You should insist on a router that enables you to set WPA or WPA2 encryption. Use of WEP level encryption should be avoided as it is easily cracked through the use of the tools mentioned above.
- Use a firewall – A firewall monitors attempts to access your system and only allows a connection by approved sources. It can stop unauthorized users from accessing your system.
- Shut down your wireless router when not in use – If you will be gone or will not be using the network for an extended period of time, just shut it down. This will eliminate the possibility of wardrivers discovering and attacking it.
Bluetooth attack
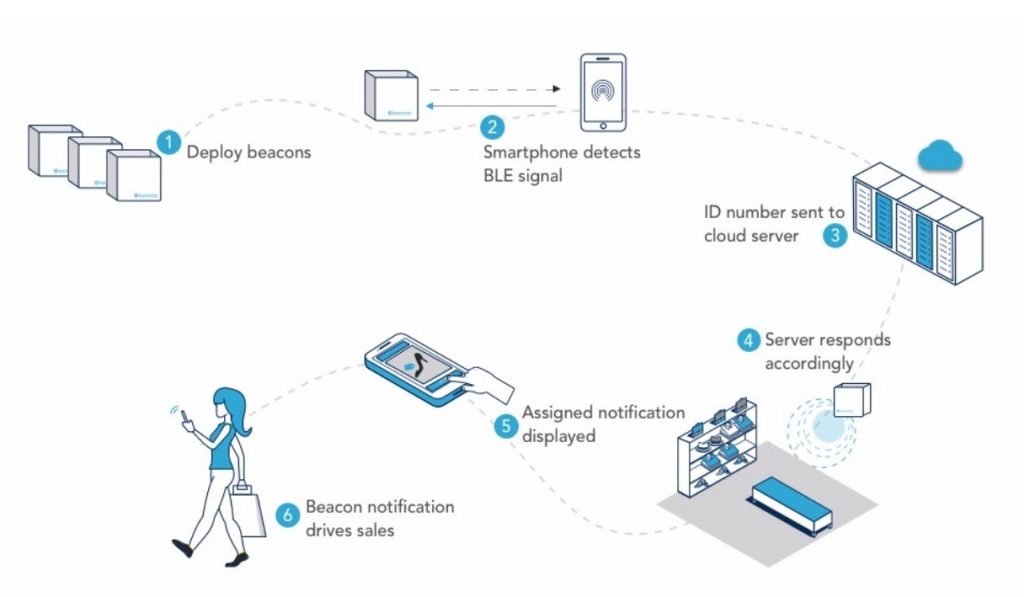
Bluetooth Security Issues Are Out There
- Bluetooth security issues are out there and affect potentially billions of devices, including both Apple and Android smartphones, Windows and Linux computers and anything else running unpatched Bluetooth firmware, such as the millions of IoT or so-called ‘smart’ devices.
- The two biggest issues known to-date are BlueBorne and BleedingBit. BlueBorne is a collection of vulnerabilities first revealed in September 2017 that can allow an attacker to take over a device, infect it with malware or establish MITM attacks. While patches were made available for PCs and smartphones by the time the BlueBorne vulnerabilities were made public, millions of devices running older software remain at risk.
- This includes unpatched Windows and Linux machines, Apple devices not on iOS 10 or later, and around an estimated 1 billion unpatchable Android devices (any Android device running an OS earlier than Marshmallow).
- Bluetooth mesh networking, an innovation that arrived in the same year as the BlueBorne vulnerabilities were discovered, allows many-to-many connections and ramps up the seriousness of BlueBorne: mesh networking means an attacker could easily jump from one device to another and build a Bluetooth botnet.
- While BlueBorne and BleedingBit have attracted the biggest headlines, they’re not the only vulnerabilities discovered in the modern Bluetooth protocol. Eagle-eyed observers of Apple’s Security updates will have noticed that in July 2018, Apple delivered patches to its platforms to protect against an attack that could allow a malicious actor to force pair with a device.
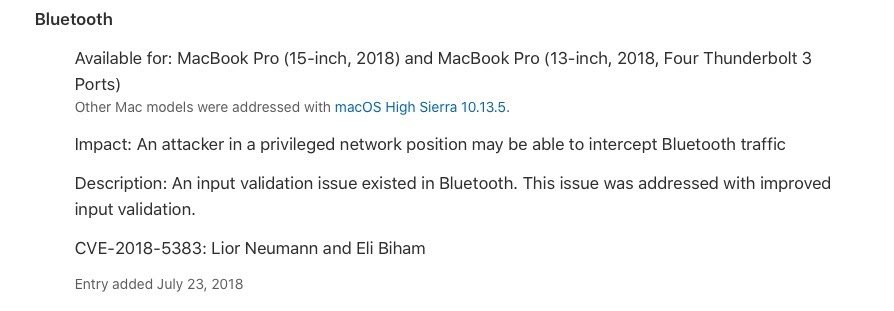
- The vulnerability allowed an attacker to discover the encryption key used on the victim’s device and use that to decrypt and forge data without alerting the user.
- CVE-2018-5383 didn’t just affect Apple devices though. Versions of the Android operating system were also vulnerable to attack, which was due to a design flaw in the Bluetooth protocol. Windows machines only escaped being implicated because at the time Microsoft were still deploying an even less-secure earlier version of the protocol.
- It is also worth mentioning that malware is taking greater interest in harvesting Bluetooth device information. Malware developed by the “ScarCruft” group was recently found to be exfiltrating Bluetooth related information from infected machines, including the device’s MAC address, class, connection status and authentication status.
Bluetooth Device Control
- For devices that are equipped with Bluetooth but do not actually need or use its functionality, be sure to reduce your attack surface with an unbeatable strategy: turn that Bluetooth off! If that’s not an option, your first step is to ensure that all devices are fully patched.
- To prevent eavesdropping by tools such as carwhisperer, ensure that Bluetooth-enabled devices like headsets cannot be paired with a default pairing code or use device control if your security software has that feature.
- Enterprise admins and security teams are also advised to implement Bluetooth device control across all the organization’s endpoints to address the more serious bugs and vulnerabilities noted in the previous section.
- Within the SentinelOne management console, this is easily achieved via the Network view and the Device Control tab. You can create a default policy to start with and then customize it or build your own custom rules from the ground up.
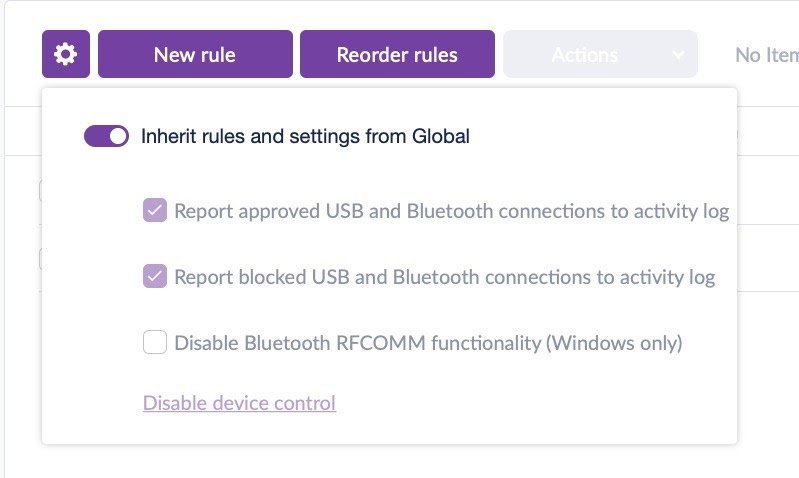
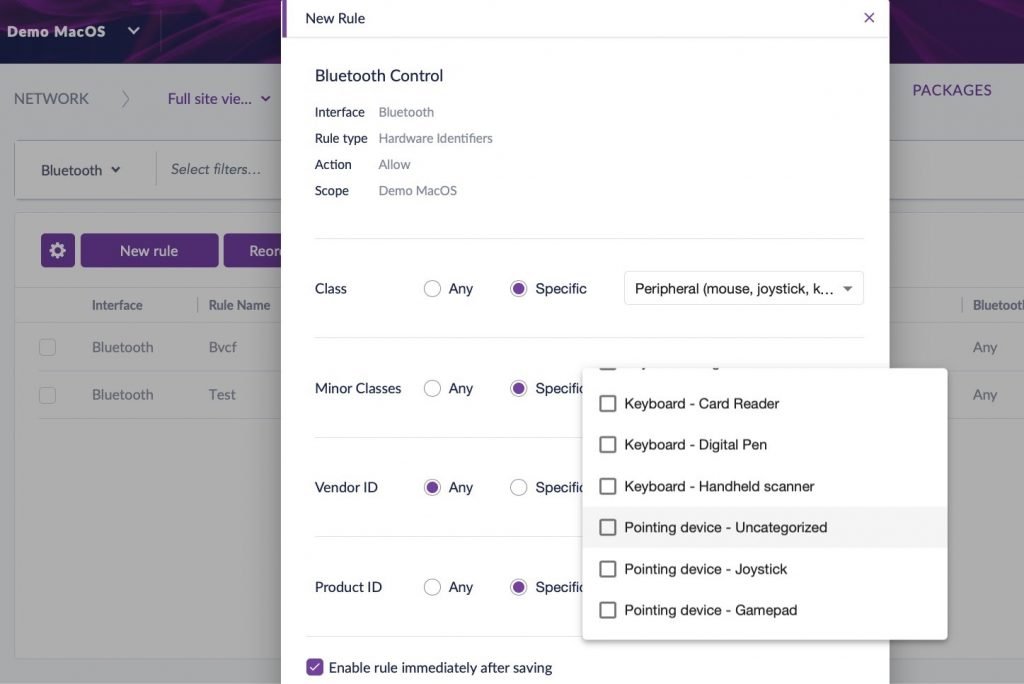
- With Bluetooth Device control, you’ll now have visibility into what Bluetooth connections are occurring on your endpoints. You also have the ability to restrict pairing to only devices you choose, or to block specific devices. The control can be as coarse or as fine-grained as you wish, with options to specify device class, minor class, Vendor ID and more,
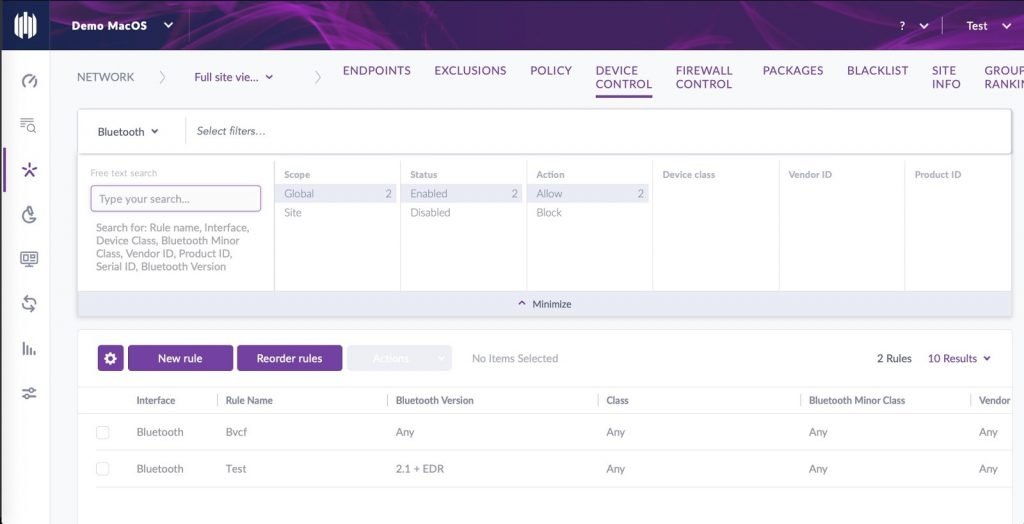
- Once you have policies in place, you can search across your network by choosing the “Device Control” tab and choosing “Bluetooth” from the drop down menu in the filter bar.
WEP Attacks:
- Packet Injections
- Fake Authentication
- FMS Attack, statistical, 2001
- KoreK Attack, statistical, 2004
- ChopChop Attack, fake ARP, 2004
- Fragmentation Attack, fragmentation, 2005
- PTW Attack (Pychkine, Tews, Weinmann) , statistical, 2007
Packet Injection
- This allows an outsider to generate a large amount of traffic on a network without being associated to it in any way. First, he must capture a packet of specific type. Although hidden behind encryption, packet type can be easily guessed based on packet size.
- An ARP request packet is always 28 bytes. By re-injecting it into the network, AP will respond to this forged request sending out packets to legitimate clients. Additional traffic is used to gather encrypted packets faster, and with more packets more the chance he’ll break the WEP faster.
Fake Authentication
Fake Authentication attack allows an attacker to join a WEP protected network even if he doesn’t know the root key. There are two ways a client can authenticate itself in an WEP protected network:
- The first method is Open System authentication, basically unprotected.
- The second method is called Shared Key authentication. This one uses the secret root key and a challenge-response authentication. Client asks AP to connect, AP sends a frame containing a challenge (random byte string, cleartext) and the client answers with a WEP encrypted frame. If ok, AP answers back with success.
- Attacker who sniffs out that handshake can join the network itself. Besides AP challenge, all bytes in 3rd frame are constant. Challenge is transmitted in cleartext in 2nd frame, so attacker can recover key stream (and IV) which is used to encrypt 3rd frame. With that he can now initiate authentication handshake and construct a valid frame (num)
FMS Attack
Attacker can perform a manupulation on RC4, enabling him to guess a byte of the key (5% probability). If key is wrong, attacker retries with a new key. To reach 50% success rate, attacker will need to capture a lot of packets (up to 6 million).
- If we know first “l” bytes of the per packet key, we can simulate “l” first steps of RC4-KSA. Don’t want to go too deep in the math here, basically next byte of key depends (is somewhat related) on the current one and that can be used to check if we’re on the right track. With each iteration we’re getting one more byte of key, eventually testing it. If it’s wrong, byte of the key is being switched with another probable value and process is restarted.
KoreK Attack
- This one is based on FMS attack (first appeared on netstumbler forum, 2004), but lets attacker finds the key faster.
ChopChop Attack
- Also found by “KoreK”, and opposed to exploiting a weakness in RC4, it attacks WEP protocol itself (CRC32 checksum and the lack of replay protection). It gives an attacker the ability to decryt a packet without knowing the key.
- Flipping a bit in the cipher text and then calculating which bit in encrypted CRC32 value must be flipped so that the packet is still valid. Frequently mentioned is approach is to take away last byte and try to guess its value.
- By injecting the altered packet back into the network, packet ends up as invalid because of incorrect ICV. The attacker can make it valid by XORing it with the value that depends on the truncated byte (0-255). The attacker can bruteforce that value. When found, AP (Access Point) will return the packet into the network.
- Knowing this value, the attacker can calculate the byte of plaintext (and the keystream). By repeating this operation, the attacker is able to decrypt a packet, getting both plaintext and keystream without main password.
Fragmentation Attack
- Great attack to run if there are no clients currently connected to the access point. Similar to ChopChop attack it speeds up cracking process by injection arbitrary packets into AP. It’s going to generate enough traffic to capture large number of IVs improving your chance of cracking the key (aircrack-ng). The “aireplay-ng” & “packetforge-ng” are standard toolkit for this attack.
- This packet is now 68 bytes long (64 bytes of known text, and 4 bytes ICV). Using XOR, the attacker gets 68 bytes of keystream for a give IV. Repeating this over and over again, attacker can get up to 1500 bytes of keystream for a IV. When he gets that, it’s easy to get keystream of other IVs, simply by sending a broadcast packet of 1500 bytes to AP. The AP will relay this encrypted with a new IV.
- As C ⊕ M = K the attacker can get the keystream for other IVs and build a dictionnary, allowing him to decipher packets on the network and create traffic.
PTW Attack
- What makes PTW powerful than all the other attacks is the fact it can make use of every packet captured. It implements a key ranking strategy which instead of trying all possible combinations of the key, picks a set number of likely keys and continues the RC4 algorithm based on those. Using different voting strategies the attacker can pick the most likely key byte at each decision in the tree to determine the correct key.
WPA [Wi-Fi Protected Access]
- Wi-Fi Protected Access (WPA), became available in 2003, and it was the Wi-Fi Alliance’s direct response and replacement to the increasingly apparent vulnerabilities of the WEP encryption standard. The most common WPA configuration is WPA-PSK (Pre-Shared Key). The keys used by WPA are 256-bit, a significant increase over the 64-bit and 128-bit keys used in the WEP system.
Note: WPA-PSK basicaly means that Wi-Fi network has a password that is shared by every single Wi-Fi network client.
- WPA included message integrity checks (to determine if an attacker had captured/altered packets passed between the access point and client) and the Temporal Key Integrity Protocol (TKIP). TKIP employs a per-packet key system that was radically more secure than the fixed key system used by WEP. The TKIP encryption standard was later superseded by Advanced Encryption Standard (AES).
- TKIP uses the same underlying mechanism as WEP, and consequently is vulnerable to a number of similar attacks (e.g. Chop-Chop, MIC Key Recovery attack).
- Usually people don’t attack WPA protocol directly, but supplementary system that was rolled out with WPA – Wi-Fi Protected Setup (WPS).
Note: TKIP (temporal Key Integrity Protocol) – The RC4 stream cipher is used with a 128-bit per-packet key, meaning that it dynamically generates a new key for each packet. Although still used, it’s considered obsolete after being replaced by CCMP in 2009.
WPA Attacks:
- Back and Tews’ Improved Attack on RC4, 2008, Inject
- Ohigashi-Morii Attack (Beck and Tews’ + Man in the middle), 2009, inject
- Michael Attacks, 2010, inject
- THe Hole196 Vulnerability, 2010, inject/dos/MITM
- Dictionary Attack against the handshake,key recovery
Conclusion
- Rogue Access Point is an unauthorized wireless access point with default settings and can be connected to any open port or network cable.
- Managing continuous and simultaneous use of the limited radio frequencies requires efficient spectrum-use techniques.
- Both interference and jamming are similar. However, the only difference is that the former is unintentional, whereas the latter is an intentional attack.
- War driving is the act of detecting wireless signals with the help of detection tools.
- The common NFC attacks include Man-in-the-middle, eavesdropping, data access or manipulation, and replay. With this, we conclude this lesson “Explain types of wireless attacks.”





